Web Filtering: Types, Benefits, Challenges and Importance
We can all agree that allowing our most valuable treasure, our children, to walk freely on a haunted street is quite risky. This holds true in the digital world as well. Our children and teenagers may expose themselves to perils in the virtual world, which has grown more hazardous than the real world.
Of course, no one is opposed to their unrestricted exploration of the world, but keeping kids out of dangerous areas is one of our most critical responsibilities as adults if their safety is at issue.
When it comes to providing security in the internet world, one of the first techniques that come to mind as a solution will be the filtering of web content.
The term "Web filtering" means managing users' web access by allowing them to choose which websites they may visit, what information they can view, and which things they can download.
This article will provide an overview of web content filtering solutions, define the various content filtering methods, and underline the necessity of blocking certain websites.
What is Web Filtering?
One technology that makes it feasible to keep an eye on the websites that employees in a business setting visit is a web filter. It is employed to restrict the websites that an end user may visit. Web filters ensure that workers use the internet securely and effectively by blocking or granting access to particular websites or information based on predetermined criteria. To determine whether or not to display the material, it compares it to a set of rules together with its source.
By putting in place a web filtering strategy, a business may prevent internet materials, including viruses, malware, and anything that is considered inappropriate for the workplace.
A web filtering system may include many other functions in addition to its main filtering function. Notable characteristics include the ability to report on traffic, soft blocking that can show warnings before denying access, and an override feature that lets administrators unclog web pages.
Why is Web Filtering Important?
The benefits of web filtering for home usage are rather obvious and will be primarily for the protection of young children. Web content filtering systems, whether hardware or software, are critical for limiting access to undesired web information. Adult sites, malware-infected sites, and sites that may be disruptive to employees or students are examples of undesirable material.
However, while the benefits to the firm may not be as visible, they are far more numerous. Some of the most risks to any organization include hacking, phishing, viruses, and malware. Phishing, for example, is when hackers steal sensitive information via deception, such as tricking employees into logging in to bogus firms in order to obtain login credentials. Without a doubt, the loss or corruption of sensitive data such as login credentials, personal information, accounting information, and legal papers may be disastrous to any business. As a result, content filtering measures are essential. Web filtering provides several advantages for both individual users and businesses.
-
Protection against malware: Malware is, of course, one of the most serious hazards to the organization. Viruses and other types of threats may infiltrate a company's network in a variety of ways, which is one of the key reasons why firms choose to limit internet access. Web filters are capable of detecting malware and blocking access before any download is completed. Exploit kits contain malware that is particularly designed to exploit web browser vulnerabilities via browser extensions and plugins. Unknowingly, a user will visit a malicious URL that contains an exploit kit that, if abused, activates a malware download.
-
Staff productivity has increased: Social networking is a known productivity drain, since it is distracting, consumes large amounts of essential work time, and leads to decreased production. Restricting access has been shown to dramatically enhance productivity. Some sectors, on the other hand, demand social media savvy for day-to-day operations. In these businesses, a separate group of sites, such as online shopping and streaming sites, become productivity drains. There is no excuse for the staff to be watching movies when they should be working. In addition to limiting access to distracting websites, it is critical to evaluate additional channels that may represent a concern, such as downloading dubious files, reading suspicious emails, and responding to unverified contacts.
-
The efficiency of network bandwidth: Non-work-related internet activity consumes a substantial amount of network capacity. By restricting access to certain sites, you boost network bandwidth efficiency and obtain speedier connections. To achieve network bandwidth efficiency, you may educate your staff on the benefits of a continuously fast network or impose limitations on video streaming sites like YouTube.
-
To Assist With IT Policy Implementation: Too many business IT policies are essentially paperwork that lies in a drawer someplace, only to be glanced over by new workers on their first day of work, and then mostly forgotten by everyone else. The second usual situation is that the IT policy is stashed away someplace on the company's intranet, where it goes mainly unread and unheeded by 90% of the workforce. This is a challenging fact for businesses to confront, and teaching people about the perils of phishing and surfing suspicious websites may be difficult. However, by utilizing web filtering, the organization may get more control over how employees use the internet, therefore preventing a lot of malpractice before it occurs.
