Top SOAR Platforms in Cyber Security Market
Security orchestration, automation, and response or SOAR, is a group of software tools that work together to help an organization find out about security threats and respond to security events without the help of a person. With SOAR technology, actions between different people and tools can be planned, done, and automated on a single platform. This improves an organization's overall security by making it easier to respond quickly to cybersecurity threats and to watch, understand, and stop similar problems from happening again.
The three main pieces of software that make up a full SOAR system are threat and vulnerability management, security incident response, and security operations automation.
SOAR solutions are still being used by organizations all over the world to improve the efficiency of security operations. "SOAR solutions are typically employed to promote consistency in security processes and improve threat detection and response by providing context enrichment and improving downstream prioritization," the most recent Gartner SOAR market guide states. At a predicted CAGR of 8.8% from 2021 to 2027, the global SOAR market is expected to grow from US$ 766.7 million in 2020 to US$ 1430 million by 2027.
Analysts are often so busy that they miss real threats and make a lot of mistakes when trying to deal with threats and bad agents. This is because there are more threats and alerts than ever and not enough resources to deal with them all. Analysts are also forced to choose which alerts to take seriously and act on, and which can be ignored.
Thanks to platforms like SOAR they can systematically orchestrate and automate their alert and response process. Security operations teams can improve the overall security of an organization by getting rid of the routine tasks that take the most time, effort, and resources. By doing this, they are better able to handle and investigate incidents.
SOAR systems can give better information about what is going on, which can also make operations more effective and efficient. They can also find and respond to incidents more quickly and make management, reporting, and working together easier.
In this article, we'll explain the best SOAR platforms available in the market, take a look at each product's key features, and differentiators from other solutions and evaluate their pros and cons.
Top SOAR Solutions
It can be challenging to determine which strong SOAR solutions are best for users given the variety that are now available on the market. To help you, we looked into the market and made a list of the best SOAR products on the market right now. Top SOAR solutions are outlined below:
-
Anomali ThreatStream
-
Cyware Virtual Cyber Fusion Center
-
FireEye Helix
-
Fortinet FortiSOAR
-
IBM Security Resilient
-
LogicHub SOAR+
-
Micro Focus ArcSight SOAR
-
Palo Alto Networks Cortex XSOAR
-
Rapid7 InsightConnect
-
Siemplify SOAR Platform
-
Splunk SOAR
-
Swimlane SOAR
-
ThreatConnect SOAR Platform
-
ThreatQuotient ThreatQ
Anomali ThreatStream
ThreatStream from Redwood City-based Anomali speeds up threat detection by consolidating security solutions into a single platform and offering tools for operationalizing threat intelligence. ThreatStream, which is powered by artificial intelligence, automates and streamlines the process of compiling all pertinent global threat data. This reduces administrative burden while enhancing visibility into your specific threat landscape through a variety of specialized intelligence sources.
The primary features of Anomali ThreatStream are as follows:
-
Global intelligence App Store management spanning countless open, private, and commercial sources
-
assembling data from various sources and formats
-
tactical, technical, operational, and strategic interactive dashboards
-
integration with security tools like firewalls, IPS, and SIEMs
-
investigate indicator correlations as soon as possible utilizing open source
-
processes and features for data analysis and sharing
-
swift action and continuous intelligence cooperation with colleagues in the business
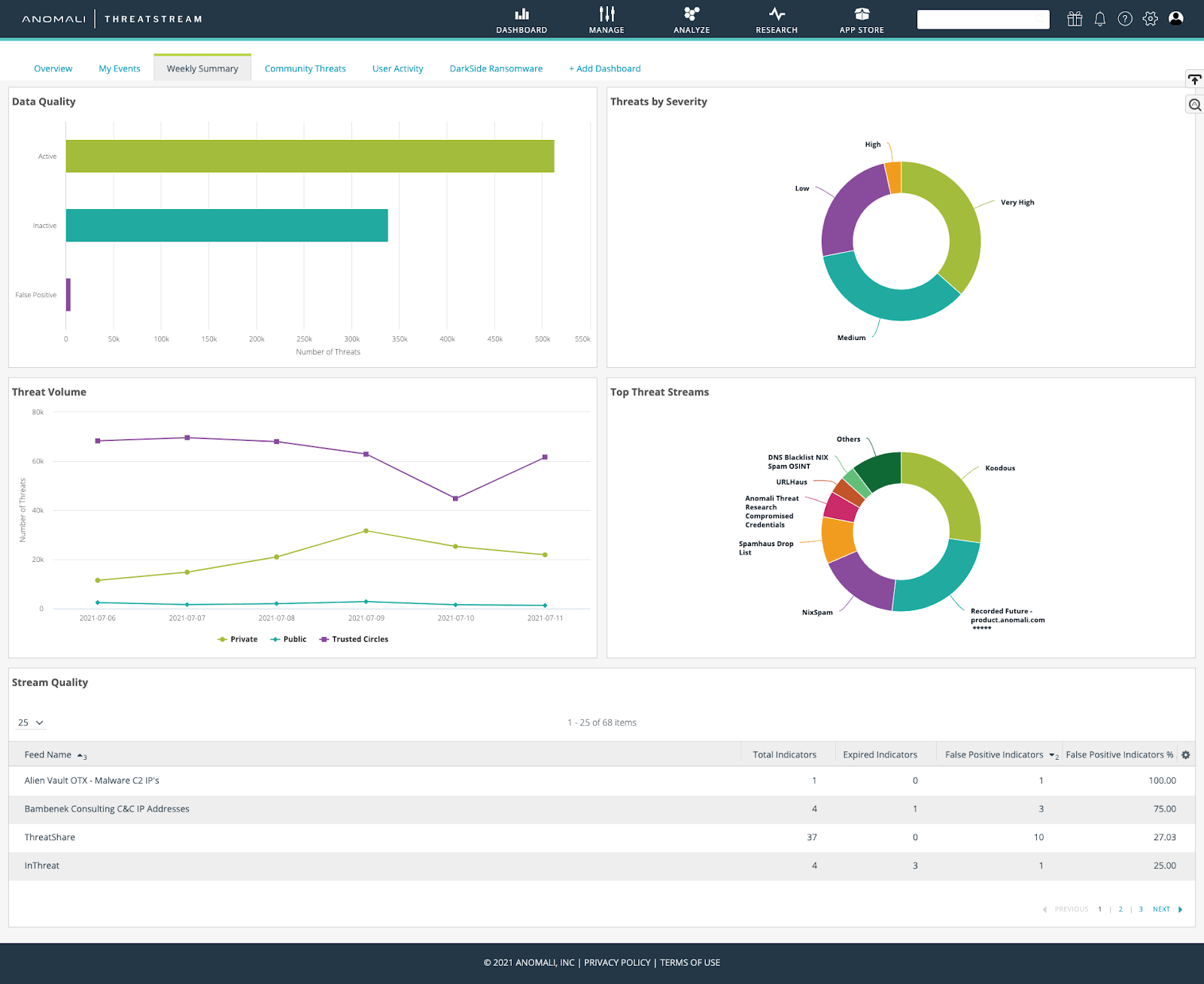
Figure 1. Anomali ThreatStream Dashboard
Some pros of Anomali ThreatStream are as follows:
- a great platform for researching security-related content
- indicators of compromise
- time-saving, and its automation makes the work easier
- intelligence-sharing facility
Some cons of Anomali ThreatStream are as follows:
- systems are taking up a lot of space, which makes it difficult for them to function normally.
