What is Bring Your Own Device (BYOD)?
Although the idea of BYOD was originally announced in 2009, it wasn't until 2010 that it gained widespread acceptance. As personal gadgets proliferated in the office, pressure mounted on chief information officers. The first iPad was released at the same time as Android began to gain popularity. As a result, more people were using their cellphones and tablets at work, and the IT staff kept allowing employees to use their own devices without providing any assistance.
When Intel saw that a growing number of its workers were bringing their own devices (such as tablets, smartphones, and laptops) to work and connecting them to the company network, the term "BYOD" was first used.
Of course, bringing personal gadgets to work has advantages and disadvantages. The biggest disadvantage is that, although allowing employees to work from any location and on any device has advantages for the company, the dangers might result in data breaches and sensitive information falling into the wrong hands.
Some companies began to prevent personal devices from accessing their networks and mail servers in retaliation. The first mobile device-related APIs were made available with the introduction of iOS 4 in 2010. Businesses and IT both started realizing they could not ignore BYOD.
As a result, the first BYOD programs were created in 2011 and are officially used in the workplace. As business leaders began to feel more at ease using touch screen keyboards, the enterprise mobility market started to quickly change.
The first significant worries over data leaking and security weren't felt until 2012, even though it was still necessary to concentrate on protecting the devices. Concern over privacy among people was starting to rise. Businesses began concentrating on effectively explaining BYOD rules to those worried users while also attempting to comprehend the ramifications for both security and privacy. The need for Mobile Device Management (MDM) solutions rose as a result.
BYOD altered how businesses offered access to computer networks. In the past, the IT division would create closed networks that could only be accessed by computers owned by the business. However, employees were allowed to connect their own cell phones, tablets, and PCs to more open networks with bring-your-own-device policies.
The BYOD movement may be attributed to the explosive growth of smartphones and tablets, as well as the decreased price of laptop computers. People who previously had to rely on their employers to provide them with hardware for work can now readily buy personal gadgets that are capable of doing the same thing.
Despite being new in the context of technology, we can anticipate that BYOD will spread over the majority of sectors. Security will advance with technology.
In this article we will discuss what BYOD is, its importance, how it works, the advantages and disadvantages of its use in schools, the security risks it contains, the approaches that can be an alternative to BYOD, the necessity of the BYOD policy and how it can be implemented, how a BYOD strategy should be applied in schools, and lastly, the relationship of Mobile Device Management with BYOD.
What is BYOD and Why is It Important?
BYOD, or bring your own device, refers to the idea that employees should bring their own cellphones and laptops to work. The employees utilize their own gadgets in addition to or in place of any provided by the employer. Bring your own technology, or BYOT, is another name for this idea.
As more people invest in their own high-end mobile and computing devices for personal use, more enterprises are moving toward BYOD. This strategy also enables workers to work with the operating system they are most familiar with, as more individuals develop loyalty to either Windows or Mac, as well as iOS or Android devices.
BYOD can occasionally take place covertly. Or, if a company encourages the use of personal mobile devices, it may become a part of corporate policy. It's likely that the business will provide employees with a stipend, so they may buy their own devices rather than provide them with corporate equipment.
For instance, if a worker interacts with clients, the company could decide to include a stipend in each paycheck so that the worker can have a different mobile phone plan or add a second line to their account.
Employees want to access business data on their own devices more and more, while IT teams struggle to keep up with new technological advancements.
It's a component of the burgeoning Bring Your Own Device (BYOD) movement, which also includes the Bring Your Own Phone (BYOP), Bring Your Own PC (BYOPC), and Bring Your Own Technology (BYOT) projects. All of them have developed as a result of the so-called "consumerization of IT" to empower workforces.
BYOD promotes workers of businesses to work on the device of their choice, accessing corporate email, seeing text documents, and more as part of this consumerization. This brings cost reduction and increased productivity.
However, BYOD also has a negative side. It can endanger IT security and put users at risk if not thoroughly understood and regulated.
