DNS Tunneling: Detecting DNS Tunneling Attacks
DNS, the Domain Name System, is responsible for translating human-readable domain names into IP addresses. This vital system has been exploited by cybercriminals and is being employed to create covert communication channels. These channels are being used to infiltrate networks, exfiltrate data, and evade traditional security solutions. DNS tunneling attacks are often used to bypass firewalls, intrusion detection systems, and data loss prevention mechanisms. It is one of the most used techniques for cybercriminals to maintain anonymity and to perform malicious activities without being detected. Tunneling is the process of enclosing data packets within other packets that employ the network's protocol. Information can be transmitted over a network even if the protocol used is not supported by the network. Security breaches can utilize HTTP, SSH, or TCP to send malware and compromised information via DNS requests, which are frequently unnoticed by firewalls. A regular DNS transaction is used during DNS tunneling to exchange information with a malicious server posing as the DNS authoritative server for a certain DNS zone.
DNS tunneling is an important threat because it allows attackers to slip harmful traffic through network security infrastructure. DNS tunneling exploits take advantage of the DNS protocol's versatility to construct a covert command and control channel for malware. DNS tunneling can be used by attackers to exfiltrate sensitive data or remotely manipulate a site. DNS tunneling is difficult to detect and can circumvent typical security measures such as firewalls, proxies, and intrusion detection systems (IDS). The risk associated with DNS Tunneling attacks can be reduced with the help of modern and comprehensive threat assessment tools.
One of the best tools for DNS tunnelling detection and prevention is Zenarmor NGFW. In a matter of seconds, the Zenarmor NGFW extension enables you to transform your open-source firewall into a Next Generation Firewall. Next-Generation Firewalls (NGFWs) provide the capability to withstand the ever-more-advanced cyber threats that are currently prevalent.
The premium editions of Zenarmor include robust DNS tunneling detection and prevention capabilities as part of their advanced security protocols. Through the implementation of proactive DNS traffic monitoring, Zenarmor is able to efficiently detect and obstruct unauthorized DNS tunneling attempts. By implementing this proactive measure, it is guaranteed that cybercriminals will be unable to utilize DNS tunnels as a covert communication channel.
Zenarmor Free Edition is offered without charge to all open-source firewall users. Some of the capabilities are layer-7 application/user aware blocking, granular filtering policies, commercial-grade web filtering utilizing cloud-delivered AI-based Threat Intelligence, parental controls, and the industry's best network analytics and reporting.
The following topics are going to be covered in this article;
- What is DNS tunneling?
- How does DNS tunneling work?
- Why is DNS tunneling a security concern?
- What are the common techniques and tools used for DNS tunneling?
- How is data exfiltrated using DNS tunneling?
- What are the real-world examples of DNS tunneling incidents?
- How can organizations detect DNS tunneling attacks?
- What are the best practices for mitigating DNS tunneling risks?
- How does DNS tunneling relate to VPNs, and what are the implications?
- What resources and tools are available to assist in DNS tunneling detection and prevention?
- How can Zenamor help prevent DNS Tunneling Attacks?
What is DNS Tunneling?
DNS tunneling is a clever and deceptive technique used by cybercriminals to covertly transmit data over the Domain Name System (DNS). The purpose of DNS tunneling is to use legitimate network traffic to send secret messages hidden inside or to carry obtained data within.
DNS can be thought of as the Internet equivalent of a phone book or residential address book. Converting machine-friendly IP addresses from human-friendly URLs is its primary goal. Administrators can query and get details about domain names using DNS's basic protocol. The flexibility of the DNS protocol, which has relatively few limitations on the types of data that can be included in a DNS request, is used by DNS tunneling. Because of this versatility, hackers can utilize DNS requests to set up a malware command and control channel. Attackers employ the technique called DNS tunneling to get around network constraints and encrypt data from other protocols or programs into DNS queries and answers. It's comparable to a Trojan horse, in which a message pretending to be a DNS request contains malicious malware or applications.
