Benefits of Cybersecurity
Protecting internet-connected systems, including their hardware, software, and data, from cyber attacks, is known as cybersecurity. Individuals and businesses both use this technique to prevent illegal access to data centers and other digital systems.
A solid cybersecurity plan can offer a good security posture to harmful attacks intended to gain access to, change, delete, destroy, or extort sensitive data and systems belonging to a business or user. Security measures are essential in preventing attacks that try to take down or impair a system or device's functionality.
The importance of cybersecurity is still only going to increase as there are more people, devices, and programs in the contemporary workplace, along with an influx of more data, most of it critical or private. The problem is made much worse by the increase in the quantity and level of sophistication of cyber attackers and attack methodologies. Cybersecurity is crucial because it aids in the protection of many types of data, including protected health information, government data, personal data, and intellectual property. Businesses and people may be shielded against ransomware, phishing, malware, and other sorts of attacks with effective security.
Because of the ecosystem's digitalization and connectivity, users are more open to online attacks, which makes cybersecurity a crucial element. The seven most important advantages of cybersecurity services are as follows and will be explained in detail in the article:
- Protect Sensitive Information
- Boosts Customer Confidence
- Business Continuity
- Boosts Productivity
- Information Privacy
- Compliance with Regulations
- Enhances Cyber Posture
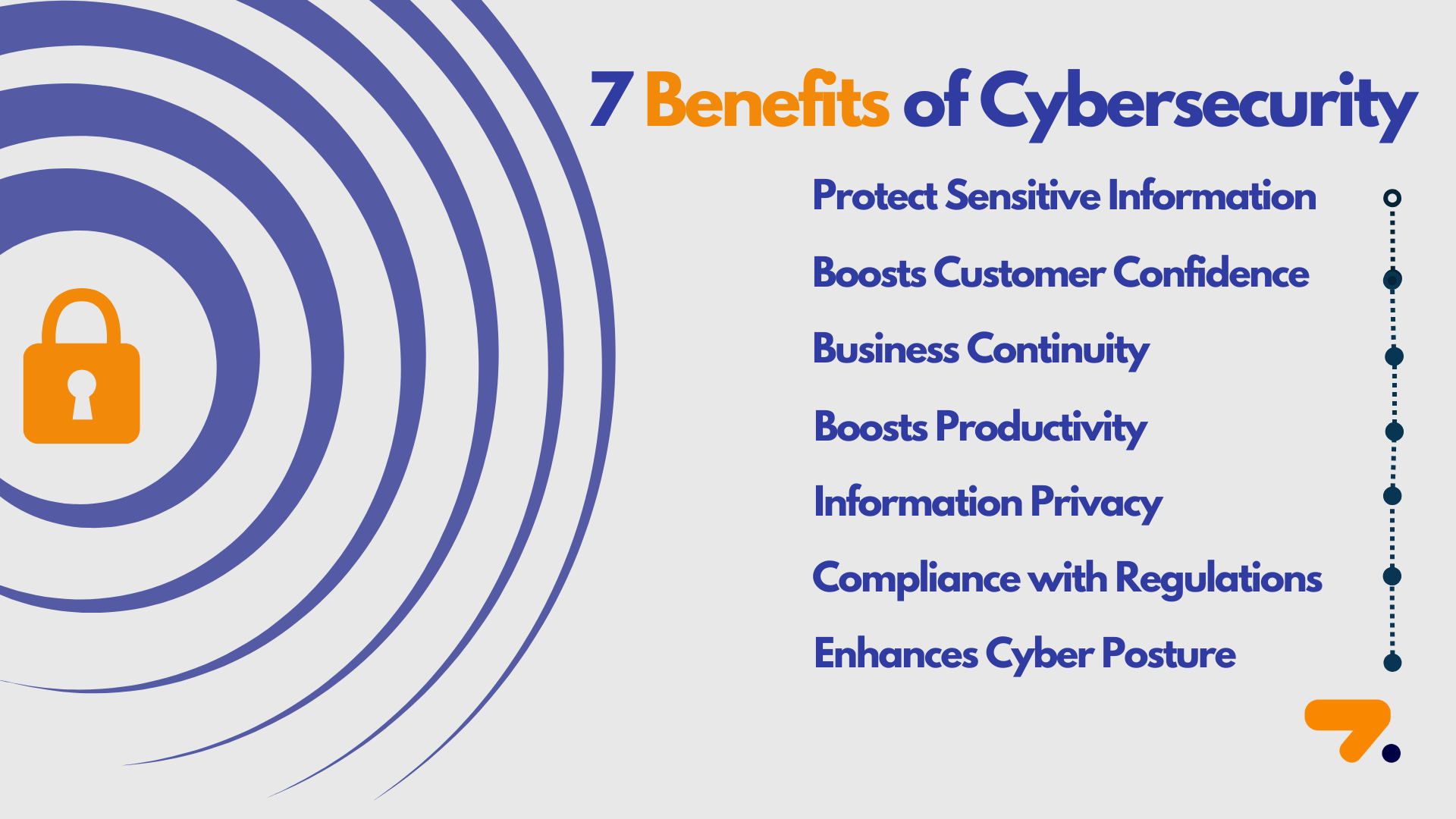
Figure 1. 5 Benefits of CyberSecurity
1. Protect Sensitive Information
Gaining access to an organization's confidential information through data leakage is one of the most desired benefits for thieves. Additionally, cybersecurity safeguards prevent unwanted access to private data. To protect data, they employ methods like access restrictions, firewalls, and encryption. Regular updates and patches to address any vulnerabilities that hackers could attempt to exploit are another aspect of good cybersecurity. It's a continuous process that adjusts to emerging dangers. Employee risk recognition and avoidance training is another aspect of cybersecurity. Frequent security audits assist in identifying and addressing any vulnerabilities before they may be taken advantage of. This might include private or corporate data, confidential R&D data, intellectual property, or trade secrets, as well as sensitive information like customer lists that might contain names, email addresses, physical addresses, and phone numbers. The purpose of a data security plan is to prevent the theft of sensitive information. If this information ends up in the wrong hands, it might give rivals an unfair and ill-gotten edge.