Of course, for BYOD to function, there needs to be a framework for data consumption and security. Here is where a Bring Your Own Device (BYOD) policy is put into action. To allow access to the device, IT departments must impose constraints like passwords, pins, or biometric settings. These gadgets should only be usable by authorized users. Information should be protected through data encryption. To lower the risk of virus exposure or data breaches, it may occasionally be necessary to demand that only critical apps be installed on employee-owned devices. Additionally, policies must be in place for when workers leave the organization to guarantee that all corporate access and information is safely stored.
How Does BYOD Work?
There are many BYOD functioning options. Since data loss might occur as a result of unprotected devices and weak passwords, the business should first set security policies for each device. The BYOD guidelines should specify:
-
What are the minimum security measures, such as data encryption and strong passwords?
-
What kinds of business data can be kept on local devices? (if any)
-
Whether or not timeout restrictions and auto-lock functions will be implemented
-
Which mobile data management (MDM) or mobile device security software, if any, is required to be installed on BYOD devices?
-
Whether the company is permitted to remotely erase the device of any business data in the event that it is lost, if an employee is fired, or if a policy violation is discovered.
Depending on the type of company, different levels of security are needed for different businesses. For instance, a tiny start-up web design firm needs less protection than a bank or healthcare organization. Organizations should develop acceptable use standards to specify how BYOD devices may be used while conducting business after security measures have been established. Insecure websites and programs won't be able to access malware or viruses as a result. These contracts should include
-
Applications that are allowed for workers to use on their own devices, with a clear distinction between those that are and those that are not.
-
Certain websites are blocked while using business resources, a corporate network, or a VPN.
-
Which user devices may access company apps and data, such as email, calendar, messaging, contacts, etc.
-
Storing and transmitting illegal content, or using personal devices for any work-related outside business operations
BYOD MDM software, which enables monitoring, controlling, and configuring BYOD and employee-owned devices from a single central dashboard, should be used to enforce policies. The typical MDM capabilities for BYOD include
-
Automatic malware checks on BYOD devices, including removing malicious software from the corporate network
-
Updating devices with anti-malware software and guaranteeing its installation
-
Remote patch and update installation for operating systems and software
-
Enforcement of security policies
-
Automatic recurring or on-demand data and application backup for businesses
-
Remotely wiping corrupted, stolen, or lost devices
Once BYOD rules have been defined, they must be made known to the workforce and supported by adequate training to ensure easy and widespread adoption. The concern of the company "spying" on employees may be reduced and employees' comfort level with rules and MDM software can be increased by providing recruits with a training booklet that explains the policies and why they were adopted. Every BYOD employee should sign a statement acknowledging that they have read and comprehended these guidelines to shield the company from any liability resulting from improper or unlawful usage of their devices.
Finally, no matter the reason for an employee's leaving, BYOD strategies should include an exit strategy. A BYOD leaves checklist that includes deactivating corporate email accounts, remotely erasing employer data from devices, completely deleting company-issued devices, and updating any shared passwords for company accounts should be included in the HR and network directory exit strategy.
BYOD policy specifies whether employees who check their email or take business calls after work hours are eligible for overtime pay as well as any company-provided subsidies for BYOD data plans or home internet access.
What are the Advantages of BYOD?
Like practically anything else, BYOD has advantages and disadvantages. Starting with benefits, BYOD reduces the cost of delivering education because schools don't have to invest in their own technical infrastructure. Additionally, it guarantees that kids are well organized. You may even visit a special classroom where kids and teachers switch places if you'd like. However, the BYOD strategy has the following additional benefits:
-
Financial Savings: Companies and schools save money with BYOD since they do not have to purchase devices for each employee or student. BYOD may save costs in the hardware, telecoms, and support and training categories. It also reduces the cost of maintenance and upgrades. According to research conducted by Cisco's Internet Business Solutions Group, businesses may save around $3,150 per employee annually via BYOD. This number is based on the cost of devices, data plans, and $1,518 per employee per year in time savings.
-
Familiarity: The ease of utilizing one's own mobile device is perhaps the most significant benefit that BYOD offers. Implementing a BYOD policy reduces training time since staff are already acquainted with their own devices and know how to maximize their performance. This will result in an improvement in efficiency and a decrease in the time required to accomplish activities, which will have a favorable effect on production.
