Data: Definition, Type, Storage, and Loss Prevention
It is commonly stated that we live in the era of data. We produce, curate, gather, compute, and purify more of it daily.
Data fuels the development of innovative technologies such as artificial intelligence (AI). It facilitates the customization of our internet experiences and advances our desire for more information.
Many people believe that data-driven research occurs primarily in the sciences. It is frequently imagined as involving a spreadsheet full of numbers. Both of these assumptions are incorrect. Research data is collected and used in scholarship across all academic disciplines, and it can take many forms, including videos, images, artifacts, and diaries, in addition to numbers in a spreadsheet. Whether a psychologist is collecting survey data to better understand human behavior, an artist is using data to create images and sounds, or an anthropologist is using audio files to document observations about different cultures, scholarly research in all academic fields is becoming increasingly data-driven.
We will go over what data is, what the history of data is, how it is stored, how it is shared, the different types of data, how data loss happens, and how to prevent data loss throughout this article.
What is Data?
Data is information that has been transformed into a format that is useful for transferring or processing in computing. Data, in the context of today's computers and transmission devices, is information translated into binary digital form. The topic of data may be used in either the singular or the plural.
Data serves as the building blocks of decision-making since they are the smallest pieces of factual information that can be utilized to support calculations, discussions, or other types of reasoning. Data might include anything from statistics to abstract concepts to precise measurements. It is measured, gathered, processed, published, and visualized in the form of graphs, tables, or pictures. In general, the term "data" refers to the fact that certain knowledge or information already in existence has been represented or coded in a way that allows for more efficient use or processing. Unprocessed data, often known as "raw data", is a compilation of numbers or characters that have not yet been "cleaned" and fixed by researchers. The "processed data" from one step may be regarded as the "raw data."
History of Data
The notion of data in computers may be traced back to the work of Claude Shannon, the "Father of Information Theory" and an American mathematician. In electrical circuits, he pioneered binary digital principles based on Boolean logic with two values. Today's CPUs, semiconductor memory, and disk drives, in addition to numerous peripheral devices, are all based on binary digit representations. Early computer input for both control and data consisted of punch cards, followed by magnetic tape and the hard drive. Early on, the prominence of the phrases "data processing" and "electronic data processing" highlighted the significance of data in business computers, which for a while encompassed the entirety of what is now known as information technology. Along with the expansion of corporate data processing, a separate data profession has arisen throughout the history of corporate computers.
The advent of the internet is the most significant event in the history of data that occurred in the 1990s. Sir Tim Berners-Lee invented hyperlinks and hypertext, allowing for global data sharing.
In the mid-1990s, AT&T introduced the first web-based storage service.
Other significant events in the history of data in the 1990s included the debut of Google Search in 1997. This made data extremely accessible to anybody with computer access.
The age of data has arrived. It is referred to as "the modern oil". With this has come a greater understanding of the need for data security while gathering, using, and keeping information. This led to laws such as the General Data Protection Regulation (GDPR) of 2018 as a result. (Which emphasizes the significance of privacy and data protection.)
The requirement to secure data extends beyond the present. It must also be preserved for the benefit of future generations so they can learn from what we know now.
Thus, today's data fuels the inventions of the future.
How is Data Stored?
Computers store data, such as video, images, sounds, and text, as binary values, which are represented by patterns of only two digits: 1 and 0. A bit is the smallest unit of data and can only represent one value. A byte is composed of eight binary digits. Megabytes and gigabytes are units of storage and memory.
As the amount of data collected and stored grows, so do the units of measurement. For example, the relatively new term "brontobyte" refers to data storage equal to 10 to the 27th power of bytes.
The computer stores all data as numbers. For instance, letters become numbers; the Complete Works of Shakespeare, which is around 1,250 pages long and includes 40 million bits, one byte per letter, for a total of five gigabytes, is converted into numbers (5MB). Photographs are turned into a series of integers that represent the position, color, and luminance of each pixel. Binary numbers employ two digits to express all possible values, whereas conventional numbers use ten (0, 1, 2, 3, 4, 5, 6, 7, 8, 9). The binary representations of the conventional numerals 0 through 8 are 0, 1, 10, 11, 100, 101, 110, 111, and 1000. Any value may be recorded as a succession of objects that are either true (1) or false (0) using binary integers (0).
