What is Cloud Security?
Increasing numbers of businesses are recognizing the many commercial advantages of transferring their systems to the cloud. Cloud computing enables firms to operate at scale, minimize technological expenses, and implement flexible systems that provide a competitive advantage. 76% of businesses already use two or more cloud providers. 35% of enterprises have more than 50% of their workloads in the cloud, and 29% want to increase this figure to 75% in the next 12 to 18 months.
However, enterprises must have total confidence in their cloud computing security and ensure that all data, systems, and applications are safeguarded against data theft, leakage, corruption, and deletion.
Malicious actors recognize the advantages of cloud-based targets and are increasingly probing them for vulnerabilities. In 2020, there was a 600% increase in attacks against cloud services. In the last several years, cloud misconfigurations alone have cost organizations about $5 trillion and led to the disclosure of over 33 billion pieces of user information. So it should come as no surprise that the cloud security industry is estimated to surpass $68 billion by 2025.
Cloud security provides all the capabilities of conventional IT security, allowing organizations to use the numerous benefits of cloud computing while staying safe and meeting all data privacy and compliance standards. Cloud providers do not handle everything, despite taking on several security responsibilities from customers. Even non-technical users must thus educate themselves on cloud security. However, users are not solely accountable for cloud security. Understanding the breadth of your security responsibilities will make the overall system considerably safer.
In this article, we will explain what cloud security is, why organizations need cloud security, what types of cloud security solutions should be implemented, the challenges and benefits of cloud security implementation, the details of the shared responsibility model, and the best practices for cloud security deployment. Lastly, we will outline the responsibilities and required skills of a cloud security engineer.
What is Meant by Cloud Security?
Cloud security is a cybersecurity discipline that focuses on safeguarding cloud computing platforms. This involves maintaining the confidentiality and safety of data across infrastructure, apps, and platforms against external and internal security risks. In cloud security, these systems must be secured by cloud providers and their customers, whether they are individuals, small- to medium-sized businesses, or enterprises. The complete breadth of cloud security is intended to safeguard the following assets:
-
Operating systems (OS)
-
Data storage. hard disks, etc.
-
Physical networks include routers, electrical power, cabling, and temperature controls, among other components.
-
Data servers
-
Applications, conventional software services like email, tax software, productivity suites, etc.
-
Runtime environments, program execution, and maintenance
-
Computer virtualization Frameworks, like virtual machine software, host computers, and guest machines.
-
Data, all information that is saved, changed, and accessed
-
Middleware, administration of application programming interface (API)
-
End-user devices like computers, mobile devices, and Internet of Things (IoT) devices.
How Does Cloud Security Work?
Since cloud security involves a vast array of technologies and procedures, there is no one explanation for how it works. The most crucial aspect of cloud security is ensuring that only authorized users may access cloud-stored data. Each cloud security measure accomplishes at least one of the following:
-
Permit data recovery in the event of data loss
-
Protect storage media and networks against data theft
-
Prevent human mistake or carelessness that results in data loss.
-
Reduce the effect of data and system breaches
Enterprises use the following instruments and methods for cloud security:
-
Identity and Access Management: Identity and access management (IAM) refers to the permissions granted to user accounts for gaining access. Managing user account authentication and authorization also applies here. Access controls are essential for preventing authorized and unauthorized individuals from entering and compromising sensitive data and systems. IAM encompasses password management, multifactor authentication, and other mechanisms.
-
Threat Intelligence: Governance focuses on the prevention, identification, and mitigation of threats. Aspects such as threat intelligence may aid SMBs and organizations in identifying and prioritizing threats to keep vital systems adequately protected. However, even individual cloud customers might benefit from adopting rules and training on safe user conduct. These pertain mostly to corporate situations, although standards for safe usage and threat response may be beneficial for any user.
-
Data Security: Cloud data security encompasses the technological component of threat avoidance. Tools and technology enable providers and customers to place barriers between sensitive data's accessibility and visibility. Encryption is among the most potent of these techniques. Encryption scrambles your data so that only someone with the encryption key can decipher it. If your information is lost or stolen, it will be illegible and meaningless. Data transit safeguards such as virtual private networks (VPNs) are also stressed in cloud networks.
-
Disaster Recovery: Planning for data retention (DR) and business continuity (BC) includes disaster recovery methods in the event of data loss. Methods for data redundancy, including backups, are essential to every disaster recovery and business continuity strategy. In addition, having technological mechanisms in place to ensure continuous operations might be beneficial. Equally essential to a comprehensive BC strategy are frameworks for validating the integrity of backups and recovery instructions for employees.
-
Compliance: Compliance with the law relies on preserving the privacy of users, as mandated by legislative agencies. Governments are aware of how important it is to stop the commercial exploitation of user data. Therefore, firms must adhere to rules to comply with these policies. The use of data masking, which obscures the identity of data using encryption techniques, is one option.
Why is Cloud Security Important?
IT professionals are still worried about moving more data and apps to the cloud because of security, governance, and compliance issues. They are concerned that extremely sensitive corporate information and intellectual property may be exposed owing to inadvertent leaks or the sophistication of cyberattacks.
