What is Data Loss? Is Any Data Recovery Safe?
If you've lost your data, your initial inclination may be to use whatever tools are available to recover as much as possible. However, before downloading any new program, you should be informed of the hazards associated with data recovery software.
So, is it secure to utilize any data recovery software? Some are, some aren't. Not all software for data recovery is created equal. You might make problems worse or infect your computer with malware if you do not thoroughly examine the software you download or use.
You'll discover the solution to the question of how safe the Data Recovery Tool is in this article. We will first discuss what data loss is and how it occurs, after which we will discuss data recovery safety concerns and variables that affect data loss. You will have a better understanding of data loss and recovery security issues by the article's conclusion.
What is Data Loss?
Data loss is the planned or unintentional deletion of data by people or systems inside or outside an organization. Data loss is analogous to a data breach in the sense that data is compromised. In a data leak, the information is often intact but in the wrong hands. A data breach may result in data loss, but the data itself is deleted.
There are several sources of data loss, which might vary by industry. Some firms may be more concerned with external threats, whilst others may be more concerned with internal human error. Data loss can occur during routine IT activities, such as migration, or as a result of ransomware or other malicious software.
The consequences of data loss may also vary depending on whose data is lost. In addition to impacting an organization's internal data, the loss of a third party's sensitive data might compromise its legal compliance status.
Regardless of how or why data loss happens, all businesses must have preventive and recovery procedures in place, as well as an understanding of the implications and repercussions of data loss.
How Does Data Loss Work?
Hardware failure, software corruption, human mistakes, and natural disasters are all frequent unintended sources of data loss. Data loss can also occur during migrations, power outages, and erroneous system shutdowns.
Hardware failure is the leading cause of data loss. A hard disk may fail as a result of improper handling, overheating, mechanical problems, or even the passage of time. Proper hard drive maintenance can help avoid data loss, and users who are aware of a disk's lifespan can plan for its replacement.
When computers are inappropriately shut down, software corruption is an additional frequent source of data loss. Typically, these shutdowns are caused by power failures or human mistakes, so it is the responsibility of the company to plan for these situations and guarantee the appropriate shutdown of systems. All of the following can result in data loss due to natural catastrophes, including hardware damage and system failure without data backups. Having a disaster recovery (DR) strategy and performing frequent backups are the most effective ways to prevent this sort of data loss.
How Safe is Data Recovery?
The Internet is flooded with guidelines and tutorials on how to restore deleted data at home. Using data recovery software is a far safer method of retrieving lost data than attempting physical data recovery. However, this does not mean that data recovery software is risk-free. Although there are several excellent data recovery solutions available, you should exercise extreme caution. There are two primary dangers associated with data recovery software. When installing data recovery software, you run the risk of overwriting the data you are attempting to recover. Secondly, if your hard disk has a physical defect, executing data recovery software may cause more damage.
Let's begin by addressing the problem of data recovery software overwriting your data. When data is removed from a hard disk drive, it is not destroyed in the conventional sense. When you delete a file, all you are doing is deleting the reference to the master file table, which is simply a map to the location of the real data, which is stored as a series of 0s and 1s. As long as no new data is written to the same portion of the hard disk, data recovery software should be able to recover your data. But if data is written to this portion of the disk, which the operating system has now identified as free space, data recovery would be difficult. In addition to using data recovery software, your data might be overwritten in other ways. Your operating system is continually writing data, including driver updates, cookies, and OS updates, while your computer is in use. The longer your disk has been in use after your data has been wiped, the more likely it is that it is irretrievable. This problem has two solutions. In the event of an emergency, you should ensure that you have data recovery software installed immediately. In this manner, there is no chance of overwriting the data you desire to recover. Additionally, you may install data recovery software on portable media, such as a USB flash drive.