The hard disk drive (HDD) mostly stores binary data. The device consists of a spinning disk (or disks) with magnetic coatings and heads that can read and write information as magnetic patterns. In addition to hard disk drives, magnetic data is also stored on floppy disks and cassettes. Solid state (or flash) storage is utilized in modern computers, mobile devices, tablets, USB "Universal Serial Bus" flash drives, and SD "Secure Digital" cards.
How is Data Shared?
There is still no universally accepted definition of "data sharing" or "shared data." It is not uncommon for one of the many possible names and definitions of a new technology or practice to take some time to become mainstream. The Support Centre for Data Sharing (SCDS) defines "data sharing" as a collection of practices, technologies, cultural elements, and legal frameworks that are relevant to digital information transactions between various types of organizations. Although the terms "data sharing" and "shared data" are frequently used interchangeably, we at The Support Centre for Data Sharing (SCDS) prefer the term "data sharing". The reason for this is that our emphasis is on sharing practices rather than data.
Data sharing is not a new concept. Individuals, organizations, and governments have been exchanging information since the dawn of computers and networks. However, advancements in digital literacy and skills, technology, and the adaptation of legislative frameworks to the digital space over the last decade have enabled data to be shared at an unprecedented rate and scale. This sea change is demonstrated by the data-sharing practice examples that we have begun to collect. JoinData, for example, promotes long-term innovation in the Dutch agricultural sector by allowing farmers to share data in a quick, easy, and secure manner. Three factors have significantly altered the range of opportunities for information sharing:
-
The first is the increased availability and quality of data, as well as how inexpensive and simple it is to store, process, and transfer it today.
-
The second is a cultural shift. we now understand data better and are willing to treat it as a resource, investing in it - and this applies to governments, private organizations, and individuals alike.
-
Finally, the third component is the involvement of policymakers, who understand the implications of digital in people's lives better than ever before and are committed to regulating this field in the best way possible. This process requires an understanding of the benefits and drawbacks of data sharing.
The technique for data sharing may be broken down into eight steps.
-
Data storage: The initial component of a data-sharing scenario is the storage of actual data. Concerning the storage of data that must be shared, several factors must be taken into account. The first concern is that data has multiple sorts of value for the company that owns it, and a cost-benefit analysis must be undertaken due to the expense of storage options. In addition to the business usefulness of the data, sensitivity must also be considered. Financial data and trade secrets are intrinsically more sensitive than, for example, promotional materials; hence, they must be held with the appropriate access and usage rights.
-
Ownership or control over data: It is frequently desirable or required to be able to validate the integrity of shared datasets. When there is a reasonable danger that the shared data can be altered, the recipient must be able to confirm that the datasets are the ones that the data owner or holder intended to provide.
-
Anonymization: Sometimes the data to be provided includes sensitive or private information. In these instances, it must be determined if the owner of the data has permission to disclose certain portions of the data, or whether they must be erased or disguised. It is known as data anonymization.
-
Ethics check: Sometimes, shared databases contain personally identifiable information. For instance, if research entails the collection of data from individuals, the organizations engaged are required to uphold high ethical standards, such as those advocated by professional groups, institutions, and funding agencies, both during processing and dissemination. Even when datasets contain personal or secret information, they can be shared ethically and legally if the company pays sufficient attention to the following factors:
- The individual's identity must be safeguarded (this is required in almost every case).
- The provision for data sharing must be mentioned during the consent process.
- Consideration should be given to regulating access to shared data.
-
Licensing: Regarding the license, two issues must be addressed:
- Who has the legal right to produce copies of creative work?
- How may copyright holders grant others permission to utilize their intellectual property?
-
Data security: The proper management of data security is a crucial part of data sharing. When data is shared, one of the most typical criteria is the supply of legitimate data that only contains the relevant personal or sensitive information and corresponds in full to the underlying license. The recipient of the shared data must be certain that the received information originates from the specified source and has not been altered along the route. Physical, network, and system security are the three major components of data security.
-
Discoverability: To enable widespread discovery and utilization of shared data, the data must be well organized. It is not enough to collect and provide information to potential consumers. Instead, it is crucial to specify (document) the data to be shared in a format that is discoverable, understandable, and accessible to other users. The documentation of data tackles both technical and business challenges, such as how data was created, what it means, and its structure and content. Utilizing metadata, data documentation is performed.