-
CIPA (The Children's Internet Protection Act ) Compliance: To be in compliance with CIPA, the protections that schools put in place must restrict or filter Internet access to images that are vulgar, include pornography, or are detrimental to kids (for computers that are accessed by minors).
CIPA-eligible schools must meet two extra certification requirements:
- Minors' online activity must be monitored as part of their Internet safety regulations.
- They must include provisions for educating children about proper online conduct, such as engaging with other people on social networking sites and in chat rooms, as well as cyberbullying awareness and reaction.
What Are the Benefits of Web Filtering?
Beyond only improving internet security, web filtering improves overall corporate efficiency and compliance. The main advantages of putting web filtering into practice inside a company are examined here.
-
Cutting Down on Malware Infection: By restricting access to known catastrophic sites, you may protect your data and users before malicious payloads are deployed. Web filtering lowers endpoint maintenance and virus alerts.
Present-day URL filtering technology successfully stops malicious apps. In addition to banning domains, firewalls equipped with online URL filtering systems may also scan web pages for threats.
-
Improved security: By preventing access to harmful websites and material, web filtering dramatically lowers the risk of cyber threats like malware, ransomware, and phishing assaults, safeguarding critical corporate data and infrastructure.
-
Keeping Children Safe from Unwanted Content: The primary benefit of URL content cleaning is that it shields young people from violent and obscene content. In the fast-paced world of today, parents cannot always be there to keep an eye on their kids' content or be aware of all the websites that need to be blocked. Without resorting to user or administrator policies, URL filtering in a firewall provides complete control over what is available.
-
Defense Against Exploit Kits: Hackers are coming up with new ways to get in as network security gets better. Through browser extensions and plugins, exploit kits take advantage of vulnerabilities in online browsers.
An attack kit that takes advantage of flaws in the operating system or browser may be released when malicious websites are mistakenly visited. Attackers may download malware, take over sessions and passwords, and more thanks to vulnerabilities. Content filters are able to stop payload downloads and identify exploit kits.
-
Increasing Employee Output: Social networking is a huge productivity killer and time waster. Productivity is increased by restriction, and social media knowledge is necessary in many industries. Sites for streaming and online shopping reduce productivity in these sectors. Employees have no justification for watching movies while at work. Avoid downloading harmful files, reading odd emails, and replying to contacts you don't know, in addition to blocking distracting websites.
-
Efficiency of Network Bandwidth: Network capacity is depleted by non-work-related internet activity. Restricting certain websites increases network performance and bandwidth efficiency. You might limit bandwidth-hungry video streaming services like YouTube or train your staff on the advantages of a consistently fast network to attain network bandwidth efficiency.
-
Adherence to Regulations: Internet-related accidents can be avoided by keeping an eye on employees' web activity. Liability may arise from posting offensive, racist, or abusive speech on blogs or social media, engaging in cyberbullying, or downloading work that is protected by copyright. Given how divisive the world is becoming, you must always protect your company and brand by exercising caution over the information that you and your employees send or allow to enter.
What are Web Filtering Types?
A web filtering service can function in a number of ways. One way web filtering solutions might be distinguished is by how they define permitted material. There are several techniques to define web filters, including:
- DNS Filtering
- IP Filtering
- URL Filtering
- Content Filtering
- Keyword Filtering
- Category Filtering
- Search Engine Filters
- Application-Level Filtering
1. DNS Filtering
DNS One method that filters internet traffic at the DNS level is called Domain Name System (DNS) filtering. By rerouting or blocking requests to their corresponding Internet Protocol (IP) address, it prevents access to particular websites or content. It functions as the phone book of the Internet, converting domains like google.com into IP addresses that computers use to route traffic. DNS filtering keeps an eye on DNS lookup requests and, depending on the policy, either blocks or permits traffic.