Cloud adoption success is contingent on implementing effective remedies to guard against current attacks. When assuring business continuity, cloud security solutions and best practices are essential regardless of whether companies work in a public, private, or hybrid cloud environment.
The protection of data and business information, such as client orders, confidential design blueprints, and financial records, is a vital aspect of cloud security. Preventing data breaches and theft is essential for retaining consumer confidence and safeguarding the assets that contribute to a company's competitive edge. The capacity of cloud security to protect valuable data and assets makes it essential for every business transitioning to the cloud.
Security in cloud computing is essential for any organization seeking to secure its apps and data from malicious attackers. Maintaining a robust cloud security posture enables enterprises to reap the advantages of cloud computing, which are now generally acknowledged. By default, the majority of cloud service providers adhere to standard security policies and proactively defend the integrity of their servers. However, enterprises must take precautions while safeguarding cloud-based data, apps, and workloads. When managing client information, regardless of where it is housed, companies may face major governance and compliance risks if they do not take proactive actions to strengthen their cloud security.
What are the Benefits of Cloud Security?
The benefits of cloud security include fewer upfront expenses, decreased continuing operational and administrative costs, simpler scalability, higher stability, and availability, and enhanced DDoS defense. The primary advantages of cloud security are listed below:
-
Increased Reliability: Cloud computing services provide the highest level of reliability. With the proper cloud security measures in place, users may securely access cloud-based data and apps regardless of their location or device.
-
Centralized Protection: As cloud computing centralizes apps and data, so too does cloud security centralize protection. When dealing with shadow IT or BYOD, cloud-based corporate networks include various devices and endpoints that might be challenging to manage. Managing these entities centrally improves traffic analysis and web filtering, simplifies network event monitoring, and reduces software and policy upgrades. When disaster recovery plans are handled in a centralized location, they may be readily developed and executed.
-
Reduced Administration: When you choose a reliable cloud services provider or cloud security platform, you can say goodbye to manual security setups and frequent security upgrades. When you migrate these responsibilities to the cloud, all security administration takes place in a centralized location and is administered on your behalf.
-
Reduced Costs: One of the advantages of cloud storage and security is that it reduces the need to invest in specialized hardware, hence reducing expenses. This not only minimizes capital expenditures but also decreases administrative costs. Cloud security provides proactive security features that enable protection 24 hours a day, 7 days a week with little or no human interaction. Previously, IT staff had to respond to security concerns as they arose.
What are the Cloud Security Challenges?
Nearly all businesses have embraced cloud computing to varying degrees. With the increased embrace of the cloud, however, comes the requirement to ensure that the organization's cloud security plan is capable of guarding against the most prevalent cloud security risks. Major cloud security challenges are explained below:
-
Access Control and Shadow IT: While organizations are able to control and limit access points across on-premises systems, implementing the same restrictions in cloud environments is problematic. This is risky for firms that do not have bring-your-own-device (BYOD) regulations and provide unfiltered access to cloud services from any device or geographic location. In contrast to an organization's on-premises infrastructure, its cloud-based installations are immediately accessible through the public Internet and are located outside the network perimeter. This is advantageous for the accessibility of this infrastructure to workers and customers but also makes it simpler for an attacker to obtain unwanted access to a company's cloud-based resources. Inadequate security configuration or compromised credentials might allow an attacker to get direct access, sometimes without the organization's awareness.
-
Unsafe Interfaces and APIs: Cloud service providers (CSP) often provide their clients with a variety of application programming interfaces (APIs) and interfaces. These interfaces are often well-documented to make them user-friendly for CSP clients. However, this raises significant problems if a client has not adequately protected the cloud-based infrastructure's interfaces. A cybercriminal may also utilize the material intended for the client to find and exploit possible access and exfiltration techniques for sensitive data from the cloud environment of an enterprise.
-
Inadequate Visibility: The cloud-based resources of an organization are situated outside the corporate network and operate on an infrastructure that the organization does not control. Consequently, many standard network visibility technologies are ineffective in cloud settings, and many enterprises lack cloud-specific security capabilities. This may hinder an organization's capacity to monitor and safeguard cloud-based resources against attack. It is easy to lose track of who is accessing your data since many cloud services are accessible outside corporate networks and by third parties.
-
Cloud-native Breaches: Unlike on-premises breaches, cloud-based data breaches often include the use of cloud-native capabilities. A cloud-native breach is a series of actions performed by an adversarial actor in which they "land" their attack by exploiting bugs or vulnerabilities in a cloud deployment without using malware, "expand" their access through improperly configured or protected interfaces to locate valuable data, and "exfiltrate" that data to their storage location.
-
Automation, DevSecOps, and DevOps: Early in the development cycle, organizations that have adopted the highly automated DevOps CI/CD culture must ensure that the relevant security measures are established and integrated into code and templates. After a workload has been put into production, implementing security-related modifications might compromise the organization's security posture and extend the time to market.
