Application Control: Types, How It Works, Benefits and Challenges.
The dynamics of security have shifted as a result of web-based applications. Previously, certain apps were linked to specific protocols and ports, making policy enforcement very simple at the host level. Nearly all traffic now uses HTTP (ports 80/443). Employees, contractors, partners, and service providers can access web applications over the firewall from anywhere, posing access control issues. Instant messaging, peer-to-peer file sharing, Webmail, social networking, and IP voice/video collaboration all circumvent security measures by altering communication ports and protocols, or tunneling within other regularly used services (for example, HTTP or HTTPS). To secure their assets from threats and manage bandwidth, organizations require control over the apps and traffic on their networks.
Application control is a security approach that prevents unauthorized applications from damaging data by blocking or restricting their execution. The control functions vary depending on the application's business purpose, but the fundamental goal is to assist maintain the privacy and security of data that is utilized by and sent between apps.
Completeness and validity checks, identity, authentication, authorization, input controls, and forensic controls are all examples of application control.
-
Application controls guarantee that records are processed correctly from start to finish.
-
Only legitimate data is input or processed thanks to application controls.
-
All users have identified uniquely and indisputably thanks to application controls.
-
Authentication for the application system is provided by application controls.
-
Only authorized business users have access to the application system, thanks to application restrictions.
-
Data integrity inputs into the application system from upstream sources are ensured by application controls.
-
Application controls guarantee that data based on inputs and outputs is scientifically and mathematically valid.
In this article we cover the following topics:
- How does Application Control Work?
- What are the Features and Examples of Application Control?
- What Are the Benefits of Application Control?
- What are the Types of Application Control?
- What is the Relationship of the Next Generation Firewall with Application Control?
- What Are The Key Differences Between General And Application Controls?
What is Application Control?��
Application control is a security strategy that inhibits unauthorized apps from compromising data by obstructing or limiting their execution. As a security measure, application control prevents or limits unauthorized apps from operating in ways that endanger data. The primary goal is to assist in ensuring the privacy and security of data utilized by and sent across apps, while the control functions differ depending on the particular application's business purpose.
Integrity checks, validation, identification, authorization, authentication, input management, and forensics are all covered by application controls.
Application controls guarantee appropriate coverage as well as the availability, confidentiality, and integrity of the application and the data that goes with it. Businesses and organizations significantly lower the risks and dangers related to application usage by implementing appropriate application controls, which stop programs from running if they endanger the network or sensitive data.
How does Application Control Work?
Application control technology works based on a basic concept: different types of network traffic flow are compared to predetermined condition models. As a result, these requests must adhere to particular specifications for the computers in the network to interact with one another. These standards allow application control to determine which traffic flow originates from which location in the system. Taking this into consideration, you may prioritize which apps to whitelist and blacklist, as well as which ones require more frequent monitoring.
At Layer 7, the application identification (App ID) classification engine and the application signature pattern-matching engine evaluate the payload's real content to identify apps. Until the application is recognized, App ID performs a deep packet inspection (DPI) of network traffic and every packet in the flow that travels through the application identification engine. To speed up future identification, application results such as IP addresses, hostnames, and port ranges are kept in the application system cache (ASC).
After identifying a traffic flow as belonging to a certain application, it can be categorized in a variety of ways:
-
Type: Teleconferencing systems, for example, can be categorized according to their function. This can assist in determining the traffic's priority.
-
Level of cybersecurity risk: Different apps have varying levels of cybersecurity risk. Due to the possibility of data exfiltration, protocols that convey data, such as email or FTP, may be categorized as high risk. Identifying traffic security threats allows a company to implement security measures based on risk assessments.
-
Resource consumption: Some apps consume significantly more resources than others. Videoconferencing programs, for example, which require a lot of high-speed network bandwidth to broadcast both audio and video, can use a lot of it. Identifying traffic from apps that consume a lot of resources might aid in network performance optimization.
-
Productivity implications: Social networking apps, for example, can have a beneficial or bad influence on employee productivity. For this reason, an organization may want to filter specific types of traffic on its networks.
What are the Features and Examples of Application Control?
There are seven key characteristics to consider when it comes to application control, three of them deal with user accounts and the remaining four with data processing. Identification, authentication, authorization, completeness and validity checks, input controls, and forensic controls are all examples of these controls. A brief description of each application control examples is given below:
- Identification: The correctness and uniqueness of user account credentials are ensured via identification.