-
Data access: Additionally, the appropriate ethical norms impact the extent of data access restrictions. In some situations, personal or sensitive data can be safeguarded by restricting or regulating access. Typically, data acquired during research projects and stored in data centers and/or archives are not available to the public. User registration and the informed consent obtained by study participants restrict access. In order to To have access to the shared data, data re-users must agree and comply with the terms of the appropriate license.
Nevertheless, access to secret information can be further restricted by:
- Specific authentication/authorization method use requirements.
- Granting access only to authorized users.
- Limiting access by allowing only distant analysis and prohibiting data download and local processing.
- At a minimum, the removal of private data for the duration specified.
What are the Types of Data?
Data types are employed by type systems, which provide a number of means for their definition, implementation, and use. Type safety is guaranteed to varying degrees by various types of systems.
Although different languages may employ different terminology, almost all computer languages explicitly include the concept of data type.
Typical data types are:
-
Integer
-
Floating-point number
-
Character
-
String
-
Boolean
For instance, the 32-bit integers with values between 2,147,483,648 and 2,147,483,647 are represented by the type int in the Java programming language, along with the operations that may be carried out on integers, including addition, subtraction, and multiplication. On the other hand, the color might be represented by a string that contains the name of the color plus three bytes that indicate how much of each color -red, green, and blue- is present.
The majority of computer languages also let the programmer build new data types, typically by merging several elements of different types and specifying the new data type's legal operations. For instance, a programmer could develop a brand-new data type called "complex number" that would have both real and fictitious components. A data type describes the representation, interpretation, and structure of values or objects stored in computer memory. It also reflects a restriction placed on the interpretation of data in a type system. The data type information is used by the type system to verify that computer programs that access or alter the data are valid.
The following table illustrates how most data types in computer programming and statistics are equivalent:
| Statistics | Programming |
|---|---|
| real-valued (interval scale) | floating-point |
| real-valued (ratio scale) | floating-point |
| count data (usually non-negative) | integer |
| binary data | Boolean |
| categorical data | enumerated type |
| random vector | list or array |
| random matrix | two-dimensional array |
| random tree | tree |
Table 1. Data types in statistics and computer programming
1. Integer (whole number)
In computer science, an integer is a data type of integral data type, a data type that represents a range of mathematical integers. Different widths and the presence of negative values are also possible for integral data types. Computers frequently display integers as a collection of binary digits (bits). The collection of integer sizes that are available varies depending on the size of the grouping and the type of computer being used. In computer hardware, a processor register or memory address can almost always be represented as an integer.
Common integral data types
-
Bytes and octets
-
Words
-
Short integer
-
Long integer
-
Long long
2. Floating point (decimal number)
Floating-point arithmetic (FP) is arithmetic that supports a trade-off between range and precision in computing by approximating real numbers with formulas. Because of this, systems with extremely small and very large real numbers that demand quick processing speeds frequently use floating-point calculations. A floating-point number is typically approximated by a significant, which is a fixed number of significant digits, and scaled using an exponent in a fixed base, which is typically two, ten, or sixteen. An accurate representation of a number has the following structure:
Where significand, base, and exponent are all integers, the base must be greater than or equal to two. For example,
A number's radix point, often known as the decimal point or, more frequently in computers, the binary point, can "float", or be positioned anywhere in relation to the significant digits of the number. The exponent serves as a marker for this position, making the floating-point representation a type of scientific notation.
A floating-point system can be used to represent values of multiple orders of magnitude with a fixed number of digits; for example, the diameter of an atomic nucleus or the distance between galaxies can be stated using the same unit of length. The numbers that can be displayed as a result of this dynamic range are not evenly spaced; depending on the scale used, the difference between two successive representable integers varies.
Computers have utilized a number of different floating-point representations over the years. The IEEE 754 Standard for Floating-Point Arithmetic was created in 1985, and since the 1990s, the IEEE-defined representations have been the most widely used.
A computer system's ability to do floating-point operations quickly - often expressed in terms of FLOPS- is crucial, especially for applications that need extensive mathematical computations.
A computer system's floating-point unit (FPU), sometimes known as a math coprocessor, is a component created specifically to perform operations on floating-point numbers.
3. Character
Graphemes, graphene-like units, or symbols, such as those found in an alphabet or syllabary in the written form of a natural language, are broadly equivalent to the units of information known as characters in computer and machine-based telecommunications.
Letters, numbers, and punctuation marks like "." and "-". as well as spaces, are examples of characters. Control characters are also included in this notion; these characters represent formatting or processing instructions rather than visual symbols. Carriage return and tab are examples of control characters, as well as commands for printers and other text-processing equipment. Strings are frequently made up of individual characters.
