Best Cloud Security Posture Management (CSPM) Tools
"Cloud security posture management" (CSPM), an automated data security solution, controls the monitoring, finding, alerting, and fixing of compliance issues and misconfigurations in cloud settings. With the help of CSPM, good cloud security practices can be used for risk visualization and assessment, incident response, compliance monitoring, and DevOps integration in hybrid, multi-cloud, and container environments.
The primary features of Cloud Security Posture Management Tools are as follows:
-
In multi-cloud environments, it can give policy visibility and guarantee uniform enforcement across all providers
-
Automatically find and fix cloud configuration errors
-
Scan your storage buckets for setup errors that can provide public access to your data
-
conducts risk assessments
-
Because the notifications arrive through one system, CSPMs also reduce alert fatigue
-
identify the footprint of your cloud environment and keep an eye out for the emergence of fresh instances or storage resources like S3 buckets.
-
Generates audit-ready reports for analysis
-
Connect the current configuration statuses to a regulatory or security control framework
Businesses can identify risks and take the necessary action thanks to CSPM systems' automated compliance monitoring and security evaluations. After moving to the cloud, a lot of firms make the mistaken notion that security is the entire responsibility of their cloud hosting provider. This unfounded notion contributes to security lapses and data leaks.
The CSPM systems' automatic and continuing inspections search for configuration mistakes that could lead to data leaks and breaches. This automated detection enables organizations to continuously and continuously make the required adjustments.
In this article, we will discuss CSPM tools, their features, pros and cons, and things to consider when buying IT security tools for the enterprise. These are the top 10 CSPM tools available on the market to choose from.
-
BMC Helix Cloud Security
-
Check Point CloudGuard
-
CloudGuard
-
CrowdStrike Falcon Horizon CSPM
-
Datadog
-
Fugue
-
Lacework
-
Palo Alto Prisma Cloud
-
Threat Stack
-
Trend Micro Hybrid Cloud Security Solution
-
Zscaler CSPM
BMC Helix Cloud Security