-
Modern Technology: People may not frequently update company-owned gadgets. They may even opt to disregard security upgrades, putting your private data at risk. However, they are more likely to keep their own computers and other devices updated and install the most recently available updates.
In addition, it may not be feasible for a firm to continue acquiring new devices for all personnel in order to stay up with the most recent computer and mobile technologies. However, staff may often replace their personal gadgets when newer ones become available. When people utilize these devices for business, they will have quicker, more powerful, and more contemporary gadgets that can operate without a significant number of hiccups.
-
Flexibility: By enabling workers to use their own devices, they are able to access work-related data regardless of their location. A BYOD policy also provides the business with additional freedom, which is a crucial aspect of employee happiness and positive motivation. Flexibility is one of the primary motivators for employee satisfaction, and it may also enhance employee loyalty, morale, and engagement.
-
Productivity: According to research conducted by Forbes, 49% of workers claim to be more productive while using their own devices. In general, employees avoid communicating on devices with which they are uncomfortable. To ensure that vital information reaches your workers via the proper routes, it is preferable to allow them to use a gadget with which they are comfortable.
What are the Disadvantages of BYOD?
Although it has many wonderful advantages, BYOD also has drawbacks. |The main disadvantages of BYOD are as follows:
-
Security: A firm might mandate that all staff gadgets registered with the company be continually monitored. It may also need the use of backup software, antivirus software, or certain password protection rules. It is more challenging to administer the security of personal devices. Even if just during business hours, imposing restrictions on an employee-owned device seems like an invasion of privacy. Businesses implementing a BYOD program must accept that they will lose control over the proper use of staff devices.
-
Data Retrieval: When an employee quits a firm, it may be important to erase the company's sensitive information from his or her device in order to prevent the information from being misused. This might be hard since it could be seen as an invasion of the employee's privacy, and there is a legal need to safeguard employee personal information.
-
Application Difficulties: A business may use certain software to complete specific tasks. In certain instances, workers bringing their own devices may encounter installation or use difficulties with this program. Their hardware may not be compatible with the software.
-