An effective cybersecurity program will involve early detection of data exfiltration to avoid efforts to steal sensitive proprietary information, as well as a data loss prevention plan that aims to secure all data with suitable degrees of encryption while in use, in transit, and at rest.
2. Boosts Customer Confidence
Strong cybersecurity increases company partners' and customers' confidence. This could be among the main advantages of cybersecurity. People are more inclined to conduct business with a firm when they are certain that their data is secure. Partnerships with other companies can be facilitated by strong cybersecurity, as they will feel more comfortable exchanging information. Stronger, more enduring commercial partnerships may result from this trust.
Establishing a cybersecurity program may provide verified proof that your business is treating risk management seriously.
Vulnerability scanning and penetration testing are common components of cybersecurity programs that confirm that the security mechanisms in place are successfully imposing robust security.
Reports generated by these procedures may be used to show partners, clients, and customers that you are proactively mitigating cyber risk.
Additionally, if compliance certification is part of your organization's cybersecurity program, you should share those accomplishments to foster evidence-based trust.
Strong cybersecurity contributes to the preservation of a business's reputation. In the modern world, information about a data breach may travel swiftly and erode consumer confidence. Strong security demonstrates to clients that a business values their privacy. Additionally, it helps a company differentiate itself from rivals who might not be as cautious with data.
3. Business Continuity
Because cyberattacks may cause prolonged downtime, cybersecurity is essential to sustaining corporate operations. Businesses can prevent interruptions and bounce back from catastrophes fast when they have a robust security structure in place.
An efficient cybersecurity plan may reduce downtime and guarantee little disruption to business operations in the case of a cyber-attack. One important strategy for preserving productivity and avoiding revenue loss is operational business continuity. By implementing cybersecurity, the company itself can react and bounce back with minimal impact on operations.
Cybersecurity guarantees that the company can continue to function normally even in the face of threats by safeguarding systems and data.
