Top 10 Anti-Phishing Tools
Phishing is a form of cybercrime in which a criminal contacts a target or targets via email, sms, or phone call while posing as a reputable company in an attempt to obtain sensitive information such as passwords, personally identifiable information, credit card information, etc.
Phishing attacks frequently succeed by making malicious communications appear to be sent by a reliable source, such as a bank or phone company. The data is then exploited to gain access to critical accounts, potentially leading to identity theft and financial loss.
All businesses and organizations are threatened by phishing. In fact, phishing attacks play a role in almost a third of data breaches. Phishing, in contrast to other cybersecurity threats, preys on people's psychological vulnerabilities to obtain their personal information, making it historically very challenging to stop.
Anti-phishing is the practice of preventing or resolving phishing attacks or scams. The prevalence of phishing increased by 600% globally in 2020, necessitating the use of anti-phishing software.
This article explains the best anti-phishing programs and how to use them to effectively combat phishing on a large scale. The article will include the following headings as a summary.
-
Why anti-phishing tools are crucial
-
What are the key features of anti-phishing tools?
-
What are the most popular anti-phishing tools and technologies available?
-
How to Configure Zenarmor NGFW to Block Phishing?
Why Anti-phishing Tools are Crucial?
Phishing operates by sending messages that appear to be from a reliable business or website. The link in phishing messages typically directs the user to a fake website that mimics the real thing. After that, the user is prompted to enter personal data like their credit card number. The person's identity is then stolen, or unauthorized credit card charges are made using this information.
It is difficult for people to recognize phishing attacks because they can be concealed as legitimate-looking emails. Their personal information and email security are at risk when victims fall for these scams. The consequences of phishing emails can include reputational harm, financial loss, and identity theft.
Hackers are adept at running their phishing scams through social media. They use social engineering to deceive their victims into disclosing private information. An effective phishing attack causes considerable financial losses and reputational damage to an organization.
Throughout the forecast period of 2022-2030, the market share of cyber security is anticipated to increase at a CAGR of 8.9%. In 2021, it had a $184.93 billion market value. An additional layer of security is added to your domain by anti-phishing solutions, one of the crucial components of cyber security, making it more difficult for fraudsters to impersonate you. This feature has the ability to recognize and stop incoming spoof emails.
The following advantages highlight the significance of anti-phishing solutions:
- Finding Risk: A phishing prevention solution finds risks in email, the web, or text that could compromise users' sensitive information. The email conveys a suspicious tone and increased urgency, which is a common tactic used to identify phishing.
- Reduce Cyber Risk: By raising awareness and taking proactive precautions, cyber risks can be reduced. Business email compromise (BEC), internal impersonations and vendor fraud, supply chain attacks, account takeover (ATO), and other financial frauds that are specifically targeted against your company are a few of the cyber risks.
- Damage Control: It prevents malware downloads or credential theft from phishing websites.
- Zero Trust Security: Consider all user interactions to be potentially malicious.
- Deliver Operational Efficiency: This leads to improved end-user satisfaction, faster business growth, and operational efficiency.
What are the Key Features of Anti-phishing Tools?
The number of phishing attacks worldwide increased to over 250,000 in 2016 and is continuing to rise. Despite the alarming statistics, there are steps you can take to protect yourself from becoming a victim.
Purchasing a specialized anti-phishing solution is one such precaution. This involves a number of security measures that close gaps in your online safety. These are some of the main characteristics of anti-phishing software.
- Email filtering: Cybercriminals can access your network by sending phishing emails or visiting malicious URLs. Incoming message attachments are checked for viruses, malware, and other malicious intentions by anti-phishing software. The majority of anti-phishing programs prevent malicious emails from getting to your inboxes.
- URL analysis: Malicious URL clicks can result in serious harm, including data loss, ransomware attacks, and financial losses. Anti-phishing software reduces these effects by analyzing a URL to determine whether it contains a genuine link or a phishing one. Other techniques for spotting phishing websites include looking for grammatical, spelling, and punctuation errors, looking for missing information like contact information, or using a fictitious password.