By integrating compliance and security testing into service delivery and cloud operations, BMC Helix Cloud Security improves governance and lowers risk. Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) services can be set up in a secure and consistent way with an audit trail thanks to BMC Helix Cloud Security, which checks and fixes cloud configuration security without any code. Its supplier is BMC Software, and it has a free trial available. BMC provides proof-of-concept (POC) for 30 days at no cost. With 8 evaluations, BMC Helix Cloud Security has an overall rating of 4.4 out of 5 on G2 Grid for CSPM Platforms.
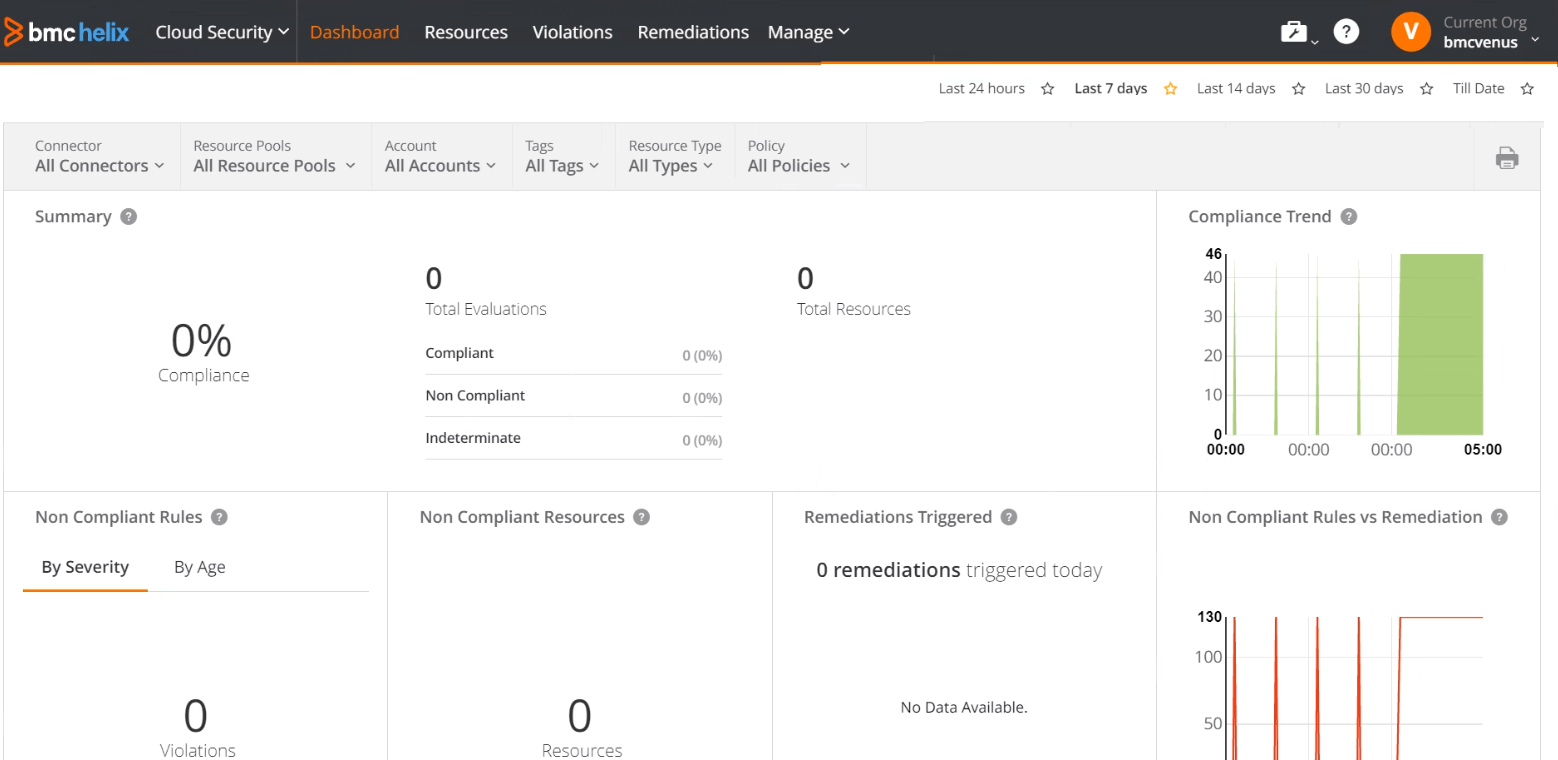
Figure 1. BMC Helix Cloud Security Dashboard
The primary features of BMC Helix Cloud Security are as follows:
-
Automatic cloud advancement tools for updating user data
-
It includes policies such as CIS, GDPR, and PCI
-
Cross-platform supervision
-
Perform blind-spot detection and audit assessments
-
Automated remediation
-
Provides visibility into complex infrastructures
-
Cloud server security
-
Allows for infrastructure-wide scanning
Some pros of BMC Helix Cloud Security are as follows:
-
Multi-cloud security
-
Easy installation
-
Vulnerability management tools
-
Very user friendly
-
Strong container security
The main cons of BMC Helix Cloud Security is cost. Price can be a little cheaper.
Check Point CloudGuard
Check Point CloudGuard is a dependable security tool that detects threats, security flaws, and incorrectly configured systems. It protects your sensitive data by making sure that all of your projects, accounts and virtual networks follow the best security rules and guidelines. With the help of Check Point CloudGuard, which automates governance and compliance across many cloud services, you can see your security posture. Its supplier is Checkpoint, it has a free 30-day evaluation license. With 88 evaluations, Check Point CloudGuard has an overall rating of 4.6 out of 5 on Gartner for CSPM Platforms.
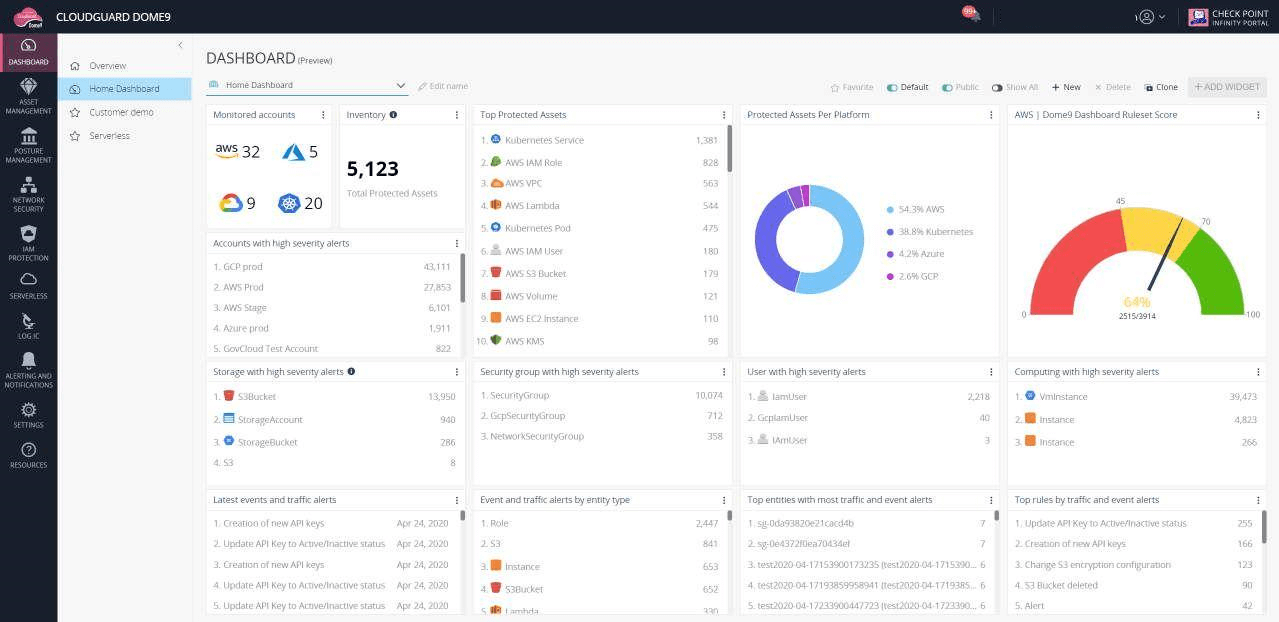
Figure 2. CloudGuard Dashboard
The primary features of Check Point CloudGuard are as follows:
-
Users are kept up to date on their security
-
Initiate policies for multiple accounts
-
Offers high-fidelity visibility
-
Protects from insider threats
-
Provides real-time alerts
-
Users can visualize security posture
Some pros of Check Point CloudGuard are as follows:
-
Alerts for discovered weaknesses
-
Rapid deployment
-
easy to manage granular permissions
The main cons of Check Point CloudGuard is that it covers only off-premises systems.