For a better understanding, imagine you have a postcard with a message that you want to send to someone. You write it in a foreign language on the postcard instead of sending the message directly. Now it seems like a card sent while traveling a foreign country, or a card from a pen pal. The card is then sent through regular mail without anyone suspecting that it contains a hidden message. Only you and the recipient understand the foreign language and can decode the real message. DNS tunneling operates on a similar principle. Instead of sending data directly over the internet, cybercriminals encapsulate it within DNS queries and responses. These DNS packets are like postcards, appearing as normal traffic to most observers. However, they carry hidden information that can be used for many hidden purposes. It is mostly utilized for data exfiltration, command-and-control (C&C) communication, including bypassing network security measures.
By employing DNS as a communication channel, the purpose of DNS tunneling can vary, but some common uses are as follows:
- Despite the added latency, complexity, and encoding, intruders can still prefer DNS Tunneling for data exfiltration and slip confidential information out over DNS.
- DNS tunnels are utilized as a total controller channel for a previously attacked internal host, permitting attackers to download code to malware, steal data from the company, or acquire full unauthorized access to the systems.
- DNS tunnels are capable of helping to get around captive portals and reach unpaid internet access.
- As DNS is a very flexible protocol with few restrictions on the data it can contain, DNS tunneling sneaks data past an organization's network security solutions like firewalls and intrusion detection systems.
- DNS is to be employed as a communication channel to send and receive messages. Encoding data in DNS in a way that can be understood by the DNS protocol, like a specific format or the DNS queries on both sides with added info.
- Some are designed to go to attacker-controlled DNS servers, to receive the requests and responses in the corresponding DNS replies. Malware can communicate with its handler without being detected easily. While outgoing communication can either respond to queries from the malware operator or exfiltrate sensitive data, incoming DNS traffic has the potential to deliver commands to the malware.
DNS tunneling presents a significant security challenge because it can be challenging to spot among the vast amount of legitimate DNS traffic. To effectively defend against this technique, it's essential to understand how it works, recognize its signs, and implement appropriate security measures. Organizations can use specialized tools to monitor DNS traffic and detect DNS tunneling. They can implement best practices, such as only allowing outbound DNS to trusted sources and incorporating a DNS firewall.
How does DNS tunneling work?
DNS tunneling is a method that exploits the structure of DNS to smuggle non-DNS data within DNS packets, allowing malicious actors to create covert communication channels. In limited networks, DNS tunneling was first intended to be a straightforward method of getting around captive gateways and accessing the internet without restriction. However, in current times, it's frequently employed for evil intent, including theft of information or command and control techniques. This method usually necessitates that the infiltrated machine be connected to the outside world and that the attacker be in control of a domain and server that can function as an authoritative server. To understand how it works, let's have a look into the technical workings of DNS tunneling:
- A domain is assigned by the attacker, who then directs it to the server it administers. The malicious software for tunneling is preinstalled.
- There are no limitations on DNS requests entering or leaving the firewall. Using this, the hacker breaks through the victim's firewall by infecting a machine with malware.
- By utilizing the top-level and root domain servers, the DNS resolver obtains the IP address.
- At this point, the attacker-controlled authoritative DNS server has the tunneling software installed. It receives the DNS query after it has been routed via the DNS resolver.
- As a result, without a warning, a connection gets established between the
Why is DNS tunneling a security risk?
DNS tunneling is a pressing security concern with wide-ranging implications for both organizations and individuals. The significance of DNS Tunneling as a security concern lies in its ability to facilitate covert communication and data exfiltration. It evades traditional security measures and encourages attackers to bypass firewalls and security protocols for their malign purposes.
Here are the key reasons why DNS tunneling is a serious security issue:
- DNS tunneling allows malicious actors to sneakily exfiltrate sensitive information from compromised networks. Encrypted or not, exposure to confidential business data and personal customer information might lead to significant financial and reputational damage for organizations and individuals.
- Cybercriminals often use DNS tunneling to establish command and control channels for malware and botnets. Allowing attackers to control the compromised system and execute commands can lead to further attacks, such as ransomware or data theft. Industry-wide available off-the-shelf tunneling toolkits on the internet make it possible for even unsophisticated attackers to use this technique.
