Best SIEM Tools
Security information and event management (SIEM), which combines security information management (SIM) and security event management (SEM), provides real-time event monitoring and analysis as well as tracking and logging of security data for compliance or auditing needs.
Simply said, SIEM is a security tool that aids companies in identifying possible security flaws and threats before they have a chance to interfere with daily operations. For security and compliance management use cases, it surfaces user behavior abnormalities and employs artificial intelligence to automate many of the manual operations related to threat identification and incident response. It has become a mainstay in contemporary security operation centers (SOCs).
Throughout time, SIEM has developed into something more than the log management technologies that came before it. Thanks to the power of AI and machine learning, SIEM now provides powerful user and entity behavior analytics (UEBA). It is a very effective data orchestration solution for handling constantly changing risks as well as reporting and regulatory compliance.
This article is basically about SIEM tools. You will find information on the following topics related to SIEM tools:
-
Who uses SIEM software?
-
Which are the Top Open-Source SIEM Tools?
-
Which are the Top Commercial SIEM Tools?
-
What is the Difference Between SIEM Tools?
-
What are SIEM alternatives?
Who uses SIEM software?
With a high number of devices connected to their networks, enterprise organizations invest in SIEM technologies, which enable them to gather log data from hardware, operating systems, apps, and security tools to continuously monitor their networks. Moreover, these businesses assign IT workers to system upkeep, security monitoring, and attack response. ArcSight ESM (Enterprise Security Management), AT&T Cybersecurity (formerly known as AlienVault), Fortinet, IBM QRadar, McAfee SIEM, and Splunk are a few popular SIEM examples you may be familiar with.
The SIEM software is not a viable alternative for the majority of small enterprises due to its breadth and resource needs. However, the software can be too expensive for many small enterprises, costing tens of thousands of dollars annually. Thus, SIEM is typically a superior option for business security.
Which are the Top Open-Source SIEM Tools?
There is no open-source SIEM solution that is entirely flawless. As there isn't a single fully functional open-source SIEM, this is also not a list of them. Current solutions either require merging with other tools or lack fundamental SIEM features like event correlation and reporting. But if you decide to undertake the challenging task of creating your own SIEM from scratch using open-source software, these are the parts we believe you ought to employ. Best open-source SIEM solutions are explained below:
-
OSSEC
-
OSSIM
-
ELK Stack
-
OpenSearch
-
Prelude
-
Suricata
-
Snort
-
SecurityOnion
-
MozDef
OSSEC
OSSEC is a well-liked host intrusion detection system (HIDS) that is open-source and compatible with a number of different operating systems, including Linux, Windows, Macintosh, Solaris, OpenBSD, and FreeBSD.
The manager (or server), which is in charge of gathering log data from various data sources, and the agents, which are software programs in charge of gathering, processing, and making the logs simpler to examine, are the two primary parts of OSSEC.
There is no visualization layer included in the OSSEC project itself. The advice is to utilize external visualization tools like Kibana and Grafana instead of the UI that was deprecated.
OSSEC keeps an eye on a variety of host-specific factors directly. Log files, file integrity, rootkit detection, and Windows registry monitoring are all included in this. Other network services, such as the majority of well-known open-source FTP, mail, DNS, database, web, firewall, and network-based IDS solutions, may be analyzed using OSSEC. OSSEC may also examine the logs produced by a variety of paid network services and security programs.
As part of automated intrusion detection or active response systems, OSSEC offers a variety of alerting alternatives. A simple log storage engine is used by OSSEC. Host agent log messages are not kept around by default. OSSEC deletes these logs after analysis unless the logall> option is present in the ossec.conf file for the OSSEC management. OSSEC keeps the receiving logs from agents in a text file that is rotated daily if this option is enabled.
It is debated whether OSSEC qualifies as an "all in one" SIEM system. OSSEC undoubtedly puts in the effort necessary to set up a SIEM system by gathering and analyzing data, but it is missing some of the essential elements for log management and analysis. It's important to note that other HIDS solutions (such as Wazuh) have cloned the OSSEC project, extending its features and transforming it into a more comprehensive SIEM alternative.
OSSIM
Unified Security Management (USM) by AlienVault's open-source product, OSSIM, is perhaps one of the most well-known open-source SIEM solutions. Important SIEM elements, including event gathering, processing, and normalization, are included in OSSIM.