CrowdStrike Falcon Horizon CSPM
Once a possible asset is added to the monitoring system, the CrowdStrike Falcon system can automatically find it. This will make a list of all the supporting structures, look at how those systems are set up, and make a list of your most valuable assets. CrowdStrike Falcon is a great way to keep your business's most important data safe. It is a well-known cloud-based endpoint protection solution that keeps systems that use more than one cloud compliant and finds and stops misconfigurations. Its supplier is Crowdstrike, and it has a free trial available. Users can register for a 15-day free trial. With 837 evaluations, CrowdStrike Falcon Horizon CSPM has an overall rating of 4.8 out of 5 on Gartner for CSPM Platforms.

Figure 3. CrowdStrike Falcon Horizon Dashboard
The primary features of CrowdStrike Falcon Horizon CSPM are as follows:
-
cross-environment visibility and control that is unified across all cloud environments
-
a step-by-step process is utilized to address security vulnerabilities
-
It can spot and keep an eye on data threats and breaches.
-
gives access to multi-cloud environments' visibility
-
It helps developers avoid making costly errors by assisting them.
-
SIEM solutions are seamlessly integrated
Some pros of CrowdStrike Falcon Horizon CSPM are as follows:
-
easy to obtain and find information on the dashboard
-
reasonable pricing and licensing
-
real-time response piece
-
includes the examination of virtual networks and containers
-
Implements compliance reporting
The main cons of CrowdStrike Falcon Horizon CSPM is that it needs some improvement on the correlation of data in the search algorithms.
Datadog
Datadog is a reliable CSPM tool that constantly scans and checks the performance of hosts, accounts, containers, and the network. Datadog has a unified Datadog agent, so you don't need any more agents. The security tool's deep observability features make it easier for users to find, track and deal with threats.
Datadog monitoring software is installed as a cloud-based service (SaaS) or on-premises. Datadog runs on Windows, Linux, and macOS X systems. Among the cloud service providers supported are Google Cloud Platform, Red Hat OpenShift, Microsoft Azure, Amazon Web Services, and others.
Datadog Cloud Security Posture Management is a subscription service. Modules from Datadog are available for a 14-day free trial. It can be used with other security systems from Datadog, like its SIEM or Cloud Workload Security package. With 354 evaluations, Datadog has an overall rating of 4.3 out of 5 on G2 Grid for CSPM Platforms.

Figure 4. Datadog Dashboard
The primary features of Datadog are as follows:
-
Over 250 product integrations are supported
-
Gives users access to use the API.
-
Provides alerts about potential misconfigurations and violations.
-
Dashboards that may be rearranged and redesigned.
-
Supported programming languages include Java, Python, PHP,.NET, Go, Node, and Ruby.
-
Logs, latency, and error rates are automatically collected and analyzed
Some benefits of Datadog are as follows:
-
Covers cloud platforms and containers
-
Flexible licensing scheme
-
Overall usability and architecture
-
Cross-platform cloud management
-
Insightful reports
-
Log management and visualizations
The main drawback of Datadog is that UI and some of the integrations are not user-friendly for someone new.
Fugue
Fugue is an interactive cloud security system that protects the whole system with a single policy. Teams working on security and cloud engineering are better able to trust cloud security because of Fugue. In order to do pre-deployment security checks on CloudFormation, AWS, Kubernetes manifests, and Docker files, users can use Fugue. They can then use developer-friendly tools to receive meaningful remedial input.
By using Fugue's open-source policy engine, organizations can make sure that compliance and security are applied in a consistent way throughout the software development lifecycle. Fugue assists customers in securing their CloudFormation and Terraform IACs at every level of creation and deployment.
Fugue has four plans to choose from Developer, IAC Security, Cloud Runtime Security, and Enterprise. The Developer plan is free and only allows one user, whereas the other plans allow an unlimited number of users. For 1,000 resources, IAC Security starts at $500 per month, and for 2,500 resources, Cloud Runtime Security starts at $1,250 per month. The Enterprise plan, which has a unique pricing structure, is the last option. With 17 evaluations, Fugue has an overall rating of 4.8 out of 5 on G2 Grid for CSPM Platforms.