- Link and attachment scanning: Your legitimate emails are safe because anti-phishing software scans incoming messages to identify spam and block malicious emails. To distinguish between legitimate emails and spam, these solutions typically employ machine learning. Anti-phishing software will only ignore emails with this feature if they deviate from standard behavior.
- Domain spoofing detection: Hackers may attempt to spoof your domain in an effort to deceive staff members into thinking a message is coming from a reliable source. Employees can occasionally be careless, and all it takes for a successful spoofing attack is a small, imperceptible change to your display name or email address. Anti-phishing programs increase the security of your domain and make it more difficult for fraudsters to impersonate you. This feature has the ability to recognize and stop incoming spoof emails.
- Real-time threat intelligence: Certain con artists might attempt to spoof your domain name, particularly if you receive a lot of traffic. By incorporating additional security measures into your signatures, anti-phishing software can deter online criminals from forging your domain name. Additionally, this software can detect incoming spoof emails. Sometimes, only a slight modification to the display name or email address is necessary for a spoofing attempt to be successful. Anti-phishing software can relieve you of responsibility by automatically spotting spoofing.
- User awareness and training: The foundation of the total solution should be security awareness training, with technical mitigations being developed to support the training and awareness.
- Various Mail Servers are Supported: You won't have any trouble integrating the anti-phishing software with your current server because the majority of anti-phishing solutions support various mail servers. So you're good to go, whether you're using the Gmail or Yahoo mail servers.
- Acceptable for Mobile: Anti-phishing tools should work seamlessly on mobile devices for employees who work from home. The best anti-phishing software works flawlessly with all mobile devices running Windows, iOS, or Android operating systems. Anti-phishing software is necessary to safeguard your data, whether you are at home or on the go.
What are the Most Popular Anti-phishing Tools and Technologies Available?
In order to gain access to accounts, steal data and identities, and download malware onto the user's computer, the attacker contacts people for their private information via email, a web browser, a phone call, or social media. There are several phishing protection solutions and some open-source anti-phishing tools available to stop these kinds of activities.
These solutions assist users in blocking both the phishing payload (malware) and its delivery (email, text), as well as raising user awareness.
What are the Types of Anti-Phishing Tools?
Anti-phishing software categories are listed below:
- Browser-based Solutions: Browser-based anti-phishing tools evaluate attack methods on any web page. This solution aims to get rid of phishing payloads (malware downloads, theft of credentials, etc.).
- Email-based Solutions: Email-based anti-phishing tools scan each email for red flags of suspicion. This type of solution focuses on phishing delivery and only protects emails.
- API-based Solutions: API-based anti-phishing tools use a cloud sandbox with an API to check files, messages, and URLs. This type of solution is compatible with many collaboration tools, but it is largely reactive rather than proactive.
What are the Best Anti-Phishing Tools?
The top ten products created to defend your company from phishing attacks are listed below. These include security awareness training platforms, post-delivery cloud email security solutions, and secure email gateways, which screen incoming and outgoing emails for potential threats before they reach the user's inbox. Education is one of the most effective forms of prevention; by being aware of phishing attacks, you'll be less likely to fall for them. We'll give you some background on the supplier, the key components of each solution, and the kinds of clients each is best suited for.
The top ten anti-phishing tools are as follows:
- Microsoft Defender for Office 365
- Mimecast
- Proofpoint
- Barracuda Sentinel
- IRONSCALES
- BrandShield Anti-Phishing
- Cofense
- Avanan
- Sophos Email
- Trend Micro ScamMail Suite
1. Microsoft Defender for Office 365
A cloud-based email security service called Microsoft Defender for Office 365 (formerly known as ATP) provides defense against viruses and malware that are unknown. Defender is an add-on module that can be purchased or is included in select Exchange and Microsoft 365 subscription levels. Administrators can use the built-in reporting and URL trace features to learn more about the types of assaults taking place.
The anti-phishing tool from Defender scans incoming messages for telltale signs that they might be phishing attempts using machine learning modules. These consist of the message's header, sender's address, and body. The attack is stopped when a threat is identified. Microsoft Defender is equipped with the ability to recognize and reject harmful links and attachments. Many third-party solutions struggle to safeguard SharePoint, OneDrive, and Teams from malicious files, but this functionality extends that protection.