In the past, the term "character" was also used to simply refer to a certain number of consecutive bits. The term "character" is most often used to refer to 8 bits (or one byte), but other definitions have also been used in the past. For example, 6-bit character codes were once common (using only upper case, though there were enough bits to also represent the lower case, without numbers and punctuation allowed) and even 5-bit Baudot codes. Despite the fact that the term has also been used to refer to 4 bits with only 16 possible values, it was never intended to see the characters of the Universal Character Set, which can all be represented by one or more 8-bit code units but for which 8 bits are insufficient.
4. String
A string is typically a sequence of characters in computer programming, either as a literal constant or as some sort of variable. The latter can either be constant in length or allow its elements to alter (after creation). A string is sometimes implemented as an array data structure of bytes (or words) that contains a succession of elements, typically characters, using some character encoding. A string is generally thought of as a type of data. More generic arrays or other sequences (or list) data types and structures may also be referred to by the term "string".
A variable declared to be a string may either enable memory storage to be statically allocated for a set maximum length or utilize dynamic allocation to allow it to carry a variable number of elements, depending on the programming language and specific data type used.
A string is referred to as a string literal or an anonymous string when it appears literally in the source code.
A "string" in formal languages is a finite series of symbols selected from an alphabet, which is a set used in formal logic and theoretical computer science.
5. Boolean
The Boolean data type in computer science (often abbreviated to Bool) is meant to represent the two truth values of logic and Boolean algebra and can take one of two possible values (typically labeled "true" and "false"). It bears George Boole's name because he was the first to define an algebraic system of logic in the middle of the 19th century. The Boolean data type is most often related to conditional statements, which enable various operations by altering control flow based on whether a programmer-specified Boolean condition evaluates to true or false. Logic need not always be Boolean; it is a specific example of a more broad logical data type.
What are the Differences Between Quantitative and Qualitative Data?
You'll need multiple methods for data gathering, hypothesis testing, and analysis, so it's crucial to comprehend the main distinctions between quantitative and qualitative data:
-
Numbers, counts, or measurements make up quantitative data. Qualitative data is descriptive, language-related, and interpretation-based.
-
In calculations, quantitative data provides us with how many, how much, or how frequently. We can better comprehend particular behaviors by using qualitative data to show us why, how, or what actually occurred.
-
Quantitative information is universal and fixed. Qualitative data is individual and subjective.
-
Quantitative research techniques involve counting and measuring. Interviewing and observing are examples of qualitative research techniques.
-
Statistical analysis is used to analyze quantitative data. Analyzing qualitative data involves classifying it into categories and topics.
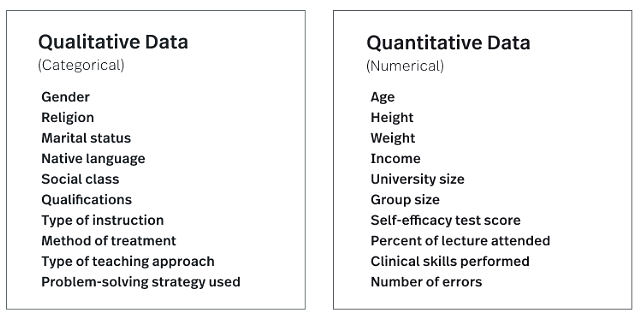
Figure 1. Quantitative and Qualitative Data Samples
As you can see, both are essential to really discover solutions and patterns in data and offer enormous value for any data collection.
What is the Difference Between Analog and Digital Data?
Digital data has discrete values, while analog data is represented in a continuous form. Information that has been preserved in a manner consistent with its original organization. Analog signals, in contrast to digital data, recreate the data being conveyed using continually varying electric currents and voltages.
Data conversion between analog and digital is necessary. In an analog system, data is transmitted using fluctuating currents, making it particularly challenging to eliminate noise and wave distortions throughout the transmission. For this reason, analog signals cannot transmit high-quality data.
Digital signals, on the other hand, use binary data strings (0 and 1) to replicate the transmitted data. High-quality data transmission is made feasible since noise and distortions have a negligible impact.
What is the Difference Between Data and Information?
The terms "data" and "information" are frequently used interchangeably, but they are not synonymous. There are subtle distinctions between these components and their functions. Individual facts are defined as data, whereas information is the organization and interpretation of those facts.