-
Changeable Workloads: Cloud assets are dynamically provided and retired at scale and velocity. Traditional security methods are incapable of imposing protection requirements in a flexible and dynamic environment with ephemeral and ever-changing workloads.
-
External Data Sharing: The cloud is intended to facilitate data exchange. Numerous clouds provide the ability to expressly invite a collaborator by email or to give a link that allows anybody with the resource's URL to access it. This ease of data sharing is a benefit, but it also poses a significant cloud security risk. It is difficult to limit access to the shared resource when link-based sharing is used, which is a common choice since it is simpler than inviting each intended collaborator individually. The shared link may be sent to a third party, stolen as part of a cyberattack, or guessed by a cybercriminal, so granting illegal access to the shared resource. In addition, it is difficult to cancel access from a single receiver of a shared link when using link-based sharing.
-
Misconfiguration: In 2019, 86% of hacked data was due to misconfigured assets, making the accidental insider a major concern for cloud computing settings. Misconfigurations might include keeping default administrator passwords in place, or not defining suitable privacy settings. Numerous individuals have highly inadequate password security, including password reuse and the usage of insecure passwords. This issue exacerbates the effects of phishing attempts and data breaches since it permits the use of a single stolen password across several accounts.
As enterprises become more dependent on cloud-based infrastructure and apps for critical business processes, account compromise is one of the most significant cloud security threats. An attacker with access to an employee's credentials may get access to critical data or functionality, and a customer's credential breach grants complete access to their online account. In addition, cloud technology often hinders enterprises' capacity to recognize and react to these risks as effectively as on-premises infrastructure.
-
Cyber Attacks: Cybercriminals choose their targets depending on the anticipated profitability of their attacks. Cloud-based infrastructure is immediately accessible from the public Internet, is often inadequately protected, and includes an abundance of sensitive and important information. In addition, the cloud is used by several businesses, which means that a successful assault may be replayed multiple times with a high likelihood of success. Consequently, cloud installations are a frequent target of cyber attacks.
-
Insider Threats: Insider dangers are a significant security concern for any company. A malevolent insider has already been granted access to an organization's network and some of its key resources. This degree of access is what most attackers use to show themselves to their target, making it difficult for an unprepared business to discover a hostile insider. Even more challenging is the discovery of a malicious insider in the cloud. With cloud deployments, organizations lost control over their underlying infrastructure, rendering ineffective many conventional security measures. This, coupled with the fact that cloud-based infrastructure is readily accessible from the public Internet and often afflicted by security misconfigurations, makes it even more challenging to discover malevolent insiders.
-
Denial of Service Attacks: The cloud is vital to the operations of many businesses. They use the cloud to store mission-critical data and execute crucial internal and external apps. This implies that a successful Denial of Service (DoS) attack on cloud infrastructure is likely to have a significant effect on a variety of businesses. Therefore, DoS attacks when the attacker demands a ransom to terminate the attack represent a major risk to the cloud-based resources of a company.
-
Compliance: Regulatory compliance management is usually a cause of difficulty for organizations implementing public or hybrid cloud installations. Overall responsibility for data privacy and security remains with the organization, and excessive reliance on third-party solutions to handle this component might result in expensive compliance difficulties.
-
Multitenancy: Public cloud environments contain various client infrastructures under the same roof, therefore it is possible for hostile attackers to penetrate your hosted services while attacking other enterprises. If a cloud platform that operates on a multi-tenancy model (Public cloud) fails to isolate the data of its users owing to a software or system weakness, this results in a security breach that enables a user to readily access the data of other tenants.
Lack of appropriate traffic and bandwidth segregation makes the public cloud multi-tenancy system more vulnerable. Malicious users may thus target co-users in the same cloud data center, and the present procedures to limit unauthorized access are inadequate to scale this multi-tenancy system.