- slow customer service
Cyware Virtual Cyber Fusion Center
Cyware Virtual Cyber Fusion Center is a next-generation approach to cybersecurity that combines all security functions, including threat intelligence, security automation, threat response, security orchestration, incident response, and others, into a single connected unit with the ability to bring together all constituting units for detecting, managing, and responding to threats in a coordinated and cooperative way.
To respond quickly to threats, modern businesses need to improve communication between their different security teams and share threat intelligence in real time. A cyber fusion-driven approach makes this possible by allowing the automatic intake of threat data from different sources and bringing together different security teams so that incidents and threats can be quickly found, ranked, and dealt with.
Threat intelligence, detection, analysis, hunting, and response are the key elements of Cyber Fusion Centers.
Some features of Cyware Virtual Cyber Fusion Center are listed below:
- Threat Actor Management
- Threat Actor Tracking Engi- Management Workflow for Cases
- Malware Management
- Incident Response & Management
- Triage Management
Some benefits of Cyware Virtual Cyber Fusion Center are as follows:
- regular updates
- security situational awareness
FireEye Helix
FireEye Helix is a security operations platform that is hosted in the cloud. This means that businesses can handle any event, from alert to fix. To unlock the full potential of security investments, FireEye Helix, a feature available with any FireEye solution, integrates your security products and enhances them with next-generation SIEM, orchestration, and cyber threat intelligence capabilities. It gives security teams the tools they need to easily do things like manage alerts, search, analyze, investigate, and report. It was created by security experts, for security specialists. FireEye Threat Analytics was the previous name for FireEye Helix.
FireEye Helix collects event data from both FireEye and non-FireEye parts of a security architecture with the help of frontline intelligence, rules, and analytics. This gives companies the information they need to decide which attacks are the most dangerous and how to respond to them. FireEye Helix streamlines all Security Operation Center (SOC) tasks from a single interface, including alert management, search, analysis, investigations, and reporting.
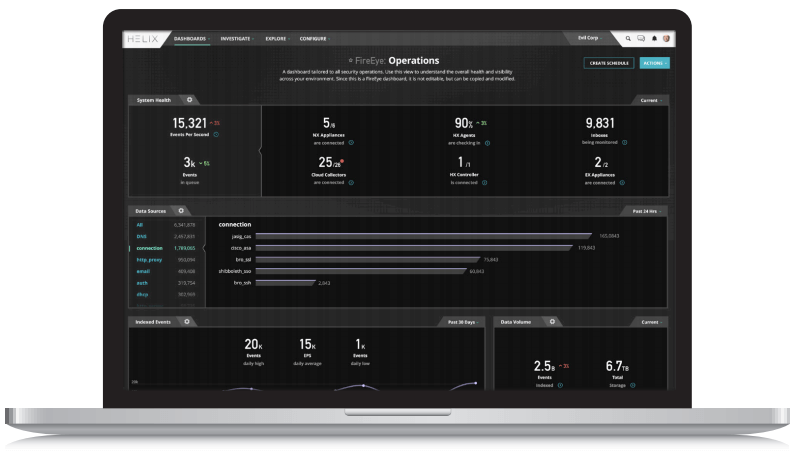
Figure 2 FireEye Helix Dashboard
Some capabilities of FireEye Helix are given below:
- Find your real adversaries and learn how they behave.
- accelerate your response to threats
- increase the effectiveness of current security investments
- utilize contextual threat intelligence to make wise decisions.
- increase endpoint and network visibility
- reduce operational costs
Some benefits of FireEye Helix are listed below:
- a great platform for combining threat intelligence, warnings, and metadata.
- helpful tech support
- being able to change quickly from Helix to endpoint
Some drawbacks of FireEye Helix are listed below:
- expensive licenses
- dashboard may use some improvement
Fortinet Forti SOAR
Fortinet, a market-leading cybersecurity company with headquarters in California, offers a wide range of products for SMBs, corporations, and MSPs. FortiSOAR, a potent SOAR solution that is a component of the Fortinet Security Fabric platform. It focuses on tool consolidation, security orchestration and automation, case management, and incident response.
FortiSOAR brings together all of an organization's tools, helps to streamline processes, and reduces alert fatigue, switching contexts, and the average time it takes to deal with problems. The FortiSOAR solution is very adaptable. More than 160 pre-built playbooks that can be readily modified using its drag-and-drop visual playbook builder are included, along with more than 350 integrations, over 3,000 automated process activities, and with the help of role-based dashboards and reporting tools, teams can keep track of metrics, evaluate performance, build data models, make weekly reports, and do a lot more.
Figure 3. FortiSOAR Dashboard
The main features of FortiSOAR are as follows:
- flexibility, adaptability, and simple third-party tool integration
- improved data understanding with a simple interfaced
- flexible configuration
- establishing team hierarchies and custom roles
- a solution for enterprise role-based incident management
The main advantages of FortiSOAR are listed below:
- completely customizable in every way
- matching scan results to notifications to speed up incident response
- flexibility to add additional fields to existing modules
- supportive service
The main disadvantages of FortiSOAR are listed below:
- Reports and dashboards can be more appealing visually.