In fact, the greatest advantage of cybersecurity for businesses is that IT security solutions can offer your company complete digital protection. This will protect your staff from possible hazards while enabling them to use the internet whenever they need to. You and your staff are always in danger from a possible cyberattack if your company does not have the finest cybersecurity solutions. Your productivity may need to be improved, and you may even need to replace computers if your system or even individual machines are infected.
4. Boosts Productivity
There are several detrimental effects on operations when a company's digital systems go down. If customer-facing services are not accessible, system outages can directly lower sales income in addition to wasting resources and reducing productivity.
The secondary effect may result in a decline in consumer trust and reputation, which would further reduce income.
Furthermore, because viruses interfere with networks, processes, and functionality, they have a detrimental effect on productivity. A company's outage might bring the organization to a complete halt. Effective cybersecurity solutions may greatly increase productivity by reducing the time lost due to cyberattacks. Additionally, one of the most potential cybersecurity benefits is the ability for businesses to increase productivity via the use of measures like enhanced firewalls and automatic backups.
5. Information Privacy
By guaranteeing that private data is safely kept and accessible, cybersecurity aids in data management. Businesses may safeguard their assets from breaches by putting procedures in place for data encryption, storage, and retrieval. Better data management makes it possible to recover from incidents more quickly.
For many firms, one of the most crucial elements is intellectual property (IP). Cybersecurity aids in preventing hackers from stealing these trade secrets, patents, and unique designs. Maintaining the security of intellectual property protects the ideas that propel firms forward and keeps them competitive. For sectors like manufacturing, technology, and medicines, this protection is particularly important.
6. Compliance with Regulations
Strict regulations are in place in several businesses to protect data. Cybersecurity aids companies in adhering to these regulations. This may need meticulous record-keeping, frequent audits, and certain security measures. Businesses may avoid penalties and legal issues by maintaining compliance. Additionally, it might aid in gaining the trust of clients who are concerned about the handling of their data.
Organizations and individual users are greatly protected by regulatory agencies like HIPAA, SOC, PCI DSS, and GDPR. There are severe consequences for breaking these rules.
Maintaining compliance improves the organization's overall security structure and helps to prevent penalties. Additionally, compliance guarantees that companies follow the guidelines established by industry authorities.
Compliance attestation communicates to clients, partners, and prospective partners your organization's seriousness and willingness to go above and beyond to guarantee resilience.
In order to guarantee that robust safeguards are protecting a business's assets and the data of its clients, cybersecurity compliance necessitates administrative, technological, and physical rules, controls, and standard operating procedures.
Any business might become the target of a cyberattack. However, those who have obtained a compliance certification through their cybersecurity program are prepared to respond to and recover from an attack with minimum harm and have proof of taking proactive steps to avoid being a victim.
7. Enhances Cyber Posture
Maintaining a company's resilience against emerging cyberthreats is essential to improving its cyber posture. By consistently improving and enhancing security procedures, companies may remain ahead of any threats.
Organizations may strengthen their defenses by implementing cybersecurity. In addition to reducing risks, this proactive strategy gets the business ready for new difficulties. Cybersecurity offers businesses comprehensive protection for their digital services while giving workers secure and adaptable ways to use the internet.
A simple click on a unified dashboard allows a sophisticated cybersecurity architecture to monitor all systems in real-time. This strategic strategy ensures easier operations for enterprises by reducing security risks and empowering them to respond to threats with automation.
How Important is Cybersecurity to Businesses?
It is critical to comprehend the cybersecurity definition in order to comprehend why cybersecurity is so crucial for contemporary firms. Cybersecurity is a process that comprises defending against cyber attacks on data, networks, systems, programs, businesses, and people.
The world has gone digital, which means that we are depending on technology more and more. This dependency serves as the foundation for cyber attacks. Older dangers still have the power to cause harm, but new threats are continuously emerging. Because the correct cybersecurity solutions may mean the difference between another successful business day and a complete shutdown of operations, it is crucial that companies give cybersecurity their top priority.