Similar features that Microsoft Defender for Office 365 offers include user education, phishing detection and prevention, forensic and root-cause analysis, and even threat hunting. Defender is tightly connected because it is merely an add-on for Office 365, therefore there is no need to establish the initial integration. Microsoft provides pre-set security rules that you may customize to meet your needs; these policies support enforcement, user override, and policy modifications over time. Office 365 subscribers will receive particular benefits from this service, while non-customers will have special drawbacks.
Microsoft Defender is well-known for its affordability and easy integration with an Office 365 setting. Because of this, it is appropriate for any firm searching for a quick and simple security solution.
With its sophisticated anti-phishing technology, the tool can automate investigations. It guarantees secure attachments and connections by simulating attacks and including additional safety features. It implies that the security is maintained during the duration of the transmission. The URL will be examined and processed once again for vulnerabilities with each click.
The main features of Microsoft Defender are as follows:
- Intelligence for the mailbox's anti-phishing features
- Secure links and attachments
- Automated investigation and reaction, or AIR
- Including the DefenderAttack simulator in Microsoft 365
2. Mimecast
Mimecast provides a number of tools for thwarting phishing attempts, including tools that identify harmful URLs and attachments and either remove them or make them safe using cutting-edge techniques like sandboxing. By accessing links inside the Mimecast cloud, Mimecast is able to stop code-based assaults that are started by phishing emails or more complex techniques like QR codes, making deployment easier and guaranteeing that preventive measures are constantly up to date with the bleeding edge.
With more than 36,000 customers worldwide, they primarily target enterprise organizations with their highly configurable and versatile products. The comprehensive email security, archiving, and continuity solution from Mimecast include phishing protection technology that is supplied via a subscription service to an intuitive interface.
Additionally, they provide training on phishing, DMARC compliance, DNS filtering, and email encryption. Their product is a great fit for mid-sized and large enterprises thanks to its clear reports and analytics as well as its high degree of flexibility and customization.
Beyond anti-phishing, Mimecast offers content controls, data leak prevention, browser isolation, and a secure platform for information/file exchange. Mimecast is an end-to-end solution to your information security concerns. To identify social engineering threats, it contains a specifically targeted threat dictionary controlled by Mimecast experts.
The primary features of Mimecast are listed below:
- Security against suspicious URLs and notifications
- To stop domain spoofing, analyze email attachments and sandbox them using Mimecast Brand Exploit Protect.
- Preventing attacks based on impersonation and domain spoofing
- To isolate the effects of URL clicking and surfing, use browser isolation.
- For secure communication, use Mimecast's secure messaging and large file sending.
3. Proofpoint
The email solution offered by Proofpoint, a well-known vendor of cybersecurity products, is very complete. You can track the origin of email messages and is protected from phishing and impostor emails.
They offer a security service package called Proofpoint Essentials that claims "complete defense" for small and medium-sized businesses. To assist avoid data loss and shield your staff from falling for phishing schemes, hackers, and malware, this multi-layer package solution combines email encryption, archiving, strong anti-virus technology, and a Secure Email Gateway.
The Proofpoint Essentials package makes use of a number of security measures intended to guard against phishing. In order to identify spam and phishing emails, Proofpoint MLX technology first looks at the text, image, and attachment content.This machine learning technique is 99% effective and instantly adjusts to new threats. Second, the potent "URL Defense" and "Attachment Defense" services find, stop, and sandbox harmful URLs and attachments that frequently target smaller businesses. Advanced antivirus engines then scan all messages to detect and remove any known viruses. Heuristic scanning technology is another tool that Proofpoint Essentials employs to find and guard against novel infections and altered versions of known threats.