- Authentication: All applications require authentication, which is comprised of verification system controls.
- Authorization: The authorization ensures that only authorized users have access to the company's application network.
- Completeness Checks: Checks for completeness that ensure traffic flow records are handled from beginning to end.
- Validity Checks: Application control technology performs validity checks to ensure that only legitimate data inputs are handled.
- Input Controls: The integrity of the data feeds provided into the system is ensured by input controls.
- Forensic Controls: Forensic controls, ensure that the data is correct mathematically and scientifically.
Why is Application Control Important in Cybersecurity?
With the rise of malware and zero-day threats, the threat environment has undergone a tremendous shift. Spyware, ransomware, and viruses are examples of malware that takes advantage of holes in applications. It steals private information and compromises systems. Zero-day attacks circumvent conventional security protections by focusing on undiscovered flaws. They are even more dangerous.
Application control is essential for protecting user privacy and data. Organizations may reduce the risk of data breaches and unauthorized access by limiting the use of applications to those who are trusted and approved. This is especially crucial in sectors that handle sensitive data, including government, healthcare, and finance, where strict data protection laws apply.
In conclusion, for an IT environment to remain safe and effective, application control is essential. Organizations may lower the risk of malware infections, illegal software installs, and possible security breaches by limiting which programs can be run. By stopping resource-intensive or non-business-critical apps from operating, it also aids in system performance optimization.
What are the Types of Application Control?
Types of application control are explained below.
-
Input Controls: Input controls are a form of application control that restricts the amount of data that can be entered into an application. This control restricts the addition of illegal inputs to the system. There are several types of input controls, and some need authorization for data entry before it can be stored in the system.
-
Output Controls: Output controls are another kind of application control that deals with the distribution of data across applications and ensuring that the proper and appropriate data is provided to the relevant recipient. Output controls keep track of what data is being transferred and whether it is correct and complete; they also keep track of who the data is being sent to and where it is going.
-
Integrity Controls: Integrity controls assist in ensuring that data is formatted consistently and can be readily validated as legitimate and proper.
-
Access Controls: Access controls limit the activities that users may do on a particular piece of data. This application control restricts the actions that users may do with data based on their access role. Certain users are only permitted to access data, while others are permitted to edit it. Others may even have the power to modify the data by adding new inputs and lines.
How to Implement Application Control in an Organization?
Application security measures can be implemented in a variety of ways, but typically, the following stages are involved.
-
Identifying which programs are allowed to use a resource or carry out a task.
-
Establishing guidelines to control application operations and stop illegal apps from operating.
-
Managing modifications to application security rules using a system.
-
Reviewing and revising the regulations and restrictions on a regular basis (at least once a year).
What Are the Benefits of Application Control?
Application control is a technique for identifying the traffic flows of different applications on a network. This makes it easier for businesses to develop and implement network routing and granular security rules based on the constraints set by the aforementioned traffic flows. It's especially important for safeguarding businesses that have a strong BYOD policy. Some of the notable benefits of application control can be listed as follows:
-
Verification and Access Control: Beyond application-specific restrictions, application control is a cybersecurity strategy that makes identity-based policies easier to apply. This means you may specify access criteria for certain individuals or user groups who operate with different resources within your firm. You will also be able to use the zero trust model as a result of this.
-
Application-Specific Policies: The key benefit of application control is that it allows you to impose application-specific security policies for your company. You may use these to allow, deny, or limit specific types of application traffic.
-
Malware Protection: Because IT application controls prohibit unapproved apps from running inside your company's IT environment, malware entering your network through an application would be challenging. Malware injection through an application is a technique used by cyber attackers to breach high-security networks.
-
Increased Network Visibility: Application control provides your company with a better understanding of the traffic that enters and exits your network. As a result, your security team will be able to track incoming and outgoing inquiries, either across the whole online perimeter or between particular endpoints.
-
Preventing Application Exploits: Exploits are another technique for a cyberattacker to get access to your network. Application exploits function as "backdoor" entry and are often found in third-party programs and out-of-date operating systems.
-
Optimized Resource Usage: You may optimize resource utilization in the corporate network by being able to differentiate between policies for certain apps. Prioritizing traffic from latency-sensitive applications above less vital apps like social media will guarantee that key infrastructure programs receive the best possible system performance.