One of the most promising fields with significant development potential in the next few years is cybersecurity for businesses. At some point or another, every piece of technology needs cybersecurity. Cybersecurity is all about securing cyberspace, safeguarding users' privacy, and preventing any kind of cyber attack by implementing strict security standards and protocols.
Cybercrime poses a danger to businesses of all shapes and sizes. Businesses now use digital technology at every stage of their operations thanks to the internet, including email sending and receiving, financial transactions, networking, and cooperation, real-time work, etc. There is a serious consequence that can have a catastrophic impact on the business's overall operation when these communication channels are severed. Any cyber-attack might damage the company's reputation owing to the possible loss of sensitive client data.
Given our reliance on technology, cybersecurity has become essential. It will be a major issue if the general population is afraid to use the internet for fear of having their devices infected or their data stolen. Cybersecurity experts work to avoid this. The advantages of cybersecurity are numerous. Some of the most significant advantages are as follows:
-
Protection against data theft: Today, data is perhaps the most valuable resource. Preventing data theft is crucial in cases of corporate espionage and widespread cyber attacks. Protections against data theft and misuse are put in place with the aid of cybersecurity.
-
Increased privacy: Over time, organizations and individuals have both grown to be quite concerned about privacy. The average person wants privacy because it keeps them secure. While companies desire privacy to get a competitive edge over their rivals. By guaranteeing that harmful actors are kept at bay, cybersecurity safeguards user and organizational privacy.
-
Lessening of hacking incidents: If individual and commercial systems are better protected, hackers will have a more difficult time locating an access point and then carrying out an attack.
-
Improved system performance: There are several types of cyber attacks. System performance increases when systems are better secured against these attacks because they are free of harmful programs and applications.
What are the Types of CyberSecurity Attacks?
Cyber attacks may affect both individuals and corporations. Cybersecurity attacks come in a wide range and all aim to steal data or interfere with a person or organization's system, website, software, data, or processes. The following section discusses some of the most common types of cyber attacks.
-
DDoS (Distributed Denial-of-Service): This kind of hack tries to exhaust the resources and bandwidth of a certain network or server. DDoS attack, which includes flooding a website's servers with many fake requests, frequently involves the use of compromised devices. This kind of attack puts the website under stress and may even cause it to crash, making it unavailable to authorized users.
-
Phishing: A dishonest technique in which hackers pose as reliable organizations in order to steal confidential information. Frequently makes use of phony emails or websites that imitate authentic ones. To avoid phishing attempts, confirm the sender's identity and use caution when entering personal information online.
Social engineering assaults of this kind frequently entail deceiving victims into disclosing personal information. They typically send texts or emails that seem to be from a reputable source, such as your card issuer or the bank you currently bank with
-
Malware: A broad category of cyber attacks that compromise systems by exploiting flaws is known as malware. Viruses, spyware, and other types of harmful software that carry out the wishes of their creators are all considered malware. When someone clicks an email attachment or follows a link to a malicious website, malware frequently enters the system.
-
SQL(Structured Query Language) Injection: Servers that use SQL are frequently impacted by this kind of cyber attack. Malicious code is injected into the server during the attack, causing the website to disclose protected data. The people who created the SQL injection can either sell the exposed information or use it to steal money.
-
Man-in-the-Middle Attack: An assault in which two parties' communications are intercepted by a third party. The attacker eavesdrops on your conversations with other people, such as your bank, during this type of assault. He is capable of stealing your personal data. The attacker might keep an eye on or manipulate the data that is sent. To reduce the danger of MitM attacks, use encrypted connections and stay away from unprotected public Wi-Fi networks.
-
Password Attack: An effort to compromise credentials in order to get unauthorized access. This is an effort to figure out someone's password by utilizing different letters, numbers, and character combinations. With automated systems, attackers may scan millions of passwords in a matter of seconds. Techniques vary from basic guesswork to sophisticated algorithms. To improve account security, use strong, one-of-a-kind passwords and turn on multi-factor authentication.
What Are the Tools to Ensure Effective Cybersecurity?