To provide users with more thorough and sophisticated coverage, Proofpoint has improved its Proofpoint Essentials product. The Business+, Advanced+, and Professional+ subscriptions include these new features. The Supernova threat engine is now being used by Proofpoint to triple the rate of BEC detection.The riskiest links can be found via predictive URL scanning, and this can make sure that they are sandboxed right away. With tags and notifications, the new changes make it simpler for users to recognize potentially questionable emails. In the event that a malicious email does reach a user's inbox, a one-click pull enables the admin to quickly delete every instance of that email from the user's accounts.
Some capabilities of Proofpoint are given below:
- Use an email classifier to divide emails into categories such as bulk mail, fraud, impostor, spam, malware, explicit content, and circle of trust.
- Email cautionary tags to assist consumers in making wise decisions
- Administration restrictions for handling encrypted messages and low-priority messages will be evaluated by Proofpoint NexusAI and taken into consideration.
- Many layers of detection, such as reputation and content analysis
- Identification of graymail (such as newsletters and mass mail) with granular email filtering
The primary benefit of using Proofpoint email security is the ability to extend it to utilize other email security solutions like Threat Response Auto-Pull (TRAP) and Email Fraud Defense. This enables you to design a secure communication environment from beginning to end according to your needs.
4. Barracuda Sentinel
Barracuda offers a wide variety of multi-layer solutions for network, cloud, and email security. Their AI-based security product, Barracuda Sentinel, shields customers from spear phishing, account takeover, and business email compromise (BEC) assaults.Through DMARC research and reporting, Barracuda offers brand protection and domain fraud prevention.
Microsoft 365 and Barracuda Sentinel work together seamlessly to identify and stop inbound and outbound email assaults. It employs a potent AI engine to learn each employee's communication styles and then recognize signs within each email that indicate if it was sent maliciously. Before the user may open the email, Sentinel blocks it if a threat is found. Sentinel requires almost no IT administration thanks to the utilization of AI.
Organizations can use Barracuda's simulation platform, PhishLine, for anti-phishing training in addition to the technological security provided by Sentinel. Through a series of adaptable simulations, PhishLine seeks to turn employees into an extra line of defense.
Barracuda Sentinel is fully cloud-based and works with Office 365. This, together with its affordable cost, makes it the perfect option for smaller businesses and MSPs seeking efficient cloud-based phishing prevention.
Threats that are already present in the inbox are discovered by Barracuda Sentinel. In addition to watching the incoming emails, this feature. To stop harmful tries in incoming communications, it uses AI-based threat detection to identify vulnerable accounts. Threats that get past the email gateway's protection are rapidly identified by Sentinel.It notifies external receivers and deletes emails that were sent among internal users that were vulnerable.
The primary features of Barracuda Sentinel are as follows:
- Deleting emails from users' inboxes
- Sending out warnings
- ?ncident response that is automated
- Forensics and reporting in real-time
- Detecting individuals who interact with uneasy emails
- Sending suspicious mail reports
- Stopping domain fraud
5. IRONSCALES
Through dynamic detection and analysis, IRONSCALES is an email security platform that aims to augment your current email system by blocking, flagging, or even putting a banner to potentially suspect correspondence. Additionally, IRONSCALES provides end-user training that is centered on email security and general awareness. This helps you bolster your defense against the social engineering attack that is at the heart of phishing.
Their post-delivery protection technology provides defense against sophisticated phishing emails attacks such as account takeover (ATO), VIP impersonation, and corporate email compromise (BEC). They have a cloud-based solution that is completely compatible with Office 365 and Google Workspace, making it simple to implement and requiring no modifications to MX records.
In order to detect and instantly delete harmful emails in real-time, IRONSCALES blends human and artificial intelligence.After a suspicious event is discovered, Themis, a virtual security analyst from IRONSCALES, finds and eliminates the threat from all impacted end-user inboxes, lightening the load on your harried security team. The platform records and remembers each time this occurs so that the network will never be compromised by the same assault again.
In addition, IRONSCALES gives users the option to report questionable emails via a button located right in their email inbox, whether they are using a desktop or mobile device. All other users who have received the email will be alerted with a customizable warning banner when an end-user reports an attack in this manner.