-
Application Monitoring: With so many endpoint devices on a corporate network, it may be difficult to keep track of which programs are operating. IT application controls assist in the management of apps in your IT environment.
-
PAM Solution Integration: Another advantage of application control is that it may be used in combination with privileged access management (PAM), a form of cybersecurity technology that ensures the correct use of administrative permissions inside a network. PAM adheres to the principle of least privilege (POLP), which states that user accounts should have just the degree of access necessary to do everyday chores.

Figure 1. What Are the Benefits of Application Control?
Are There Specific Industries That Benefit Most from Application Control?
Yes, some industries like healthcare, automotive, and consumer products stand to gain the most from application management, as seen by the growing demand for such solutions across these sectors.
The global application control market is expected to develop at a compound annual growth rate (CAGR) of 13.78% from 2024 to 2031, reaching 21.42 billion. This expansion is a result of both the growing market prospects and the growing use of application control solutions.
Due to rising demand and technical improvements, the global application control market is expanding significantly across a range of applications. Technology, consumer products, industry, and healthcare are important uses. Application control solutions are used by every industry to boost productivity, boost performance, and satisfy changing customer demands. For instance, application control applications are essential to diagnosis and treatment in the healthcare industry, and they also help to automate and simplify operations in manufacturing. Application control is being used by the consumer goods industry to enhance the sustainability and quality of its products. The market is anticipated to increase significantly as these applications continue to spread, with businesses concentrating on innovation and customized solutions to seize new possibilities. This development trajectory positions the market for continued improvement in the upcoming years by demonstrating the adaptability and crucial function that application control plays in a variety of sectors.
What are the Challenges of Application Control?
Although application controls have numerous advantages, they provide a number of difficulties. Here are a few of application control difficulties.
-
Security and Usability in Balance: One of the main challenges is striking the correct balance between security and usability. Tight regulations can improve security by stopping illegal software. However, if genuine apps are prohibited, they may hinder productivity. Users must complete tasks without delays or disruptions. It is necessary to create and administer policies with consideration.
-
Keeping Whitelists and Blacklists Up to Date: The continuous administration and upgrading of blacklists and whitelists presents another major obstacle. To make room for new software, patches, and upgrades, whitelists-which list permitted applications- and blacklists-which list forbidden ones-, need to be updated on a regular basis. In order to guarantee that the lists are correct and current and reduce the possibility of illegitimate applications sliding through the gaps, this activity can be time-consuming and demands ongoing attention to detail.
-
Combining Additional Security Measures: Application control must be integrated with other security measures as part of a holistic strategy. It must integrate easily with intrusion detection systems, firewalls, and antivirus programs. Although difficult, ensuring system compatibility and communication is essential. A multi-layered defense that is more resistant to attacks is produced by proper integration.
Can Application Control Prevent All Types of Cyber Threats?
No, not all cyber threats can be prevented by the application control feature. Application control, sometimes referred to as application whitelisting, is a critical cybersecurity precaution that guarantees that only authorized applications may operate on your systems.
Only by preventing the use of dangerous or unauthorized software can application control lower the risk of malware infections, data breaches, and other cyber security risks. It can support the upkeep of a reliable and safe computing environment, safeguarding the integrity of your system and your private data.
Application control works especially well at thwarting internal threats, such as malware. It stops them from operating without permission.
It's not the end-all and be-all, though. Application control still has to be incorporated into a thorough cyber security plan. For instance, if an employee reads a dubious email and downloads the Trojan that is concealed in its attachment, application control is completely useless.
How Does Application Control Differ from Antivirus Software?
Although they both aim to protect against dangerous software, their methods of operation are essentially different. While application control stops harmful apps before they can run, antivirus software finds and eliminates malware that already exists. Application control adds an extra degree of security, but both are crucial parts of an all-encompassing cybersecurity plan.
The mainstay of cybersecurity is antivirus systems, sometimes called anti-malware software. They have been in use for decades and are made to identify, stop, and eliminate many kinds of harmful software, such as trojans, worms, viruses, and other malware.
Another proactive security technique that employs a different strategy is application control. It focuses on permitting only pre-approved or "whitelisted" programs to operate on a system, hence prohibiting all others, as opposed to detecting and blocking known dangers.
