What is Security Orchestration Automation and Response (SOAR)?
Cybercrime results in more than $4.2 billion in yearly damage, according to the FBI Internet Crime Complaint Center 2020 Internet Crime Report, and most information security teams struggle to keep up owing to limited resources and personnel. Overstretched teams have amassed various, sometimes different security solutions to limit the deluge of threats, each of which must be watched, evaluated, and prioritized.
In the continuous fight against cyber threats, it has never been more crucial for security operations teams to be equipped with the proper weapons. Security Orchestration, Automation, and Response (SOAR) solutions are quickly becoming a necessity for Security Operation Center (SOC) teams to allow more effective and efficient threat detection, triage, investigation, and remediation. Security Orchestration, Automation, and Response (SOAR) is a set of technologies that enables a Security Operation Center (SOC) to classify, analyze, and remediate threats using standardized workflows and automation in order to improve SOC efficiency.
Enterprises must have flexible and adaptable security postures and infrastructure to combat escalating cyber threats. SOAR technologies increase the value of the human-machine synergy inherent in all forms of security automation by enhancing the mix of human and machine capabilities.
SOAR platforms are intended for the following purposes:
-
Security orchestration connects and coordinates diverse tool sets, as well as defines incident analysis parameters and methods.
-
Automation initiates certain processes, activities, and triages depending on these factors, including automated procedures for situations with less risk.
-
Response speeds general and tailored reactions by letting analysts access, query, and share threat data via a single interface.
There are two primary commercial benefits to using SOAR technologies in security initiatives. First, SOAR centralizes threat visibility and intelligence. Second, it handles low-level issues concurrently to assist and scale human analysts.
This article examines what Security Orchestration, Automation, and Response (SOAR) is and how SOAR technologies help your organization develop a more rational security ecosystem and improve your effectiveness against all threats. From the advantages of SOAR to the implementation problems, we will discuss the best practices of SOAR implementation and what you should consider when selecting a SOAR solution for your business. We also compare it to the Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) principles and discuss how they are utilized to avoid cyberattacks.
What Does SOAR Mean?
Security Orchestration, Automation, and Response (SOAR) is defined by Gartner as:
"technologies that enable organizations to collect inputs monitored by the security operations team. SOAR tools allow an organization to define incident analysis and response procedures in a digital workflow format."
SOAR technologies enable a company to design incident analysis and response methods in a digital workflow format. In other words, SOAR is a security technology that enables the automated accumulation and flow of security threat data between disparate security technologies (such as firewalls, SIEM, threat intelligence platform, incident response platforms, etc.) deployed on different environments (cloud and on-premise) and enables automated responses to security threats. SOAR's purpose is to simplify security operations.
Initially, in 2015, Gartner recognized Threat and Vulnerability Management, Security Incident Response, and Security Operations Automation as the three most important SOAR capabilities.
In 2017, Gartner expanded the definition of SOAR technology to include three key components: Security Orchestration and Automation, Security Incident Response, and Threat Intelligence Platforms.
In 2022, Gartner has revised its SOAR security definition to include solutions that integrate incident response, orchestration and automation, and threat intelligence platform management capabilities on a single platform. According to Gartner's 2022 Market Guide for Security Orchestration, Automation, and Response Solutions, modern enterprises use SOAR tools to document and implement security processes, support security incident management, provide machine-based assistance to security teams, and better operationalize threat intelligence.
SOAR tools are used for a variety of security operations duties, such as:
-
To provide security analysts and operators with machine-based support
-
To optimize the operationalization of threat intelligence.
-
To facilitate incident management for security
-
To document and implement procedures
Workflows may be coordinated via integrations with other technologies and automated to accomplish desired results; some examples of a use case are as follows:
-
Threat intelligence (TI) collection, curation, and administration
-
Incident response
-
Incident triage
-
Recent use cases. Some customers are using SOAR solutions for more IT-based processes as well as in other areas, such as "low code" solutions, according to Gartner.