Legal Issues: Legal, privacy, and safety issues may emerge after the implementation of a BYOD system. Employees, particularly new recruits, may not completely comprehend the proper procedures to follow while using personal devices for work. Therefore, you should implement a comprehensive BYOD policy. Certain problems, including data retention, sharing, access, and deletion, must be addressed explicitly in the policy. You should also explain the consequences of accessing corporate data outside of business hours or misusing this information.
-
Inconsistency: Some employees may still be utilizing laptops or mobile devices from 2010, while others use modern technologies. Although corporations save money when they embrace a BYOD strategy, they incur additional end-user support expenses. It may be tough to assist them when they encounter certain obstacles.
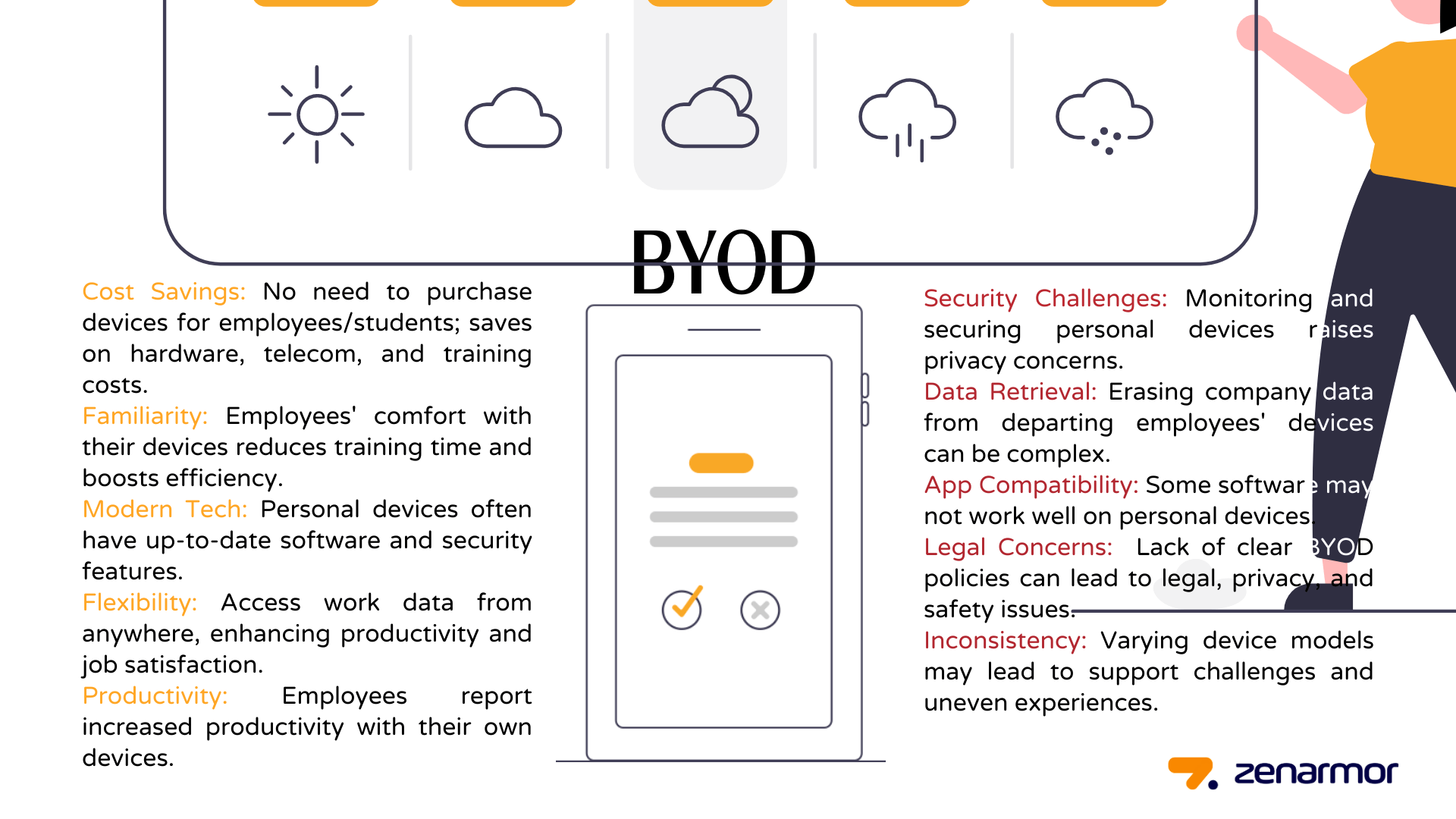
Figure 1. Advantages & Disadvantages of BYOD
What are the Security Risks of BYOD?
BYOD decisions are made in many businesses for a variety of reasons unrelated to security. You're undoubtedly worried about the security dangers if you're in charge of a program that permits or is thinking about allowing workers to use personal devices for work. The primary security risks of BYOD implementation are explained below:
-
Data Breach: Data leakage is a concern when employees use their own devices to access business email or secure payroll information, regardless of the situation. When devices are lost, stolen, or have malware installed on them, data might be lost or exposed. Although cloud computing has significantly reduced the amount of data loss caused by damaged devices, backups and security measures are essential for a successful BYOD program. Data loss prevention techniques include:
- Mobile Device Management: An MDM application can allow IT to remotely "wash" a device in the event of loss or theft to guarantee that critical data is not revealed.
- Smarter Data Provisioning: The best strategy to reduce vulnerability is to just allow the bare minimum access. The best provisioning model for security is role-based.
- Using a VPN and/or App Segregation: Separation and VPNs can provide walls between personal and professional material on a personal device, preventing critical data from being disclosed over dubious public wifi hotspots.
- File Integrity Monitoring (FIM): Software that runs at the kernel level and is agent-based may alert IT the instant malware enters a device, allowing you to take action before it affects your network.
-
Sketchy Apps: Not all personal applications are what they seem to be or should be on the mobile devices of your end consumers. You might recall the Pokemon Go mania from July and the several phony and harmful applications that were available. In an attempt to appeal to lovers of the game, TechCrunch claims that some of the verified malicious applications had names like "Pokemon Go Ultimate," "Guide & Cheats for Pokemon GO", and "Install Pokemongo".