- Complexity of playbook creation
IBM Security Resilient
The IBM Resilient Incident Response Platform (IRP) is a platform for orchestrating and automating incident response processes. It connects quickly and simply with the current IT and security investments in your company. It makes it possible for security alarms to go off right away and gives useful information about events and their context. It offers adaptive defense against sophisticated online attacks.
IBM Security Resilient keeps track of and organizes your incident response procedures so that you have the information you need to handle security events. It will help you plan and speed up a response by intelligently automating operations and connecting to other security solutions. It also helps you see and understand security problems so you can set priorities and take action.
Figure 4. IBM Resilient Incident Response Platform Dashboard
The primary features of the IBM Resilient Incident Response Platform are as follows:
- Manage incident response proactively using the Security module.
- Using the Privacy module, you may manage the rules for violation notice
- Understanding the environment with Incident Visualization
- Using the Action module, edit and automate
- Using visual workflows to streamline difficult tasks
The primary benefits of IBM Resilient Incident Response Platform are as follows:
- the solution is easy to use
- simple and flexible interface
- without human intervention, it may directly automate security occurrences.
- malware analysis feature
- it has excellent monitoring capabilities that make it simple to find concealed risks
Some drawbacks of IBM Resilient Incident Response Platform are as follows:
- need to generate reports manually
- scanty DSM modules
LogicHub SOAR
LogicHub is a cybersecurity company that started in 2016 and makes products for automated and intelligence-driven threat detection and response. Its security automation, orchestration, and response (SOAR) solution, called LogicHub SOAR, offers end-to-end automation and orchestration throughout the whole threat lifecycle, allowing security teams to work more effectively and efficiently together. SaaS, on-premises, or cloud deployment options are available for the solution.
The entire threat lifecycle, from detection and analysis to response and forensics, is fully automated by LogicHub SOAR. The solution includes a library with hundreds of pre-built playbooks and out-of-the-box connections with security products and platforms from third parties. Particularly notable is its case management function, which adds event context, proposed corrective actions, task management, and more to cases. The technology is very simple to integrate with numerous paid and open-source threat intelligence sources.
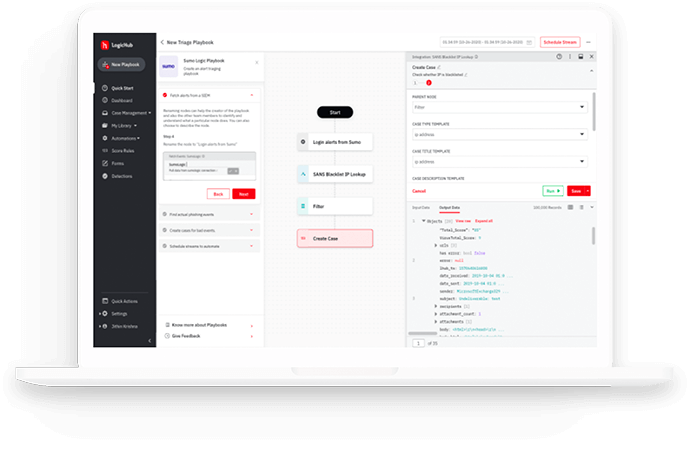
Figure 5. LogicHub SOAR Dashboard
Some capabilities of LogicHub SOAR are listed below.
- automated detection, triage and response
- adaptation to your entire security architecture
- automated reaction that is flexible
- constantly updated content
- playbook creator with recommendations and guidance
Some advantages of LogicHub SOAR are listed below.
- automation and security incident response solution
- support and service teams
- affordable pricing
- releasing updates/enhancements to it very frequently
Some disadvantages of LogicHub SOAR are listed below:
- time spent on implementation
- need to enhance UI color
Micro Focus ArcSight SOAR
ArcSight SOAR is a leading Security Orchestration, Automation, and Response Platform (SOAR) that seamlessly integrates automation, incident management, and orchestration of both technology and people. With the help of ArcSight SOAR, security teams may be able to respond faster to cyberattacks.
ArcSight SOAR makes it easier to manage security by making it faster to find threats and fix them. It also provides an automated incident response solution for security events that happen often.
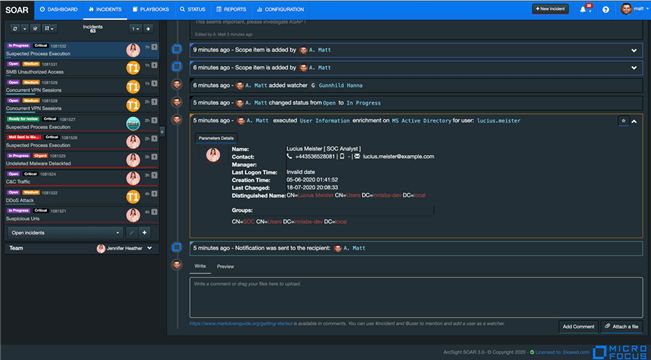
Figure 6. ArcSight SOAR Dashboard
ArcSight SOAR is easy to set up and can be easily added to your organization's existing technology stack. This tool can be changed to fit the needs of security teams and has an easy-to-use interface that supports many types of automation, analyst enhancement, collaborative investigation and response, and response.
The main features of ArcSight are as follows:
- Ease and Case Management
- Consolidation
- Automate for efficiency
- Reporting and Analytics
- Enable Collaboration
The main advantages of ArcSight are as follows:
- Reporting and Logs Analysis Capabilities
- protects endpoints devices from unauthorized access
- receiving incredibly helpful reports regularly
The main disadvantage of ArcSight is that dashboard and user interface need improvement.
Palo Alto Networks Cortex XSOAR
Global leader in business security solutions, Palo Alto Networks has its headquarters in California. Cortex XSOAR is a security orchestration, automation, and response solution that combines Demisto's powerful SOAR platform (which Palo Alto Networks bought in 2019) with native Cortex threat prevention and response capabilities, as well as advanced threat intelligence management. The platform is accessible for MSPs as a multi-tenant solution, in the cloud, or on-premises.