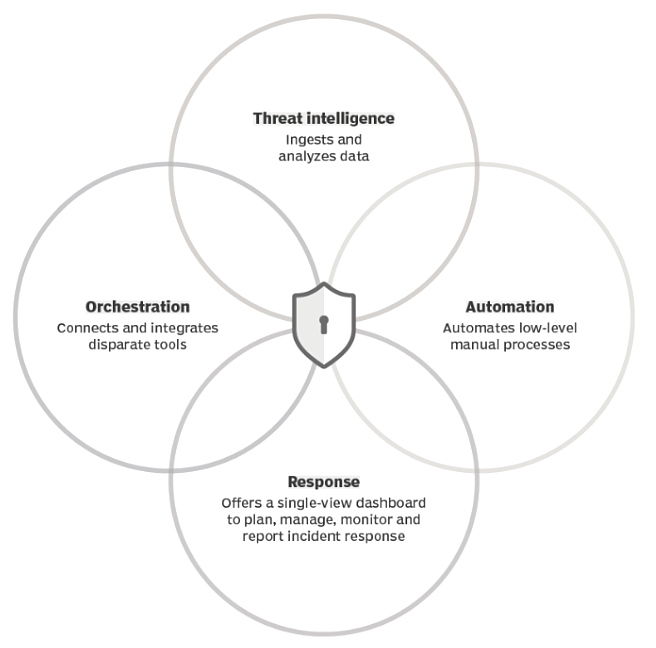
Figure 1. Elements of SOAR
Security orchestration, automation, and response are denoted by the acronym SOAR. SOAR aims to reduce the workload of IT workers by automating reactions to a range of situations. A SOAR system may also be designed to meet the specific requirements of an organization. This enables teams to determine how SOAR can achieve high-level goals, such as saving time, lowering the number of IT personnel, or freeing up existing people to work on innovative initiatives.
SOAR platforms offer a comprehensive threat management solution. An incident response plan is then adopted after identifying threats. The system is then automated as much as possible to increase its efficiency. An efficient SOAR system may be used as a beneficial tool to reduce the pressure on IT staff.
SOAR is gaining popularity as an enabling technology for managed security services, and is currently prevalent in managed detection and response (MDR) services. Its usefulness is in assisting MDR providers to identify and react to threats with greater speed and consistency, hence improving SLAs. Other major markets have seen notable convergence patterns during the last three years (for example, SSE and XDR). This will benefit enterprises that have a dedicated SOAR in place or are assessing them for the first time and want to construct complex processes.
What are the 3 Key Elements of the SOAR Solution?
The three primary components of SOAR systems are security orchestration, security automation, and security response. These key elements of SOAR are explained below:
-
Security Orchestration: Security orchestration is the machine-based coordination of a sequence of interdependent security tasks, such as incident investigation, response, and resolution, across a single complex infrastructure. Security orchestration links and combines dissimilar internal and external technologies using pre-built or bespoke integrations and application programming interfaces (APIs). Connected systems may include endpoint security solutions, end-user behavior analytics, vulnerability scanners, firewalls, security information and event management (SIEM) platforms, intrusion detection and prevention systems (IDS/IPS), and external threat intelligence feeds.
With all the data collected, there is a greater probability of spotting risks, as well as a more complete context and enhanced cooperation. The trade-off is an increase in alarms and data to consume and evaluate. Whereas security orchestration consolidates data to activate reaction functions, security automation takes action.
Security orchestration provides the following functions:
- Enhance the context around security events. A security orchestration tool compiles data from several sources to provide more insight. Thus, you have a holistic perspective on the environment as a whole.
- Permit more in-depth and relevant investigations. Instead of maintaining notifications, security analysts investigate why events are happening. In addition, security orchestration solutions often include highly dynamic and intuitive dashboards, graphs, and timelines, which are of great assistance throughout the investigation process.
- Improve collaboration. Certain sorts of security events need the participation of other parties, including analysts at various levels, managers, the CTO and C-suite executives, legal teams, and HR. Security orchestration puts all relevant information at everyone's fingertips, enhancing the efficacy of cooperation, issue solving, and resolution.
Ultimately, security orchestration improves the integration of your defenses, enabling your security team to automate complicated procedures and optimize the value of your security personnel, processes, and technologies.
-
Security Automation: Security automation is the machine-based execution of security operations that may identify, analyze, and mitigate cyber threats without requiring manual human interaction. Security automation, which is fueled by the data and alarms gathered by security orchestration, ingests and analyzes data and generates automated procedures to replace human activities. SOAR systems standardize and execute tasks formerly handled by analysts, including log analysis, vulnerability scanning, auditing, and ticket validation capabilities. SOAR automation provides suggestions and automates future reactions by using artificial intelligence (AI) and machine learning to interpret and adjust analyst findings. Alternately, automation might amplify dangers if human involvement is required.
Playbooks are predetermined, automatic activities that are either pre-built or custom-built. SOAR Playbooks are crucial to the success of SOAR. Multiple SOAR playbooks are linked together to perform complicated activities. For instance, if a malicious Uniform Resource Locator (URL) is discovered in an employee's email and recognized during a scan, a playbook may be implemented to block the email, and warn the employee of a possible phishing attempt, and block list the IP address of the sender. If required, SOAR technologies may also initiate follow-up investigations by security teams. Regarding the phishing scenario, further actions may include checking other employees' inboxes for similar emails and banning them along with their IP addresses.
-
Security Response: Once a threat is identified, security response provides analysts with a single point of view into the planning, management, monitoring, and reporting of measures taken.