2. IP Filtering
Filtering and banning IP addresses that can be a hazard to your business is known as IP address filtering. Almost anything that is linked to the internet, including computers, routers, servers, and websites, is given a numerical identification known as an IP address. A technique called IP address filtering decides how to handle network data packets according to their source or destination address. Any IP address, including those of websites and internet-connected appliances, can be filtered. In either scenario, a network router or firewall examines the packet before forwarding it to the subsequent node on the network in accordance with administrator-established rules. The packet is just disregarded if the rules state that packets with a certain address shouldn't be passed on. This indicates that it is not spread over the existing network path. Given that Internet communication can take several routes to reach its destination, it might still be transmitted via a different network route.
3. URL Filtering
In essence, a URL is the webpage's address. A method called URL filtering uses a website's URL to determine whether to grant or deny access. This type of filtering organizes websites into categories including social networking, entertainment, adult material, and more, as covered under URL classification. Organizations may streamline web access control by implementing policies that allow or prohibit access to whole categories.
The basic idea behind URL filtering is simple. It makes use of an up-to-date database of URLs that have been sorted according to their content. The URL filtering system compares the URL to this database whenever a user tries to access a website. Access is banned if the website belongs to a forbidden category (such as social networking, gambling, or adult material).
In settings like workplaces and schools where access to particular types of websites must be rigorously regulated, URL filtering works especially well. It serves as a first line of protection against websites that are obviously detrimental to productivity or that are known to hold hazardous information.
Keeping the database up to date is the biggest obstacle when it comes to URL filtering. Every day, new websites are created, and the content of old ones may change. Another issue is over blocking, which occurs when trustworthy websites are blocked because they share a domain with content that is forbidden.
4. Content Filtering
The most sophisticated kind of web filtering is content filtering, which examines a webpage's content in its whole context rather than simply its URLs or certain keywords. It makes use of complex algorithms and occasionally artificial intelligence to determine the appropriateness and meaning of information in real time. Using content analysis, content filtering assesses a webpage's text, photos, videos, and other media to find and remove offensive or dangerous information. Because it may restrict particular pages or aspects inside a website rather than the entire website, it's particularly helpful for enterprises wishing to impose comprehensive regulations on web content.
5. Keyword Filtering
Depending on whether certain keywords are included in the website's content or URL, web filtering systems can either grant or deny access to a website. It is possible to identify particular keywords or phrases by scanning the HTML elements, metadata, and content of online pages. This gives online filtering alternatives a competitive advantage by enabling them to proactively detect information that needs to be filtered. This method assists in identifying offensive or unsuitable information that the classification process might miss.
Keyword filtering looks for certain prohibited words or phrases in a webpage's content. A webpage is prohibited or marked if it includes one or more of these keywords. This approach is more flexible in reacting to fresh content since it does not rely on a predetermined set of URLs.
This method works well for monitoring or restricting certain kinds of information, such as hate speech, violence, or pornographic content, that can be recognized by specific terms. Additionally, it works well in more dynamic settings where new websites are often appearing and information can change quickly.
Keyword filtering's accuracy may be both a strength and a weakness. On the one hand, it is capable of efficiently identifying improper content. However, it can result in false positives, which block harmless or even required information because it contains an out-of-context term.
6. Category Filtering
While some people use "directed category" as a synonym for "filtered category," in category theory, "filtered categories" refer to a generalization of the concept of "directed set" as a category.
Using URL classification, the category filtering regulates website access.
More detailed filtering is made possible by the dialog's listing of the primary categories, each of which expands to reveal related subcategories.
Depending on your business requirements, you may add as many categories and subcategories as you like when you set up category filters. For instance, you may choose and include these subcategories in your category filter if you wish to identify and ban online content associated with alcohol and tobacco. For the category filter to be effective, you must next assign the Block action and add the category filter to a security policy.
You can choose Allow, Block, or Schedule after choosing a parent category or one of its subcategories.