Figure 5. Fugue Dashboard
The primary features of Fugue are as follows:
-
Customers' CloudFormation is more protected because of Fugue's Regula policy engine.
-
With Fugue's open-source policy engine, businesses can apply compliance and security uniformly throughout the software development lifecycle.
-
It gives consumers advanced tools for data reporting and data visualization.
Some advantages of Fugue are as follows:
-
Detecting the regular and complicated vulnerabilities
-
Simple overview and fast SaaS service
-
Continuous compliance reports
Lacework
Lacework is a cloud security platform that is driven by data and automates cloud security at scale. This lets users build quickly and safely. Lacework collects, analyzes, and correlates data from a company's Kubernetes, AWS, Azure, and GCP systems with pinpoint accuracy. It then condenses the information into a small number of important security events. Lacework stands out from the competition because it has automated intrusion detection, security visibility, and one-click investigations, and makes cloud compliance easier.
Using its built-in machine learning analysis function, administrators may be able to find, identify, and keep an eye on threats and weak spots in the cloud more quickly. Lacework gives you information about the context, which includes all configuration problems and the most recent changes. With 78 evaluations, Lacework has an overall rating of 4.5 out of 5 on G2 Grid for CSPM Platforms.
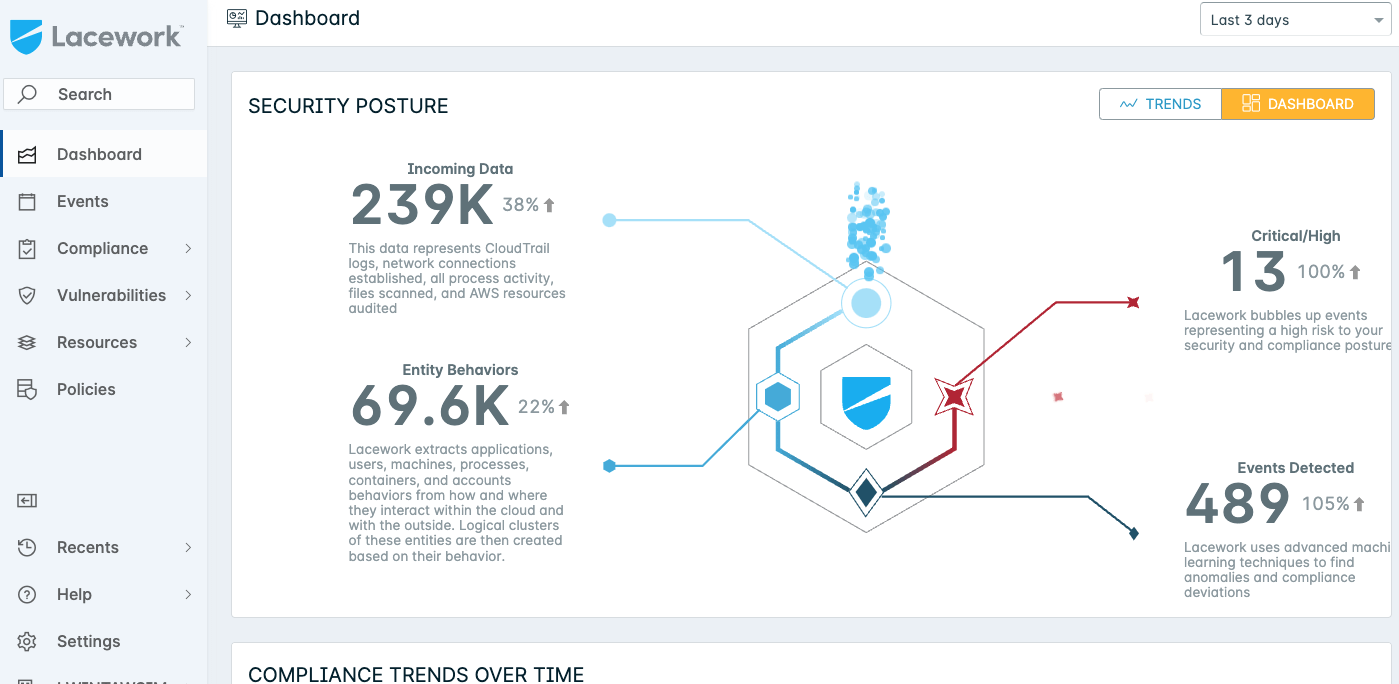
Figure 6. Lacework Dashboard
The primary features of Lacework are as follows:
-
It analyzes account activity for anomalous behaviors
-
Enables users to undertake analysis of container and cloud workload
-
By doing a daily re-audit, Lacework users can maintain their compliance and security up to date.
-
Detects threats, suspicious activities, and misconfigurations
-
It monitors critical account activities
-
Incident and risk management
-
It records changes to policies, roles, and accounts, and informs users.