The second major danger associated with data recovery software is that it may exacerbate a physical failure, leaving your data unrecoverable. When the read/write heads of a hard disk drive come into contact with the magnetic platters, data recovery software will be unable to repair the resulting damage. If you attempt to use data recovery software after a hard drive failure, you will make it more difficult for a professional data recovery specialist to recover your data in the future. In the case of a head-on collision, the drive should be shut off immediately.
Be cautious when utilizing data recovery software. You should check that emergency software is already installed on your computer, or install one on a USB flash drive. If you install data recovery on your hard drive after your data has been lost, you risk overwriting it. If your hard drive has had a physical failure, such as a head collision, you should avoid data recovery software and instead seek the help of a data recovery professional.
What Factors Affect Data Loss?
With the necessary procedures and protections in place, you may prevent data loss, even if it seems inevitable. Understanding the key causes and warning indicators of possible data loss is the first step. Knowledge is strength. After gaining this knowledge, the next step is to discover the best data loss prevention strategies. With this information, you should be able to take the required precautions to avoid data loss from occurring.
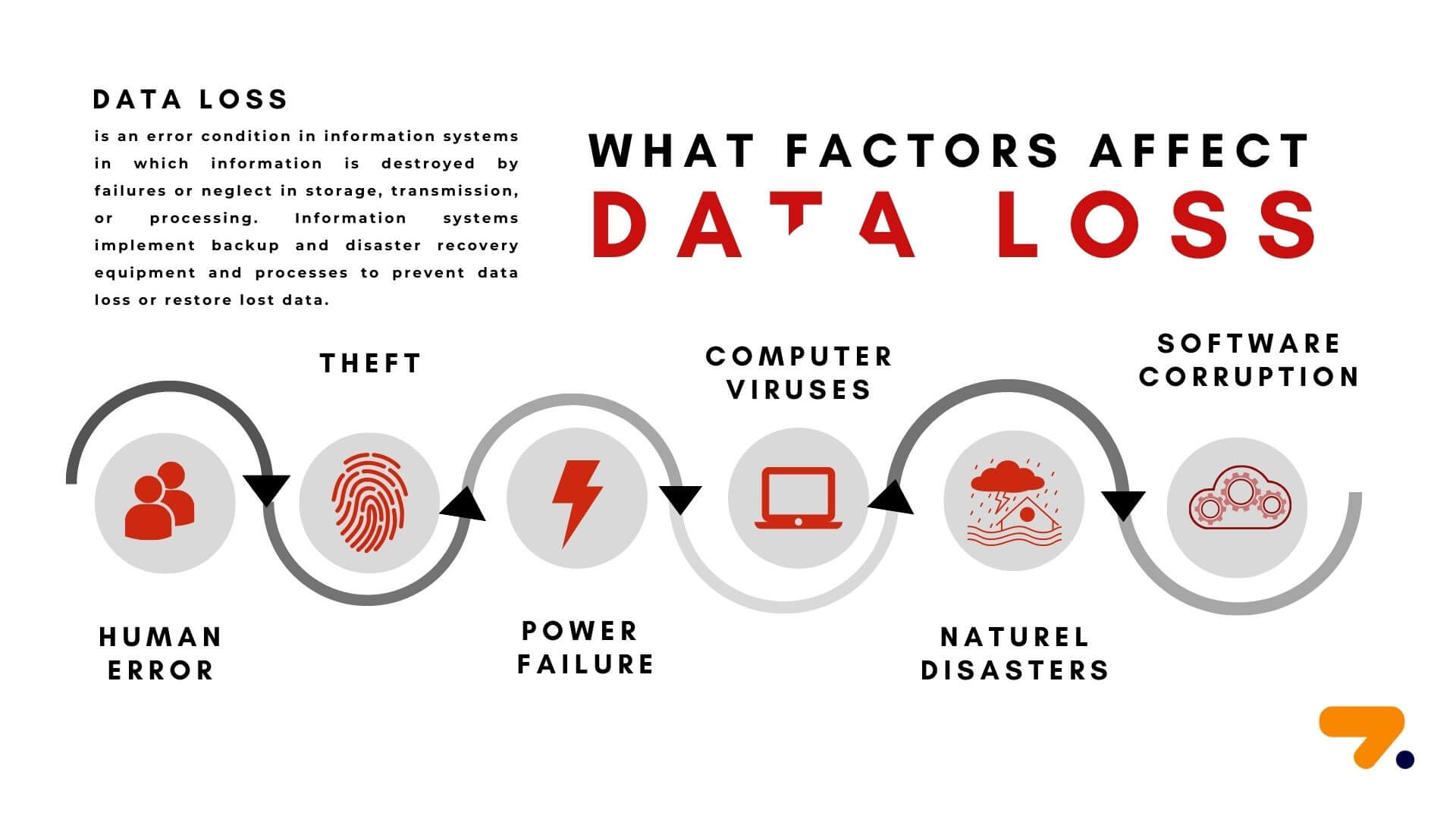
Figure 1. Factors Affect Data Loss
Here are the six leading reasons for data loss:
- Natural Disasters
- Theft
- Human Error
- Computer Viruses
- Power Failure
- Software Corruption
1. Natural Disasters
In different regions of the United States, many types of severe weather can occur. On the Atlantic coast, for example, hurricane season lasts from early June to late November, with the highest frequency of storms occurring between late August and September. They are capable of causing structural damage to a structure and sweeping away documents.
Mid-spring to early summer is tornado season in the Midwest, which can damage or destroy property as well as priceless data and information. The majority of the nation is plagued by blizzards and ice storms throughout the winter months. The accumulation of snow and ice during these storms can cause roofs to collapse.
If and when any of these natural disasters occur, any papers stored there are likely to be ruined by the elements. As weather forecasting grows more precise, you will likely have at least some warning of an approaching storm. This will allow you to carry any sensitive documents away from the office. Preparing a collection of backup papers in advance is another alternative.