To create a comprehensive SIEM, OSSIM integrates native log storage and correlation features with a number of open-source projects. OSSIM contains FProbe, Munin, Nagios, NFSen/NFDump, OpenVAS, OSSEC, PRADS, Snort, Suricata, and TCPTrack among its list of open-source projects. The SIEM will undoubtedly demand more management time to maintain as a result of the additional open-source projects you add to the mix.
The addition of OpenVAS is particularly noteworthy because OpenVAS uses IDS logs and vulnerability scanner data to identify vulnerabilities.
As might be expected, the open-source OSSIM has fewer features than its for-profit counterpart, and both have serious scaling issues, even in small situations. The open-source version of OSSIM has almost no log management functionality.
ELK Stack
When it ceased to be really open source, the ELK stack was likely the most well-liked open-source product used as a foundation in a SIEM system. Indeed, a construction block. A comprehensive SIEM system is not necessary since there is much area for disagreement on whether the ELK Stack counts as an "all in one" SIEM system.
Elasticsearch, Logstash, Kibana, and the Beats family of log shippers make up the ELK stack. As of January 14, 2021, Elasticsearch and Kibana are covered under SSPL licensing.
A log aggregator called Logstash can gather and analyze information from virtually any data source. Any log data that it gathers can be enhanced by filtering, processing, correlating, and other means. The storage engine and one of the top options for indexing and storing time-series data is elasticsearch. The visualization layer in the stack is Kibana, and it's a very potent one at that. The data collection and Logstash shipping into the stack are the responsibilities of Beats, which consists of a number of lightweight log shippers.
To gather logs, Logstash makes use of a variety of input plugins. However, it incorporates data from more specialized programs like OSSEC or Snort. The log processing, storage, and visualization powers of the ELK Stack are functionally unrivaled. Yet the ELK Stack, at least in the free version provided by Elastic, is lacking several essential elements for SIEM.
There isn't any built-in reporting or alerting feature, first and foremost. This is a well-known sore issue for customers attempting to utilize the stack for security as well as for more typical use cases, including IT operations. The Elastic X-Pack, a for-profit solution, or open-source security add-ons may both be used to provide alerting.
Moreover, there are no applicable built-in security restrictions. The stack becomes somewhat more expensive to manage as a result, both in terms of resources and operating expenses.
OpenSearch
As a derivative of the Elasticsearch and Kibana projects, OpenSearch is an open-source software project that was started in 2021 with development overseen by Amazon Web Services. The project consists of an OpenSearch-branded database and OpenSearch Dashboards, which are front-end visualization and analytics tools.
Elastic, the company that created the Elastic Stack, also known as the ELK Stack or Elastic Stack and made up of the Elasticsearch, Kibana, Beats, and Logstash projects, announced in January 2021 that it would switch to a dual licensing model based on the Server Side Public License (SSPL) and the Elastic License, neither of which have been acknowledged as open source licenses by the Open Source Initiative (OSI). As a result, Logz.io collaborated with Amazon and other top business players to develop OpenSearch, an open-source alternative to the recently closed-source ELK stack.
Several businesses utilize OpenSearch as a custom logging repository for security data. Due to the fact that any basic SIEM functionality, such as security detections, content, analytics, and threat enrichment, must be manually implemented, it cannot be considered a SIEM per se. Yet it is a cost-effective and future-proof strategy for firms with a lot of technical skill but little funding.
Prelude
Prelude is a SIEM framework that integrates several other open-source tools, much like OSSIM does. Moreover, it is an open-source variation of the identical commercial program, much like OSSIM. Prelude tries to perform the functions left unfilled by programs like OSSEC and Snort.
Prelude uses the Intrusion Detection Message Exchange Format to store all of the logs and events it receives from various sources in a single area (IDMEF). It offers tools for filtering, correlating, alerting, analyzing, and visualizing.
Prelude's open-source version is severely constrained to OSSIM in comparison to the commercial product in terms of all of these features, which is possibly why it is not especially well-liked. Prelude OSS is intended for evaluation, research, and test purposes on extremely tiny settings, according to the official documentation. Please be aware that Prelude OSS performances are significantly worse than Prelude SIEM.
Suricata
By serving as a common intrusion detection system (IDS), PCAP processing, intrusion prevention, and network monitoring tool, it has eroded Snort's user base. The Open Information Security Foundation (OISF) is its owner. It is uniquely constructed using the Lua programming language, which is a compact, quick, and embeddable language.
For other databases like Elasticsearch and Splunk, it maintains integrations in YAML and JSON. While there are minor variations, it employs many of the same principles as Snort. It can identify HTTP and SSH traffic using application-layer detection rather than OpenAppID.