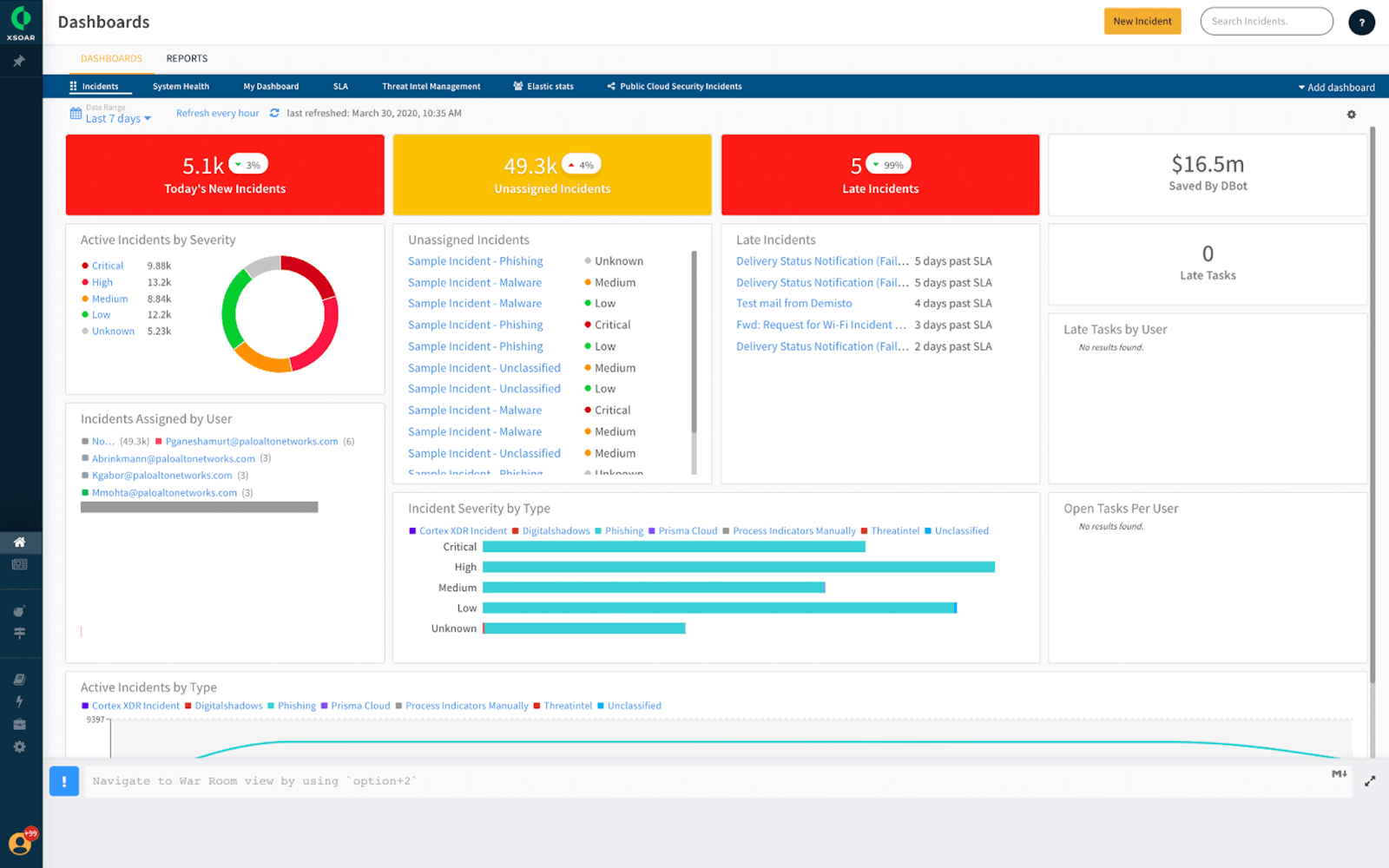
Figure 7. Cortex XSOAR Dashboard
With Cortex XSOAR SOC teams may manage and investigate occurrences, as well as automate incident response workflows and processes. All significant SIEMs may be integrated into the platform, which automatically correlates alerts and offers a "War Room'' for each incident where teams can work together to conduct real-time investigations. With the threat intelligence management (TIM) module of the platform, teams can use Palo Alto Networks' network sources and third-party feeds to put warnings into context. What's nice about the platform in terms of automation is that teams can decide whether to use the Cortex XSOAR marketplace, an ecosystem that allows users to browse and discover pre-built automation playbooks made by SOAR industry professionals, or customize their own integrations.
Some features of Cortex XSOAR are listed below:
- reducing time spent on managing threats
- provides guidance based on past incidents and analyst actions
- easy to orchestrate and automate incident response workflows
- can tie external threat intel to incidents in real time
Some pros of Cortex XSOAR are listed below:
- the ability to track IOC across different incidents
- regular updates
- dynamic playbook can reduce overall work
- saving time when investigating incidents
- an extensive list of integrations that are available out of the box
Some cons of Cortex XSOAR are given below:
- too much data on a single pane
- need more search areas to be more interactive and easy to navigate
Rapid7 InsightConnect
Rapid7 is a Boston-based cybersecurity company that helps keep client settings safe by using automation, analytics, and visibility. After buying SOAR provider Komand in July 2017, Rapid7 now offers InsightConnect, a powerful cloud-based SOAR solution that runs on the Insight Platform and lets SOC teams streamline security procedures and workflows quickly and effectively.
InsightConnect is meant to make it easier for teams to talk to each other, give more visibility across environments, and speed up tasks that need to be done quickly. One of the most important parts of the solution is that analysts can automate processes without writing any code by using more than 200 plugins and fully customized workflows. However, what makes InsightConnect so intriguing is its ChatOps feature, which interfaces with teamwork tools like Slack and Microsoft Teams to let SOC teams build chat-driven workflows, collaborate more easily, and produce better results.