Malicious applications occasionally have the ability to control the user's mobile device. This may lead to monitoring, unforeseen data or call costs, or the loss of personal or professional information. Emphasis should be placed on the value of just downloading content from app stores throughout knowledge-based training. Malicious mirrors or individual programs are frequently distributed via websites.
-
Lack of Management: There are dangers related to a loss of control with any mobile device, whether owned by an employee or a firm. It might be challenging to regulate if an endpoint leaves your business's premises and is utilized on dubious public wireless networks or if it is lost and stolen.
IT professionals must concentrate on a combination of device security, layered protection, and intelligent provisioning in order to safeguard mobile and laptop endpoints from exposure. The following technologies are used for the management of BYOD:
- Mobile Device Management (MDM): MDM enables workers to remotely manage the privacy and security settings on a worker's device. When used in conjunction with file integrity monitoring, IT professionals can set up the ideal amount of control.
- Business App Stores: The hazards associated with "shadow IT", or staff utilizing applications without authorization or your VPN, can be reduced by giving workers simple access to the appropriate apps permitted for business usage.
- Single Sign-On: Protecting endpoints with a password-protected lock screen is probably insufficient. IT professionals may provide smart user authentication without interfering with productivity by separating and safeguarding your mobile apps with a single sign-on (SSO) requirement.
- Infected Devices: The great majority of smartphone owners who have spyware on their devices are unaware of it. What's worse is that excessive exposure to mobile material, or "app fatigue", might make consumers indifferent to mobile security. When downloading new content, they might not read the terms of service for new programs or exercise caution before allowing excessive rights. Some of the most virulent types of malware target obsolete mobile operating systems, making them a significant risk factor. IT professionals should make sure that mobile OSs are kept up to date with any BYOD scheme. It's essential to employ file integrity monitoring to instantly detect and respond to device infection since even modern operating systems have vulnerabilities.
-
Poor Policies: Without strong security measures in place, it might be possible to try a BYOD program, but it's definitely hazardous. Effective policy is important to prevent penalties if your firm must adhere to PCI DSS, HIPAA, or any other regulatory standards.
IT professionals should take care of each of the following with a combination of written policy and policy-based administration for a BYOD program:
- Passwords, lock screens, and single sign-on
- Network connectivity
- Required use of a VPN
- Real-time updates and patches
- Location tracking
- Mobile device management
- Mixing personal and professional use: BYOD makes it inevitable to blend personal and professional use. You have no influence over whether or not your employees choose to shop on hacked websites or lose gadgets. Despite your best efforts to educate your staff on security best practices, there is no way to ensure that they won't lend their device to a friend or utilize public wireless networks to store data.
When employees don't adhere to recommended practices, security teams should be prepared to control that. The most effective strategies for handling bad employee conduct probably include:
- Application segregation: prevents unintentional access to work data on the device by putting up a solid barrier between private and public use.
- Use of a VPN: Even if employees are attempting to access a coffee shop's wireless network, a VPN can shield conversations from being intercepted.
- File integrity monitoring: IT professionals may get information about harmful modifications to crucial system files or security, enabling them to take fast action.
- Devices are difficult to control: What happens if a worker quits or misplaces their mobile device? The absence of device control is a primary source of security anxiety in many BYOD operations. Employees aren't always careful, and if they have too much access, displeased personnel can cause a lot of harm. Smarter access governance and mobile device management are crucial. This policy should enable you to swiftly remove access to sensitive information in the event that an employee is fired or starts behaving oddly before it is released.
Security for bringing your own devices is complicated.
Yes, it is considerably simpler to maintain control over employee-owned mobile devices, particularly if they all have the same type and operating system. With the appropriate security assessment and compromise detection technologies, BYOD security is feasible.
Security teams require tools for evaluating device integrity in addition to standard technical practices like using a VPN, SSO, and MDM, particularly when additional employee-owned devices are added to your company's network. Although using a jailbroken cell phone for business can render built-in security measures completely useless, mobile devices do carry certain inherent hazards.
What are the BYOD Alternatives?