It is better at handling problems with contemporary computers because it is a newer tool. Instead of Snort executing several instances on a single thread, it supports multithreading natively.
Snort
Network intrusion detection system (NIDS) for Windows and Linux called Snort. It differs from other host-based solutions like OSSEC because of this. In light of this, Snort is not necessarily a replacement for OSSEC or other SIEMs but rather a potential addition.
Being a packet sniffer that can "sniff" out security dangers to networks, Snort derives its name. It recognizes and reports attack vectors, alerting syslog or another channel as a result. Together with logs, it does real-time traffic analysis. A broad variety of diverse attack vectors, such as OS fingerprinting, DDOS, CGI, SMB probes, buffer overflows, and stealth port scans, are among the many things it is made to identify. It recognizes apps using OpenAppID.
Martin Roesch, the Snort program's founder, put together Sourcefire to oversee the software for its hundreds of thousands of users. Cisco purchased Sourcefire in 2013, but Snort's open-source roots remain (while Cisco has gone on to develop commercial alternatives based on the original software).
Snort 3.0, the most recent major version, was released in January 2021 and solved numerous issues with Snort 2.x, notably the absence of multithreading. Suricata and Snort are frequently contrasted, and Snort may be used in place of Suricata.
SecurityOnion
A free Linux distribution (distro) for intrusion detection and business security monitoring is SecurityOnion (ESM). Several open-source initiatives including the ELK Stack, OpenSearch, OSSEC, Snort, Suricata, and others are leveraged by this project. Doug Burks created it and released it in 2008; he then introduced Security Onion Solutions in 2014.
It offers full packet capture (FPC) through netsniff-ng and host-based and network-based intrusion detection systems (IDS) for detecting network-based vulnerabilities including data exfiltration and malware (other open-source options for FPC include GUI-based TCPDUMP and command-line interface Wireshark).
Users have the option of Snort or Suricata for network-based IDS, and Wazuh for host-based IDS (also known as HIDS).
MozDef
MozDef security incident and response automation tool was created by the Firefox-famous firm using other open-source technologies as a portmanteau for Mozilla Defense (and possibly more significantly, as a nod to rapper-activist Mos Def). 2014 saw its initial release.
A Docker container is used to operate each service in its architecture. According to Mozilla, it is a SIEM add-on that uses Python to create new rules and Elasticsearch as a logging engine.
According to the MozDef documentation, they can output JSON to HTTP(S) or rabbit-mq and interface with a variety of log shippers. Also, it is compatible with Amazon CloudTrail and GuardDuty. They cite the subsequent open-source tools as their foundation in addition to those already mentioned: Nginx, Meteor, MongoDB, VERIS (from Verizon), and several JavaScript or Python-related technologies.
Which are the Top Commercial SIEM Tools?
The list of top commercial SIEM tools with their most popular features is provided below.
-
Splunk Enterprise
-
SolarWinds
-
Datadog Security Monitoring
-
Salesforce
-
LogRhythm
-
ManageEngine Log360
-
ArcSight
-
IBM QRadar
-
RSA NetWitness
-
McAfee ESM
-
Rapid7 Insight IDR
-
PRTG
-
AlienVault
Splunk Enterprise
Splunk Enterprise is ideal for medium-sized, large-sized, and small enterprises. The product is eligible for a free trial, albeit each product's trial length varies. On the main enterprise platform, a free trial is offered. They can provide you with a quotation. According to evaluations, the enterprise license will cost $6000 for a permanent license that allows for 500MB per day. Moreover, the term license is offered for $2000 a year.
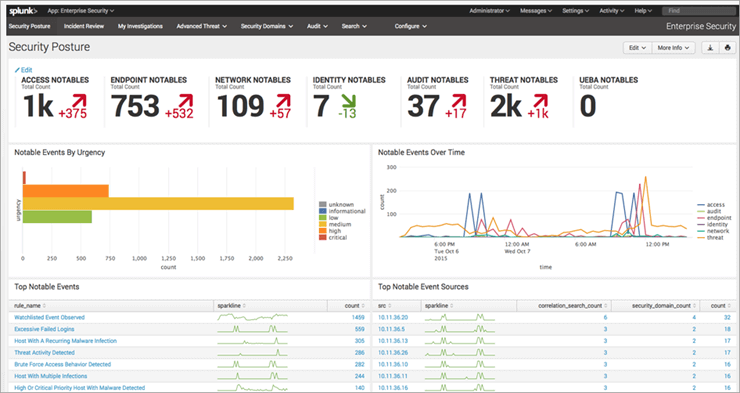
Figure 1. Splunk Enterprise Dashboard
Via configurable dashboards, asset investigators, statistical analysis, incident review, classification, and investigation, Splunk offers enhanced security operations. It contains capabilities for managing alarms, risk rankings, etc. It offers healthcare, financial, and security services to the public sector.