Data and information differences are listed as follows:
-
While information places such facts into context, data is a collection of facts.
-
Information is ordered, whereas data is raw and unorganized.
-
Data points are unique and occasionally unrelated. This data is shown in order to provide an idea of how everything fits together.
-
Data is pointless by itself. Meaningful information is created after it has been studied and interpreted.
-
Information depends on data; data does not depend on information.
-
The most prevalent data types include graphs, numbers, figures, and statistics. Normally, information is communicated using words, language, thoughts, and concepts.
-
Although data alone is insufficient for decision-making, you can nevertheless base your choices on facts.
How Does Data Loss Occur?
When sensitive or valuable information on a computer is compromised by theft, human error, malware, viruses, or power outages, data loss happens. It might also happen as a result of an edifice's physical harm, mechanical malfunction, or other equipment.
Theft of laptops, unintentional file deletion or overwriting, power surges, liquid spills, and hard drive wear and tear are some of the leading causes of data loss. Data recovery is made feasible in the event of data loss by regularly backing up files. Professional recovery services could be able to retrieve lost data from data that hasn't been backed up.
Data loss can happen to servers just like it can to individual PCs and devices.
The following is a summary of the facts that should be understood regarding data loss.
-
The destruction of private or sensitive data that was saved on a computer or network is known as data loss.
-
External circumstances like a power outage, theft, or a widespread phishing attack can result in data loss.
-
Human error may result in data loss when someone opens an email that has a virus, their antivirus program expires, they drop their computer, or they spill something on it.
-
Companies can safeguard themselves by implementing software-based data loss prevention measures and setting up employee standards that allow them to handle and distribute company documents in a secure manner.
-
People can safeguard themselves by using current virus and malware protection and refraining from opening shady emails.
How to Prevent Data Loss?
Data security is more important than ever since society depends more and more on data. The cost of data breaches reached its highest level in 17 years in 2021. Business losses from breaches averaged $4.24 million. Fortunately, your company can take steps to prevent data loss. Your business will save money, defend its reputation, and protect its most sensitive information if you take a proactive approach to data protection and prevent a data leak or breach.
8 Solutions for Data Loss Prevention
There are various types of data loss. It could be accidental, like when someone spills coffee on their computer, or malicious, like when a bad guy hacks into the system of your business. Data loss happens when information is lost, corrupted, or otherwise rendered unrecoverable. There are different data loss prevention methods since there are numerous ways for data loss to occur. Eight ways of preventing data loss are explained below.
- Create a Device Security Policy: Your staff members can work from home with the use of portable devices like laptops or mobile phones, which boosts productivity across the board for your business. Additionally, the gadgets may increase your business's susceptibility to data loss or theft. For instance, a vengeful ex-employee could take a corporate laptop or smartphone, access important files, and delete them. If a third party gains access to a company's device, it could also do harm.
The danger of data loss can be decreased by developing and executing security policies for all mobile and portable devices. Your business can keep track of where devices are and who last used them by implementing a sign-in and sign-out policy. Your data can also be protected by using a remote wipe procedure or a method of locking a computer or smartphone when you can't find it.
- Backup Your Data: Always have a backup of your company's data, if not numerous backups. If something goes wrong with the original version, you won't have to stop working if you have backup copies of your most important data. Having several backup copies of your data is a good idea. You can rely on the following system if the first one has problems.
Think about creating three backup copies of the most crucial information for your business. One copy may be on a physical server, and the rest may be in the cloud. Having off-site and on-site backups in addition to on-site backups is also a smart move. idea. The least vital data should only be kept in one copy, while important but less crucial data should be kept in two copies.
- Secure Sensitive Information: Making sure that a bad actor can't do much or anything with your company's data if they obtain access to it is another aspect of securing it. Due to encryption, it is extremely challenging for an unauthorized person to understand or use stolen data.
When your data is at rest, on a server, or in the cloud, it should be encrypted. When someone emails a client or colleague or uploads data to the cloud, it should also be secured while in transit.
- Follow the "No Food or Drink" Rule: The data for your firm could be destroyed by a dropped water bottle or coffee cup. Data loss can be decreased by enforcing a no-eating or drinking rule around business computers or other electronic devices.
It can be useful to have a designated location in your office or corporate headquarters for employees to eat and drink in order to assist in enforcing the "no food or drink" policy. Encourage your team to take frequent breaks or stops for water, coffee, or a snack to lessen the possibility that they will consume food or beverages near sensitive machinery.