Globally, businesses are searching for a way to guarantee that their workers are using safe gadgets without enforcing a Bring Your Own Device (BYOD) strategy. While some firms may benefit from these rules, many require BYOD alternatives for a variety of reasons.
Years ago, BYOD swept the industry, gaining traction immediately after its introduction. In light of the many advantages, including increased productivity and cost savings, 81% of businesses already provide or intend to offer a BYOD policy, according to Syntonic research on BYOD Usage in the Enterprise. In addition, 68% of workers who use their own devices use their phones for work-related activities for at least 4 hours a week away from the office. In addition, their employer saves, according to appstechnews.com, roughly $1,300 annually. Even though BYOD has many positive aspects, there are also disadvantages, such as an increase in security risks.
According to Syntonic, 75% of respondents expressed reservations about BYOD. If you fulfill that description, the following alternatives could work for your company:
-
Corporate Owned, Personally Enabled/COPE: Your organization could benefit more from a corporate-owned, personally enabled (COPE) mobile policy than BYOD. An organization is permitted to possess the devices under this sort of regulation, but employees are still permitted to make and receive personal calls on company time. The device and operating system sent to employees have been pre-approved, ensuring that they will work with the company's specialized Mobile Device Management (MDM) or Enterprise Mobility Management (EMM) solution.
A COPE policy also grants a business corporate data ownership, enabling it to manage and destroy sensitive data as needed. Although COPE is more expensive than a BYOD strategy, organizations might get carrier savings. Additionally, bear in mind that only a small number of hardware and operating systems frequently permit
-
Direct-to-carrier Stipends: Direct-to-carrier stipends are an additional choice to think about; with this option, employees are responsible for purchasing their own equipment and carrier subscriptions. The majority of the burden is removed from the business by this sort of policy, but employees still receive a monthly credit. The credit's value is determined by the employee's position and often covers only a fraction of the phone bill.
With this choice, businesses can avoid paying some taxes and levies since they can divide the use of personal and corporate data. Given that a vast array of devices and operating systems have access to the firm's network, support from within the organization and threat management is incredibly challenging to manage.
-
Choose Your Own Device: BYOD and COPE are combined into Choose Your Own Device, or CYOD. Even if they are paying for it, employees can choose from a list of pre-approved devices and operating systems under a CYOD policy. Given that devices must be pre-approved, this type of policy ensures interoperability with an organization's MDM or EMM system. This improves security and lessens the anxiety that a BYOD policy causes. However, problems can still arise when erasing corporate data. While CYOD can resolve some support concerns, the lack of separation between personal and corporate data puts a company at risk.
What is a BYOD Policy?
You've made the decision to allow BYOD in your company, but what does this actually mean? BYOD, which stands for "Bring Your Own Device," refers to the practice of employees using their own mobile devices to connect to your network, use your corporate apps, and access client data while at work.
BYOD is undoubtedly beneficial for productivity. It enables your employees to do more using a device they are accustomed to. But it's also dangerous. To prevent a new device from being utilized as an entry point for unauthorized access, it is important to protect any possible vulnerabilities it may introduce into your network environment.
It is essential to have a policy in place that explains the organization's approach to BYOD in detail if you want BYOD to successfully strike a balance between your employees' desire for productivity and your organization's need for cyber security. That's accurate. You must have a BYOD policy in place for the good of everyone.
Creating a BYOD policy is the first step in establishing security for external devices, so it will be important to determine the BYOD goals for your company. This policy must cover issues including the BYOD program's objectives, who are eligible to use their own devices, whose devices will be supported, and what access levels are given to employees while using their own devices. And that's only the start.
Your BYOD policy must also consider the following:
-
Who will cover the cost of the necessary equipment and data usage?
-
Which laws, rules, or other requirements have to be followed when utilizing external devices?
-
What steps will be taken to secure devices before they may be utilized with corporate systems, such as setup, software installation, and similar procedures?
-
Where will BYOD device data be kept? Will there need to be a contract that employees sign to permit them to bring their own devices if they so choose? (Locally, in the cloud - these are important considerations, given PoPI's demand that personal information be locally kept and hosted)
-
What happens if a worker disregards the provisions of your BYOD policy?