The primary features of Splunk Enterprise are listed below:
-
All machine data, whether it is stored locally or on the cloud, may be used with it.
-
Automatic processes and procedures for prompt and precise responses.
-
It has the capacity to sequence events.
-
Detecting harmful threats quickly.
Splunk uses AI and machine learning to provide you with predicted and actionable insights. The dashboards and visuals may be altered. Customer evaluations indicate that it is an expensive product, making it ideal for businesses.
SolarWinds
SolarWinds is ideal for medium-sized, large-sized, and small enterprises.
SolarWinds offers a free 30-day trial that is completely functional. The starting price is $4665. You'll have to pay a one-time charge.
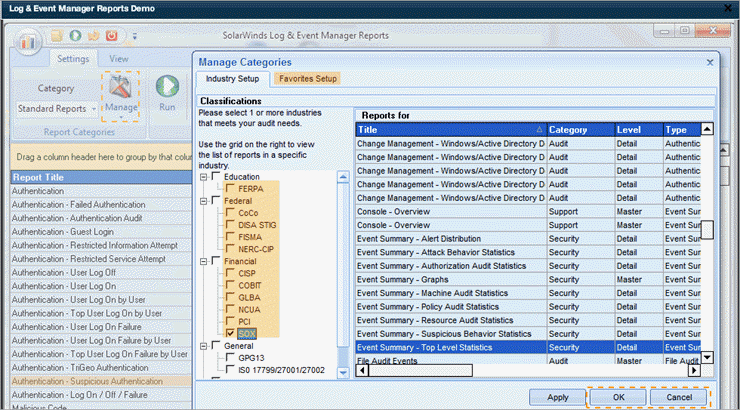
Figure 2. SolarWinds Dashboard
Via Log and Event Manager, SolarWinds offers a solution for on-premises network threat detection. It has tools for monitoring USB devices and automating threat mitigation. Log filtering, node management, log forwarding, the Events panel, and a greater storage ceiling are new features in the Log and Event Manager.
The main features of SolarWinds are as follows:
-
It has forensic analysis and powerful search capabilities.
-
Threats are identified more quickly with event-time detection of questionable activities.
-
It is prepared for regulatory compliance. It supports HIPAA, PCI, DSS, SOX, DISA, STIG, and other regulations for this.
-
It keeps up ongoing security.
Windows, Linux, Mac, and Solaris can all run SolarWinds. Reviews indicate that while SolarWinds lacks a comprehensive security suite, it nevertheless has useful features and capabilities for threat detection. For SMEs, it may be an excellent option.
Datadog Security Monitoring
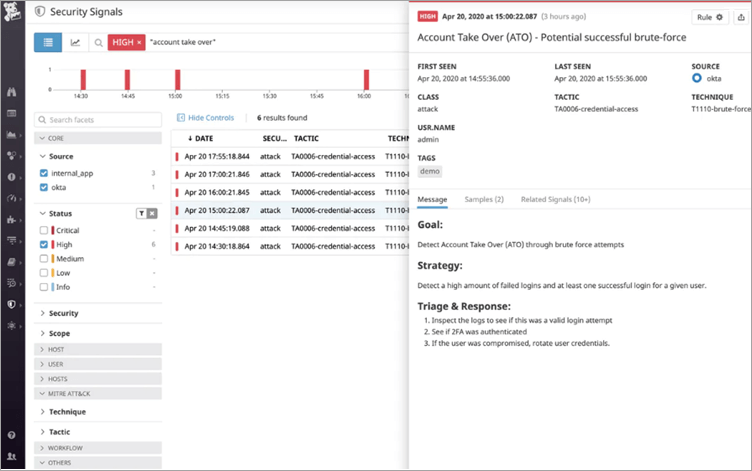
Figure 3. Datadog Security Monitoring Dashboard
By real-time threat detection, Datadog Security Monitoring assists you in securing your tech stack. It is simple to build up important security integrations, employ OOTB detection rules without a query language, and correlate security signals to check into suspicious activities.
The development, operations, and security teams are all integrated into a single platform using Datadog Security Monitoring. DevOps content, business KPIs, and security material are all shown on a single dashboard. Real-time threat detection and security alert investigation spanning infrastructure measurements, distributed traces, and logs.