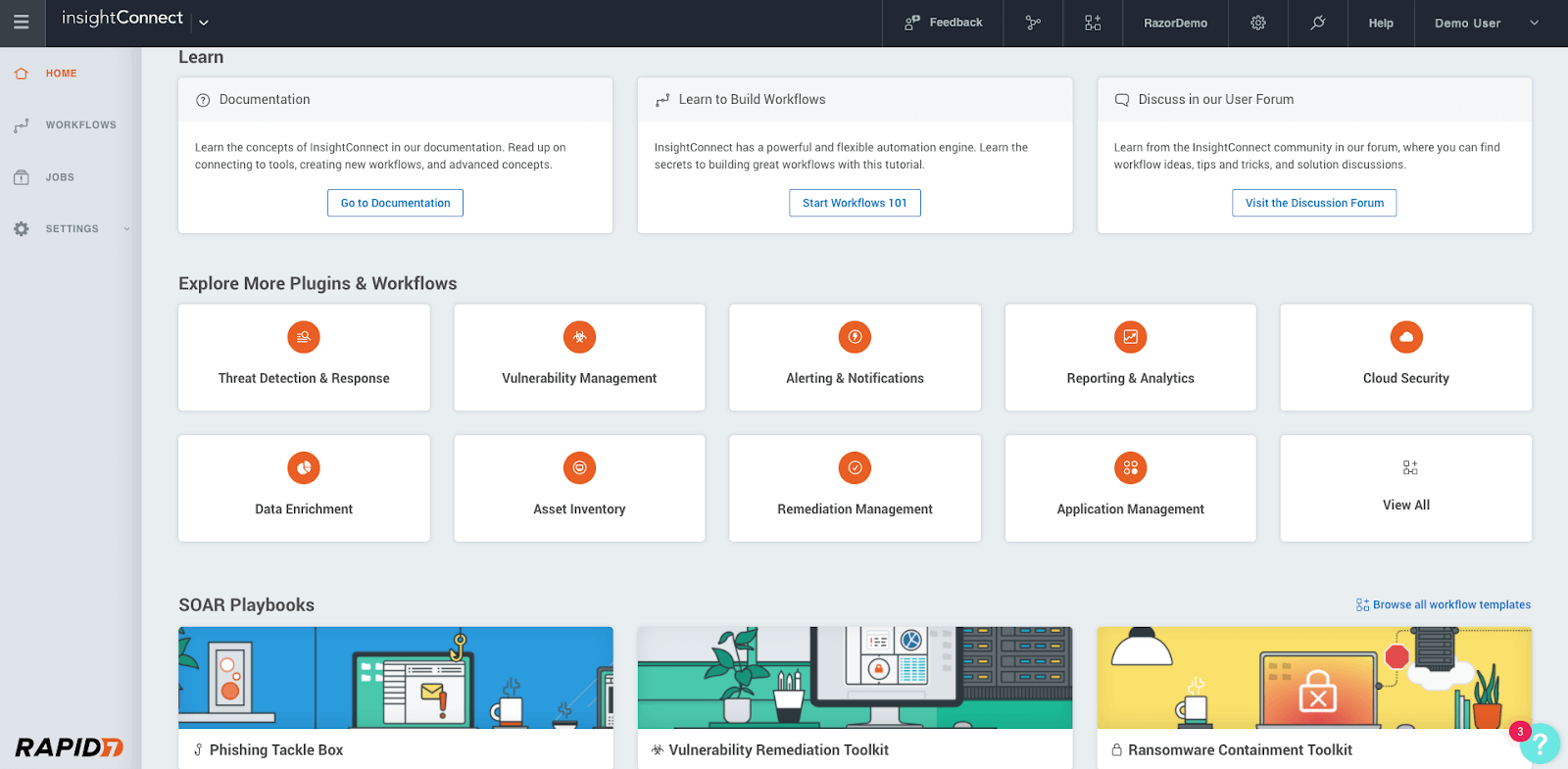
Figure 8. Rapid7 InsightConnect Dashboard
The main capabilities of Rapid7 InsightConnect are as follows:
- a library of customizable workflows
- integrating IT and Security Systems
- vulnerability management
- cloud security
- orchestration and automation
The main advantages of Rapid7 InsightConnect are as follows:
- user-friendly solution
- deep visibility across environments
- the wealth of integrations
- reducing phishing emails
The main disadvantages of Rapid7 InsightConnect are as follows:
- need more out-of-the-box integrations
- some issues with the discovery scan
Siemplify SOAR Platform
Siemplify is a top SOAR vendor that was started in Tel Aviv and bought by Google Cloud in January 2022. Its goal is to improve the user experience of SOC teams around the world while also streamlining and improving security operations. Its Security Operations Platform, which can be used in the cloud or as a software as a service (SaaS), brings together several tools, automates routine tasks, and speeds up response.
The platform has all of the basic SOAR features, such as security orchestration, playbooks that are easy to change, correlation and prioritization of incidents based on machine learning, reporting and dashboards, case management, and suggested responses. But what distinguishes the platform from rivals is how well it performs in the areas of alert triage, contextual alert enrichment, and machine learning capabilities, organizing alerts in a threat-centric manner and enhancing them with potent threat knowledge. The software supports hundreds of integrations and is also quite customizable.