- Evasion of conventional security measures, including firewalls, proxies, and intrusion detection systems. IP-Over-DNS Tunneling utilities actualized the IP stack on the DNS inquiry reaction convention. That simplifies moving information by using standard communication programs like FTP, Netcat, SSH, etc.
- State-sponsored actors and cybercriminals use DNS tunneling for corporate espionage, stealing intellectual property, or gaining unauthorized access to sensitive information. The hidden nature of these attacks makes attribution challenging.
- Malicious domains and subdomains established for DNS tunneling are used for phishing campaigns and distributing malware. DNS tunneling can be difficult to detect and mitigate, as it can make the traffic appear to be legitimate DNS traffic. This puts individuals and organizations at risk of falling victim to these cyberattacks.
- The covert transmission of data through DNS tunneling can lead to serious violations of data privacy regulations and laws. Organizations may unknowingly breach data protection rules due to the hidden nature of these activities. DNS tunneling is used to bypass captive portals, allowing users to access Wi-Fi services without paying for them. This can lead to financial losses for service providers.
The prevalence of DNS tunneling attacks continues to rise, as cybercriminals adapt to security advancements. These attacks are no longer limited to nation-state actors; cybercriminal groups also utilize DNS tunneling to carry out financially motivated attacks. A study done in previous years claimed a number shy of 80 percent of organizations had experienced at least one DNS tunneling attempt. In 2021, a group of hackers used DNS tunneling to exfiltrate data from a US government agency.
What are the DNS tunneling techniques?
DNS tunneling can be used for various malicious purposes, including data exfiltration, command and control, and malware propagation. To make the DNS tunneling more effective and difficult to detect, attackers can use various methods for encoding or disguising the data. Some common DNS tunneling techniques are outlined below:
- Subdomain Labeling: Attackers create a series of subdomains under a malicious domain and encode data within these subdomain labels. Each subdomain may contain a portion of the hidden information. Subdomain labeling is a fundamental DNS tunneling technique. It's often used in combination with other methods to transmit data covertly.
- DNS Data Query Manipulation: Attackers modify legitimate DNS queries to include non-DNS data, using various encoding techniques. The DNS response from the server carries the hidden data. This technique is used when attackers want to disguise their communication as regular DNS queries and responses.
- Base64 Encoding: Data is encoded using Base64, a binary-to-text encoding scheme, to make it compatible with DNS subdomain labels, which accept alphanumeric characters and hyphens. Base64 encoding is commonly used in DNS tunneling to represent non-DNS data within DNS subdomain labels, as it provides efficient encoding and decoding.
- Hexadecimal Encoding: Data is converted into hexadecimal format and then embedded within DNS subdomain labels. This encoding method uses numbers from 0 to 9 and characters from A to F. Hexadecimal encoding is used when attackers need to work with binary data, as it provides a way to represent the binary information in DNS traffic.
- Binary Encoding: Data is directly converted into binary format and inserted into DNS subdomain labels, with 0s and 1s representing the information. Binary encoding is employed when attackers want to keep the encoding process minimal and work with the most compact representation of data.
- IP-over-DNS tunneling: Some utilities may have implemented the IP stack via the DNS inquiry response protocol, making malicious activities easier.
- High and low throughput DNS tunneling: This technique is characterized by a significant change in DNS traffic volumes to one specific domain or a few domains. The DNS request length to the domains will increase, and the time between the requests will be shorter. Similar to high throughput DNS tunneling, this technique uses the DNS protocol to transfer data that is unrelated to the DNS query. However, it is designed for slower data transfer and may not be as easily detectable as high throughput tunneling.
- Legitimate DNS Servers: Attackers may compromise or abuse legitimate DNS servers to conduct tunneling. They use these servers to handle their covert communication, leveraging the trust associated with established DNS infrastructure. This approach can help attackers evade detection by disguising their activities among legitimate DNS traffic.
What are the DNS tunneling tools?