It encompasses operations like case management, reporting, and threat intelligence sharing. Typically, SOAR systems link with case management and reporting solutions to guarantee that information about any attacks may be accessed in the future. Most use cyber threat intelligence services, allowing you to readily learn what other security professionals are facing and share your own experiences with the community.
Recent SOAR systems have a Threat Intelligence Management(TIM) feature, in addition to security orchestration, automation, and response. Threat intelligence management is the gathering, standardization, enrichment, and use of data regarding possible attackers' objectives, motives, and capabilities. Threat intelligence management (TIM) helps enterprises to better comprehend the global threat environment, predict the next steps of attackers, and take immediate action to prevent assaults.
How are Security Orchestration and Security Automation Different?
Even though security automation and security orchestration are sometimes used interchangeably, the two technologies fulfill vastly distinct functions:
Security orchestration enables simple information sharing, allowing many tools to react to crises as a group, even when data is dispersed over a vast network and several systems or devices:
-
A SOAR solution's strength comes in the breadth of its pre-built connectors, which accelerate and simplify the implementation of security operations use cases.
-
Multiple automated tasks are used by security orchestration to accomplish a comprehensive, complicated procedure or workflow.
Security automation decreases the time required to identify and react to recurrent occurrences and false positives, ensuring that alarms are not left unattended for extended periods:
-
Each automated playbook addresses a predetermined course of action for a recognized circumstance.
-
Allows security experts to devote their attention to strategic activities, such as investigative research.
Security automation is all about streamlining and improving the efficiency of security operations because it deals with a variety of single tasks, whereas security orchestration connects all of your security tools so that they feed into one another, thereby creating a fast and efficient workflow process from start to finish.
When both security orchestration and automation are implemented, security teams enhance their efficiency and productivity.
Why SOAR is Needed?
In an ever-expanding and more digital world, enterprises confront several cybersecurity issues today. The more complicated and malevolent the attacks, the greater the necessity for firms to build an efficient and successful future security operations strategy. SOAR is redefining how security operations teams organize, evaluate, and react to alerts and threats as a result of this requirement.
Today's Security Operations teams are entrusted with manually processing hundreds of warnings every day, allowing space for mistakes and huge operational inefficiencies, not to mention inefficient, siloed, and obsolete security systems, as well as a serious dearth of trained cybersecurity expertise.
Numerous security operations teams struggle to link the noise from various systems, resulting in an excess of error-prone manual procedures and a shortage of highly experienced staff to resolve the issue.
Due to the growing volume of threats and alerts and the lack of resources to address them all, not only are analysts forced to decide which alerts to take seriously and act on, and which ones can be ignored, but they are often so overworked that they risk missing real threats and making an egregious number of mistakes as they attempt to respond to threats and bad agents.
Automation of security operations and procedures is no longer a "nice to have" but rather a "must have". Managing many security tools and procedures manually has become not only more difficult but also wasteful and susceptible to human mistakes.
For example, manually investigating typical dangers such as phishing emails takes considerable time, which leaves room for human mistakes. Security analysts and incident responders must hop from system to system to evaluate email content for malicious attachments, phishing URLs, and suspicious requests for sensitive information. The effort required to manually obtain this data is considerable.
By enhancing efficiency, SOAR security aims to ease all of these obstacles. It offers a standardized approach for data aggregation to aid human and machine-led analysis and automates detection and response procedures to decrease alert fatigue, enabling analysts to concentrate on activities requiring deeper human analysis and intervention.
The major benefit of SOAR technologies is that they enable human analysts to scale and automate laborious and repetitive operations, allowing SOC personnel to concentrate on higher-level threats.
With security orchestration, businesses can transform complicated operations into streamlined, automated workflows.
Consider user provisioning and de-provisioning as an example. Numerous businesses use single sign-on (SSO) systems, which may significantly simplify the login process while protecting users and data. However, not all applications offer SSO, which poses a significant security risk for individuals with varying levels of access across platforms. Security orchestration provides a solid solution to this issue.
With security orchestration in place, SOCs may automate the addition or removal of users in various circumstances by using pre-built connectors with the business's applications and a custom procedure to guarantee that access is allowed only to personnel who need it.
Even better, security orchestration does not require the replacement of your existing technologies. It pulls even more value from them by including an orchestration layer to connect the dots between each tool and better notify security team members during an incident.
As a result, SOAR is being used by a growing number of organizations to enhance their cybersecurity posture.
What are the Advantages of a SOAR Solution?
Faced with developing threats, a lack of experienced security professionals and the need to manage and monitor expanding IT estates, SOAR enables enterprises of all sizes to identify and react to cyber attacks more quickly. SOAR systems provide corporate security operations (SecOps) teams with several advantages, including the following:
-
Reduced Expenses: As opposed to manually executing all threat analysis, detection, and response operations, supplementing security analysts with SOAR solutions may save expenses in many cases.