The main features of IRONSCALES are listed below:
- Mailbox-level BEC security, democratized threat hunting, and threat simulation for phishing attack analysis and user training
- Protection against malicious file attachments and shady URLs
- Incident response with AI
- Themis, a virtual SOC analyst, and assistant, uses crowdsourcing to identify threats both inside and outside the enterprise.
IRONSCLES' patented AI and ML technology is one of its key USPs. By allowing for human discretion and understanding, it enhances assessment capabilities with each possible hazard and corrective measure.
6. BrandShield Anti-Phishing
BrandShield is only dedicated to safeguarding the reputations of your executives and your company. One part of BrandShield's portfolio is identifying phishing assaults (via email, social media, or other channels) that use your brand or the names of your executives. Additionally, BrandShield keeps an eye out for unauthorized websites using your brand as well as online shops like Amazon where actual knockoffs of your goods can appear for sale.
Its extensive toolkit keeps an eye on particular locations to find phishing sites. Its sophisticated system is effective in identifying spoofing. Blacklists and protecting digital assets from fraudulent websites are only a couple of the capabilities that the BrandShield product is equipped with.
The major features of BrandShield are given below:
- Web and social media anti-phishing features Brand protection (including the logo and other digital assets)
- Anti-copying characteristics
- Mitigation of executive impersonation
7. Cofense
Cofense PDR (Phishing Detection and Response) is a managed service that combines the use of AI-based algorithms with security experts to detect and stop phishing attempts in real-time. If you need to increase the level of security, managed services can be a smart alternative. In fact, since the managed services team is able to assess threat data from all of the enterprise systems they secure, they may be even more effective than hiring a full-time team to handle phishing prevention.
The anti-phishing expert Cofense provides a variety of products to address phishing concerns. This includes an employee resilience program, a phishing detection and reporting service, a learning management system for awareness training, and phishing threat intelligence.
The technology behind Cofense's phishing defense comes from Cyberfish, an Israeli business they bought in 2021.
Outlook, Gmail, and IBM Notes are all compatible with the Reporter button. After that, Cofense Triage employs an automated spam engine along with human intelligence to separate real known threats from false alerts. Threats that are real are isolated. The Cofense Vision technology can then be used by security teams to conduct thorough searches to find and contain any dangers. Administrators can remove a dangerous email from all other user inboxes with a single click. The email may be "un-quarantined" if it is later determined to be safe.
Some features of Cofense PDR are listed below:
- A dynamically updated danger database has over 25 million global threat reporters.
- Integrations with systems for SOAR, SIEM, next-generation firewalls, and endpoint security
- Service for automatically identifying and isolating dangers in emails
- Simulations of phishing threats to increase worker resiliency
- SPAM engine and automated phishing email analysis
- An employee interface to combat phishing scams
Cofense provides specialized solutions for a variety of industries, including healthcare, finance, energy & utilities, retail, manufacturing, and the public sector. The specialized solutions offered by Cofense can be used by companies without an experienced internal IT team.
8. Avanan
Avanan provides anti-phishing software for cloud-hosted email and integrates with your email provider via APIs to train their artificial intelligence (AI) using previous email. The service assesses relationships between senders and receivers in addition to message contents, formatting, and header data to determine a level of trust.
Avanan, an email security solution, protects any instant messaging service or email client, such as Microsoft Teams, Slack, Microsoft 365, etc., from fraudulent attacks. In addition to conventional email, it is helpful for spotting social engineering efforts that might be started through collaborative channels.
Cloud-based email and application security from sophisticated phishing, malware, account breach, and data loss attacks is provided by Avanan. Once installed, it provides protection for any associated cloud-based programs like Teams, OneDrive, and Google Drive.
Avanan's engines can identify user impersonation or fraudulent emails before they reach the inbox by analyzing email conversation patterns using machine learning technologies. In order to detect threats, it does this by identifying signs of malicious emails, such as the domain, the time and place of transmission, and the email's actual content.
The use of machine learning technology in Avanan's solution allows it to constantly adapt to new and creative attacks intended to get beyond traditional email security solutions and gateways. Instead of protecting users from inbound, outgoing, and internal emails on the organization's broad domain, it offers protection for each user's specific inbox.