Some features of Datadog Security Monitoring are listed below:
-
Datadog Security Monitoring allows you to get metrics, logs, and traces from your whole stack in addition to your security products thanks to its more than 450+ vendor-backed connectors.
-
You may use Datadog's Detection Rules to quickly and effectively identify security risks and unusual activity in any ingested logs.
-
With default out-of-the-box rules for common attacker approaches, you can start identifying threats in only a few minutes.
-
No query language is necessary; just change and customize any rule using our straightforward rules editor to match the unique demands of your company.
-
With Datadog Security Monitoring, you can eliminate silos between the development, security, and operations teams.
Salesforce
Salesforce provides excellent service operators and agents with security information software. They receive total access to all cases, incidents, and client information in a single workspace. This gives them more context, which they use to solve an issue more effectively. Prior to the consumer ever being aware of a security risk, the platform actively detects it.
Moreover, Salesforce can address security vulnerabilities before they worsen because of its many other external system integrations. The platform also gains from intelligent AI, which can quickly identify problems in a huge number of situations that are comparable.
Figure 4. Salesforce Dashboard
Large to small enterprises should use Salesforce.
Price: $25/user/month for the Essentials plan, $75/user/month for the Professional Plan, $150/user/month for the Enterprise Plan, and $300/user/month for the Unlimited Plan. There is also a free trial period of 30 days.
The primary capabilities of Salesforce are as follows:
-
Proactive in identifying problems
-
Instantaneous cooperation
-
Get regular information to solve issues quickly.
-
Use digital avenues to communicate with customers and keep them informed.
In conclusion, Salesforce provides a SIEM solution that satisfies the needs of both agents and customers. We highly suggest it because of its capacity to use AI to speed up the problem-solving process and proactively identify security risks.
LogRhythm
For issues including fragmented workflows, alarm fatigue, segmented threat detection, lack of automation, lack of metrics for determining maturity, and lack of centralized visibility, LogRhythm offers Next-Generation SIEM solutions. It offers diverse possibilities for data storage.
LogRhythm is ideal for medium-sized businesses.
Price: A high-performance appliance, software solution, and Enterprise license program are all available for quotation. Online reviews indicate that the starting price is $28000.
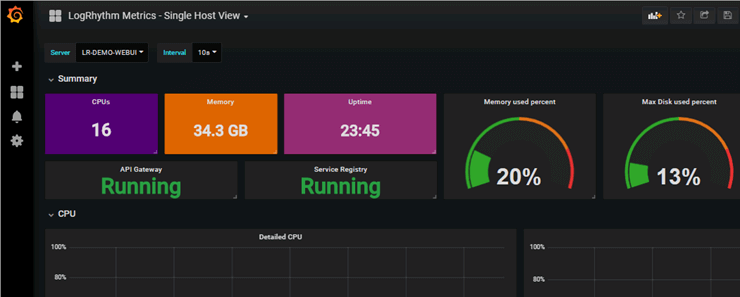
Figure 5. LogRhythm Dashboard
Some features of LogRhythm are given below:
-
You will have a consistent, standardized view as well as processing for unstructured data.
-
Linux and Windows are supported.
-
This technique is based on AI.
-
It works with a broad variety of hardware and log formats.
This platform contains all the features and functions, including AI, log correlation, and behavioral analysis. It has a learning curve, according to user evaluations, but the instruction booklet with hyperlinks to functions will help you become familiar with the application.
ManageEngine Log360
With the help of the excellent SIEM solution ManageEngine Log360, you can foresee, thwart, and mitigate security risks. The program continuously scans your files and directories and notifies you right away if any suspicious changes are found. You receive notifications in real-time, which improves the speed and effectiveness of your response to events. Very effective at detecting and reducing threats.
Price: Send an inquiry to receive a free estimate. The premium plan is available for 30 days without cost. End-of-year discounts just for ManageEngine products.