Some advantages of Lacework are as follows:
-
Detects most of the security vulnerabilities
-
Easy to use once set up
-
Very well-organized dashboard
-
Customer Success team open to feedback and requests
-
Log and event correlation and alerting
Some disadvantages of Lacework are as follows:
-
some integrations can be complex
-
IAM security control could be improved
Palo Alto Prisma Cloud
Prisma Cloud is a serverless solution that gives hosts and public cloud security and protection in one place that is easy to understand. API (application programming interface) testing tools are used to make sure that the data is correct.
The platform has more Prisma Cloud modules, such as Cloud Workload Protection for virtual server processes, Cloud Network Security, Cloud Identity Security, and Cloud Code Security. By using the full set of Prisma Cloud services, you can keep all of your cloud assets safe. It is sold by Palo Alto Networks, and it has a free, fully featured 15-day trial. With 20 evaluations, Palo Alto Prisma Cloud has an overall rating of 3.9 out of 5 on Peerspot for CSPM Platforms.
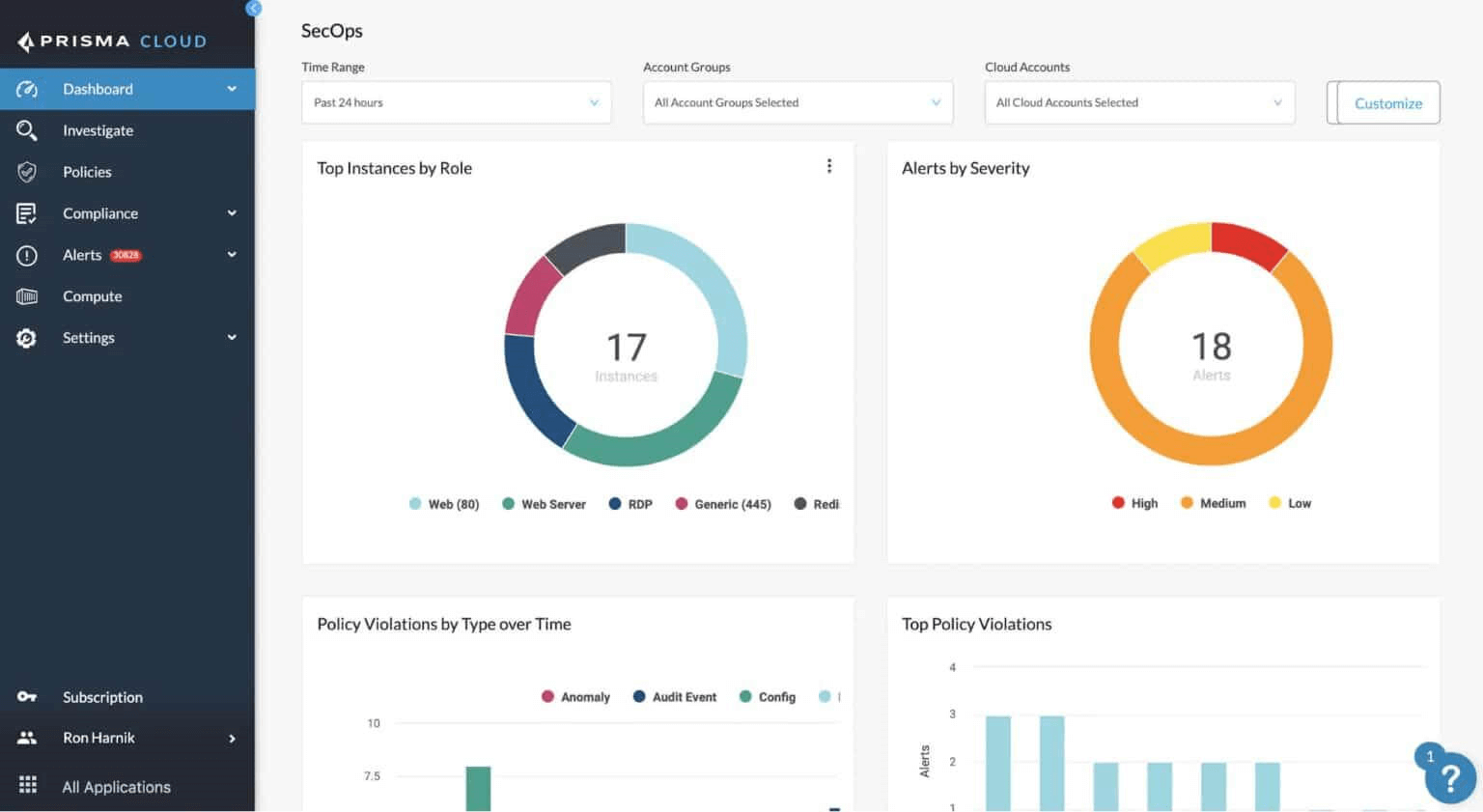
Figure 7. Prisma Cloud Dashboard
The primary features of Prisma Cloud are as follows:
-
Automated remediation of discovered issues
-
Conducts malware checks on cloud-based shared storage
-
Regular backups and updating of the software
-
Supported by Application Programming Interface (API)
-
Detection of network intrusions into the public cloud
-
Guards the workload in the cloud, the network, and the security posture.