Cybercriminals often develop custom tools or scripts designed specifically for DNS tunneling. These tools simplify the process and allow for greater control, providing flexibility and customization for attackers over the tunneling process. There are also several off-the-shelf DNS tunneling toolkits and solutions readily available on the internet, making it possible for even unsophisticated attackers to use this technique. Some are open-source programs like sliver, dnscat2, iodine, and DNSStager. With the help of these tools, generic messages can be encoded as subdomains for DNS queries and as several kinds of DNS responses, including TXT, CNAME, MX, IPv4, and IPv6 addresses. DNScat2 is designed to create an encrypted command and control channel for malware. In addition, TCP-over-DNS, OzymanDNS, DNS2TCP are employed for tunneling TCP traffic through DNS queries and responses. Some attackers employ commercially available DNS tunneling tools that are designed for legitimate purposes, for bypassing network restrictions or censorship, such as Cobalt Strike. DNSTrap is for detecting DNS tunneling by using an artificial neural network. These tools can be repurposed for malicious activities including DNS tunneling attacks.
The prevention of DNS tunneling threats necessitates a multifaceted strategy that incorporates both human and technological components. Security professionals should employ specialized tools and advanced methods for DNS traffic analysis, anomaly detection, and threat intelligence feeds to identify and block malicious DNS tunneling activities. DNS traffic should be monitored for any signs of malicious activity, the outbound DNS should be restricted, and DNS firewalls should be implemented.
How is data exfiltration using DNS tunneling?
DNS tunneling is used to exfiltrate large amounts of data by encoding the data in DNS queries and responses, which are then transmitted to the attacker's server. One method is by direct internet communication between the malware on the victim's computer and the perpetrator's DNS server. The data can be encoded using various techniques such as base64 encoding or hex. A character set that is employed as well in DNS names is used to encode the information inside of the file, before being encapsulated within the DNS packets. This helps to ensure that the data remains intact during transmission and can be easily decoded on the receiving end. Chunks are then generated from the encoded character stream. In order to enable the receiving end to reconstruct the file structure in the event that multiple files are exfiltrated, the filename is attached to each portion of the information. This method will not work if the firewall is configured to prevent outgoing DNS communications. However, because the attacker's domain name is omitted from the DNS query and the payload to total data size ratio is improved, it is efficient. Regular DNS resolver chains are utilized in another DNS exfiltration technique. Using a business network, for example, the malicious program on the victim's computer interacts indirectly through its configured DNS server. The address of an internet domain under the attacker's control is attached to the default name server that is set up on the victim's computer. The nameserver for the domain receives a request for the IP address from the corporate network DNS server, which then forwards it to DNS Server. The attacker receives the encrypted binary data from the nameserver. Because it makes use of the company's DNS infrastructure, this method is unaffected by firewall limitations.
Some of the techniques used for data exfiltration through DNS tunneling include High and Low throughput DNS tunneling and fragmentation. High throughput technique is characterized by a significant change in DNS traffic volumes to one specific domain or a few domains. The DNS request length to the domains will increase, and the time between the requests will be shorter. It is used to exfiltrate large amounts of data quickly. Low throughput DNS exfiltration technique is designed for slower data transfer and may not be as easily detectable as high throughput tunneling. It is used to exfiltrate smaller amounts of data over a longer period. The data can be fragmented into smaller pieces and distributed across multiple DNS packets. This makes it more difficult for network security solutions to detect the presence of non-DNS data within the DNS packets. DNS tunneling can be used for large amounts of data exfiltration). It is an attractive choice for intruders as DNS traffic is often unmonitored and unrestricted. Mostly it does not interfere with DNS traffic for the functioning of the internet.
What are the real-world examples of DNS tunneling incidents?
Here are some real-world examples of DNS tunneling incidents:
- Some attacks were carried out by a group known as APT1 in 2014 employing DNS Tunneling techniques. APT1 is a sophisticated cyberespionage group that is believed to be state-sponsored by China. The Chinese government was accused of using DNS tunneling to exfiltrate data from the US government and private companies.
- The Syrian Electronic Army (SEA) launched a series of attacks in 2015, against high-profile websites. Twitter, Facebook, and Microsoft were included in these DNS tunneling attacks. The SEA is a hacktivist group that is known for its attacks against websites that support the Syrian government.
- The Fancy Bear hacking group used DNS tunneling to exfiltrate data from the Democratic National Committee (DNC) in 2017. It's a group that is believed to be sponsored by Russia.