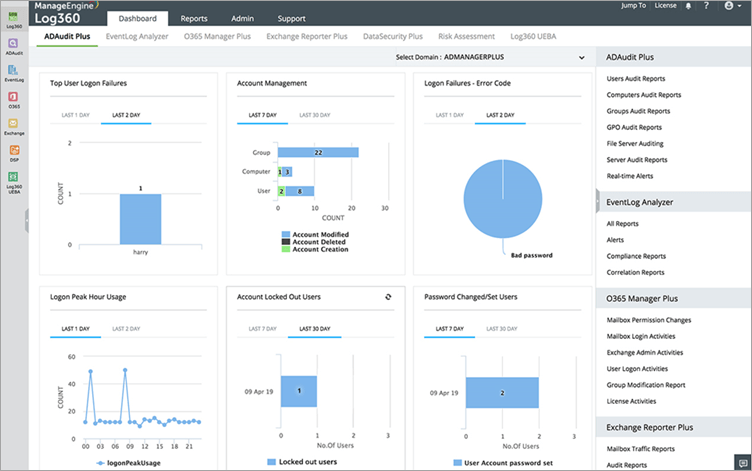
Figure 6. ManageEngine Log360 Dashboard
The main features of ManageEngine Log360 are listed below:
-
Always keep an eye out for security dangers by keeping an eye on your network devices, web servers, databases, and file servers.
-
Give users and entities risk ratings.
-
Using machine learning, evaluate threats
-
Use personalized templates to set internal security policies.
Log360 is a fantastic SIEM product for real-time network, server, and application monitoring. It is very good at managing and identifying security threats. Both virtual and real settings can use the platform. In order to help security professionals better battle threats and occurrences, it is excellent for displaying data.
Micro Focus ArcSight
It is effective at ingesting sources since it supports more than 500 different types of data analysis devices. It is accessible via the software, Amazon, Microsoft Azure, and appliances.
Micro Focus ArcSight is ideal for medium-sized, large-sized, and small enterprises.
ArcSight is available for a free trial from Micro Focus. Your costs will vary depending on how much data is consumed and how many security events are associated per second.
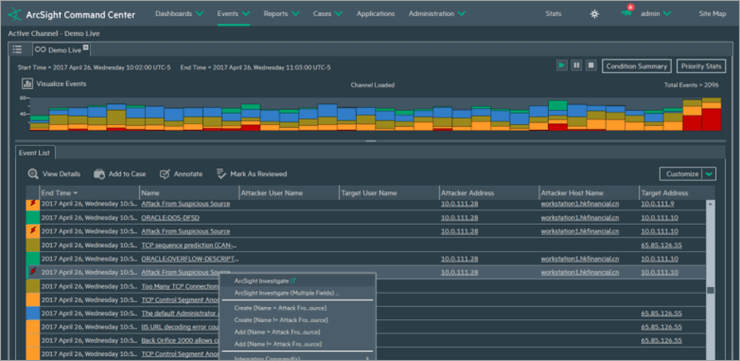
Figure 7. ArcSight Dashboard
Distributed correlation and cluster views are features of ArcSight Enterprise Security Management.
The primary features ArcSight are as follows:
-
By fusing distributed cluster technology with the SIEM correlation engine, it offers a distributed correlation.
-
It may be integrated with a variety of artificial intelligence and machine learning platforms.
-
Agents or connectors are used. More than 300 connections are supported.
Micro Focus Scalable solutions like ArcSight can handle stringent security needs. It is effective in thwarting attacks and boosting performance (100000 EPS).
IBM Security QRadar
With log data collecting, event correlation, and threat detection, the industry-leading SIEM platform IBM Security QRadar delivers security monitoring of your entire IT infrastructure.
Using threat intelligence and vulnerability databases, an integrated risk management solution, and support for interaction with antivirus, IDS/IPS, and access control systems, QRadar enables you to prioritize security warnings.
As QRadar is an extensible SOC core, it may be enhanced with new features by plugging in numerous practical programs found on the IBM Security App Exchange website.
QRadar is for medium-sized and big companies.
Price: Contact IBM Security QRadar for a price. Online reports indicate that the starting fee is $800 per month. The cost is $10,700 for the 100 EPS virtual appliance. There is a 14-day free trial period.
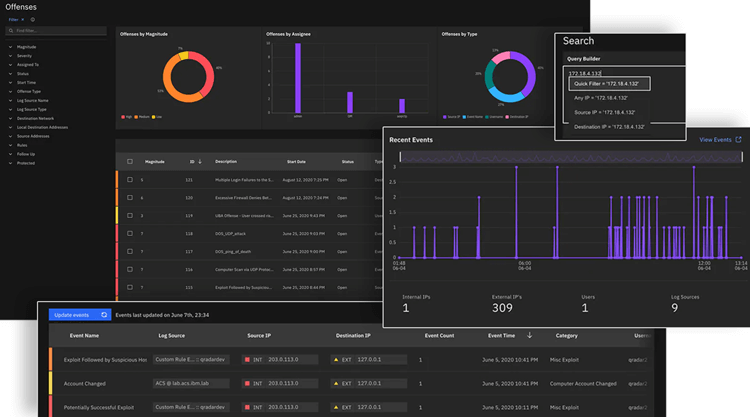
Figure 8. QRadar Dashboard
Some features of QRadar are listed below:
-
Advanced behavioral profiling technique and rule correlation engine.