-
Automates risk prioritization
Prisma Cloud has the following advantages:
-
Customized dashboard/queries
-
Provides solution recommendations
-
Integrates with third-party systems
-
Support for Amazon Web Services, Microsoft Azure & Google Cloud
-
Threat response
The main disadvantage of Prisma Cloud is that it needs to improve the GUI quality.
Threat Stack
Threat Stack Cloud Platform is a unified cloud security system that manages the development, operations, and security of a single piece of software. With its interface and policies, you can find vulnerabilities and reduce risks effectively.
With the help of the platform Threat Stack, cloud service providers can monitor their infrastructure, apps, and management interfaces more effectively. For modern apps and cloud-native architecture, it was created. It is a popular platform that runs in the cloud that helps companies analyze, prioritize, and respond to both immediate and unanticipated risks.
Threat Stack uses machine learning, rules, and a combination of full-stack telemetry in a special way to secure clouds. It is one of the strongest tools for protecting application infrastructure, it also supports CloudTrail monitoring and IAM settings. Threat Stack is a solid option for your company if you're searching for a CSPM product that reacts to both known and unknown vulnerabilities and threats.
Threat Stack offers three plans, Cloud Security Platform, Oversight, and Insight, but it does not have a free version or a free trial. With 41 evaluations, Threat Stack has an overall rating of 4.4 out of 5 on G2 for CSPM Platforms.
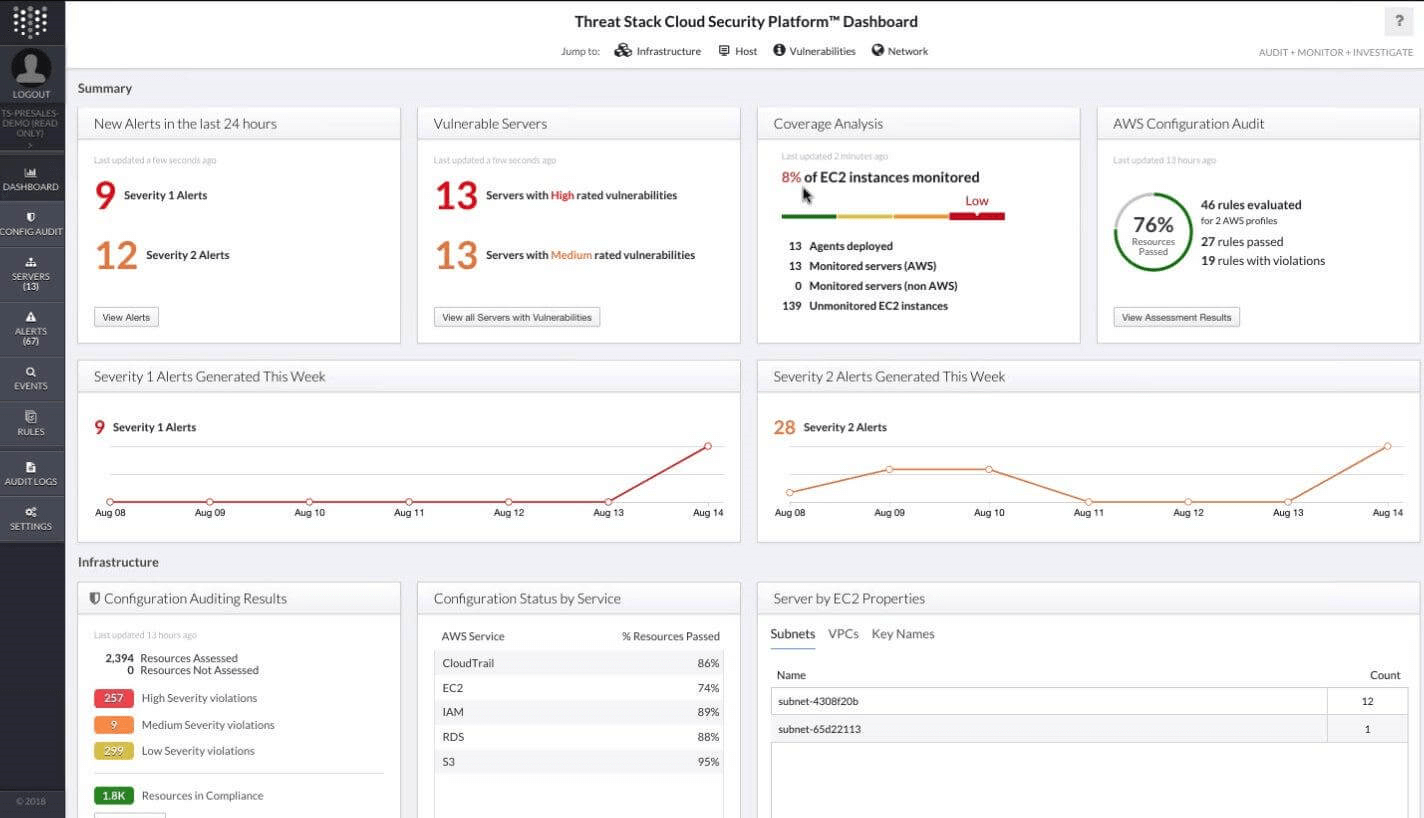
Figure 8. Threat Stack Dashboard
The primary features of Threat Stack are as follows:
-
Compatible with several third-party security operations solutions.