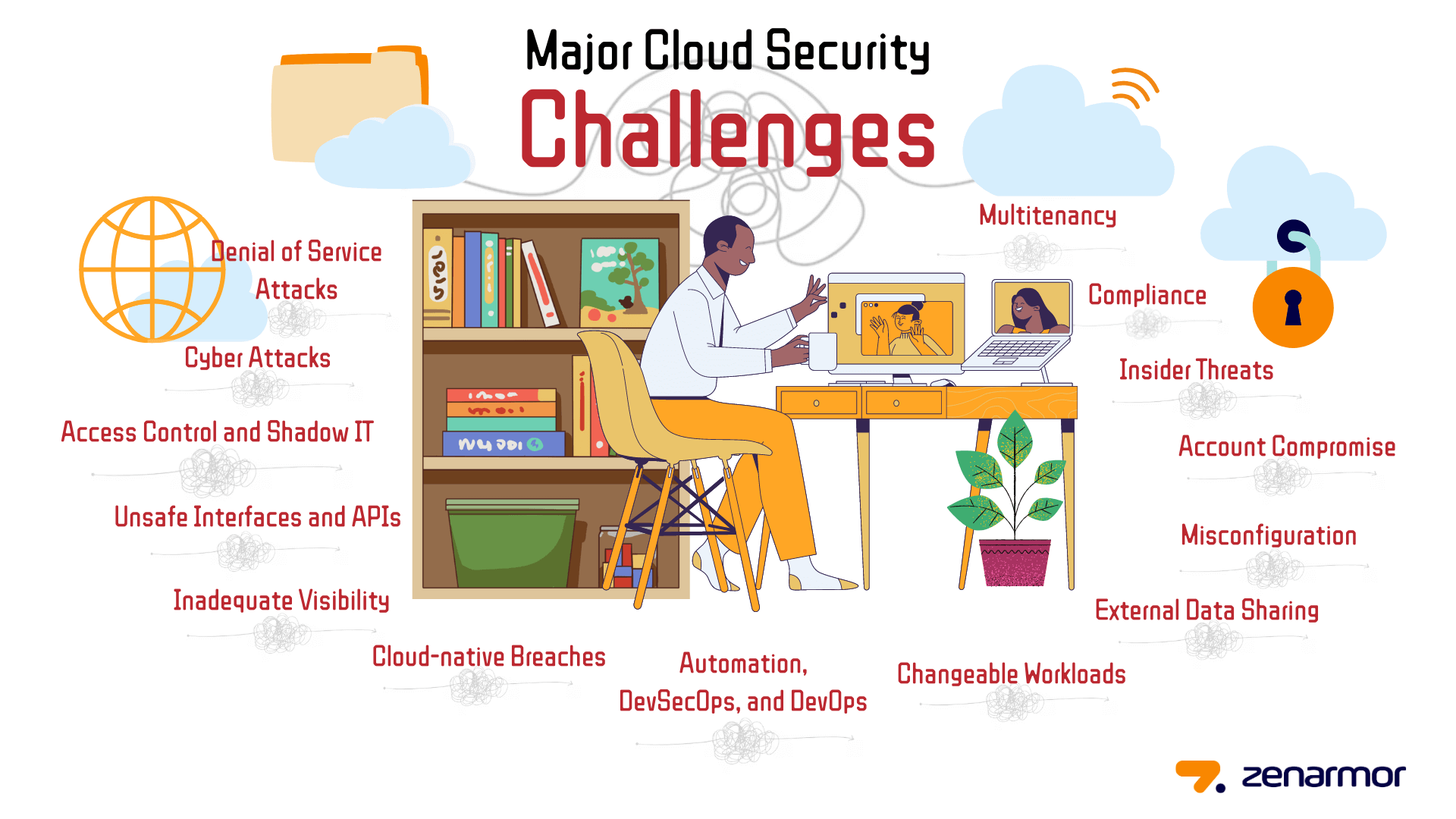
Figure 1. Cloud Security Challenges
What is the Shared Responsibility Model?
Both the customer and the cloud service provider share responsibilities for providing security in the cloud.In the Shared Responsibility Model, there are essentially three types of responsibilities:
-
those that are always the provider's
-
those that are always the customer's, and
-
those that change depending on the service model: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS).
The precise allocation of cloud security obligations is determined by the specifics of the cloud service a client is using. A cloud client has stronger security responsibilities in an Infrastructure as a Service (IaaS) model than in a Software as a Service (SaaS) one, for instance.
The provider is always responsible for the security of the infrastructure itself, as well as access to, patching of, and configuration of the physical hosts and physical network on which the compute instances and other resources operate and are stored.
Monitoring users and their access entitlements (identification and access management), protecting cloud accounts from unwanted access, encrypting and protecting cloud-based data assets, and managing its security posture are always the customer's security obligations.
| Service Type | CSP Responsibility | Customer Responsibility |
|---|---|---|
| IaaS | Security of all infrastructure components | Security of any application installed on the infrastructure (e.g. OS, applications, middleware) Endpoints, user and network security, workloads, and data |
| PaaS | Platform security, including all hardware and software | Security of applications developed on the platform. Endpoints, user and network security, and workloads |
| SaaS | Application security | Endpoints, user and network security,misconfigurations, workloads and data |
Table 1. CSP and Customer Responsibilities on Cloud Services
What is Shared Responsibility Model for Infrastructure on AWS?
The infrastructure services offered by Amazon include computation, storage, networking, and associated capabilities. Using Amazon EC2 as an example, the user may install and configure their own operating system and run whatever apps they choose on top of it.
Because EC2 provides the client with a high level of access and control (i.e., down to the operating system level), they place a significant amount of security responsibility on the customer. In these deployment situations, the user is responsible for safeguarding their operating system and any services under their control, including Elastic Block Store Inside their virtual private cloud (VPC), they use elastic block storage (EBS), auto-scaling, and networking infrastructure.
AWS is responsible for safeguarding its physical infrastructure, though. This consists of physical servers, networking, and virtualization technologies.
What is Shared Responsibility Model for Containers on AWS?
EC2 is used by containerized services, which offer an extra layer of abstraction. In this instance, the client is not responsible for managing their operating system or platform.
A cloud client has a lesser degree of security responsibility under this approach than under the prior paradigm. They lose sight and control over their operating system, therefore AWS assumes responsibility for it. Under this arrangement, the client has primary responsibility for firewall setup and data security (i.e. using encryption and access management).