-
Platform that is flexible and highly scalable, with extensive out-of-the-box functionality and presets for many use scenarios.
-
A strong community, third-party suppliers, and IBM integration environment.
IBM QRadar provides a wide range of functions for asset management, network activity, log activity, and data collecting. The browsers IE, Firefox, and Chrome are supported. It emphasizes significant situations, according to user feedback.
RSA NetWitness
RSA NetWitness Network, RSA NetWitness Endpoint, and RSA NetWitness UEBA are some of the data sources this platform employs.
It offers analysts coordination and automation tools for a conclusive answer. In order to do this, it links to the episodes over time and determines the size of an assault. It will assist analysts in eliminating dangers before they have an effect on the firm.
RSA NetWitness is ideal for big and medium-sized organizations.
Price: For more information about its cost, get a quotation. According to online evaluations, the first cost for a term license will be $857 each month. These costs are valid for typical enterprises.

Figure 9. RSA NetWitness
The major capabilities of RSA NetWitness are given below:
-
Real-time data enrichment is done using threat intelligence and business context.
-
By making security data more usable, this real-time data enrichment will assist analysts during the inquiry.
-
Using specialized algorithms, it can automatically extract threat-relevant meta-data.
-
Complete incident management is offered.
-
Due to its ability to be implemented as single or numerous appliances, on-premises or in the cloud, partially or fully virtualized, it offers flexibility in deployment.
Our platform will benefit you with unparalleled visibility, decisive reaction, and sophisticated threat identification. It uses a variety of sources to extract threat-relevant metadata into more than 200 metadata fields for comprehensive metadata.
McAfee ESM
McAfee is a well-known SIEM tool. It checks your active directory records to assure system security. Both Windows and Mac OS are supported. You will have real-time insight into system, network, database, and application activity thanks to McAfee ESM.
They include McAfee Investigator, Advanced Correlation Engine, Application Data Monitor, Enterprise Log Manager, Event Receiver, Global Threat Intelligence for Enterprise Security Manager, and Enterprise Log Search. It also offers a variety of security-related products. McAfee ESM will provide you with data that may be used.
Price: There is also a free trial period. To learn more about the cost, you may request a quotation. According to internet evaluations, the cost for VM is $39995 and the cost for equivalent hardware is $47994.
Figure 10. McAfee ESM Dashboard
Some features of McAfee ESM are listed below:
-
Notifications with a priority.
-
It will be simpler to identify and prioritize risks with powerful analytics and extensive context.
-
Data display that is dynamic. It will be information that can be used to investigate, contain, correct, and adapt to import alarms and patterns.
-
Data from a large, diverse security infrastructure will be tracked and evaluated.
-
For two-way integration, it offers open APIs.
Rapid7 Insight IDR
Rapid7's Insight IDR is a cloud-based SIEM solution. It offers an Insight Platform that is hosted in the cloud for data collecting and searching.
Risks including malware, phishing, and credentials that have been stolen can be found. It contains attributes like centralized log management, deception technology, file integrity monitoring, analytics of user and attacker activity, etc. It will do a real-time detection scan on the endpoints.
Large, medium, and small enterprises should use Rapid7 Insight IDR.
Figure 11. Rapid7 Insight IDR Dashboard
The main features of Rapid7 Insight IDR are as follows:
-
It offers analytics on attacker activity.
-
Centralized log management is present.
-
It consistently establishes healthy user activity as the baseline for user behavior analytics.
-
It utilizes Insight Agent for endpoint visibility and detection.
-
For whatever form of alert that InsightIDR creates or manages, associated tickets are automatically produced.
Cloud-based log and event management are offered by Rapid7. There won't be any continuing maintenance needed. Combining log search, user behavior, and endpoint data, will assist you in making rapid decisions that are well-informed.
PRTG
All the tools required to monitor a user's whole IT infrastructure, including all devices, traffic, apps, etc., are provided by Paessler PRTG. You may use this tool to find out how much bandwidth your hardware or software is utilizing. Also, you may use the program to monitor certain datasets using SQL queries and individually configured PTRG sensors.
The PRTG software gives customers the ability to manage all apps and get comprehensive statistics about any program that is active on your network from a single location. The technology excels at real-time server monitoring for all kinds of servers. It rates them according to their usability, dependability, and availability. PRTG is a very effective for feature-rich network monitoring.