The expanding quantity and variety of risks provide organizations with considerable fiscal challenges. Each new danger necessitates the development of a unique procedure, which may require the appointment of additional personnel to handle the process. With each new type of cyber attack, an organization must devise methods for data analysis and devise mechanisms for resolving the issue. This requires time, effort, and assets. But with SOAR, every aspect of the process is simplified, and a great deal of it can be automated, saving time and money. By incorporating a SOAR platform into its business strategy, a typical company will realize substantial cost reductions:
- 30% for shift management
- 60% for analyst training
- 70% for alert management
- 80% for playbook building
- 90% for reporting
-
Improved Threat Context: Tackling increasingly complex cybersecurity threats needs a comprehensive grasp of attackers' tactics, methods, and procedures (TTPs) and the capacity to recognize indicators of compromise(IOCs). SOAR platforms provide greater context, superior analysis, and up-to-date threat data by integrating more data from a larger variety of tools and systems. This enables security staff to contextualize situations, make more educated judgments, and speed up the identification and reaction time to issues.
-
Enhance Decision-Making Skills: SOAR systems strive to be user-friendly, even for inexperienced security analysts, by providing features such as pre-built playbooks, drag-and-drop playbook creation, and automatic alert prioritizing. In addition, a SOAR tool may collect data and provide insights that make it simpler for analysts to review occurrences and take the appropriate corrective steps.
-
Rapid Identification and Response to Incidents: The number and pace of security threats and incidents continue to rise. In conjunction with automation, SOAR's enhanced data context may reduce the Mean Time to Detect (MTTD) and Mean Time to React (MTTR) (MTTR). By identifying and reacting to hazards with greater speed, their effects may be mitigated.
Enterprises may gain when problems are managed more efficiently and dangers are dealt with more promptly. The SOAR architecture enables quicker reaction times and more precise interventions. As a result of fewer errors, less time is spent repairing issues. The reduction of human error results in an overall more effective issue-management system.
-
Scalability: As the number of security events increases, scaling time-consuming manual methods may be a burden on personnel or possibly impossible to maintain. SOAR's processes, automation, and orchestration can more readily satisfy scaling requirements.
-
Simplified Administration: SOAR platforms aggregate the dashboards of several security systems into a single interface. This aids SecOps and other teams by centralizing data and information management, simplifying administration, and saving time.
-
Streamlining Processes: Standardized processes and playbooks that automate lower-level operations allow SecOps teams to react to a greater number of threats in the same amount of time. These automated procedures also guarantee that the same standard repair activities are implemented across all systems in the business.
-
Flexibility: SOAR is configured according to an organization's requirements. SOAR's architecture allows it to adapt to the requirements of the current security system. This implies it is integrated into your existing system without requiring a time-consuming or resource-intensive overhaul. SOAR gathers data from a variety of sources, including user input, machines, and emails. The IT staff then selects how the data is tracked according to what best meets the requirements of the firm.
-
Increasing Analysts' Efficiency: Automating lower-level threats augments the duties of SecOps and security operations center (SOC) teams, allowing them to prioritize activities more efficiently and react to dangers requiring human involvement more promptly.
-
Enhance Time Management and Productivity: As time is saved using the SOAR method, productivity is enhanced. People on the team who previously spent numerous hours doing tasks that have been automated by SOAR now devote their time to supporting other corporate goals. This results in more effective utilization of human resources. This results in less time spent recruiting and hiring new employees since the present workforce is more productive.
-
Collaboration and Report Writing: The reporting and analysis capabilities of SOAR systems rapidly combine information, allowing improved data management procedures and response activities to update current security policies and programs for more effective security. The consolidated dashboard of a SOAR platform increases information sharing across diverse corporate teams, hence improving communication and cooperation.
As various sorts of risks are handled by the central SOAR system, teams that would ordinarily handle them individually may cooperate in determining the optimal SOAR configurations and automation. This results in a more consistent set of procedures and provides IT teams the ability to cooperate on new solutions.
Automating reporting makes life simpler, but it also removes the need for manually generated metrics. By enabling SOC personnel to extract data on demand, ideally with a single click, or on a predetermined schedule, organizations get accurate and timely metrics for each reporting period. Most SOAR programs feature reporting templates and the option to build custom reports to further ease this process.
-
Communication Standards During Incident Response: Managing and responding to issues may require looking outside the SOC, particularly for severe occurrences. This implies that incident response teams might comprise stakeholders from both within and outside the SOC, making it difficult to develop a reliable and repeatable information flow.