-
Threat Stack CSPM alerts clients to changes made, such as instances spun up in unused regions, by ingesting data from AWS CloudTrail.
-
The users can view the inventory of the servers across multiple accounts.
-
Offers protection for both containerized applications and Kubernetes.
Threat Stack has the following advantages:
-
Comprehensive cloud security & compliance management
-
It runs on a Container-based OS perfectly
-
Very helpful customer service
Some drawbacks of Threat Stack are as follows:
-
Configuring custom rules is tedious and cumbersome.
-
Some improvements on the integration for Windows workloads.
Trend Micro Hybrid Cloud Security Solution
Trend Micro Hybrid Cloud Security Solution is an all-in-one solution that assists organizations in meeting all of their cloud security requirements. Users can easily protect cloud infrastructure because it provides a complete and unified cloud security solution. Customers can take advantage of the cloud's benefits and economies for their businesses because of its high security. Trend Micro Hybrid has solutions that work with all of the major cloud platforms and integrate easily with DevOps workflows and toolchains.
Its security services are not just limited to cloud platforms; they also support DevOps processes and the toolchains for AWS and Azure.
Services are being resold by Trend Micro. It does not have a discount for educational organizations. For pricing, users can choose between a pay-as-you-go option and an annual subscription. for the cost of Trend Micro's seven pay-as-you-go services. Additionally, a 30-day free trial is available for the software. With 127 evaluations, Trend Micro Hybrid Cloud Security Solution has an overall rating of 4.6 out of 5 on G2 for CSPM Platforms.
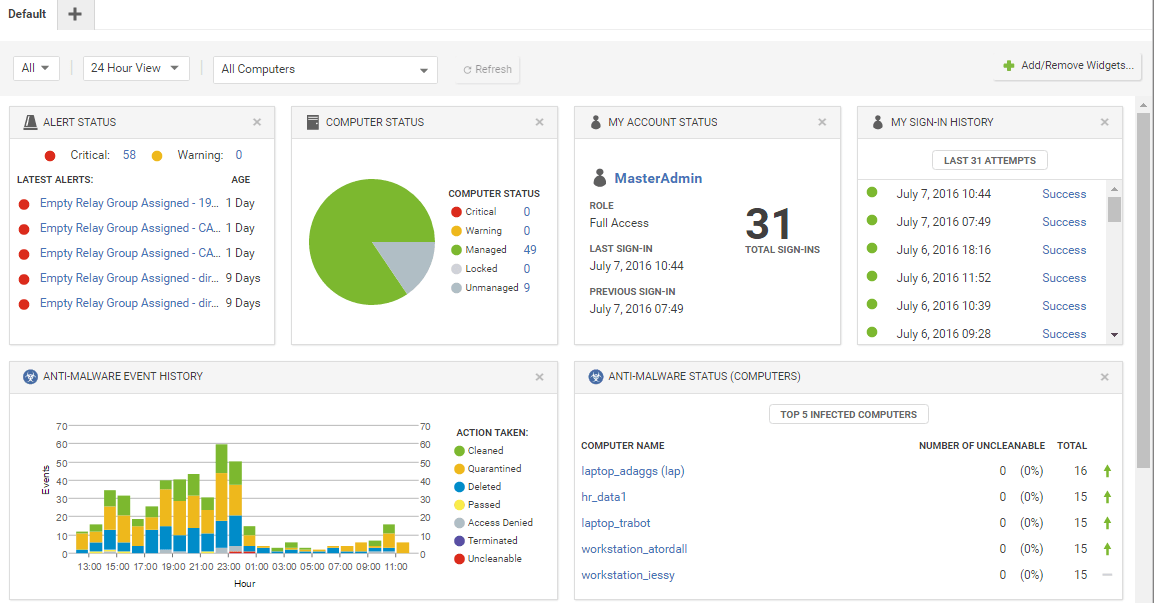
Figure 9. Trend Micro Hybrid Cloud Security Dashboard
The primary features of Trend Micro are as follows:
-
Provides 24/7 Managed Detection Response (MDR) service
-
Helps users quickly and efficiently analyze all data and threats.
-
Complete and all-encompassing visibility.
-
Provides application security that is current with respect to developing approaches and technology.
-
Safeguards against APTs, Ransomware, Zero-Day vulnerabilities, and IDS/IPS.