Although you may change each sub-category as needed, when you choose an action for a parent category, the option is immediately applied to all of its children.
7. Search Engine Filters
Filters for search engines filter out inappropriate content from the results a user gets while using a search engine to look up information. This function is included in the user interface of several search engines. Safe Search options are available on Google and Bing for people who want to filter out inappropriate information in search results.
Both of these search engines have Safe Search enabled by default, however, these filters may be disabled without requiring administrator access.
Search engine filters may also be readily bypassed if the user knows the URL of the site they are attempting to visit or if they use a different search engine that does not have a comparable filter.
8. Application-Level Filtering
To control the usage of web-based apps and services, application filtering goes beyond standard web pages. This category restricts access depending on the kind of application rather than online content, targeting certain apps such as cloud storage providers, email clients, and instant messaging networks. It's especially pertinent in today's workplaces, where internet resources and cloud services are essential to day-to-day operations. Application filtering improves security and productivity by limiting the use of unapproved or distracting applications by enabling companies to prohibit or permit usage depending on the application's relevance to work.
You may examine the content of emails, web pages, or messages using email filters, web filters, or messaging filters and decide whether to allow or prohibit them based on certain standards, such as keywords or categories.
What Are the Challenges of Implementing Web Filtering?
Although putting web filtering into practice is crucial for corporate security and productivity, there are a number of issues that must be carefully considered. It is essential to strike the correct balance between strict security protocols and a satisfying user experience. Below, we examine typical online filtering obstacles and the factors to take into account in order to successfully overcome them.
- False positives: These happen when trustworthy websites are inadvertently blacklisted, which may impair worker productivity and information access. This emphasizes how crucial it is to optimize filtering algorithms in order to reduce mistakes.
- Possible effect on user experience: Excessively stringent web filtering may cause annoyance and lower staff morale. Businesses must make sure that their web filtering rules are both sensible enough to not negatively impact everyday operations and effective in reducing risks.
- Regular changes are necessary: Because of the ever-changing nature of digital dangers, web filtering technologies must be updated often in order to identify and stop emerging risks. This makes it necessary to maintain and update filtering criteria proactively in order to stay up to date with new security threats.
How to Set Up Web Filtering for a Business?
Depending on the architecture and needs of an organization, there are several ways to implement web filtering systems.
On-premises deployment is a popular strategy in which the web filtering program is locally deployed on the servers or hardware devices owned by the business. Although it necessitates local management and upkeep, this alternative offers greater control and customization.
The provider hosts and provides cloud-based web filtering solutions as a service, which removes the need for local hardware and streamlines deployment and upgrades.
Hybrid web filtering, which blends cloud-based and on-premises elements, enables organizations to use the advantages of both models, including scalability and local control.
Additionally, web filtering may be included in already-existing security systems such as secure web gateways, firewalls, or proxies, offering a centralized platform for threat protection and online access policy management.
Furthermore, following a set of best practices that improve web filtering's effectiveness and alignment with the organization's changing needs is essential to its successful implementation.
-
Regular policy reviews: By keeping web filtering rules up to date and efficient in meeting organizational needs and internet usage patterns, regular policy reviews provide an adaptable security posture.
-
User education: By empowering users to understand the justification for web filtering regulations and safe online habits, a company may foster a culture of security awareness.
-
Integration with other cybersecurity measures: To offer a multi-layered defense against online threats, web filtering should be a component of an all-encompassing security strategy that collaborates with other cybersecurity measures.
Can Web Filtering Be Bypassed?
Yes. It is possible to get around web filtering. Web filters are great tools for keeping children and staff from visiting unsuitable and dangerous websites. Tech-savvy individuals have found more intricate and inventive ways to get around local security regulations over time. The ways to to get around web filters are listed below.
-
DNS-Over-HTTPS: A technology called DNS-Over-HTTPS (DoH) encrypts DNS queries, preventing network-level filters from detecting the URL that is accessed. The information required for network-level web filters to successfully block websites is concealed by the same encryption that conceals DNS traffic from ISPs.