A comparison of antivirus systems and application control is outlined below.
- Effectiveness: While antivirus software is good at identifying and thwarting known threats, it may not be able to handle sophisticated or novel malware. Application control is a powerful barrier against zero-day attacks since it effectively stops unknown and unapproved apps from operating.
- Administrative Overhead: Antivirus software may produce false positives and has to be updated often. Application control lowers ongoing maintenance but requires upfront administrative work to define what is permitted.
- Resource Usage: While scanning in real time, antivirus software may use up system resources. Because application control only has to verify whitelisted apps, it usually uses fewer resources.
- Adaptability: To stay ahead of emerging dangers, antivirus software must constantly change. Although Application Control offers consistent protection, adding or removing apps from the whitelist may occasionally require upgrades.
What are the Best Practices for Managing Application Control?
We've put up a list of application control best practices that experts advocate.
-
Blacklisting ought to be done carefully: Depending on the time of day, applications should be blocked from running. In addition to preventing the abuse of business-critical files, an authorized operating schedule will help staff complete their jobs quickly.
Additionally, application control policies may be created for a certain department or user group, reducing security concerns based on the idea that only specific people need access to specific applications in order to do their jobs.
-
Group apps according to departments or functionality: One effective strategy to streamline application management within your company is to group apps together. You may use application groups to organize apps according to departments or roles within your company, in addition to resemblance and functionality. This guarantees that users only have access to the apps necessary for corporate operations and makes it simpler to map applications to certain users depending on their job requirements. Administrators may easily create policies for the application groups as a whole rather than managing individual apps by grouping comparable programs together (such as development tools, finance-focused software, or communication apps). Additionally, by lowering the possibility of unlawful program use, this strategy contributes to the upkeep of a safe and effective IT environment.
-
Whitelisting holds equal significance to blacklisting: Selecting which applications will be automatically allowed is just as critical as creating the list of barred apps. The technique is more effective against known and undiscovered dangers because of this dynamic approach that combines blacklisting and whitelisting, with whitelisting being crucial in ensuring that applications are allowed to operate in compliance with policies and admin-specified regulations.
-
The deployment must be executed effectively: Implementing an application control strategy should prioritize planning and analysis, as advised by the National Institute of Standards and Technology (NIST), necessitating a detailed plan. Potential risks will be lessened with a phased approach. Additionally, when it comes to deployment, the environment should be considered as well, as, for example, whitelisting is more effective on centrally managed servers that have a higher burden.
-
Audit the apps that are operating on your company network: One crucial requirement for application security is being able to see which programs are being utilized on the company network. This helps administrators make well-informed judgments about whether programs should be permitted or prohibited from accessing the network, in addition to guaranteeing seamless functioning. It is possible to ban the apps that reduce productivity.
-
Keep the software up-to-date: Security researchers are always finding new flaws in software and patching them. To keep dangerous outsiders out of your company, you must make sure that all of your software is patched on a regular basis.
What Tools Are Available for Application Control?
Application control solutions aid in establishing a stronger default-deny posture on endpoints, which prevents malware and other unfamiliar, possibly dangerous apps from running. The following are the top application control solutions.