-
Use Anti-virus software: Antivirus and anti-malware software to shield your computer against threats that could delete important files or erase data on it. The software routinely checks the computers and other devices at your firm and notifies you if it discovers anything unusual, such as a virus or an unapproved piece of software. To check for viruses, the software may also scan both incoming and outgoing email messages.
-
Establish a password policy: The security of your company's equipment and data depends on how secure the passwords you use to protect access to them are. A password policy can make it more difficult for hackers to guess employees' passwords and get access to your system.
Your password policy ought to have numerous sections. It should first specify exactly what constitutes a strong password. It is essential to use a combination of capital and lowercase letters, numerals, and special characters. Your system should prevent employees from using default passwords like "12345" or "password".
The policy should ideally call for employees to update their passwords on a regular basis, like every two months or every three months. Finally, when an employee types a password, it should always be encrypted or concealed to safeguard the password. itself. Some apps allow users to check that they entered their password correctly by selecting the "display password" option. However, that functionality also makes it feasible for an uninvited bystander to see another person's password.
Finally, the password policy should mandate that when finished using the system or any applications, employees log out of them.
-
Develop Your Group: Educating your employees to safeguard company data and prevent loss includes more than just implementing a password policy. Additionally, it's a good idea to provide employees with regular training about the dangers of data breaches and loss, as well as their responsibility for securing firm data. Your training course can go over email security, how to safeguard electronic equipment from power surges, and how to spot potential security holes.
-
Upgrade Hardware: Data loss can occasionally be caused by outdated or worn-out equipment. Hard drives aren't permanent fixtures. They'll eventually deteriorate and stop working. Prior to a breakdown, replacing your company's computer hardware helps you prevent the loss of crucial data. While developing and adhering to an updated schedule is a good idea, it is also beneficial to train your staff to see any early indications of probable failure.
Hard disks in computers that overheat easily or make a lot of noise when loading programs are probably beyond repair. Your business will continue to run smoothly if you replace them as soon as they show signs of failing.
When Do Data Breaches Happen?
The assumption is that an outside hacker is to blame for a data leak, but that isn't always the case.
Sometimes, deliberate attacks might be linked to the causes of data breaches. It may, however, also be the result of a person's carelessness or weaknesses in the infrastructure of a business.
When a data breach can happen is as follows:
-
Misuse of insiders and privileges: Business insiders understand the value of knowledge and occasionally steal it. They might decide to sell it or use it to launch a new business.
-
Physical theft and loss: Secure information can be accessed via a laptop left in a hotel lobby. Nevertheless, breaches may still include hardcopy records. Physical assets might be lost intentionally or unintentionally.
-
Denial of service: Systems and networks are the targets of these types of cyber attacks. Large enterprises are frequently the target of distributed denial of service attacks(DDOS), which overload and flood systems to obstruct service.
-
Crimeware: Malware, short for malicious software, or social engineering attacks, falls under this category. Criminals may specifically use:
- Computer files are held hostage by ransomware until their owner pays to unlock them. However, this might not happen.
- An online user web form is compromised when a hacker uses SQL injection to introduce random code. The website can be harmed if the form isn't handled correctly when it's sent through the backend database.
-
Phishing attempts: Phishing is a sort of social engineering assault in which a cyber thief approaches the victim via email, phone call, direct chat, or text message while posing as a reliable source. The intention is to deceive the victim into downloading malware or disclosing personal data like bank account information or passwords.
-
Attacks on web applications: When you register for a web application, you frequently share personal information. Attackers take information like names, addresses, and other details and utilize it elsewhere.
-
Payment card skimmers: To steal a person's identity and money, thieves can attach a skimming device to a credit card reader. ATMs and gas pump terminals are two common targets.
-
Cyber Espionage: This malicious email has links to actors with ties to the government. Over time, it is intended to breach a system and obtain data.
-
Intrusions at the point of sale: Point-of-sale controllers and terminals are the focus of remote assaults. Attacks on restaurants and small businesses have intensified.
-
Other mistakes: security mishaps might lead to data compromise. This covers the accidental disclosure or loss of anything containing private information.
-
Everything else: This pattern is varied. Recently, it has used hijacked email accounts, where a hacker impersonating the "CEO" of the business can ask an employee to wire money for a plausible cause. It can have astonishing consequences if, for example, a firm finance employee complies with the false instruction and transfers money to a criminal's account.