-
Application and Web Proxies: Websites and apps that serve as a conduit between a user and the internet are known as proxies. Employees can use third-party proxies to get around internal content filtering systems, but companies frequently deploy their own specially designed proxy servers that serve as firewalls and web filters.
-
VPNs, or virtual private networks: Using a VPN is a common way to get around internet censorship. In order to conceal your IP address and shield your online activity from filters, it establishes a secure connection between your device and a distant server. To use a VPN, sign up with a provider and install their app or program. Next, establish a connection with a server on their network.
-
Making use of cellular data as a hotspot for WiFi: Tethering is a feature of smartphones that enables you to establish a private Wi-Fi hotspot using your phone's mobile data. Another computer, tablet, or phone can be connected to the internet via this hotspot.
By unplugging their work laptop from your filtered network and connecting to their cell phone's private Wi-Fi hotspot, your employees can get around your web filter if you are using a DNS filter or firewall to filter websites at the network level.
-
Using USB Storage to Open a Portable Web Browser: Your users may install portable web browsers on a USB flash drive by using services like
portableApps.com. Since the browsers may be started straight from the portable media device without requiring the user to visit a website or install an application on their computer, this approach is more challenging to detect than the others.
Bypassing your network's internet filtering regulations, these USB-based web browsers are set up to send their internet traffic via a proxy address.
How Does Web Filtering Enhance Cybersecurity?
The internet is a huge resource in today's connected society, but it can serve as a gateway for cybersecurity risks like ransomware, spyware, and phishing scams. By preventing access to dangerous or illegal material before it might jeopardize network security, web filtering acts as a proactive protection measure. By preventing access to harmful websites and material, web filtering dramatically lowers the risk of cyber threats like malware, ransomware, and phishing assaults, safeguarding critical enterprise data and infrastructure. Phishing websites frequently aim to steal sensitive information, including user passwords. An organization reduces the chance that such data may be compromised or disclosed by preventing access to these pages. According to this perspective, web filtering is essential for shielding businesses from a wide range of online dangers and making sure staff members can continue to use the internet effectively.
Access to dangerous websites that might infect a user's computer with malware can be blocked by web filters. Web classification allows enterprises to prevent employees from collecting, diverting, or utilizing inappropriate websites, even on a micro level.
Businesses may maintain commercial integrity and cultivate a healthy corporate culture by putting web filtering into place, which will make the internet environment safer, more effective, and compatible with regulations.
How Does Web Filtering Work?
Content filtering works by implementing restrictions regarding the sorts of sites that may be viewed using hardware or software-based solutions. Content is classified by categories based on keywords or other similarities across sites (for example, sports, gambling, pornographic, streaming, and so on), and sites in undesirable categories are prevented from accessing the network.
One of the most apparent applications for web content filtering is keeping unwanted information away from youngsters.
Let's examine some of the main technologies used in conjunction with web filtering to establish a safe and effective online environment.
- Classification of Uniform Resource Locators (URLs): Web filtering is based on uniform resource locator (URL) classification, which aids in grouping websites into discrete categories including social networking, entertainment, education, and adult material. Administrators may quickly prohibit or permit whole content categories using this strategy, depending on how relevant and suitable they are for the workplace. Web filters are able to swiftly apply general policy restrictions to comparable kinds of web material by keeping track of a database of classified websites.
- Analysis of Content: By analyzing online sites' actual content in real time, content analysis goes beyond web filtering. Information analysis evaluates a page's text, graphics, and other components to identify harmful information, such as malware or improper material that does not adhere to the organization's policy guidelines, in contrast to URL categorization, which depends on pre-existing databases. Even newly created or unclassified websites may be effectively evaluated for dangers or policy breaches thanks to this dynamic technique.