Cybersecurity solutions are becoming more widely available to fulfill demand as the frequency of cyber attacks rises. Although many of these technologies might be expensive, they provide complete cybersecurity solutions that shield people and organizations from assaults such as data theft. The security offered is far less expensive than the possible damage that can be experienced as a result of a cyber attack. Below is a list of some of the most well-known cybersecurity tools.
-
Antivirus software: The main purpose of antivirus software is to detect, stop, and eliminate viruses from your computer. Most antivirus software operates automatically in the background after installation, providing real-time defense against any threats.
Having antivirus software installed on your computer is a proactive cybersecurity measure. Keyloggers, browser hijackers, adware, botnets, phishing emails, and ransomware assaults are just a few of the numerous online dangers it helps defend against.
To safeguard the businesses they work for, cybersecurity experts must stay current on the newest advancements in antivirus software. Since viruses are always changing, it's critical for businesses to stay up to date on the latest, most efficient antivirus technology and update their current software as soon as it becomes available.
-
Firewalls: Firewalls, which can be implemented as software, hardware, or a combination of the two, stop unauthorized people from accessing the business intranet.
The simplest defenses against online attacks are firewalls. Incoming and outgoing traffic is watched over and filtered, and anybody who doesn't fit the network's defined security rules is excluded. From personal PCs to the larger private Internet network, firewalls safeguard hardware and software resources.
-
Encryption Tools: The purpose of encryption technologies is to prevent data theft, alteration, and compromise. They function by jumbling the information into a code that only a special digital key can decipher. Because there are so many potential cryptographic keys with strong encryption, it is almost difficult for an unauthorized individual to guess the right one. Because of this, encryption is an effective method of protecting your private data.
-
Penetration Testing: Penetration testing assists in finding weaknesses in a company's network that hackers may take advantage of using their tools and strategies.
One cybersecurity method that mimics a cyberattack on a system is penetration testing. Another name for this would be ethical hacking or a pen test. The purpose of the test is to find a system's vulnerabilities and assess the possibility of a breach. Additionally, it assists cybersecurity experts in identifying the system's strongest components and those that don't presently need to be improved.
-
Vulnerability Management: To find potential flaws and vulnerabilities that an attacker may exploit, vulnerability assessment tools examine your networks, systems, and apps. These technologies enable you to prioritize and proactively resolve vulnerabilities by assisting you in understanding the security posture of your environment. You can keep up with threats and make sure your systems are sufficiently secured by doing vulnerability managements on a regular basis.
-
Endpoint Protection: Software for endpoint protection is made to guard against malware, illegal access, and other security risks on individual devices, including laptops, desktop computers, and mobile phones. It offers complete endpoint protection with capabilities including intrusion prevention, firewall, and antivirus. Endpoint security is now more important than ever due to the rise in remote work configurations. Devices connecting to your network are safe and adhere to your company's security guidelines thanks to endpoint protection software.
-
Network Intrusion Detection: Network defense solutions are essential for safeguarding networked systems' availability, confidentiality, and integrity. By keeping an eye on network traffic, these technologies may identify and stop attacks, protecting data while it moves across the network.
What are the Best Cybersecurity Companies?
The market for cybersecurity technology and the variety of solutions available have both skyrocketed in tandem with the growing need for strong security protection. Based on their innovation, revenue and growth, user evaluations, product features and advantages, analyst reports, independent security testing, and use cases, we have selected 10 of the top cybersecurity technology suppliers in the globe to assist you in navigating this expanding industry.
The platforms developed by the businesses on this list include cloud-based administration and sophisticated data analytics, and they use AI and genAI to provide security experts access to real-time information. The best cybersecurity companies in the world are listed below.
-
Zenarmor: Zenarmor is a provider of cybersecurity solutions. The company's products provide enterprise-grade network protection and include features including content filtering, threat detection, and web and application access management. Its products are designed to be easily deployed on any network and offer real-time security safeguards.
Zenarmor's appliance-free, all-in-one, all-software, lightweight, and simple architecture allows it to be implemented right away on any healthcare cybersecurity system with network connectivity.