- In 2018, the Iranian hacking group APT33 used DNS tunneling to exfiltrate data from the US government and defense contractors. APT33 is a sophisticated cyberespionage group that is believed to be sponsored by the Iranian government.
- In 2020, the North Korean hacking group Lazarus Group used DNS tunneling to exfiltrate data from South Korean cryptocurrency exchanges. The Lazarus Group is a sophisticated cybercrime group that is believed to be sponsored by the North Korean government.
- A malware group based in the Middle East named OilRig developed tools with unique DNS Tunneling protocols for C2. The perpetrators did manage to use this as a backup channel in case the first ones didn't go through, in addition to using it as their primary means of communication.
- APT29, also known as Cozy Bear, is a sophisticated Russian state-sponsored hacking group. In 2018, FireEye reported that APT29 used DNS tunneling to exfiltrate data from targeted organizations. They used various subdomains to encode and transmit stolen information, evading detection by disguising their malicious activity as DNS traffic. APT29's use of DNS tunneling allowed them to exfiltrate sensitive data while maintaining a low profile. The scale of the impact varied depending on the specific targets, but it underscored the group's advanced capabilities in conducting covert cyber espionage.
- The Sea Turtle cyber-espionage group targeted organizations by hijacking DNS infrastructure to redirect traffic and gain unauthorized access to sensitive data. Sea Turtle's DNS tunneling attacks exposed the vulnerability of DNS infrastructure and the potential for large-scale data breaches.
- Astaroth is a notorious information-stealing malware that uses DNS tunneling to communicate with its command and control servers. It encoded and transmitted stolen information within DNS queries, making it difficult for security solutions to detect the malicious activity. Sophisticated attackers have employed steganography-based DNS tunneling. This technique involves hiding data within images or other media files, which is challenging to detect, encoding them, and then transmitting them via DNS queries and responses.
How can organizations detect DNS tunneling attacks?
DNS tunneling is a type of attack that exploits the Domain Name System (DNS) protocol to tunnel malware and other data through a client-server model. DNS tunneling attacks are difficult to detect and pose a significant threat to organizations. Here are some techniques and tools to detect DNS tunneling attacks.
- Anomaly Detection: This method involves monitoring DNS traffic and looking for anomalies such as an unusually high volume of DNS queries, large DNS txt records, or DNS requests to unknown or suspicious domains.
- Payload Analysis: It involves analyzing a single DNS payload to detect specific DNS tunneling utilities.
- Traffic Analysis: This technique involves analyzing multiple requests or overall traffic to detect malicious activity. A domain's history, location, number of hostnames per domain, and volume of DNS traffic are a few of the attributes that can be used for network traffic analysis.
- Statistical Examination: It involves checking the specific character staff of the DNS names. DNS names that are authentic commonly contain fewer numbers, while encoded names tend to have a lot of numbers. Examining the percentage of numerical characters in domain names and examining the percentage of the length of the Longest Meaningful Substring (LMS) help detect DNS tunneling.
- Specialized Tools: Various specialized tools, like Zenarmor NGFW, exist that specifically are designed to monitor DNS traffic and detect DNS tunneling. These tools often combine different approaches into a single package and they offer a more comprehensive solution for DNS tunneling detection.
The primary line of protection regarding DNS tunneling attacks is constant DNS traffic monitoring. Advanced threat detection products can help automate this process and they provide real-time monitoring and alerting. Additionally, organizations can reduce the risk associated with DNS tunneling by implementing DNS-over-HTTP or DNS-over-TLS to secure internal DNS traffic and by having security tools with decryption capabilities for every widely used encryption technology, such as Kerberos and TLS 1.3. For example, you may easily configure DoT on your OPNsense firewall to hide your DNS queries.