What is Shared Responsibility Model for Abstracted Services on AWS?
For abstracted services, such as Amazon S3 and Amazon DynamoDB, the customer is generally responsible for setting the service's security correctly. For instance, if a client configures DynamoDB using user credentials that are readily guessed, they would be liable for any resultant data breach.
What are the Types of Cloud Security Solutions?
Moving operations to the cloud enables organizations to do business with a worldwide client base and staff in a cost-effective manner. However, cloud computing presents new security concerns that need appropriate management solutions. These solutions provide insight across several cloud environments and automate the discovery of vulnerabilities and configuration/compliance concerns. Cloud security solutions are software applications that safeguard cloud infrastructures and identities, discover and repair vulnerabilities, thwart attacks, and aid in incident response. The types of cloud security solutions that your organization may use to enhance its security posture are outlined below:
-
Secure Access Service Edge(SASE): Secure Access Service Edge (SASE) is a more recent solution to cloud security that minimizes latency for distant users by review and authorize traffic at a nearby enforcement point, rather than routing all traffic to a data center for inspection and then sending it back. This is especially advantageous if corporations keep work-from-home policies in the aftermath of the COVID-19 epidemic, despite the fact that these policies are expensive and labor-intensive to implement and maintain. Therefore, SASE is a rising cloud security solution among enterprises.
-
Cloud Access Security Brokers: Cloud Access Security Brokers (CASB) let security experts extend corporate security standards to cloud apps. They intervene between the cloud service provider and the user to monitor data access, regulatory compliance, and virus detection. Four important pillars addressed by CASB are as follows:
-
Threat Protection: CASB can identify aberrant user activity for early identification of a compromised account or insider threat using behavior analytics. They identify and prohibit the uploading or sharing of viruses via the cloud.
-
Data Security: One of the advantages of cloud computing is quicker remote access to data, but this poses new dangers, such as data transiting across cloud environments and threat actors getting unauthorized access to sensitive data. CASB gives insight into the transfer of data in the cloud as well as data security capabilities such as encryption, tokenization, and access control.
-
Visibility: CASBs were originally designed to provide visibility into cloud use, especially unsanctioned use of SaaS apps or Shadow IT. Today, as enterprises shift entirely to the cloud and provide more access to cloud apps through remote work and bring-your-own-device (BYOD), visibility remains a crucial CASB function. These solutions aid in the identification of questionable requests and make it simpler to provide access to cloud services while restricting particular activities and user access inside these expansive apps.
-
Compliance: You are responsible for ensuring that you comply with requirements such as PCI DSS as a cloud user. CASB assist in monitoring compliance and identifying potential risk areas requiring attention.
-
-
Static Application Security Testing (SAST): The term "static" in static application security testing refers to the fact that the code is scanned without being executed. This varies from DAST (Dynamic Program Security Testing), which is performed when the application is operating and, thus, occurs later in the development process. With cloud-based applications, it is crucial to address security flaws that can only be proved during runtime and to combine DAST with Static Application Security Testing.
-
Cloud Infrastructure Entitlement Management (CIEM): Using the concept of least privilege, Cloud Infrastructure Entitlement Management (CIEM) technologies assist to manage identity and access in the cloud. They assist cloud customers in managing IAM across numerous cloud environments for a single identity strategy.
-
Cloud Security Posture Management (CSPM): Cloud security posture management (CSPM) is another developing technology in cloud security that helps the implementation of NIST's cybersecurity architecture. Misconfigurations are a prevalent problem in many cloud settings that CSPM solutions are meant to remedy.
Misconfigured cloud infrastructures by organizations or even cloud service providers may result in a number of vulnerabilities that dramatically enhance an organization's attack surface. CSPM tackles these difficulties by aiding in the organization and deployment of cloud security's fundamental components. Identity and access management (IAM), regulatory compliance management, traffic monitoring, threat response, risk reduction, and digital asset management are a few examples.
-
Cloud Workload Protection Platforms (CWPP): Cloud Workload Protection Platforms provide protection at the level of the workload. They secure virtual machines (VMs), serverless workloads, and containers, helping to assure security across public, private, and hybrid cloud environments, and allowing the customer a centralized place from which to manage the security of their workloads independent of the cloud services used. CWPPs are especially advantageous for the quick development cycle since they give security help for applications built with cloud workloads and may alleviate some of the security risks associated with rapid DevOps.
-
Security Incidents and Events Management (SIEM): A contemporary SIEM system is uniquely capable of absorbing and behaviorally analyzing all security alert data from any cloud or on-premises data source to help businesses identify, analyze, and react more effectively to intrusions. Modern SIEMs need various API-based interfaces to allow the intake of alarm data from any source required to maintain cloud security in order to act successfully as cloud cyber-cops. It includes on-premises data sources in a hybrid multi-cloud setting. In general, the method is identical to safeguarding on-premises infrastructure:
- Ingestion and centralization of logs inside a SIEM
- Either a security tool or a correlation rule in the SIEM generates an alert, or behavioral analytics generates a significant user or entity event.