- Filtering According to Established Rules: Organizations can establish personalized criteria for content filtering by using established policy-based filtering. Rules governing social media access during working hours, website categories that are prohibited, or websites that are necessary for company operations may all be included in policies. Customization and flexibility are made possible by this layer of web filtering, which guarantees that the filter fits the particular requirements and objectives of any company.
These technologies work together to provide a complete web filtering solution that protects a company's network from security risks and guarantees adherence to corporate guidelines. Web filtering successfully strikes a balance between security, productivity, and access to essential online resources by using this integrated method.
How to Use Web Filtering?
As mentioned at the beginning of the article there are six types of web filtering methods available. Each of them is deployed in different ways and has different requirements, benefits, and drawbacks. You can use one of them which best suits your needs. In the following sections, we will briefly explain to you how you can use browser-based web filtering and network-based web filtering.
How to Use Web Filtering in Chrome?
As a Chrome Enterprise administrator, you may restrict URLs so that users can only browse specific websites. Restricting internet access for individuals can boost productivity while also protecting your company from viruses and dangerous information accessible on some websites.
For simple URL control, use the blocklist and allowlist. Use a content-screening, web-proxy server, or extension if you require more stringent filtering.
Using the URL blocklist and allowlist, you can:
-
Allow access to all URLs except those you block: Use the blocklist to restrict users from visiting specific websites while allowing them to browse the rest of the internet.
-
Block all URLs except those you allow: Use the blocklist to prevent access to all URLs. Then, utilize the allowlist to provide access to a subset of URLs.
-
Create exceptions to very stringent blocklists: Utilize the blocklist to prevent access to all URLs. The allowlist may then be used to provide users access to certain schemes, subdomains of other domains, ports, or specified pathways.
-
Allow the Chrome browser to open applications: Allow particular external protocol handlers so that the Chrome browser may open specific apps automatically.
If you are looking for a solution for a single device you can use browser-based web filtering extensions. Browser-based filters are usually available as browser extensions or add-ons. These filters are simple to set up, but because they are less durable, they are rarely used by enterprises.
Who Uses Web Filtering?
The three most important groups that utilize web filtering are:
Parents who want to keep their children away from information they find objectionable or unsuitable.
-
Businesses: Companies who wish to restrict their employees from viewing websites that are unrelated to their jobs. Furthermore, browser filters can be of great service in preventing malware infection.
-
Schools: Schools utilize web filtering in the same way that companies and parents do, with the hopes of blocking harmful and distracting information while also protecting against malware infection.
Can a Firewall Be Used for Web Filtering?
Firewalls are a type of synchronous web content filtration system.
Firewalls can be physical appliances or virtual appliances that are cloud-based/software-based. Firewalls restrict network traffic to permitted ports, protocols, and IP addresses rather than banning specific websites.
Traditional packet-filtering firewalls filter ports, protocols, and IP addresses at OSI layer 3 (the network layer). While these types of firewalls do block web traffic, they cannot discriminate between specific websites since they cannot recognize URLs or domain names.
Classic firewalls have developed over time into "Next Generation Firewalls" (NGFW), which combine traditional firewall packet filtering with other network filtering capabilities such as web application firewalls (WAFs), web content filters, and intrusion prevention systems. These technologies are often used to protect networks and filter potentially dangerous internet traffic.
Unless you're utilizing a next-generation firewall (NGFW) with an integrated web filter that allows you to block individual URLs, a separate web filter will provide you with significantly more granularity for restricting website access.
What is the Best Web Filtering Firewall?
As mentioned earlier, if you want to choose a firewall solution for web filtering you need to look at the NGFW capabilities of the product. Zenarmor is the best web filtering firewall solutions, especially for SMB, school, and home networks. It offers not only free options on open-source firewalls, such as OPNsense, pfSense software, but also enterprise security qualifications. You can easily install and use Zenarmor® Free Edition forever on your non-commercial environment.
Zenarmor, as opposed to the typical web filtering solutions, is packed with robust enterprise-grade content filtering technology that enables enterprises to implement comprehensive security capabilities for identifying and blocking malware and advanced threats.