Regular DNS traffic analysis can be conducted to pay close attention to the volume, frequency, and size of DNS requests and responses. Abnormal spikes in DNS traffic are a red flag. Implementing anomaly detection systems can contribute to this goal. They can use machine learning and statistical models to detect unusual patterns. DNS query length analysis to look for DNS queries longer than typical DNS queries. Setting thresholds for query length and trigger alerts will be useful. Doing subdomain analysis to look for an excessive number of subdomains within DNS queries, and suspicious characters in them, which is a possible red flag. Significant imbalances in query-response ratios, and rapid and repetitive queries to a specific domain or subdomain, especially in off-hours are risk factors. A list of known malicious domains can be maintained and watched, and DNS sinkholes can be implemented to redirect the DNS traffic to a controlled server to observe. Commercial DNS security tools, DNS firewalls, and proxy servers can be employed. Regular security audits should be conducted for vulnerabilities. Detection of DNS tunneling attacks requires vigilance and proactive monitoring. By looking for unusual patterns and leveraging the right tools, organizations can increase their chances of identifying and mitigating these covert threats before they lead to data breaches or other security incidents.
What are the best practices for mitigating DNS tunneling risks?
The avoidance of DNS tunneling attacks necessitates a multifaceted strategy that incorporates both human and technological components. Some best practices to prevent DNS tunneling attacks include:
- Monitoring DNS traffic: Organizations should monitor their DNS traffic for any signs of malicious activity, as DNS tunneling attacks can be effective if launched against company networks.
- Using specialized tools: There are several specialized tools available that are specifically designed to monitor DNS traffic and detect DNS tunneling. These tools often combine several methods into a single package, offering a more comprehensive solution for detecting DNS tunneling.
- Restricting outbound DNS: Organizations can restrict outbound DNS to trusted sources, such as their own DNS servers, to prevent DNS tunneling.
- Implementing DNS firewalls: DNS firewalls can be used to block DNS tunneling traffic and detect any attempts to bypass network security.
- Restricting or prohibiting irrelevant DNS requests: Reducing the attack surface for DNS tunneling is achieved by prohibiting or restricting pointless DNS queries. This involves restricting the number of DNS queries coming from a single source and preventing DNS queries to nonexistent domains. Certain record types, such TXT or NULL records, which are frequently used in DNS tunneling, can be set by DNS servers to deny searches for them.
- Integrating technological and human solutions: To address DNS tunneling, companies should consider both technological and human strategies. This includes building familiarity with expected and required uses to ease the challenge.
- Regularly updating and patching DNS servers: Regularly updating and patching DNS servers can help prevent DNS tunneling attacks by fixing known vulnerabilities and ensuring that the DNS infrastructure is up-to-date.
In addition, DNS Security Extensions (DNSSEC) helps protect against DNS spoofing and cache poisoning attacks. DNSSEC is a set of extensions to DNS that provides authentication and integrity to DNS data. It ensures the authenticity and integrity of DNS data, reducing the risk of DNS tunneling through manipulated DNS records. Moreover, consider using commercial DNS security solutions that offer real-time threat intelligence feeds, heuristic analysis, and the ability to detect and block DNS tunneling attempts. Some general security steps can be taken like segmenting the network, implementing threat intelligence feeds, applying zero trust principles, and implementing DNS sinkholing.
Mitigating DNS tunneling risks is an ongoing process that requires a combination of preventive measures, advanced security tools, and a vigilant cybersecurity team. These practices can significantly improve DNS security and reduce the risk of falling victim to DNS tunneling attacks.
How does DNS tunneling relate to VPNs, and what are the implications?
DNS tunneling is a technique that can be used to encapsulate data within DNS queries and responses. This data can then be transmitted over a network without being detected by traditional security measures. VPNs (virtual private networks) create a secure tunnel between two devices over a public network like the Internet. DNS tunneling is used within VPNs to create additional layers of security or to bypass network restrictions. For example, an attacker could use DNS tunneling to exfiltrate data from a compromised network through a VPN. They can bypass a firewall that is blocking access to certain websites. Intruders can utilize DNS tunneling to exfiltrate sensitive data from an exposed network through a VPN. They could use DNS tunneling to bypass network restrictions, such as firewalls and content filters. This could allow them to access websites or services that are blocked on the network. They could use DNS tunneling to gain unauthorized access to networks that are protected by VPNs. This could allow them to launch attacks against the network or to steal data.