- This initiates an inquiry in which analysts examine information collected in their SIEM
- The processing of evidence into an incident chronology
- Using the timetable as a guide, the analyst may now react to an assault.
The analyst is now aware of the systems and users involved, can examine their activity, and consult or apply remediation playbooks.
-
Extended Detection and Reaction (XDR): XDR is a new security paradigm that enables enterprises to offer threat detection and incident response (TDIR ) more efficiently. Multiple layers comprise cloud environments, such as public networks, virtual private networks (VPN), APIs, workloads, and applications. Unprotected user devices connecting to cloud services is another factor. XDR assists by merging three kinds of data with the TDIR regime and automatically building attack timelines that can facilitate speedy event investigation:
- Cloud logs: Gathering massive amounts of log data from many cloud environment layers and extracting unusual events
- Identity Management: Monitoring human users and service roles for unusual behavior.
- Network flow Analyze: This goes beyond monitoring NetFlow for cloud devices by seeing network traffic across whole cloud environments and reacting automatically by setting network segmentation. XDR excels in combining data from cloud environments, on-premises systems, and other distributed systems, such as IoT.
-
Disaster Recovery and Business Continuity: Data breaches and disruptive disruptions may still occur regardless of the preventive measures in place by enterprises for their on-premise and cloud-based infrastructures. Enterprises must be able to respond rapidly to newly identified vulnerabilities or large system failures. Cloud-based disaster recovery solutions offer enterprises the tools, services, and standards required to speed the recovery of lost data and restore regular business operations.
-
Data Loss Prevention (DLP): Data loss prevention (DLP) services provide a collection of tools and services meant to safeguard regulated cloud data. DLP systems use a mix of remedial warnings, data encryption, and other preventive measures to safeguard all stored data, whether in motion or at rest.
-
Identity and Access Management: Identity and access management (IAM) technologies and services enable businesses to implement policy-driven enforcement mechanisms for all users seeking to access on-premises and cloud-based services. IAM's primary goal is to generate digital identities for all users, so they can be actively watched and, if required, limited throughout all data exchanges.
What are the Best Practices for Cloud Security?
Each organization's approach to cloud security is unique and relies on a variety of circumstances. The National Institute of Standards and Technology (NIST) has compiled a list of best practices for establishing a safe and enduring cloud computing infrastructure.
The NIST has established the procedures required for every company to self-assess their security readiness and implement suitable preventive and recovery security measures on their systems. These principles are based on the five pillars of a cybersecurity architecture established by the National Institute of Standards and Technology (NIST): Identity, Protect, Detect, Respond, and Recover.
Organizations with current cloud solutions or those planning to install them should consider the following strategies for cloud security:
-
Double-Check Your Compliance Requirements: Organizations that collect personally identifiable information (PII), such as those in retail, healthcare, and financial services, are subject to stringent privacy and security rules. Local or state governments may impose unique compliance requirements on a subset of enterprises based in certain geographic places or storing data in specified geographies. Before launching a new cloud computing service, enterprises should assess their compliance requirements and ensure that their service provider can fulfill their data security standards.
-
Comprehend Shared Responsibility Model: In a private data center, the organization is fully liable for security concerns. In the public cloud, though, things are somewhat more difficult. While the cloud client is ultimately responsible for IT security, the cloud provider bears responsibility for some areas of IT security. Cloud and security specialists refer to this as a paradigm of shared responsibility.
Infrastructural as a service (IaaS) and platform as a service (PaaS) providers like Amazon Web Services (AWS) and Microsoft Azure give documentation to their clients so that all parties are aware of their respective duties based on deployment type. In software as a service (SaaS) models, application-level controls are Microsoft's responsibility. However, in infrastructure as a service (IaaS) deployments, the client is responsible. Microsoft and its customers share responsibility for PaaS models.
Enterprises that are contemplating a specific cloud provider should study its rules on shared security duties and determine who is responsible for the different cloud security features. This aids in preventing misunderstandings and confusion. More crucially, though, responsibility clarity prevents security events caused by a specific security requirement from slipping through the gaps.
-
Pose specific security questions to your cloud provider: In addition to outlining shared obligations, enterprises should inquire about the security measures and practices used by their public cloud suppliers. It is tempting to believe that the main suppliers have security under control, yet security approaches and processes might differ considerably amongst companies. To determine how a certain cloud provider compares to others, businesses should ask a variety of questions, such as:
- What types of authentication does the supplier support?
- What process does the provider have for suspected security incidents?
- Where are the provider's servers physically reside?
- What is the disaster recovery strategy of the provider?
- How much technical help is the supplier ready to offer?
- What safeguards does the service provider use to protect the different access components?
- Which roles or personnel inside the provider have access to the cloud-stored data?
- Does the service provider encrypt data during transmission and storage?
- Which compliance standards does the service provider support?
- What are the outcomes of the most recent penetration tests conducted by the provider?