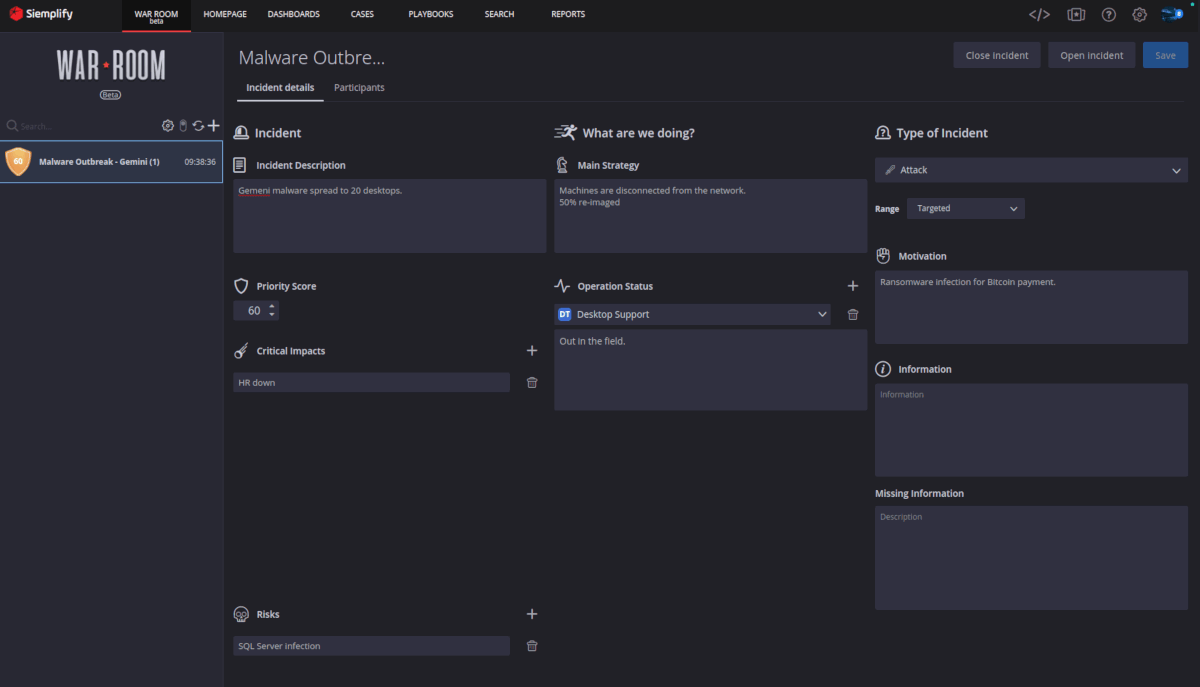
Figure 9. Siemplify SOAR Dashboard
The primary features of Siemplify SOAR are as follows:
- With case management investigating security alerts from detection tools
- Integrated Threat Intelligence
- Focusing on threats quickly and visualizing the target
- Building playbooks quickly to automate repetitive tasks and ensuring consistency in response procedures
The primary benefits of Siemplify SOAR are as follows:
- automation of repetitive processes
- alert triage quality
- simple to use and configure
- customized playbooks
- powerful and smooth to operate
The primary drawbacks of Siemplify SOAR are as follows:
- need to install regularly and use new integrations
- search function can be improved
Splunk SOAR
Splunk is a well-known software company that has been around since 2003. Its strong data platform helps businesses search, monitor, and analyze data. Splunk's advanced SOAR solution, which used to be called Splunk Phantom (as a nod to the fact that it bought SOAR provider Phantom Cyber in 2018), makes it easy for SOC teams to orchestrate and automate security procedures and work more closely with other teams.
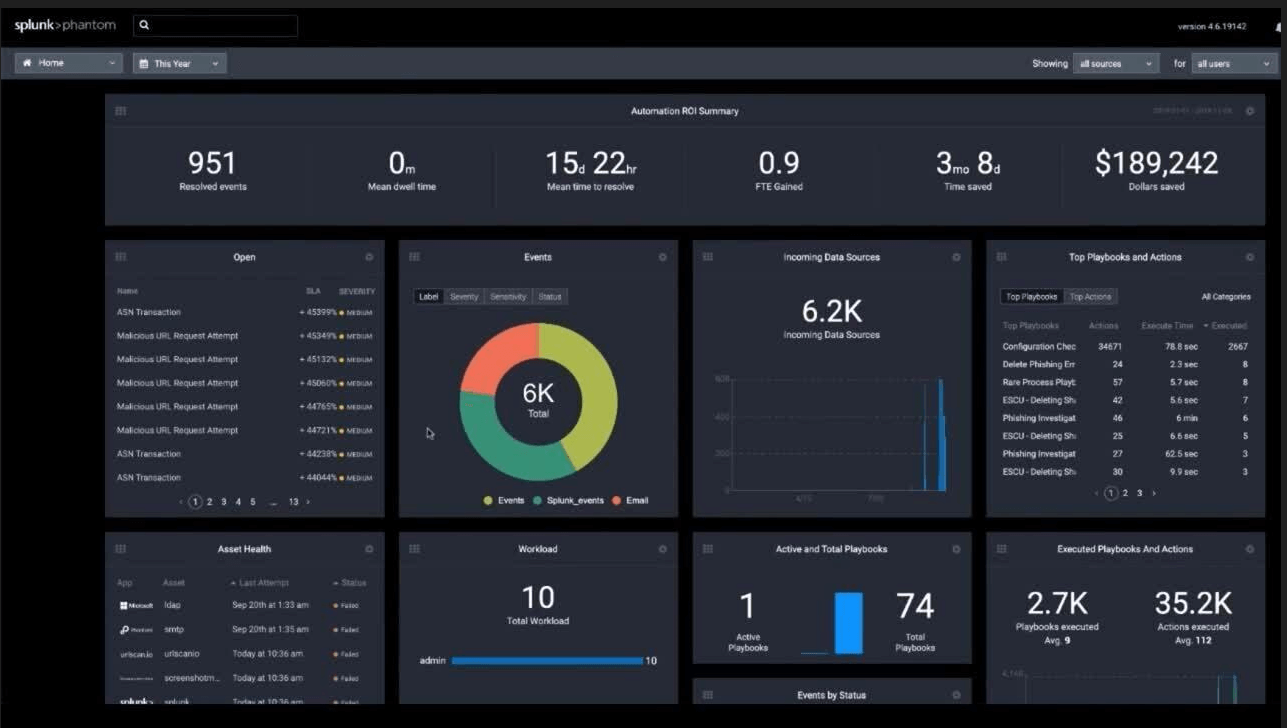
Figure 10. Splunk SOAR Dashboard
Splunk SOAR connects to third-party security solutions via its app model, supporting integrations with more than 350 products and 2,100 actions via its resource library, Splunkbase. The solution also includes 100 playbooks that are ready to use right out of the box and has a built-in visual editor for code-free editing. The cybersecurity research team at Splunk SURGe has also made the software's case management and threat intelligence even better. Splunk SOAR's adjacent SOAR mobile app, however, is what makes it unique. With it, teams can respond to security alarms, triage events, run playbooks, and talk to coworkers right from their phones, whenever and wherever they are.