Avanan is able to spot fraudulent activity across the email network, including internal communications delivered through other cloud services as well as file updates and permission changes. This reduces the risk of business email compromise threats by detecting and flagging compromised accounts.
The main features of Avanan are as follows:
- Integration of cloud applications for communication, email, messaging, and file-sharing applications
- Advanced threat patterns were trained in the core analysis model.
- AI to identify relationships between workers, email usage, and communication
- Threat management interface that supports global policy control
- TLS-encrypted, OAuth token-based communication with SaaS applications
- A group of specialists for quick incident reaction
Avanan has the special ability to warn or stop phishing assaults without changing mail exchanger records or MX data. As a result, it is hard for attackers to determine whether you are using anti-phishing software and plan to get around the protection measures.
9. Sophos Email
A phishing prevention solution with strong AI and policy-oriented attack identification is Sophos Email. In order to stop phishing and ransomware assaults, it uses behavioral analysis to allow users to administer their accounts securely. In addition to filtering and quarantining suspicious emails, it attaches them to a user's blocklist or tags them with a subject-line message. Additionally, it has a threat reduction capability that uses simulation-based training. The tool is simple to use and provides thorough security in many different languages. The use of predictive technologies to stop assaults before they reach any network is the most significant feature.
Some features of Sophos Email are listed below:
- Verification of incoming and outgoing messages
- Anti-virus protection
- Real-time security when visiting URLs
- Detailed records and pricing
- Protection from spam and ransomware
10. Trend Micro ScamMail Suite
ScanMail Suite for Microsoft Exchange uses better site reputation, sandboxing, and document exploit detection as part of a proprietary APT defense to stop spear phishing and highly targeted email attacks, protection you won't receive from competing products. Additionally, only ScanMail uses email, file, and online reputation technologies to block classical malware in addition to correlating global threat intelligence from Trend Micro's Smart Protection Network cloud-based security.
The main features of Trend Micro ScanMail Suite are given below:
- Defends against APTs and other types of targeted assaults
- Reduces targeted attacks using a variety of defense technologies
- Performs execution analysis on your particular environment and offers individualized danger intelligence through interaction with Deep Discovery Advisor
- Custom security updates are released to other security layers to address the issue and stop future malware attacks.
- Reputation technology blocks more malware, phishing, and spam.
- Detects dangerous web links and attachments to stop malware downloads
- Blocks more message threats using connected email, file, and web reputation, the only mail server security to do this
- Based on Opus, stops more spam than other security measures. Independent test one
- Reduces IT expenditures and improves performance
- Enables powerful group configuration and administration, centralized logging, and reporting to streamline email security operations.
- With centrally managed, template-based DLP, compliance and data privacy initiatives are made easier.
- A network defense is required for targeted attacks.
- With improved web reputation, a document exploit detection engine, and sandbox execution for in-depth threat analysis, Trend Micro messaging security solutions defend against targeted assaults.
How to Configure Zenarmor NGFW to Block Phishing?
Zenarmor can thwart real-time phishing and zero-day malware attacks because of its AI-based Cloud threat intelligence. Zenarmor offers a real-time large cyber threat intelligence database that includes reputation and security data for over 1+ billion websites with new ones being uploaded on a regular basis. With the help of Zenarmor, you can instantly respond to malware threats, phishing scams, and virus outbreaks.
By deploying Zenarmor on your open-source firewall, you will have effective protection against phishing attacks. Zenarmor is compatible with the most prominent BSD-based open-source firewalls, including OPNsense and pfSense, and the most popular Linux distributions, including RHEL, Ubuntu, Debian, CentOS, and Alma Linux.
You can easily prevent phishing attacks on your open-source firewall powered with Zenarmor by following the steps given below.
- Login Zenconsole, Sunny Valley Networks Cloud Management Portal.
- Launch Zenconsole by navigating to Firewalls > My Firewalls.
- Select your firewall.
- Navigate Policies > Default > Security
- Block Phishing Servers option under Essential Security.
- Block Recent Malware/Phishing/Virus Outbreaks option under Advanced Security.