-
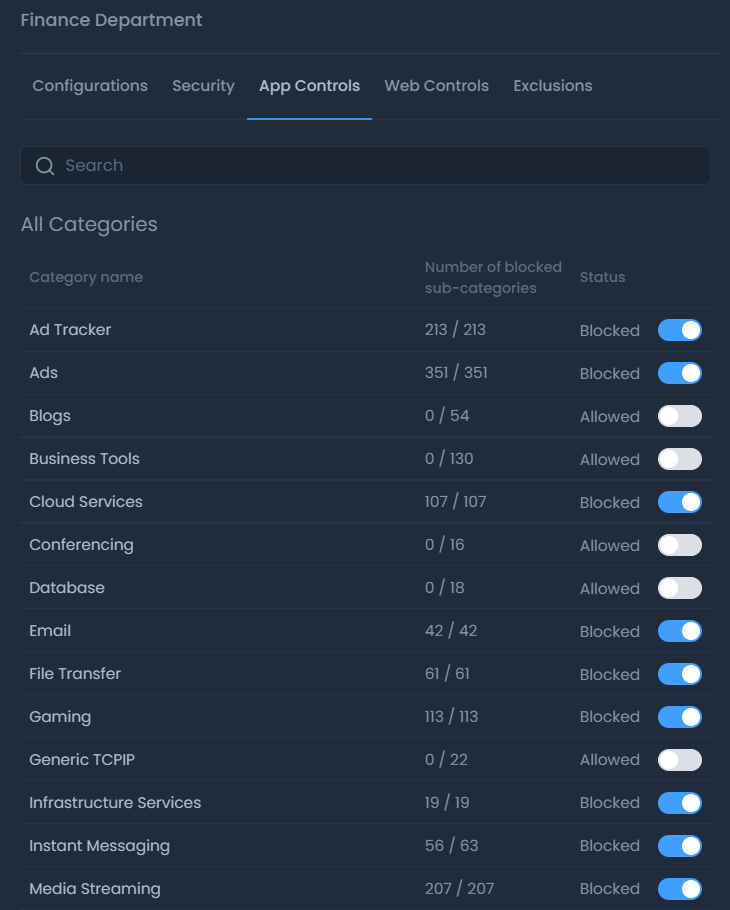
Zenarmor: Zenarmor is an appliance free and light-weight next-generation firewall solution. It can be instantly deployed onto any platform which has network access. Virtual or bare-metal. On-premise or Cloud. Any Cloud...
Zenarmor offers advanced threat detection, real-time monitoring, and customizable security policies. Its firewall solution enhances network security. Zenarmor offers a strong, enterprise-class content filtering engine that can identify and stop highly sophisticated threats and advanced malware, in contrast to simple internet traffic filtering firewalls.
To identify and filter out cyber threats and undesired or malicious traffic, real-time threat databases recognize thousands of communication protocols and applications. Some of the main features are visualization of network and connection details, including anomalies in real-time. The management of the Zenarmor firewall is simple. Any network can be utilized for deployment, and security reports can be received every day or every week. Zenarmor utilizes a sophisticated packet inspection core that can analyze network traffic in real time, even for encrypted communications. The platform offers robust reporting and visualization tools.
Zenarmor employs cutting-edge technology to detect and block threats as they occur. The product comes with a powerful content-filtering engine that surpasses basic internet traffic filtering methods. The solution integrates cloud-based threat intelligence. It comes with features including user-based filtering, application control, and web access restrictions based on a database of sites. Zenarmor provides a cloud-based management portal, Zenconsole, which lets you manage security policies from anywhere.
Zenarmor architecture doesn't require enterprise-class hardware, doesn't require any appliances, and provides easy installation on existing systems. The product can be installed on a virtual home lab system or on your previous personal computer. The product provides a free trial.
-
ThreatLocker Zero Trust Endpoint Protection Platform: By examining every executable, application, and process, ThreatLocker Zero Trust Endpoint Protection Platform creates a customized set of application control policies that may be built up to meet certain requirements.
Granular management over installed endpoints' apps and content is made possible by ThreatLocker. Ringfencing is one of the important capabilities that ThreatLocker offers. Once implemented on endpoints, RingfencingTM gives administrators control over apps. Administrators can restrict, for instance, the files a program can access, whether it can connect to the internet, and if it can communicate with other apps, if it can at all. By weaponizing trustworthy apps, this granular control lowers the risk of attackers. Administrators may establish rules for all endpoint file and media interactions, including USB devices, using the ThreatLocker Storage Control functionality.
The ThreatLocker Zero Trust Endpoint Protection Platform's Zero Trust design gives extensive control and visibility over network traffic through dynamic network access management. Its operation guarantees automated port availability regulation by allowing only authorized devices to access ports and preventing unauthorized devices from doing so. This technology significantly reduces the danger of malware and ransomware attacks by controlling the access of Internet of Things (IoT) and shadow IT devices to certain servers.
-
Akamai Guardicore Segmentation: Akami Technologies was established in 1998 with the goal of assisting clients in enhancing the dependability, security, and performance of their services and applications. Application control features, including granular segmentation capabilities, near-real-time and historical visibility for forensic investigation, and broad platform coverage for both old and new systems, are all included in their solution, Akami Guardcore Segmentation.
Additionally, the platform offers threat intelligence and breach detection, quick and easy policy building with templates for typical use cases, and customizable asset labeling that connects with orchestration systems and CMDB. .