To overcome this difficulty, businesses often establish a mission control center to manage high-priority situations. A strong SOAR platform includes a virtual war room to guarantee that important communication is standardized, preventing any team member, from PR and HR to legal and the C-suite, from losing vital information during an incident response.
-
Automated Patch Management by Reducing Human Error: Patch management is vital for system maintenance. Unfortunately, the monotony of this work causes security personnel to ignore it often. The organization faces severe risks if fixes are not applied. SOAR technologies assist security teams in properly handling updates. SOAR platforms automatically deploy fixes and monitor key systems without human interaction. Organizations coordinate this with other change management processes by integrating the SOAR platform with their configuration management system.
How Do You Implement SOAR?
A SOAR platform is not the software you can just purchase and install; it must be customized for your environment. Because of this, you should investigate the level of vendor support that comes with any potential solutions. However, you need to adapt your security operations to the new processes and capabilities a SOAR system would provide. Here, security professionals with expertise in this area guide how to tackle SOAR implementation.
-
Ensure your tools have the necessary API connections. Although certain SOAR systems offer built-in pre-written connections for common tools, they are not ubiquitous, and you will likely want to integrate custom-built tools as well. This is where API connections come in, and creating a library of tools that need to utilize is a crucial step. Consider the methods that would be used to conduct audits, alerts, and corrective actions inside the systems, and verify that any API interfaces you uncover are useable or developable and accomplish the precise tasks you need.
You may discover that you must develop these API connections on your own; most suppliers provide integration frameworks that enable you to do so. You can also develop daemons that enhance SecOps productively. There are no limitations on the sorts of daemons that may be created, such as new IoCs in threat intelligence systems or higher-risk SIEM alerts.
-
Before automating your incident response procedures, you should first map them out. Since automation is one of the primary value propositions of SOAR platforms, many businesses that deploy them hurry to automate. However, this is a grave error. The addition of automation to an inefficient operation would exacerbate its inefficiency.
Before creating playbooks based on your processes, use the opportunity afforded by the shift to SOAR to assess and justify them. Many providers offer pre-written playbooks, which you may find to be an upgrade over your present procedures. This is a great way for your team to get started, and you can modify it as you find what works best for your SOC.
-
Ensure that your internal abilities are compatible with the chosen platform. Each SOAR solution takes a somewhat different approach, with some designed for highly trained analysts and others for consumers of various skill levels. Some SOAR products, for example, demand the ability to write Python or Ruby scripts to integrate security technologies and develop playbooks.
It is recommended to inquire whether your selected platform provides both a graphical user interface and a scripting module, such as an integrated development environment. The GUI may enable non-programmers to immediately make use of the SOAR solution's benefits, perhaps via basic drag-and-drop features, while the IDE enables coders to do more complex modifications as needed.
-
Prepare for your SOAR implementation to change over time. Remember that your trip with SOAR is, in fact, a journey: you'll learn as you go how to best adapt it to your requirements, as well as what works and what doesn't. It's hard to do everything perfectly the first time. Even if you spend a great deal of time and effort developing an incident response plan, there's a good chance it won't be perfect.
Moreover, you are well aware that the threat environment is ever-changing and that your SOAR playbooks will need regular modification to address new threats. Cyber threat approaches, strategies, and processes evolve with time. Consequently, you must adjust and execute the necessary modifications. After processes have been codified using a SOAR solution, analysts must continue to monitor, evaluate, and modify them to ensure that each playbook continues to operate at peak efficiency and performance. SOAR systems that enable you to perform tests and warning scenarios on your playbooks facilitate continuous development. If everything goes well, your SOAR platform will have increased the efficiency of your SOC and provided your analysts with the time they need to think creatively, rather than just putting out fires all day.
-
Introduce automation gradually. When analyzing your present processes, you want to consider whether they should be automated immediately or ever. Even the most challenging and malevolent scenarios need the hands-on, critical thinking that only a security analyst can deliver. Consequently, the objective of any SOAR deployment is to determine the optimal balance of machine-driven and analyst-driven operations for a given SOC. Identify procedures that are excellent candidates for automation and implement SOAR in those areas initially if you are just starting. You next choose how to continue with the automated section of your trip.
What are the Challenges of SOAR Implementation?
According to Gartner, the primary barrier to the implementation of SOAR security is the absence or immaturity of protocols and procedures within SOC teams. SOAR is not a stand-alone cybersecurity solution. SOAR platforms should be included in a defense-in-depth security strategy, given that they rely on the input of other security systems to identify threats.
SOAR is not a substitute for other security measures; instead, it is a supplementary technology. SOAR systems do not replace human analysts, but rather supplement their abilities and processes for enhanced incident detection and response.