-
Encrypt Data In-Transit And At-Rest: Encryption is a fundamental component of any cloud security approach. Not only should enterprises encrypt data stored in a public cloud storage service, but they should also encrypt data in transit when it is most susceptible to attack.
A few suppliers of cloud computing provide encryption and key management services. Some cloud-based and conventional software providers provide encryption alternatives. Experts advise locating an encryption system that integrates effortlessly with current work processes, removing the need for end users to take additional steps to comply with business encryption regulations.
-
Develop And Implement Cloud Security Policies: Who may utilize cloud services, how they can be used, and whose data can be kept in the cloud should be specified in written standards for all businesses. In addition, they must outline the exact security solutions that workers must apply to secure cloud-based data and apps.
Ideally, security personnel should have automated systems in place to guarantee compliance with these regulations. In certain instances, the cloud provider includes a policy enforcement function that meets the organization's requirements. In other situations, the company is required to acquire a third-party policy enforcement solution, such as CASB. Zero trust network access (ZTNA) is one such technology that provides improved policy enforcement control. This group of tools collaborates with other systems to establish how much access each user needs, what they can accomplish with that access, and what that access implies for the company as a whole.
-
Implement an Identity and Access Management: Unauthorized access is the fourth most dangerous threat to public cloud security outlined by CloudPassage's research (and growing 53 percent, up from 42 percent in 2020). Identity and access management (IAM) solutions help limit these concerns, despite the fact that hackers' tactics for getting access to sensitive data are growing more sophisticated with each new assault.
Experts advise businesses to seek an IAM solution that enables them to design and enforce access controls based on the principle of least privilege. These regulations should also be based on authorization capabilities based on roles. In addition, multifactor authentication (MFA) further limits the chance of bad actors obtaining access to critical data, even if they acquire usernames and passwords.
Organizations may choose to seek an IAM solution that is compatible with private data centers and cloud deployments in hybrid environments. This may simplify authentication for end users and make it simpler for security personnel to maintain uniform policy enforcement across all IT environments.
-
Secure Your Endpoints: Using a cloud service does not diminish the requirement for robust endpoint security; rather, it increases it. New cloud computing initiatives provide an opportunity to reevaluate current techniques and verify that the safeguards in place are sufficient to counteract new threats.
A defense-in-depth approach consisting of firewalls, anti-malware, intrusion detection, and access control has been the norm for endpoint security for quite some time. Nevertheless, the variety of endpoint security issues has gotten so complicated that automated techniques are essential to stay up. Tools for endpoint detection and response (EDR) and/or endpoint protection platforms (EPP) might be of assistance in this area.
EDR and EPP systems integrate standard endpoint security features with continuous monitoring and automatic response. These technologies specifically handle a variety of security needs, including patch management, endpoint encryption, VPNs, and avoidance of insider threats, among others.
-
Educate Your Employees: To prevent hackers from obtaining access credentials for cloud computing products, firms should teach all employees to recognize and react to cybersecurity risks. Comprehensive training should contain fundamental security information, such as how to set a secure password and spot potential social engineering attacks, in addition to more sophisticated subjects, such as risk management. Possibly most crucial, cloud security training should assist staff to recognize the inherent dangers of shadow IT. At most firms, it is much too simple for employees to implement their own tools and systems without the IT department's awareness or assistance. Without complete awareness of all systems that interact with the organization's data, it is impossible to assess all vulnerabilities. Enterprises must disclose this danger and emphasize the organization's possible repercussions.
Additionally, organizations must spend on specific training for their security personnel. IT security professionals can only keep up with the continuously shifting threat environment if they are continually learning about the newest dangers and viable responses.
-
Backup Cloud Data: Regularly back up your data so that you can recover it in its entirety in the case of a cloud outage or data loss at your cloud provider. This backup might be stored on your home computer, an external hard drive, or even cloud-to-cloud, so long as you are certain that the two cloud providers do not share infrastructure.
-
Utilize Intrusion Detection And Prevention Tool: IDPS are among the most effective cloud security techniques currently available. They monitor, analyze, and react to network traffic on-premises and in the public cloud. When IDPS systems meet signature-based, protocol-based, or anomaly-based threats, they record them, notify administrators of odd behavior, and block the threats to give administrators sufficient time to respond. These technologies are essential for continuous monitoring and real-time notifications. Without IDPS, analyzing network data for indicators of a sophisticated assault is practically difficult.
-
Utilize Real-time Threat Intelligence: By intelligently cross-referencing aggregated log data with internal data such as asset and configuration management systems, vulnerability scanners, etc., and external data such as open source threat intelligence feeds, geolocation databases, etc., third-party cloud security vendors add context to the vast and diverse streams of cloud-native logs. In addition, they give capabilities for visualizing and querying the threat environment and expediting an incident response. Unknown threats are identified using AI-based anomaly detection algorithms, which are subsequently subjected to forensics investigation to establish their risk profile. Real-time warnings on intrusions and policy breaches reduce the amount of time required for repair, sometimes even initiating automated remediation operations.