Companies can swiftly protect environments as small as home networks or expand to multi-cloud deployments because of robust and portable appliance-free technology that allows for the quick installation of firewalls whenever needed. It's as easy as opening an application.
Although Zenarmor's packet inspection core is powerful enough to fight off encrypted assaults, its compact size and agility allow it to be utilized even in resource-constrained environments. Zenarmor's single-pass design processes all security measures just once.
Whether it's new attack routes, malware strains, or zero-day vulnerabilities, advanced security rules are your line of defense. To keep your business ahead of hackers, Zenarmor provides premium services that give you access to cutting-edge security capabilities. In the realm of cybersecurity, Zenarmor's state-of-the-art security features, such as deep packet inspection, AI-driven defenses, and real-time threat intelligence, are formidable.
A potent weapon in the battle against online threats is Zenarmor's Advanced Security Rules, which are included in its premium membership plan. These rules give companies the ability to fortify their defenses with comprehensive security measures.
-
Palo Alto Networks: From its beginnings as the developer of the application-aware firewall to its present leading position, founded on what it refers to as "platformization", or the implementation of an integrated security platform, Palo Alto Networks is one of the well-known major players in cybersecurity.
Palo Alto Networks (NASDAQ: PANW) has a long history of receiving high marks in demanding independent security testing and offers a wide range of security products. It scores well for network security tools, zero trust, extended detection and response (XDR), IoT security, software-defined wide area network (SD-WAN), secure access service edge (SASE), next-generation firewalls (NGFW), and endpoint detection and response (EDR) solutions.
-
Check Point: With a robust service portfolio and conventional solutions like firewalls, gateways, UTM, DLP, and encryption, Check Point provides high security and value.
To deliver real-time threat information, the company's cloud-based knowledge base, ThreatCloud AI, analyzes millions of danger signals every day. Check Point has maintained its position as a leader in the cybersecurity industry, especially in areas like advanced threat prevention and zero-day protection, because of its dedication to research and development, which is demonstrated by its steady investment in innovation.
-
Cisco: Networking giant Cisco has assembled a wide range of security solutions, primarily through acquisitions. The adoption of Cisco's security solutions is mostly driven by its current networking clients due to its inherent interoperability with pre-existing infrastructure.
-
Fortinet: With its experience in firewalls, Fortinet (NASDAQ: FTNT) has become a pioneer in NGFW, web application firewalls (WAF), unified threat management (UTM), and related areas such as enterprise virtual private networks (VPNs), and software-defined wide area networks (SD-WAN).
Two factors set Fortinet apart from other cybersecurity vendors: 1. Networking and security are naturally integrated into Fortinet's platform. Actually, Fortinet leads the enterprise wired and wireless LAN networking Gartner Magic Quadrant. 2. Fortinet manufactures its own chips, has its own operating system (FortiOS), and, for the most part, develops products internally. This allows Fortinet to offer complete integration from network switches to firewalls to SASE, in contrast to businesses that expand through acquisitions and must incorporate new products into their portfolio.
-
CrowdStrike: A cloud-native security platform called CrowdStrike was created to safeguard cloud data. Building on its expertise in endpoint protection, CrowdStrike (NASDAQ: CRWD) provides solutions for cloud security posture management (CSPM), vulnerability management as a service (VMaaS), XDR, and MDR.
According to 2024 IDC MarketScape, it leads the global managed detection and response services market. In the 2024 Forrester Wave for Extended Detection and Response Platforms, CrowdStrike is a front-runner. Expert administration, monitoring, protection, and optimization of identities and identity stores are provided by the additional features, which include its controlled cloud workload protection (CWP) and its completely managed identity threat prevention service.
-
Zscaler: Through a cloud-native platform, Zscaler (NASDAQ: ZS) provides edge and cloud security, converting IT infrastructure from castle-and-moat networks to distributed, zero-trust settings.
By combining cutting-edge machine learning and artificial intelligence with zero trust principles, the company's Zero Trust Exchange safeguards people, workloads, and devices. The platform now supports both OT systems and IoT devices.