Some VPN providers offer DNS-over-VPN services, which encrypt DNS queries to enhance privacy. DNS tunneling VPN assigns a security category to servers connected to its services, which you may choose to allow or prohibit and track. End users can pass off outbound traffic as DNS requests by using these services. However, if these encrypted DNS queries are compromised or manipulated, they potentially violate acceptable use, data loss prevention, or security policies and they could be used for DNS tunneling. Attackers can leverage DNS-over-VPN services to blend in with legitimate encrypted DNS traffic. Reputable VPN providers with strong encryption and a commitment to security should be picked to minimize the risk of using VPN services for malicious activities. DNS leak protection and intrusion detection and prevention mechanisms should be a part of these providers.
What are the DNS tunneling detection and prevention tools?
There are several resources, tools, and technologies available to assist in DNS tunneling detection and prevention. Some examples of DNS tunneling detection and prevention tools and resources are as follows:
- DNS monitoring and filtering tools: Implementing powerful DNS monitoring tools capable of discovering suspicious DNS traffic patterns, such as unusual query sizes or frequent queries to the same domain, can help in detecting and preventing DNS tunneling attacks. DNS filtering services can help in blocking access to malicious domains and IP addresses, reducing the risk of DNS tunneling attacks.
- DNS firewall: Firewalls can be used to block DNS traffic to known malicious DNS servers. A properly configured DNS firewall can quickly identify and block many intrusions.
- DNSSEC: DNSSEC is a set of extensions to DNS that provide origin authentication of DNS data, data integrity, and authenticated denial of existence. Implementing DNSSEC can help in preventing DNS tunneling attacks.
- Network monitoring tools: Network monitoring tools can be used to monitor DNS traffic for unusual patterns or anomalies. For example, Nagios is a network monitoring tool that can be used to monitor DNS traffic for unusual patterns or anomalies.
- DNS tunneling detection and prevention tools: There are a number of specialized DNS tunneling detection and prevention tools, like Zenarmor NGFW, available. These tools employ a variety of methods to identify DNS tunneling traffic including machine learning and anomaly detection. Intrusion detection systems/intrusion prevention systems (IDS/IPS) systems can be used to detect and block DNS tunneling traffic in addition. Some of the DNS tunneling detection and prevention tools are listed below:
- Zenarmor: Zenarmor is a comprehensive security solution that includes DNS tunneling detection and prevention features.
- CloudFlare DNS: CloudFlare DNS is a DNS filtering service that can be used to block DNS traffic to known malicious DNS servers and domains.
- Suricata: Suricata is an open-source IDS/IPS system that can be used to detect and block DNS tunneling traffic.
- Infoblox Advanced DNS Protection (ADP): This product with NIOS 7.3 or above, is capable of detecting and blocking most DNS tunneling tools.
How can Zenamor help prevent DNS Tunneling Attacks?
Zenarmor is a comprehensive security solution that includes DNS tunneling detection and prevention features. Blocking DNS tunnels is an essential component of today's cybersecurity structures. DNS tunneling involves embedding unauthorized data within DNS queries and responses, exploiting the inherently trusted nature of DNS traffic. The potential risks posed by DNS tunnels are significant, including data breaches, command and control for malware, and data exfiltration.
The DNS Tunneling feature of Zenarmor is intended to strengthen the security of your network by proactively barring attempts to circumvent network security filtering via DNS tunneling. It is a strong defense against a method that cybercriminals use to avoid detection. DNS tunneling utilizes DNS requests and responses to transmit malicious data, frequently circumventing conventional network security.
Zenarmor's premium subscription package includes advanced security rules that include strong DNS tunneling detection and prevention capabilities. Zenarmor monitors DNS traffic in real-time, allowing it to detect and prevent illegal DNS tunneling efforts. By turning on this feature, Zenarmor will be able to recognize and stop attempts at DNS tunneling. By taking this proactive measure, it is ensured that DNS tunnels cannot be used by cyberattackers as a secret communication channel.
You may easily enable DNS tunnelling prevention on your Zenarmor NGFW by following the next steps: To enable Advanced Security on your Zenarmor firewall you may follow these steps:
- Navigate to the Security tab on the policy configuration page.