According to the U.S. Fire Administration, as reported by FEMA, there were 85,400 non-residential fires in 2011 that produced damage of a little under $2.5 billion.
Even if the records survive the fire, there is a strong possibility that they will be destroyed by firefighters' efforts to extinguish the blaze, which might entail pouring water and chemicals into the blazing structure.
Some business owners take severe fire safety precautions, such as acquiring fireproof safes and cabinets, to secure their papers. However, if your company has a huge number of documents to keep, this may not be a practical option.
Seismic activity is prevalent around the nation, particularly along the coasts. Occasionally, the trembling may be so faint that it is barely perceptible. At times, the shaking may be strong enough to cause the collapse of structures.
Since earthquakes may occur without notice, there's a considerable risk you won't have time to safeguard or relocate crucial files. In regions of the nation where earthquakes are common, businesses routinely back up and store their records in a separate place or utilize cloud storage, where they cannot be lost or destroyed.
Preparedness for flooding may save your company.
Water may distort and destroy paper documents, promote the growth of hazardous mold, or cause them to completely disintegrate.
Electronic papers are less susceptible to water damage than paper documents, and it is far simpler to put an external hard drive in a waterproof container than to preserve an entire room packed with paper documents.
If you lack the money for document scanning, ensure that all of your company's essential papers are photocopied and maintained in a safe, secure area offsite.
It may seem strange to imagine that a little termite can ruin corporate data, yet a termite colony may inflict irreparable harm to vital information if left uncontrolled.
In addition, they do not target your files one by one. Instead, they form a colony and begin to consume at will. Termites usually don't represent much of a threat too often accessed data since you'll detect the damage immediately and be able to correct it. Nevertheless, boxes of paper files that are rarely accessed are an easy target for termites.
All businesses store important paper and electronic records at their office or primary location. It may be hard to duplicate these objects if they are ever lost.
There are several ways in which your company might lose important documents.
The first step in establishing a series of protections and rules to preserve your business and its precious documents in the event of a natural catastrophe is to identify possible concerns with how your organization secures its records.