Other disadvantages and challenges of a SOAR implementation are as follows:
-
Unrealistic Expectations: SOAR is not a panacea for resolving all security issues. It is crucial to avoid depending just on the playbooks and procedures that were first configured in SOAR. Companies must use current security knowledge to guarantee that their SOAR is always prepared to react successfully to new sorts of attacks.
-
Undefined Metrics: Organizations run the risk of not achieving the desired outcomes from SOAR owing to a lack of properly defined success criteria. It is essential to comprehend the scope of what they are attempting to automate.
-
Inability to repair a larger security plan
-
High complexity in deployment and maintenance
-
Inability to assess broader security maturity or integrate it into strategy
-
Failure to address the security culture
-
Undervaluing of human analysts in favor of software
-
Redirection of staff resources to technology resources
-
Potentially mistaken conflation with AI
What are SOAR's Use Cases?
Some of the SOAR use case scenarios that boost SOC security analyst capabilities are examined below:
-
Vulnerability Management: Historically, SOC analysts have depended on manual vulnerability management and inventory. Nonetheless, by utilizing SOAR, several SOC functions are automated to manage volume, monitoring, and easy replies. In particular, SOAR integrates data on threats across several security technologies to measure risk and correspondingly rank the threat.
-
Automatic Enrichment for Correction: SOAR systems expedite the IOC enrichment procedure by accessing several enrichment databases or numerous threat intelligence resources for context. This allows SOC analysts to sift, validate, triage, and react with more precision and efficiency. This SOAR use case saves analysts a substantial amount of time by swiftly enriching vast quantities of IPs, URLs, and hashes to check for malicious intent without sacrificing the required depth of investigation.
-
Case Management: Multiple instruments may identify potential hazards. Analysts thus spend considerable effort sifting through diverse data linked with the same danger. SOAR in the SOC aggregates all data into a unified narrative. This expedites the handling of instances and reduces overall mean timeframes to identify and react, whether via automation or human analysis and action.
-
Threat Hunting: In addition to ingestion and enrichment, the detection of IOCs by SOAR platforms effectively functions as a sort of proactive threat hunting. Detecting risks is a critical duty for human analysts, but it is a time-consuming one due to the expanding breadth of threats. SOAR assists with monotony and scale by incorporating data sets for continuous analysis. In addition, SOAR aids in the breadth of threat hunting by searching for malware or suspicious sites and incorporates human decision-making at crucial times.
-
Threat Intelligence Cooperation: Every day, SOAR systems consume millions of indicators of compromise (IOC). Internal and external threat intelligence feeds, network detection and response(NDR) tools, endpoint detection and response(EDR) platforms, malware analysis tools, SIEM systems, RSS feeds, email inboxes, regulatory agencies, and other databases are mined for indicators of compromise(IOC). SOAR systems coordinate, collect, and expose warnings from these technologies, in addition to identifying suspicious IOCs that develop across them.
-
Incident Response: Automating incident cleanup and response procedures are designed to tackle hazards upstream to reduce downstream expenditures. SOAR in the SOC handles remediation and response for a variety of prevalent security threats, including malware, denial of service, phishing, and ransomware.
Depending on the nature of the danger, automated responses take a variety of forms, including the following:
- Auto-quarantining indicators or compromised endpoints
- Auto-generating tickets
- Auto-adding indicators to watch lists
- Auto-triggering an antivirus scan or security compliance check
- Auto-blocking malicious indicators
- Auto-terminating user accounts
- Auto-deleting suspicious emails from other mailboxes
- Auto-blocking a suspicious email or IP address
The coordination of threat information across enormous security topologies is one of the advantages of SOAR, allowing human analysts to concentrate on more complex threats and supporting the complete lifespan of threat intelligence. From ingestion and enrichment to detection, triage, response, and containment, SOAR in the SOC is essential for acquiring additional supervision and context, from ingestion and enrichment to detection, triage, reaction, and containment.
SOAR is beneficial not just for automating but also for improving security playbooks; it enhances not only the analysts' experience but also the SOC team's capacity to communicate throughout the enterprise. Implementing SOAR use cases may enhance the basis of an enterprise's security posture if they are implemented correctly and cultural and industry factors are considered.
What are the Best SOAR Solutions?
The market guide for SOAR by Gartner includes a list of representative suppliers and the top SOAR platforms offered by those vendors, including the following:
-
Anomali ThreatStream
-
Cyware Virtual Cyber Fusion Center
-
FireEye Helix
-
Fortinet FortiSOAR
-
IBM Security Resilient
-
LogicHub SOAR+
-
Micro Focus ArcSight SOAR
-
Palo Alto Networks Cortex XSOAR
-
Rapid7 InsightConnect
-
Siemplify SOAR Platform
-
Splunk SOAR
-
Swimlane SOAR
-
ThreatConnect SOAR Platform
-
ThreatQuotient ThreatQ
What are the Best Practices for Selecting a SOAR Tool?