- Scroll down to the Advanced Security pane.
- Click on the DNS Tunneling toggle bar to block DNS tunneling traffic on your network.
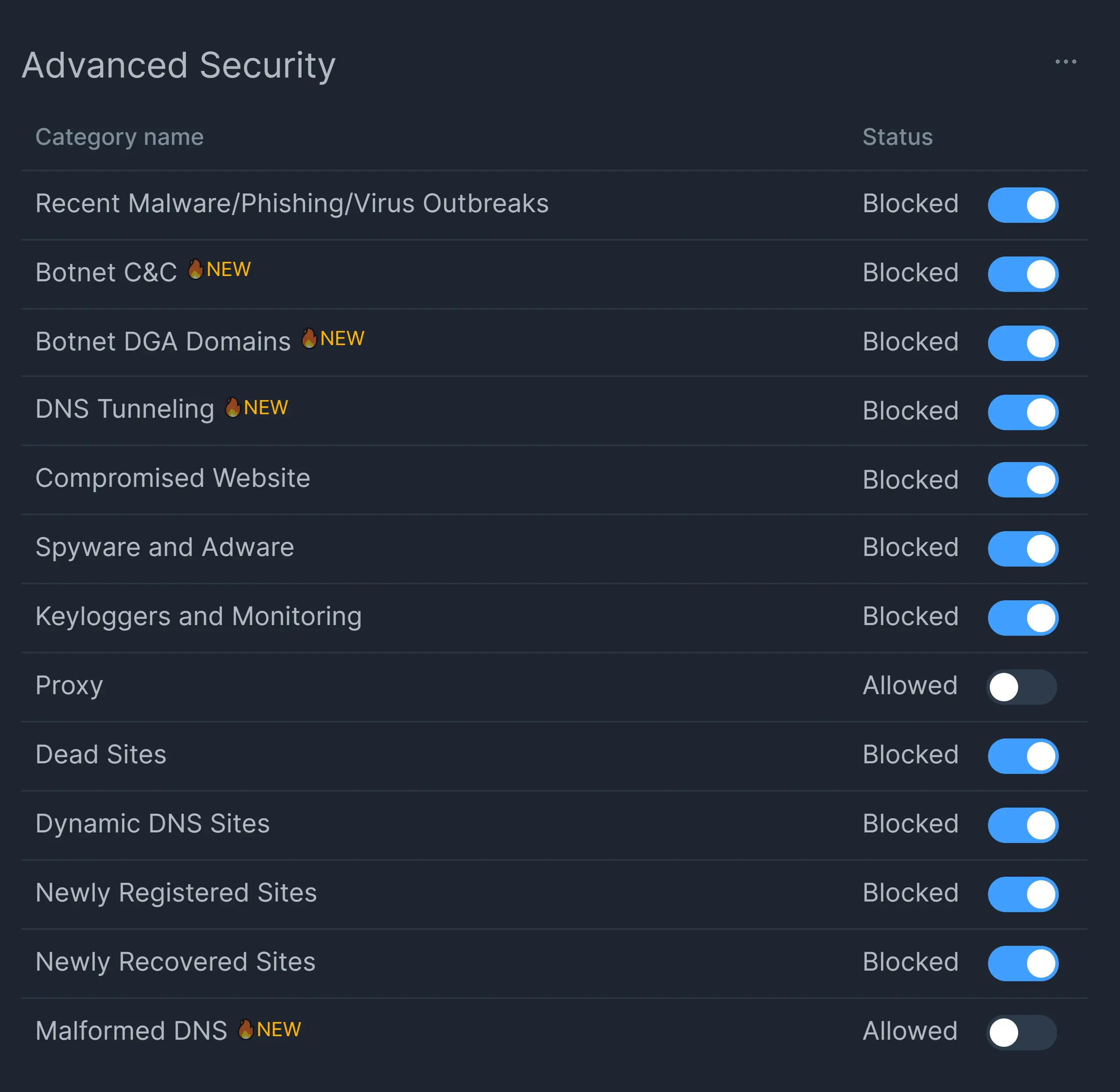
Figure 1. Zenarmor Advanced Security Control Settings