- Synchronize the Policy.
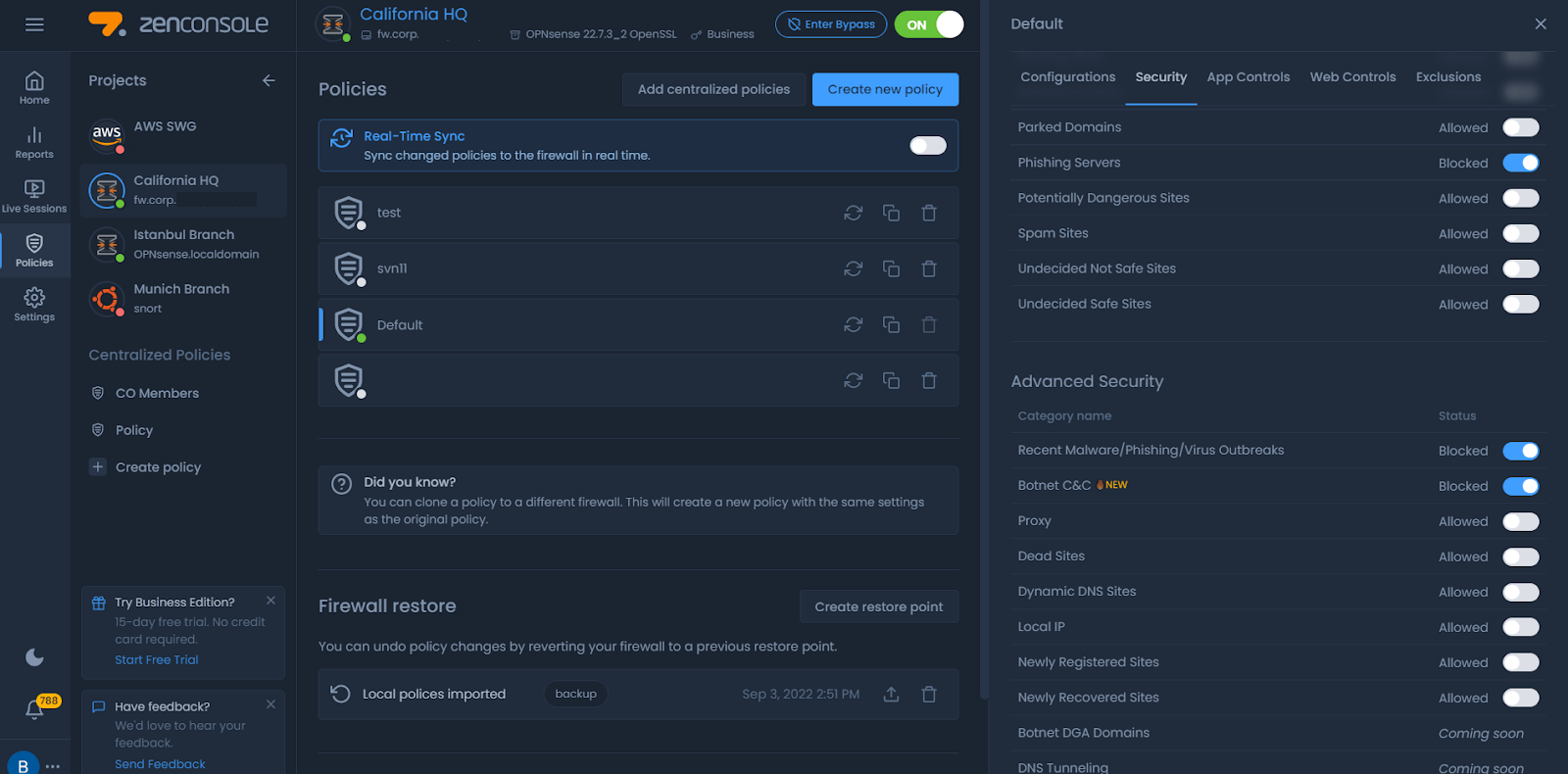
Figure 1. Preventing C2 attacks on open source firewall with Zenarmor