Before making a selection, there are several aspects to consider while evaluating various SOAR service providers. The decision-making process of the buyer is highly impacted by the elements and services that follow the core technology. Before deploying any SOAR solution, businesses should evaluate their maturity, their current procedures, the required technological integrations and tool stack, and their preferred deployment technique.
After conducting an internal audit of its security, a firm must next analyze the SOAR product's specific aspects. Considerations for choosing a SOAR platform are as follows:
-
Bespoke Integration Capabilities: Does the onboarding time for the platform include bespoke integration assistance from the services team? Does the platform provide a method, such as an internal SDK, ticketing systems,, and collaboration tools, for constructing custom integrations? Are these services extra or included in the price of the product?
-
Case and Incident Management: Does the platform provide native case management or interface with appropriate case management tools? Does the platform permit incident-after documentation and review? Does the platform generate audit trails to demonstrate data movement and preserve accountability? Does the platform support incident timeline reconstruction?
-
Ease of Use and Interoperability with Other Tools: A security orchestration tool should serve as a link between detection, enrichment, response, and associated products.
Organizations should strive for a future state in which the SOAR tool consumes alerts from the detection tools they presently use and runs playbooks that coordinate activities across enrichment, response, and allied technologies. Does the platform support a broad selection of security products across many current point solution marketplaces (for example, endpoint, firewalls, intrusion detection and prevention systems (IDS/IPS), SIEM, secure email gateways, SSE and vulnerability assessment technologies). How many orders or actions may be carried out from the platform? Can the integrations address the following areas of concentration? These consist of:
- Data enrichment and feeds of threat intelligence
- Detection and surveillance
- Arrangement and mapping
- Compliance and responsiveness
-
Incorporation of Threat Intelligence: Threat intelligence is knowledge based on evidence, encompassing context, processes, indications, repercussions, and actionable recommendations regarding a current or emerging danger or risk to assets. SOAR systems that integrate threat intelligence leverage the information acquired to assist SOC teams in making educated judgments on the effect of external threats on the environment. The ability to link external threat intelligence to network issues accelerates incident investigations, perhaps revealing previously unnoticed malicious behavior. Automated processes allow for the scalable, real-time delivery of pertinent threat intelligence to enforcement locations. Does the platform support the ingestion of a broad range of threat intelligence sources and formats from third-party sources, including open-source, industry, and government (information sharing and analysis centers [ISACs] and computer emergency response teams [CERTs]), and commercial suppliers?
-
Pre-built/Out-of-the-box (OOTB) Integrations: How many integrations (category breadth and category depth) does the platform have? Are new integrations continually introduced to the platform? What is the frequency? Are these updates free, or are they optional extras?
-
Implementation Adaptability: The technologies used by businesses to perform their operations and safeguard their data are always evolving and changing. With all of these moving parts, agility and scalability are vital when selecting a security orchestration tool. These characteristics rely greatly on the flexibility of deployment choices and how well they connect with other products and organizational needs.
What type of deployment flexibility does the platform offer? Does the platform have the capability to be deployed on-premises or in the cloud (like SaaS)? Does the platform provide horizontal scalability across different tenants and a degree of high availability that is guaranteed? Is the platform intended for multitenancy and does it allow network segmentation for communication across corporate networks?
-
Workflow and Playbook Capabilities: Does the platform support workflow and playbooks? Does the platform enable playbook nesting? Does the platform display playbooks for each occurrence in real time? Does the platform facilitate task transfer across playbooks? Does the platform permit the manual and automatic construction of custom playbook tasks?
-
Pricing: Before picking a security orchestration platform, consider the price model that best complements your entire budgeting procedure. The following are the popular pricing techniques on the market today:
- Annual membership with supplemental fees for extra administrator users
- Pricing per node or endpoint
- Pricing based on automation or actions
-
Additional Services: In addition to the core SOAR skills, what additional unique resources do the firm provide that might be advantageous to your organization?
-
Post-sales Support: What type of post-installation assistance does the firm offer? Does the firm provide the assistance you and your organization require?
-
Providing Expert Services: Does the organization provide consumers with expert services to ensure a smooth implementation from beginning to end?
Finding the optimal SOAR solution for any security operations demands congruence between the vendor's offers and the SOC organization's desire to increase efficiency and effectiveness. The ideal SOAR solution should not only complement and be compatible with the existing products, playbooks, and procedures, but it should also maximize collaboration, provide deployment and hosting flexibility, and have a pricing model that corresponds with the organization's goals.
What is the Difference Between SOAR and SIEM?