-
Enable Security Logging: In addition to doing audits, firms should enable logging capabilities for cloud systems. It would be almost hard for system administrators to manually keep track of which users make modifications to the environment without logging in. If an adversary obtains access and makes modifications, the logs will reveal all of their actions so that they may be remedied.
Misconfigurations are one of the greatest issues of cloud security, and adequate logging capabilities can assist identify the modifications that lead to a specific risk so that it may be addressed and prevented in the future. Logging lets managers discover people that have more access than they need to do their duties, allowing them to reduce their rights to the absolute minimum.
-
Implement CASB Or Cloud Security Solution: Dozens of organizations provide solutions or services geared particularly to improve cloud security. If an organization's internal security team lacks cloud experience or its current security solutions do not support cloud environments, it is time to seek outside assistance.
Cloud access security brokers (CASBs) are instruments designed specifically to implement cloud security rules. As more firms have begun using cloud services, their popularity has increased. According to experts, a CASB solution may make the most sense for businesses that use several cloud computing services from multiple providers. Additionally, these systems may monitor for illegitimate applications and access.
-
Perform Audits And Security Testing: If a business decides to work with an external security firm or maintain security teams in-house, experts advise that all organizations should do penetration testing to establish whether current cloud security measures are enough to secure data and apps. In addition, enterprises should undertake routine security audits that include a study of the capabilities of all security suppliers. This should indicate that they are complying with the stipulated security conditions. Access logs should be inspected to verify that only authorized individuals have access to critical cloud-based data and apps.
What are the Differences Between the Cloud Security and Traditional Network Security?
The purpose of network security stacks is to safeguard business networks, not the cloud. They cannot deliver the complete cloud data protection and cybersecurity that cloud-based apps and mobile consumers need today. To support mission-critical SaaS applications (such as Microsoft 365) and manage other bandwidth-hungry services as well as increased network traffic without incurring additional costs or complexity, you need an elastically scalable multitenant security platform. This is impossible with a conventional network security design.
The most effective method for securing applications, workloads, cloud data, and people, regardless of where they connect, is to shift security and access controls to the cloud. Cloud-based security is constantly current and ready to defend your data and users against the most recent ransomware and other sophisticated attacks.
A complete cloud security platform integrates security services and cloud access restrictions to provide insight into all traffic traversing dispersed networks (cloud and on-premises). In a matter of seconds, you can receive visibility into every request -by user, location, server, and endpoint device- through a single interface. API interfaces with other cloud service providers, such as those that provide SD-WAN, cloud access security broker (CASB), identity and access management (IAM), and endpoint protection services, enhance your security posture.
What Does a Cloud Security Engineer Do?
Cloud security engineers use technical assistance and engineering best practices to design and grow cloud-native apps safely and implement network security defenses inside the cloud environment. These professionals have expert knowledge in identity and access management (IAM), utilizing cloud technologies to offer data protection, container security, networking, system administration, and zero-trust architecture.
What skills does a cloud security engineer need?
In many circumstances, a bachelor's degree is necessary for entry-level positions; however, people with hands-on experience from vocational institutions may flourish in the role of a cloud security engineer. Cloud security engineer position frequently requires a degree in engineering, computer science, programming, or information security.
Employers often want applicants with three to five years of information security experience. Experience in software development, programming, or ethical hacking, as well as familiarity with technological tools and platforms, are all advantageous. Additionally, knowledge of at least one of the three main cloud service providers (CSPs), Amazon Web Services, Microsoft Azure, or Google Cloud Platform, is essential.
Obtaining certification is an excellent idea if you want to improve your skills or enter a new field. Certifications for cloud security engineers include Cloud Security Professional (CISSP), AWS Certified Security Specialty, AWS Certified Solutions Architect Associate, Google Cloud Professional Cloud Security Engineer, Certificate of Cloud Security Knowledge (CCSK), and Certified Cloud Security Professional (CCSP).
Developing your commercial skills is just as crucial as developing your technical abilities. Successful cloud security engineers must be able to effectively communicate and collaborate with others. Cloud security engineers are problem-solvers and researchers. They like problem-solving and coming up with creative solutions. They like working on difficult challenges and gaining new knowledge.
As a cloud security engineer, it is essential to have a firm grasp of the fundamentals, including information security, network and application security, DevOps, and programming languages like Python and Ruby. Cloud computing models Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) should also be well-known to a cloud security engineer candidate. Additionally, an understanding of operating systems, such as Windows and Linux, and cloud architecture is advantageous.
What is a Cloud Security Engineer's Salary?
The average yearly salary for a Cloud Security Engineer in the United States as of Oct 8, 2022, is $141,511. This equates to around $68.03 per hour. This is equal to $2,721 every week or $11,792 per month.
It is observed that annual salaries are as high as $190,500 and as low as $86,000, the majority of Cloud Security Engineer salaries currently range from $121,000 (25th percentile) to $161,000 (75th percentile), with the highest earners (90th percentile) making $180,000 annually across the United States. There may be various prospects for development and greater income dependent on skill level, location, and years of experience, as shown by the Cloud Security Engineer's typical salary range, which ranges by as much as $40,000.