Some features of Splunk SOAR are given below:
- Supporting cloud, on-premises, or hybrid deployments
- Utilizing security and IT tools to carry out operations in seconds rather than hours
- More than 350 third-party products are integrated, and more than 2,800 different automatable activities are supported
- Creating playbooks using visual, intuitive editing
Some pros of Splunk SOAR are listed below:
- Easy to use playbooks
- Easy to integrate within the Splunk ecosystem
- Highly mature automation and orchestration module
- Reducing work time with regular actions.
Some cons of Splunk SOAR are given below:
- hard to integrate with other tools outside Splunk Ecospace
- visibility of user access is not that much
Swimlane SOAR
Swimlane is a top-tier SOAR provider with a Colorado base that focuses on security automation. Its low-code SOAR platform is made to collect alerts from a variety of sources and automate manual operational workflows and incident response processes. This makes SOC analysts' jobs easier by reducing the amount of work they have to do.
The solution has both strong case management and advanced dashboards for reporting for SOC analysts. The configurable and open platform of the Swimlane SOAR platform, on the other hand, makes it stand out from its competitors and lets SOC teams use it for a wide range of use cases and problems. The platform also offers hundreds of free out-of-the-box integrations.
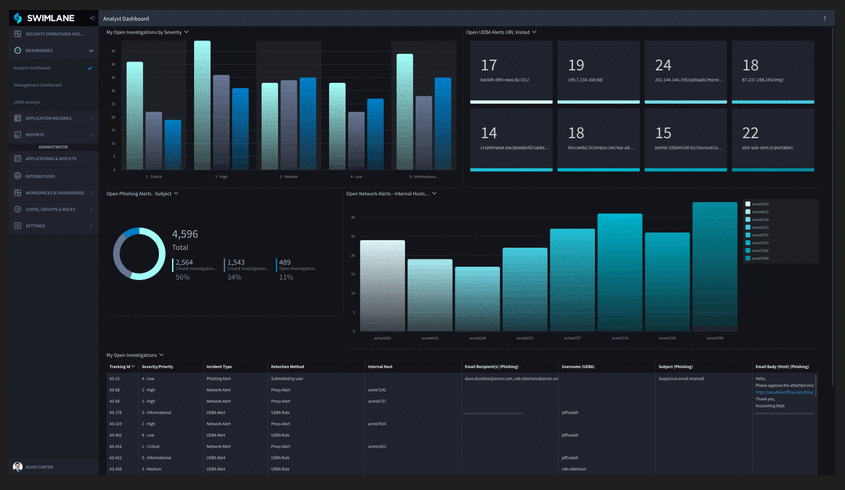
Figure 11. Swimlane SOAR Dashboard
Some capabilities of Swimlane SOAR are listed below:
- can be deployed on-premises or via cloud
- Diagnosing and resolving incidents without the need for human interaction
- Gathering information related to threats in order to gain further information on remedies
- Administrators can access and arrange incident-related data to generate reports or make the data easier to navigate
The main benefits of Swimlane SOAR are listed below:
- easy playbook configuration
- Flexibility of workflows and integrations
- increased efficiency having workflows and tasks pulled into a single pane
- clean interface and the customer success team
The main drawback of Swimlane SOAR is the difficulties it poses for users that aren't familiar with Python.
ThreatConnect SOAR Platform
ThreatConnect was started in 2011 as a cybersecurity company that focuses on threat intelligence and analytics as well as strong solutions for cyber risk quantification, threat intelligence, and SOAR. Its Security Orchestration, Automation, and Response (SOAR) platform is made to effortlessly interact with security technologies and give businesses the context and coordination they need to effectively analyze and address attacks.
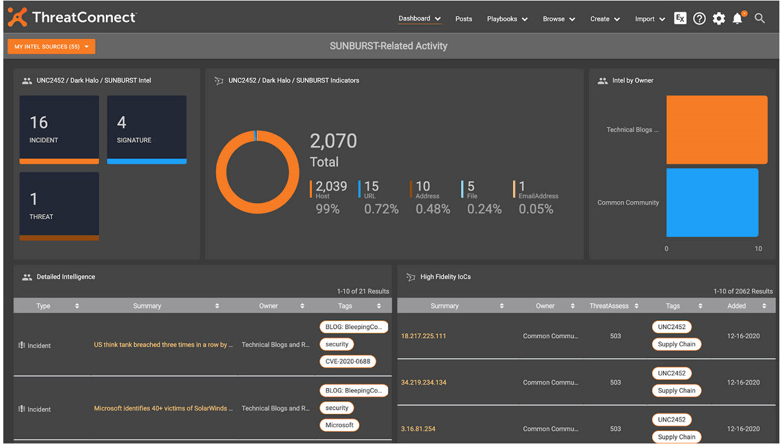
Figure 12. ThreatConnect SOAR Dashboard
ThreatConnect's SOAR platform shines in its threat intelligence management skills, in particular as an expert in threat intelligence and analytics. SOC teams can benefit from context-rich threat intelligence from a variety of streams and sources, along with tight integration between their case management and threat intelligence capabilities, in addition to security orchestration and automation.
Some features of ThreatConnect are as follows:
- Decreasing Time To Response and Remediation with ThreatConnect SOAR
- Saving time by Automating Manual Tasks with Playbooks
- Maximizing the Amount of Threat Intel Collected from Day-to-Day Operations
Some advantages of ThreatConnect are as follows:
- easy threat detection via actionable analysis
- improves the process and workflow
- playbook engine works smoothly
- helps achieve better security
Some disadvantages of ThreatConnect are as follows:
- prices could be a bit lower
- need improvement for the reporting engine
ThreatQuotient ThreatQ
The end result is less noise, threats with clear priorities, and the ability to use high-quality data to automate procedures.
ThreatQuotient improves security operations by bringing together different data sources, technologies, and teams to make finding and responding to threats faster. ThreatQuotient's data-driven security operations platform helps teams prioritize, automate, and work together on security events by putting existing procedures and technology into a single workspace. It also enables more focused decision-making and makes the most of scarce resources. ThreatQuotient's market-leading data management, orchestration, and automation features can also be used as a threat intelligence platform. It can be used for things like incident response, threat hunting, spear phishing, alert triage, and vulnerability prioritization. ThreatQuotient was established in Northern Virginia, and its foreign operations are run out of locations in MENA, APAC, and Europe.