2. Theft
With computers becoming smaller and lighter, and public Wi-Fi allowing us to work in cafes, on trains, and other public locations, technical improvements have made it simpler to work while on the move.
Unfortunately, this convenience increases the likelihood that gadgets may be stolen. If you're not looking or if you leave your laptop or cell phone unsecured, an opportunistic thief may steal it.
Approximately one laptop is stolen every 53 seconds, according to Gartner. It might happen to you. Therefore, never leave your laptop alone or in a location where it could be stolen. According to studies, 80% of the expenditures involved with theft are attributed to data breach fees and retrieving the stolen data. Any organization must be able to remotely delete a computer if a laptop holding sensitive information is taken. To protect your business, you must maintain reliable backups to guarantee that critical data is never irretrievably lost and is always recoverable.
3. Human Error
People's usage of data poses the greatest dangers to organizations. Employees are prone to destroying files or other material, which is particularly detrimental if the information is in hard copy or if there are no backups.
This issue is worsened when firms fail to develop information handling rules and processes. This risk may be mitigated by reminding staff to exercise caution and back up data whenever feasible.
Water (or other liquid) damage to electronic equipment can also cause data loss. When we work, many of us keep a glass of water or a cup of coffee on our desks, and it only takes one spill to harm a laptop's internal systems.
Laptops lack additional covers to protect them from water damage, which increases the likelihood of electrical components short-circuiting. Once this occurs, it is extremely difficult to retrieve the laptop and its stored data.
4. Computer Viruses
There are several types of viruses that may delete data from a hard disk. The most prominent is ransomware, whose prevalence has increased since the beginning of 2020.
Frequently, attacks start with an infected attachment in a phishing email. When the victim opens the file, the malicious application encrypts the victim's device's data and possibly spreads across the network. The victim then receives a ransom note indicating that the information will be deleted if no payment is made.
Experts warn organizations not to pay ransoms since doing so might lead to ongoing issues, such as repeated ransomware attacks, and propose instead recovering systems from backups.
This may result in the loss of any data that has not been backed up. However, you may face this issue even if you pay the ransom, as it is uncertain if the criminal will follow through on his word.
5. Power Failure
Certainly, a power outage may drastically disrupt commercial activities. Your hard drive could be rendered inaccessible if it is harmed by a sudden power failure that causes your computer to abruptly shut down. Consequently, to prevent data loss, it is recommended to install a generator or a backup battery to safeguard your system during a power outage.
Imagine that your hard drive is busy writing data to the disk when the power goes out and it abruptly shuts down in the middle of the operation. On a good day, you may lose only one file or a small portion of a file. Imagine that your computer loses power while your hard drive is writing to the file system, which is essential for the startup process. This file may have been corrupt, preventing you from restarting your machine. Not good.
When power outages, surges, and hard reboots occur frequently, the hard drive's lifespan might be shortened. Every time a computer restarts after a power outage, the read and write heads are swiftly returned to their former positions, producing minor defects on the disk. Over time, these flaws compound and increase the risk of a head crash, which kills the hard drive. Again, not good.
Surges of electricity also pose a threat to computer gear. Surge protectors are one method of protection against a power surge. However, not even a surge protector can protect your PC from lightning. Losing your computer may be distressing, but losing all of your data would be more distressing. A reliable backup would safeguard your data in the case of a power-related data loss.
6. Software Corruption
The failure or crash of software is another leading cause of data loss. Any data-requesting program is susceptible to crashes, resulting in data loss or corruption. Software failure can also occur in file editing software when updating several files, resulting in the deletion of files that failed to save or update. In the same way, data might be lost during backup.
Common backup issues include system failure to produce file copies and an inability to halt automated file erasure. Antivirus software can potentially erase data if it erroneously identifies it as malicious software. Errors can also occur during file format conversion, resulting in data damage and loss.
When Should You Use Data Recovery Software?