-
Supports a unified security management console for threat detection across all environments
Some benefits of Trend Micro are as follows:
-
A flexible and easy-to-understand system.
-
Trustworthy security for Linux and Windows servers.
-
Unified services all under one hood
-
Malware protection feature
Some cons of Trend Micro are as follows:
-
Leading to high CPU usage when large workloads are involved.
-
Sometimes updates require a reboot.
Zscaler CSPM
Zscaler CSPM is an integrated platform of cloud services that helps eliminate operational complexity from cloud workload security and secures all workload configurations and permissions. As cloud computing services have become more popular, the risk of exposure and danger has gone up. But with the help of this simple, easy-to-use cloud security app, users can protect their businesses from malware and other threats.
Zscaler CSPM makes it easy to see the status of more than 1,500 security policies and 14 compliance frameworks across AWS, Azure, and Office365. The platform allows for large-scale application settings, private benchmarking, and quick adoption of DevSecOps.
ZCSPM offers a 1-month free product evaluation trial for all customers to evaluate various product features, user experiences, compliance reporting, and security policy coverage across cloud accounts. It is sold by Zscaler, Inc. With 105 evaluations,Zscaler CSPM has an overall rating of 4.4 out of 5 on G2 for CSPM Platforms.
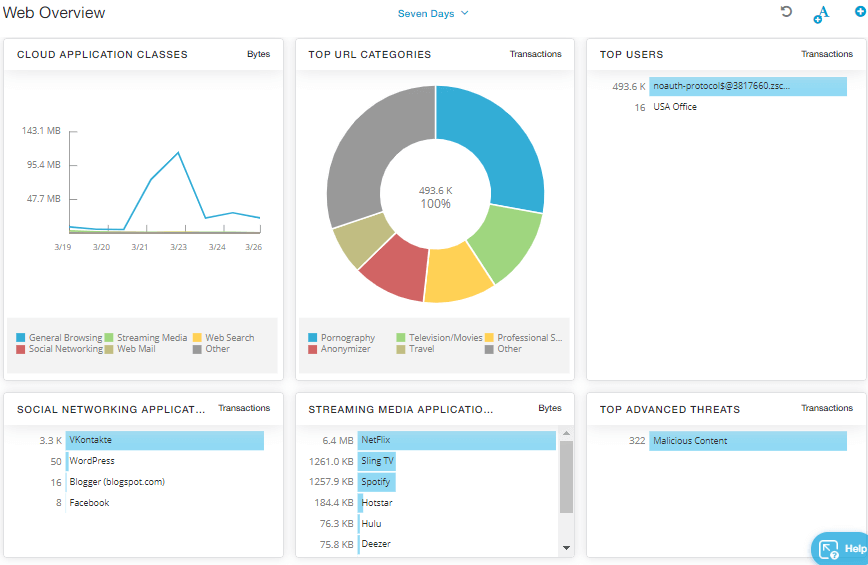
Figure 10. Zscaler CSPM Dashboard
The primary features of Zscaler CSPM are as follows:
-
A scalable and reliable cloud security solution.
-
It can prevent data breaches and prove compliance with your internal/external stakeholders and regulators
-
Includes +3000 pre-built policy templates (for AWS, Azure, GCP, and SaaS) and mappings of the main regulatory frameworks.
-
Prevents cloud misconfigurations and vulnerabilities.
-
Gain visibility into all cloud resources across multi-clouds
The following are some advantages of Zscaler CSPM:
-
ease of configuration
-
safe application access for authorized users.
-
secure in protecting the cloud workspace and the whole cloud environment
-
easy to handle and update clients' requirements
What Should be Considered Before Selecting Cloud Security Posture Management (CSPM)Tools?
On the market, there are several cloud Security Posture Management Tools. Top-tier CSPM solutions share several key features. Each tool has its own features and benefits. For a company, selecting the best cloud security posture management (CSPM) tool is crucial. With the right tool, a company can reduce the risk of data loss or theft while also improving cloud environment security. The important points organizations should consider when choosing a CSPM tool are as follows:
-
Needs of the company: It is vital to consider the sections of your organization that are vulnerable, as well as the cloud environments that, from the perspective of the business, require immediate prioritization. To find the product that best fits your needs, you need to figure out what your problems are and where they hurt the most.
-
Features of the Tools: Different organizations have different security rules, so a CSPM technology should be able to adapt to those rules. It should be able to be automated so that simple tasks can be done, like finding and fixing misconfigurations that could happen during provisioning. In this case, a CSPM would carry out a specific policy that you have set up at the organizational level. Any discovered problem should ideally be fixed automatically or with little manual assistance.
-
Free Trial Session: Many tools have free trial versions that let you try out certain features. These versions often come with the materials you need to get started. The best thing to do is to look for these tools and ask the team members if they think they are good enough to start the process. You can use it to assess the tool and, if necessary, make a transition.
-
Price Information: It is advisable to invest in a tool with comparable characteristics that is inexpensive rather than one that is expensive. Don't make a decision quickly without first looking into the costs and plans of all the options.