-
Proofpoint: With a solution range that includes cloud access security broker (CASB), data loss prevention (DLP), zero trust, threat intelligence, email security, and email gateways, Proofpoint (private) focuses on protecting end users.
Proofpoint, a pioneer in email security and threat intelligence, offers solutions to defend against phishing and other cyberthreats. Its focus on advanced threat detection and information
-
RSA Security: RSA Security, a mainstay in the cybersecurity sector, excels in offering identity and access management solutions. Because of its emphasis on protecting digital identities and preventing unauthorized access, RSA Security is recognized as a reliable steward of the digital realm.
RSA offers robust cybersecurity protections for hybrid, online, and in-person settings. For individuals working on-premises, the company's SecurID tech suite supports identity and data security initiatives. RSA's ID + package, which is intended to protect cloud and hybrid environments with mobile and endpoint security capabilities, is available to teams seeking greater flexibility.
What are the Differences Between CyberSecurity and Data Security?
As businesses increasingly rely on computer systems, the relationship between cybersecurity and data security is strengthened. However, there are important distinctions that must be considered as part of best data risk management. Understanding the distinctions between these two terms and how to effectively use their procedures can assist in improving the security of data. Protecting electronic and mobile devices against cyber attacks is the focus of cybersecurity. Data security is the field that deals with safeguarding the availability, confidentiality, and integrity of information.
Ransomware attacks, malware intrusions, and social media penetration are all addressed by cybersecurity. Firewalls and intrusion detection systems(IDS) are two instances of information security controls. Understanding and identifying sensitive information that is crucial or could be the target of a physical or cyber attack is the duty of an information security officer. The vast majority of company data and sensitive data are frequently stored on a laptop, cloud service, or other location online.
Data security focuses on safeguarding data from dangers, whereas cybersecurity aims to avoid cyber attacks by adopting a hacker's attitude. Information risk management requires a fundamental understanding of cybersecurity and data security. Information risk management requires a fundamental understanding of cybersecurity and data security. Physical security measures are still part of the duties of cybersecurity experts, even if their main priority is protecting electronic data from cyber threats and data breaches.
Cybersecurity experts require physical security measures to provide proper data protection, just as information security professionals lock a cabinet full of sensitive information. Although a laptop cannot be physically locked, security measures can be put in place (such as a keycard to enter an office) to deter illegal access in the first place. Companies have to have sufficient security measures in place to prevent unwanted access, regardless of how their information is stored. Otherwise, physical security flaws and cybercrime may easily target your enterprise.
| Cybersecurity | Data Security | |
|---|---|---|
| Definition | It is the process of securing data on the internet from outside resources. | To ensure confidentiality, integrity, and availability, data must be safeguarded from unauthorized users, access, and data change or removal. |
| Protection | It concerns the capacity to defend online activity against cyber threats. | It deals with safeguarding data against all threats. |
| Scope | Cybersecurity is to safeguard anything online. | Data security applies to all types of information, regardless of industry. |
| Threat | The threat in cyberspace is addressed through cybersecurity. | Data protection from all threats is the subject of data security. |
| Attacks | Cybercrime, cyber fraud, and law enforcement are all targets of cybersecurity. | Protection from illegal access, disclosure, modifications, and interruption is provided by information security. |
| Focuses on | It deals with issues that could or might not exist in the online world, such as securing your social media account, private data, etc. | It deals with the availability, confidentiality, and integrity of information assets. |
| Professions | Professionals in cybersecurity work to prevent active attacks or Advanced Persistent Threats (APT). | Data security is built on data security specialists, and those people are in charge of the organizational roles, procedures, and policies that ensure integrity, confidentiality, and availability. |
| Defence | Serves as the initial line of protection. | Plays a role if security is breached. |
| Examples | Application Security, Network Security, Cloud Security, Critical Infrastructure | Procedural Controls, Access Limitations, Technical Restrictions, Controls for Compliance |
Table 1. Cybersecurity vs Data Security