-
Check Point Application Control: Businesses may detect, restrict, or ban the usage of particular programs or widgets by implementing granular policies across individuals or groups using Check Point Application Control.
SSL/TLS encrypted traffic that travels through the gateway is scanned and secured by the solution. The AppWiki Application Classification Library is used to automatically detect and update new data on the Application Control database. Regardless of the port, protocol, or evasive methods used to navigate the network, Check Point Application Control allows application security policies to regulate the operation of thousands of programs.
-
Heimdal: In order to simplify control over program executions, Heimdal is an application management solution for whitelisting and disabling active apps. The solution employs a default rule to expedite application acceptance or rejection and may control application access and execution through vendor, file path, published, and certificate. In order to efficiently manage user sessions, this offers several levels of granular configurability and can function in both active and passive modes. Heimdal offers a highly customized and secure administrator experience by fusing access governance with app management. The platform simplifies the process of approving or rejecting access and offers audit reporting tools.
-
Ivanti Application Control: Ivanti Application Control enables users to simply define restrictions on access to particular consoles, programs, and server commands while managing privileges without affecting productivity.
You can automatically manage user rights and policies using Ivanti Application Control. Simplified allow and deny lists, context-aware user access policy development, and execution monitoring are among the features made possible by this granular approach.
Ivanti platform is a feature-rich, all-inclusive application control solution that is capable of managing applications for big businesses with intricate settings.
-
ManageEngine Application Control Plus: Their virtual checkpoint for all programs is ManageEngine Application Control Plus, which has an integrated privilege management tool for further protection.
With capabilities like application allowlisting and application blocklisting, this enterprise-grade application control solution gives you total control over any program on your network. Users may quickly remove overly spread local admin privileges, assign needs-based application-specific access, handle temporary application and privileged access, and flexibly govern application policies. After a predetermined amount of time, this access may be automatically terminated.
ManageEngine's adaptable solutions, which are appropriate for businesses of all sizes, assist clients worldwide in managing IT operations. They handle the management and regulation of applications in a thorough yet manageable manner.
-
Trellix Application Control: Software from Trellix (formerly FireEye and McAfee Enterprises) is used to identify and stop cyberattacks. Users may make sure that only trustworthy apps are allowed to operate on their PCs, servers, and devices by using Trellix Application and Change Control. Unauthorized programs can be intelligently whitelisted and their execution blocked by the platform. Managing enhanced execution control and an observation mode that enables you to find policies for dynamic desktop environments without requiring a whitelisting lockout are two more important features.
Trellix Global Threat Intelligence, a proprietary system that uses millions of sensors worldwide to track messages, files, and senders' reputations in real time, is another source of intelligence that improves this service.
-
VMware Carbon Black App Control: VMware Carbon Black App Control is an application control solution that integrates memory/tamper protection, file integrity monitoring, application control, and full-featured device control into a single agent.
This solution uses a "default deny" strategy that automates the acceptance of trustworthy software in an effort to reduce downtime and the attack surface. The platform offers capabilities including memory protection, open APIs, reputation services, content-based inspection, file integrity monitoring and control, application control, and device management.
When needed, this solution may lock and restrict access to vital systems. VMware's technology blocks or permits apps without interfering with normal operations by utilizing low-touch application control and excellent performance. This promotes adherence to regulations. VMware is a reliable and scalable application control system.
-
Zscaler Posture Management: Their cloud native application protection tool, Posture Control, aids in securing cloud native apps from development to execution. Cloud security posture management, cloud infrastructure entitlement management, code security, data security, advanced threat and risk correlation, intelligent threat prevention, and vulnerability scanning are all included in the platform. In addition to lowering user costs and complexity, this system may be integrated throughout your company to provide 360-degree visibility throughout your whole multi-load footprint.
For quick onboarding, Zscaler Posture Control makes it simple to link your cloud accounts. The technology then facilitates user monitoring, which helps you maintain ongoing compliance and enhances SOC efficiency by providing actionable insight.
What is the Relationship of the Next Generation Firewall with Application Control?