-
What level of privacy will be provided to employees who use their own devices at work?
-
For consumers who bring their own devices, what support (software upgrades, troubleshooting, maintenance) will your company offer for consumers who bring their own devices?
-
What cyber security measures must you take if a device has been compromised?
-
What security measures will be implemented on equipment before it is retired, sold, or discarded?
-
What happens to that employee's access to your company's apps, data, and systems once they leave?
Maintaining BYOD security once a policy has been established depends on how well your business can train its staff on BYOD best practices. Effective device management and support must be put in place, and you must be prepared to enforce your BYOD regulations. It's critical to make sure that the development of a BYOD program is a collaborative effort between your employees, IT and security teams, and management since employees who are not taught about BYOD security will only raise BYOD risks for your business. BYOD must be user-friendly and not merely cause problems for some people.
How to Implement the BYOD Policy?
Your organization needs a solid BYOD strategy to solve management and security issues. The following list of recommended practices will help you create a BYOD policy that works.
-
Put your policies in writing and formalize them: To ensure that workers are aware of when and how they should use their personal devices for work, policies must be set in writing. The following items must be present in a documented BYOD policy:
-
A list of the hardware, software, and operating systems that your BYOD program has authorized
-
Acceptable use guidelines outline what users of business networks, apps, and data may do with their own devices
-
Minimum standards for personal device security, such as setting up anti-malware software and downloading the most recent security patches
-
Reporting protocols for lost, stolen, or hacked devices
-
Assurance that your business has the authority to delete data from lost or stolen devices
-
A description of the process for replacing damaged equipment or receiving compensation when an employee loses or misplaces a personal device because of work-related issues
-
Penalties for violating policies (e.g., disciplinary action and additional training)
-
If the employee agrees to the BYOD regulations, they must sign a form.
-
Encourage a culture of security: To form responsible habits when using personal devices for work, employees must regularly undergo security training. The following subjects should be included in your security training program:
-
Basic device security: Teach staff members should install anti-malware software and upgrade their operating systems on a regular basis.
-
Physical protection: Employee gadgets being lost or stolen is the main danger of BYOD. Because of this, you should instruct staff members to always keep an eye on their devices and enable screen locks that are secured by a passcode or fingerprint scan. Additionally, staff members shouldn't use unidentified USB drives because they can be infected with malware.
-
Awareness of scams: With every unsolicited email, website, and a link they come across online, employees must use care. Cybercriminals frequently pose as reputable businesses and send phony emails to their targets to coerce them into revealing critical information or installing malware. Using software like KnowBe4, you can run phishing simulations to train staff members on how to spot and avoid phony emails.
-
Use of passwords: The significance of password best practices must be emphasized throughout security training sessions. Setting strong passwords with a minimum of 12 characters is required for this. Encourage your staff to utilize password managers like Dashlane or LastPass if they have trouble remembering complicated passwords for several accounts.
-
Access to a public network: Inform your personnel of the risks of connecting to unsecured Wi-Fi networks to access confidential data. Employees can use a virtual private network to encrypt and conceal online activities if utilizing public Wi-Fi is essential.
-
Use mobile device management to enforce regulations (MDM): MDM tools, such as Microsoft Intune, are crucial for protecting BYOD regulations. The central management console is located on the company's servers, and MDM functions by installing software agents on devices so they may connect directly to it. To enforce BYOD regulations, you may regulate company-registered devices' security settings from the central panel. To avoid data breaches, for instance, you may utilize MDM solutions to remotely delete data from stolen or lost devices. You may even put unapproved chat applications and games on a blacklist if you think they might compromise your company's security.
Over-the-air distribution is another feature of MDM systems that enables you to deploy security software bundles and updates on devices that are registered with your business. Since workers may work remotely, it is simple to maintain device security consistency and compliance with BYOD regulations. Additionally, MDM systems offer thorough reports of business-registered devices, including information on their features, whereabouts, and most recent activities. Maintaining software upgrades and spotting noncompliant user behavior is made easier by doing this.