With the help of a huge web category database (more than 300M websites within 120 web categories), it can easily filter any harmful or unwanted websites.
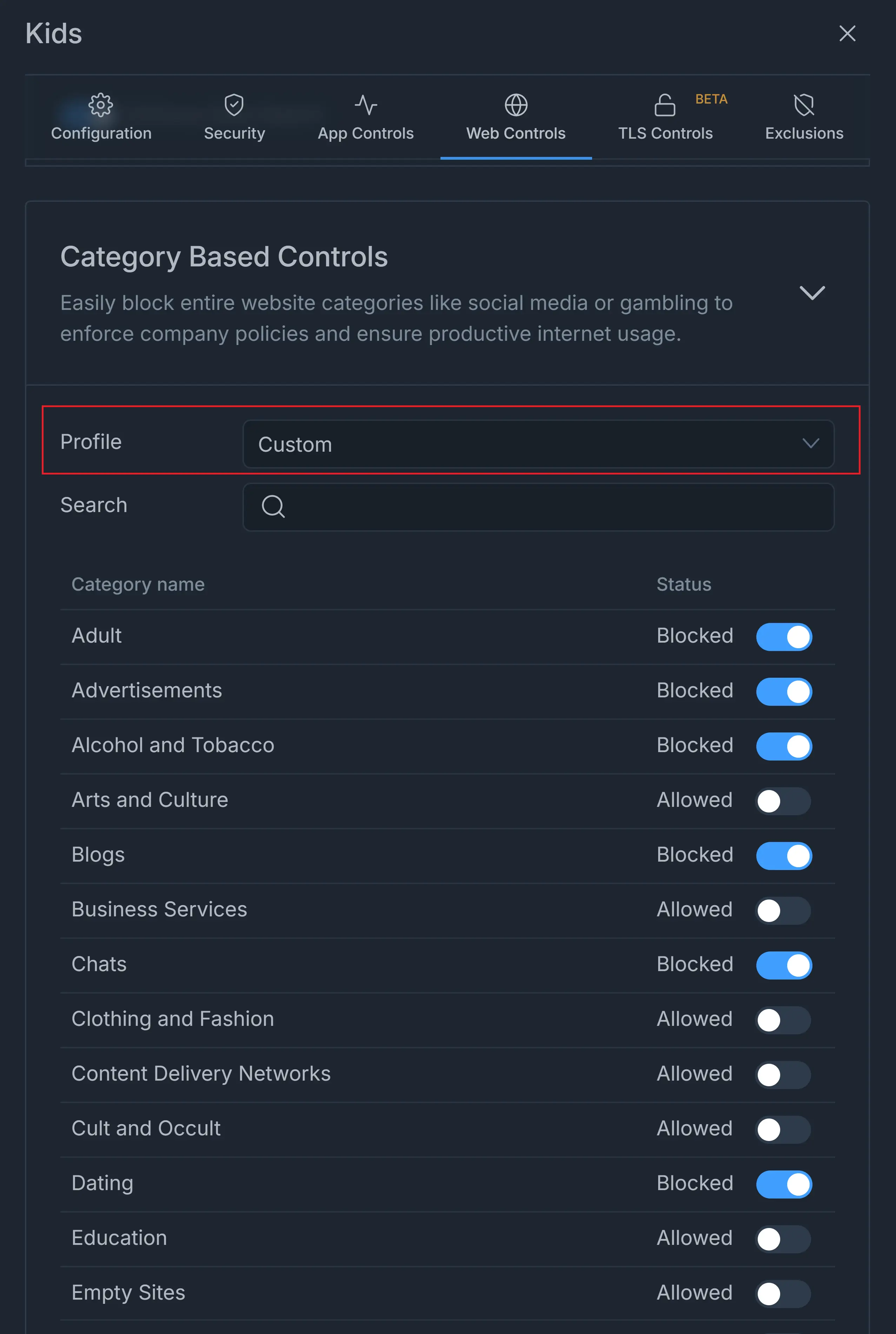
Figure 1. Zenarmor Web Filtering Options
Zenarmor Predefined Web Profiles are divided into four categories:
-
Permissive: This profile has no limitations on online browsing.