Pricing: There is a free trial period of 30 days. Each server license for PRTG 500 costs $1799, for PRTG 1000 it costs $3399, for PRTG 2500 it costs $6899, for PRTG 5000 it costs $11999, and for PRTG XL1 it costs $15999.
Figure 12. PRTG
Some features of PRTG are listed below:
-
Use maps and dashboards to see the network.
-
Flexible warnings when issues are found.
-
Tools may be modified utilizing HTTP API and unique sensors.
-
To keep track of a wide variety of devices, use SNMP.
Paessler PRTG is undoubtedly one of the most effective systems available that satisfies the needs of companies of all sizes. The program has a ton of features, is very flexible, and is simple to use. You can see your whole network architecture using its maps and dashboards, making it easy to monitor and manage all devices, apps, and traffic, among many other things.
AlienVault Unified Security Management
AlienVault is the only platform that provides a wide range of security capabilities. Moreover, it provides tools for compliance reporting, log management, email alerts, intrusion detection, vulnerability assessment, and SIEM event correlation.
Endpoint agents and small sensors are employed. MSSPs can utilize it to customize the security services they provide.
AlienVault is ideal for enterprises of any size.
Price: AlienVault has three different price tiers: Basics ($1075), Standard ($1695), and Premium ($2595). The Essentials package is best for small IT teams, the Standard plan is best for IT security teams, and the Premium plan is best for IT security teams that want to meet specific PCI DSS audit requirements.
Figure 13. AlienVault Dashboard
The main features of AlienVault are as follows:
-
It may be utilized in a dynamic cloud environment since it features an automatic asset discovery function.
-
Threats and configuration concerns will be regularly checked for on endpoints.
-
Vulnerabilities and Amazon configuration problems are identified.
-
It will automate threat hunting, deploy more quickly, and operate more wisely.
The platform for threat detection, incident response, and compliance management is AlienVault USM (Unified Security Management). It may be set up locally, on the cloud, or in a hybrid setting. It automates threat hunting, deploys more quickly, and operates more wisely.
What is the Difference Between SIEM Tools?
The best SIEM products are contrasted below:
| SIEM | Best for | OS Platform | Deployment | Free Trial | Price |
|---|---|---|---|---|---|
| Splunk | Small, Medium, and Large businesses. | Windows, Linux, Mac, Solaris. | On-premises & SaaS | Splunk Enterprise: 60 days | Splunk Cloud: 15 days |
| SolarWinds | Small, Medium, and Large businesses. | Windows, Linux, Mac, Solaris. | On-premise & Cloud | 30 days | Starts at $4665. |
| Datadog | Small, Medium, & Large businesses. | Windows, Mac, Linux, Debian, Ubuntu, CentOS, RedHat. | On-premise and SaaS. | Available | Security Monitoring price starts at $0.20 per GB of analyzed logs per month. |
| Salesforce | Small to Large Businesses. | Windows, Mac, Linux, Android, iOS. | Cloud | 30 days | Starts at $25/user/month. |
| Log360 | Small to large businesses | Windows, Linux, Web | Cloud-Hosted and On-premise | 30 days | Quote-based |
| ArcSight | Small, Medium, and Large businesses. | Windows. | Appliance, Software, Cloud (AWS & Azure) | Available | Based on the correlation between security incidents and data consumed each second. |
| McAfee ESM | Small, Medium, and Large businesses. | Windows & Mac. | On-premises, Cloud, or Hybrid | Available | Get a quote. |
| Paessler PRTG | Small to Large Businesses | Web-based, Windows, Mac, iOS, Android. | On-premise or cloud | 30 days | Starts at $1799 per server license. |
Table 1. Differences Between SIEM solutions
What are SIEM alternatives?
Due to the high expense of acquiring and installing SIEM systems, businesses are now looking at alternative security analytics technologies and attack detection and response strategies. SIEM alternatives are as follows:
-
Platforms for event collection and analytics: Products for event collection and analytics offer both SIEM and nonsecurity use cases, as well as more straightforward cost allocation techniques. Yet, a SIEM product could not have all of its potentials.
-
Products for extended detection and response: For companies ready to commit to vendor-defined and vendor-managed threat detection and response solutions, extended detection and response(XDR) platforms provide automated hands-off capabilities inside the products.
-
Managed detection and response services: Instead of escalating security events to the clients, managed detection and response (MDR) service providers look into, validate, and react to them.