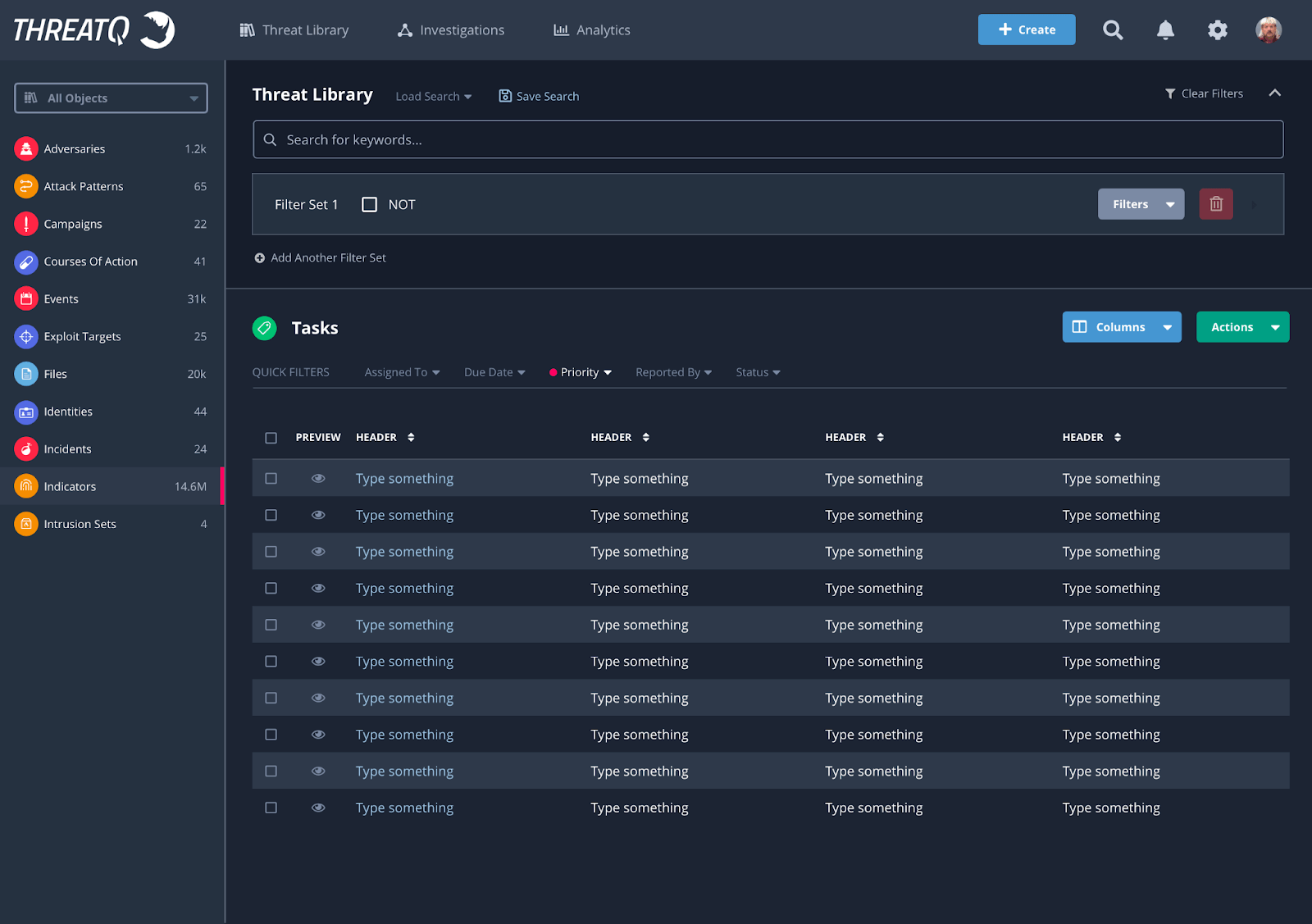
Figure 13. ThreatQuotient SOAR Dashboard
The main features of ThreatQuotient SOAR are as follows:
- Customer-defined configuration and integrations to work with processes and tools
- Open and extensible architecture enables robust ecosystem
- Threat library that automatically scores and prioritizes threat intelligence based on parameters you set
The main advantages of ThreatQuotient SOAR are as follows:
- extremely responsive customer service
- dedicated team to address operational needs
- great library option for new users
- instant feed of data
Why Do You Need to Integrate Your NGFW with SOAR?
Many of SOAR's security measures are already used by businesses, but the approach can sharpen and strengthen them so that you are better prepared for all kinds of attacks and threats. There is no such thing as perfect security, but there are ways to put as many layers of protection between your business and its most important data as possible.
In order to make your security solutions as effective as they potentially can be, SOAR is made to fill in all the gaps. The strategies can cut down on false positives, giving your team more time to concentrate on important tasks. It can automate processes that don't require human involvement and produce overall significantly stronger results. By integrating your next-generation firewall (NGFW) with a SOAR solution, you can more quickly identify and respond to security incidents. Together with automation, SOAR's expanded data context may minimize Mean Time to Detect (MTTD) and Mean Time to React (MTTR) (MTTR). By recognizing and responding to threats more quickly, their impacts may be reduced. Enterprises may also benefit from more efficient issue management and quick risk mitigation. The SOAR design allows for faster response times and more accurate interventions. Due to fewer mistakes, less time is spent fixing problems.
Can Zenarmor be Integrated with SOAR Tools?
Yes. Zenarmor next-generation firewall provides SOHO or Business subscriptions with Stream Reporting Data feature. You can easily stream reporting data to an external syslog server or a SOAR tool.
Another important feature of Zenarmor is its RESTful API support. Using the Zenarmor API, users can build their own connections between the firewall and other security solutions. Requests are authenticated using API keys.
Zenarmor is a completely software-based quick firewall that can be installed almost anywhere. It's easy to set up on any platform that can connect to the internet because it doesn't need any hardware, is all-in-one, only uses software, is light, and has a simple design. Whether virtual or bare metal, on-premises or in the cloud.