-
Moderate: Only dangerous/high-risk site categories are restricted in this profile, such as Illegal Drugs, adults, Pornography, Violence, and Advertisements.
-
High Control: In addition to the categories restricted in the Moderate profile, this profile blocks Forums, Alcohol, Blogs, Gambling, Chats, Dating, Games, Job Search, Online Storage, Social Networks, Software Downloads, Weapons, Military, Swimsuits, Tobacco, and Warez sites.
-
Custom: You may do fully customized web filtering by establishing a new profile.
You may establish user-based policies for content filtering and application control using Zenarmor. As a result, you may not only give free Internet access to your customers but also safeguard them from cyber threats like malware and phishing.
What is the Best Web Content Filtering Software?
Web content filtering solutions are helpful tools for censoring and/or blocking access to restricted web material that is considered harmful or unsuitable. They also offer overall domain name system (DNS) security, preventing users from accessing potentially harmful online pages or IP addresses.
Employees, guests, and customers might have limited access to web material when utilizing the business's wired or wireless network connection. Web content filtering solutions are widely used in businesses today and provide a number of functions that are beneficial to all sorts of enterprises.
Some popular web filtering software are listed below.
-
Zenarmor
-
Barracuda CloudGen Firewall
-
Check Point Quantum Security Gateway
-
Cisco Umbrella:
-
GoGuardian Admin
-
Forcepoint URL Filtering
-
Securely Filter
-
DNSFilter
-
Symantec WebFilter / Intelligence Services
-
cWatch
How Effective Is Zenarmor's Web Filtering Feature?
Known malware assaults may be avoided, and web/application traffic can be blocked using Zenarmor's integrated cloud threat intelligence. OPNsense with Zenarmor is a fantastic choice for consumers who want a low-cost solution with sophisticated network monitoring and security.
Businesses may swiftly implement firewalls and security settings as small as home networks or as large as multi-cloud deployments thanks to Zenarmor's powerful and portable appliance-free technology. In addition to being lightweight and agile enough to work in environments with constrained resources, the packet inspection core is strong enough to defend against encrypted attacks.
Zenarmor doesn't need any appliances and is portable and agile. This allows you to start micro firewalls at the Access, Edge, and Core levels whenever you choose. The effectiveness of micro and powerful packet inspection is so great that it can even protect against sophisticated encrypted attacks. Without requiring data packets to be backhauled between POPs and data centers, implement zero-latency security. For all security protections, Zenarmor's single-pass design processes packets just once. The same security stack is used everywhere to enforce security standards with an unparalleled degree of consistency.
Is Web Filtering Necessary for Home Networks?
Yes. The finest home web filters are a great way to stay safe. In other words, web filters should be viewed as both legitimate protection systems and watchdogs over surfing by children and the weak, with the added benefit of being far less expensive than security solutions.
We won't have to worry about an attack or extortion attempt since we can rely on an efficient web filtering solution. The risk of having your computer, smartphone, or tablet restricted is real, but less often than on a business network, and it may be annoying. Important data, such as private documents or files with login credentials for online services like home banking, might really be lost.
You may be sufficiently comfortable that your kids are browsing securely at home and aren't landing on websites that advocate firearms, religious groups, pornography, or celebrate violence by turning on Web filtering control.
To put it another way, web filters act as browsing watchdogs. There are now several different kinds of web filters, which were first developed in the 1990s specifically to safeguard internet usage on computers in libraries and schools.
Generally speaking, the web filter records and intercepts requests to visit a website from any device. Monitoring is ensured whether surfing from a PC, tablet, or smartphone. A web filter can be installed directly on the device or offered as a service that manages the whole home network. In this instance, every internet connection made over the house WiFi is tracked.