-
Establish access limitations: Enforcing access controls has two separate benefits and limits what workers may do with their devices. First of all, it limits employee access to business networks and apps so that internal data breaches are reduced. Second, if hackers succeed in accessing employee accounts and devices, access controls reduce the potential harm from the ensuing data leak.
You may limit access using MDM solutions depending on an employee's position, location, device, and other factors. For instance, MDM might plan application lockouts to stop employees from accessing work accounts after hours. Even more susceptible gadgets, including those using jailbroken operating systems or linked to public Wi-Fi networks, can be blocked.
-
Take away equipment when it is not required: A device departure strategy for when employees leave the organization must be included in BYOD rules. MDM solutions hasten the process of retiring devices. It can terminate user accounts, revoke access rights, uninstall business software, and erase data from staff devices. On a device, it may even create a partition between business and personal data so that cleaning operations don't destroy the user's data.
What is the BYOD Strategy in School?
Two strategies are needed for network connectivity on personal technological devices. The first step in putting a BYOD plan into place at your school is having a strong wifi network. The second is good security. Small, remote, or underfunded schools could find it challenging to lay the groundwork required for a successful BYOD policy.
Additionally, schools are required to protect student privacy using appropriate measures. Schools face the danger of opening themselves up to phishing scams and cyber attacks by allowing students' devices to connect to their networks.
In school networks, a sizable quantity of financial and personally identifiable information (PII) needs to be secured. School cybersecurity is routinely overlooked as these networks develop to offer better learning experiences across campuses, making schools key targets for hackers. Unfortunately, kids are less careful and informed than adults, which leaves them more open to phishing and social engineering scams.
For school districts, physical security and cybersecurity require a comprehensive, economical solution that can be applied across all campuses and help with compliance. Schools must protect children from inappropriate information while also protecting devices and school networks from malicious threats. Their IT departments have to be able to provide a network that facilitates instruction while safeguarding children.
A firewall is essential for defending teachers and students on school networks from online dangers. A firewall is a safety measure that keeps track of and controls network data and traffic. It serves as a barrier between a trustworthy network and an untrusted network to stop harmful network traffic. It automatically detects and blocks phishing attacks to stop students' curiosity from becoming a liability. A firewall not only shields pupils from online dangers but also provides domain-level security and content screening to prevent them from visiting dangerous websites, wherever they connect. Under firewall protection, professors and students can do academic research without accidentally visiting websites that could expose them to legal responsibility or that might not be in line with the school's Acceptable Use Policy.
Enterprise networks and computer networks used in educational institutions, from K-12 through colleges and universities, are related. Schools and universities may have thousands of devices, including desktop computers, servers, tablets, and mobile phones, demanding network security and appropriate access restrictions similar to those found in business networks.
The Children's Internet Protection Act (CIPA), which tackles concerns about children's access to obscene or dangerous information online, places additional requirements on educational institutions in terms of internet security.
When you have a lot of students and staff, sensitive data to protect, and a tight budget to deal with, protecting your school's network may seem difficult or even frightening. In essence, a firewall that will be used as a school firewall should be able to support next-generation firewall technology. OPNsense powered with the Zenarmor next-generation firewall plugin is the best firewall for schools to prevent BYOD risks.
What is MDM in BYOD?
Mobile Device Management (MDM) is now the most widespread type of BYOD management. MDM, or mobile device management, is the administration of mobile devices, including dealing with their deployment, security, monitoring, integration, and management in the workplace. Applications may be delivered on user-owned devices while also protecting the corporate programs and data on them.
MDM was created as a solution to guarantee that workers remain productive while also prohibiting them from breaking business rules. MDM deployments might be cloud-based or on-premises. A few of the main issues that MDM handles are:
-
business data separation
-
securing business data and emails on devices
-
implementing company rules
-
integrating and controlling mobile devices, such as smartphones and laptops
MDM enables organizations to more effectively enforce security regulations and gives developers the opportunity to deliver apps to controlled devices. Full management of user-owned devices, however, may result in harsh measures like performing a complete lockdown or wipe of the user's device if it is lost or stolen, which may include the user's own private content. Users frequently experience frustration or disappointment when confronted with these facts. As a result, users may choose to circumvent IT regulations in order to covertly access company resources, which might cause further IT issues.