If you've inadvertently formatted your disk or erased items you didn't want to, shut down your PC prematurely, or contracted a particularly virulent virus, you may be able to recover your data using one of several data recovery software programs.
Some programs perform better than others with certain difficulties or recoverable software; they are not identical. Each software solution employs a unique data reconstruction algorithm, and no two programs will produce identical results. Perform research online before making a purchase.
Remember this key guideline if you try do-it-yourself data recovery. NEVER RESTORE INFORMATION TO THE SAME DRIVE. The recovered data will overwrite the hidden files that you are seeking to recover, significantly limiting your options if the initial recovery effort is unsuccessful.
Additionally, there are inherent hazards associated with operating on a hard disk that has not been professionally inspected and diagnosed. For instance, running a drive with a malfunctioning head may cause the drive to fail and become completely unrecoverable. The rule of thumb is straightforward: if your data is critical, valuable, or exclusive to the failed disk, it is best to resist the temptation and send it to us for a free examination of the damage.
The physical damage must be fixed by a data recovery professional. If your hard drive is physically destroyed, restarting the computer in an attempt to resolve the issue will only exacerbate the problem. "Logical damage" can occur if you inadvertently format a disk or if the file directory is corrupted. It can also occur owing to malware or data overwriting.
What are the Softwares Used in Data Recovery?
There is a multitude of free data recovery software options accessible on the Internet. Some items are gratis, while others provide free downloads of evaluation versions of the utilities. We have compiled a list of the five finest data recovery programs that can be downloaded and tested for free in 2022.
-
Disk Drill Data Recovery (Windows & Mac)
-
EaseUS Data Recovery Wizard (Windows & Mac)
-
Recuva (Windows)
-
TestDisk Data Recovery (Windows & Mac)
-
Minitool Power Data Recovery (Windows)
How to Prevent Data Loss?
Nobody enjoys hearing "I told you so," especially when attempting to recover from a catastrophic data loss. Here are some suggestions for avoiding hearing them:
-
Schedule regular "fire drills" to recover data from backups. They are essential and not a luxury. If you currently lack a drilling system or if it has fallen into disrepair, it is only reasonable to inform everyone concerned that "no-excuse" exercises are on the horizon. It may sound simple, but it may be difficult, as many things can go wrong along the sequence of steps required to execute a complete backup and restoration.
-
Keep computers in secure, dust-free, and dry environments. To prevent physical harm to the computers, low-traffic settings are ideal.
-
Back up data routinely. Verify the backups by retrieving the data from the cassette and re-entering it into the computers.
-
You need a backup generator or battery system. Even very low-level energy surges are capable of erasing the data on hard drives, which can be destroyed by large power surges. An uninterrupted power supply safeguards against lightning and electrical storms, allowing data to be stored or backed up during a blackout.
-
Protect your equipment against static electricity, which can cause data loss or component damage. The storage mediums of today are increasingly susceptible to extraneous static discharge.
-
Utilize virus-detection software and keep it updated. Viruses may not be as prevalent as the media portrays, but they do exist and may be fatal to data. Utilize virus-detection software and keep it updated.
-
Utilize the "undo" function. Numerous installation and diagnostic applications include undoing DVDs that can return computers to their initial configurations in the event of a malfunction. It is a best practice to utilize this function.
-
There are other software applications that can identify potential hard disk failures. Using them often can prevent complications.
-
The operators of computer systems are mere humans. Physical components can deteriorate over time. In every type of computing environment, it is prudent to maintain reliable backups.
Does the Next-Generation Firewall Prevent Data Loss?
Next-generation firewalls(NGFW) filter network traffic to safeguard a business from external cyber attacks that might cause data loss or unauthorized access to the credentials of a system, exposing the business to larger risks. Preserving the characteristics of stateful firewalls, such as packet filtering, VPN support, community monitoring, and IP mapping, provides improved malware detection and other threat detection capabilities.