Many consider SOAR and SIEM to be comparable tools since both of them identify security vulnerabilities and gather data indicating the nature of the issue. In addition, they manage alerts that security staff might utilize to remedy issues. However, they vary significantly from one another.
Even though both the SOAR and SIEM systems collect data from different sources, the phrases are not interchangeable. SIEM systems gather data, recognize anomalies, rank dangers, and create alerts. These jobs are also done by SOAR systems, although they have extra capabilities. First, SOAR systems interface with a greater variety of internal and external security and nonsecurity applications. For instance, SOAR will include information from external emerging threat intelligence feeds, endpoint security software, and other third-party sources to get a more complete view of the network's internal and external security environment. This makes SOAR a more thorough aggregation solution since it collects data from multiple sources, which helps to unify your network security response.
Second, while SIEM systems just inform security analysts of a possible occurrence, the administrator is then responsible for determining the course of an inquiry. SOAR platforms leverage automation, artificial intelligence, and machine learning to give deeper context and automatic solutions to these risks. A SOAR that automates investigation route operations may drastically reduce the time necessary to manage alarms. It also teaches the security administrator skills necessary to finish an investigative route. Ultimately, a well-integrated SOAR may increase the efficiency of your cybersecurity staff. Even though SIEM allows alarms to be sorted and classified, human inquiry is required. The automation of SOAR removes this step and decreases the time required to process alarms.
Frequently, security workers use both a SOAR tool and a SIEM tool. The two systems are complementary and may function in tandem to enhance your security operations as a whole.
The SIEM system gathers and compares logs to determine which ones constitute an alarm. It is developed with a log repository and analysis features that are not present in SOAR systems.
When a SOAR platform is used in conjunction with a SIEM platform, the SOAR may receive data from the SIEM and take the lead on resolutions. The SOAR acts as a hub for security professionals to acquire context and respond to alarms.
Without a SOAR, security personnel is required to employ many interfaces outside a SIEM. With SOAR and SIEM, security teams operate more effectively by depending on the platforms to indicate which warnings need additional investigation and resolution.
Numerous businesses employ SOAR services to supplement their in-house SIEM software. A significant number of SIEM manufacturers include SOAR features in their SIEM solutions. SOAR features are also being implemented into other products, such as email security gateways, endpoint detection and response (EDR), network detection and response (NDR), and extended detection and response (XDR).
What is a Benefit to an Organization of using SOAR as part of the SIEM system?
SOAR and SIEM (Safety Information and Event Management) systems try to solve the same issue: the abundance of security-related data and events inside organizations.
While SOAR platforms include data gathering, case management, standardization, workflow, and analysis, SIEMs examine log data from various IT systems to identify security risks and notify engineers.
SIEM systems are utilized for data gathering and filtering, threat detection, and categorization, as well as threat investigation and analysis. SOAR technology performs the same functions as SIEMs, with the addition of automation. SOAR combines threat intelligence with incident investigation automation. SOAR also reacts to events using playbook-based reaction routines.
The two systems may function in tandem, with the SIEM identifying possible security issues and generating alerts and the SOAR solution reacting to these warnings, triaging the data, and performing any required remedial measures. SOAR may bring substantial value to a current SIEM solution when SIEM platforms include SOAR-like capability to improve responsiveness.
What is the Difference Between SOAR and XDR?
Extended Detection and Response (XDR) is the next advancement in endpoint detection and response (EDR). XDR provides a comprehensive approach to threat detection and response, streamlining security data input, analysis, and prevention and repair procedures across a company's complete security stack. With a single dashboard to monitor and act on threat data, XDR allows security teams to detect hidden and sophisticated threats with ease and automate even complicated, multistep responses across security technology stacks.
XDR solutions have the following capabilities:
-
Prioritize data and provide security teams with insights in a standardized style through a single interface.
-
Automate the collection, correlation, and analysis of data from endpoints, cloud workloads, networks, and email using artificial intelligence (AI) instrumentation.
-
When purchasing as a managed service, access to seasoned professionals in threat hunting, threat intelligence, and analytics may be included.
-
Coordinate disparate security tools, integrating and expediting security analysis, investigation, and remediation inside a centralized console.
As a consequence of these features, XDR significantly enhances threat visibility, decreases total cost of ownership (TCO), accelerates security operations, and alleviates the perpetual security manpower load.
XDR has emerged to fill the hole left by SIEM and SOAR using a methodology based on endpoint data and optimization. The powerful analytical capabilities of XDR allow the company to concentrate on incidents of the greatest importance and to react swiftly.
While XDR provides enterprises with additional security capabilities and increased protection, it cannot replace SIEM and SOAR entirely. SOAR provides essential orchestration features that assist the security team in optimizing resources and establishing activity priorities. It is essential to retain the SOAR system and connect it with the XDR solution, since XDR solutions often lack these features.