Traditional firewalls were designed for a period before people utilized many applications on various ports at the same time, making it impossible for this technology to stay up. WAF is a good option, but because it focuses on the application layer, it doesn't necessarily cover all of the bases. Next-generation firewalls (NGFWs) monitor traffic from all application levels, determining what is safe to broadcast and receive using AI and machine learning. This component is fully automated, requiring no daily oversight from IT personnel, and is capable of determining what is being delivered or received. Simply said, you have the option of allowing people to utilize Facebook. You may also ban the Facebook app or choose which individuals are permitted to use it.
Traveling by plane is a nice analogy. Data was simply verified to determine whether it had a ticket and if its credentials were in order, it may board the plane in the first few iterations of the firewall.
Then application traffic increased to the point that first-generation firewalls couldn't keep up. This is because thieves were able to place malware into application traffic, where it was invisible to the firewall ticket taker.
As a result, next-generation firewalls were created with additional features such as Application Control and Intrusion Prevention System (IPS) to identify known and zero-day threats. By constantly monitoring network traffic, this new gadget might peek into programs and detect and stop malware. Consider it akin to incorporating x-ray equipment into your aircraft boarding process. Even though you had a ticket, if you had something harmful in your luggage, you were denied entry.
What Are the Differences Between URL Filtering and Application Control?
The application control function implements refined traffic control by utilizing application identification technology to identify various applications in traffic. There are also web applications among the applications. The Facebook application, for instance, is hosted at www.facebook.com.
Application control identifies and regulates web page access traffic for web applications, whereas URL filtering regulates web page URLs. In other words, application control is delegated to a specific application program, and a given application program may be mirrored across multiple web pages. URL filtering extends to the access behavior of individual web pages.
Application control is more suitable for controlling applications at the granular level. You are more acquainted with the names of applications associated with websites like Facebook, including the Facebook browser, Facebook videos, and Facebook activities. Collecting URLs that correspond to applications may be challenging due to the possibility that a single application is associated with multiple URLs. In this situation, application control is the more practical option. Configuring application identifiers, such as Facebook videos and Facebook activities, is all that is required.
URL filtering is a more effective method for regulating user access to a specific category of websites or a collection of URLs hosted on the same domain. Using URL filtering, for instance, to restrict user access to the Facebook social networking site while preventing access to other social networking sites, is more practical. Application control requires that all applications corresponding to the domains be specified.
Consequently, URL filtering and application control each have distinct application scenarios and complement one another.
What Are The Key Differences Between General And Application Controls?
There are a number of critical distinctions between general and application controls. These controls are crucial for businesses that rely on information technology systems. Both of these restrictions are critical. However, it is vital to comprehend their distinctions. The following are some of the ways in which general and application controls differ.
-
Definition: All computerized systems or applications are subject to general controls. They are a collection of software, hardware, and manual methods that contribute to the overall control environment's form. By contrast, application controls are unique to each computerized program. For instance, payroll systems have different application restrictions than sales systems.
-
Scope: General controls have an impact on how an organization's whole information technology system operates. As a result, its use is more versatile. By contrast, application controls are exclusive to a single program. As a result, application controls have a more defined and limited reach. That is not to say, however, that these regulations are ineffective.
By contrast, application controls are more granular. As discussed before, application controls are classified into three distinct categories. These comprise controls for input, processing, and output. Each of these categories may have further subcategories, all of which are subject to application constraints.
-
Types: General controls, as previously stated, comprise software, hardware, and manual techniques. As a result, these controls may include software, computer operations, data security, administrative, and physical hardware controls, among others.
-
Example: As previously stated, general controls may include all controls over information technology systems. Controls over data center and network operations, for example, are an example of broad controls. These rules are applicable to any kind of information that communicates over networks. Antivirus or firewall protection is a common kind of generic control that is applicable to all information technology systems.
Application controls, on the other hand, are application-specific. Thus, input controls are an excellent illustration of application controls. These controls enable the validation of any data that enters the systems. In this manner, businesses can verify that only accurate data enters their systems. Application control ensures that each employee is paid once the payroll program is used.
Does Application Control Enhance Compliance?
Yes, application control improves compliance. For instance, adherence to industry standards and data protection regulations is crucial in highly regulated sectors such as healthcare and finance. By limiting the usage of non-compliant apps and implementing security regulations, application control assists companies in meeting these criteria. Organizations may prevent significant penalties, legal ramifications, and harm to their brand by keeping their software environment safe and compliant.
