What is Cloud Infrastructure Entitlement Management (CIEM)?
As organizations migrate more of their systems and business operations to the cloud, regulating and monitoring access to these resources becomes more difficult. No longer are cloud resources static and predictable. In addition, organizations are choosing multi-cloud infrastructure strategies as opposed to operating in a single cloud. Therefore, it is no longer simple to set the correct permissions for accessing these resources.
Cloud security solutions, such as Cloud Security Posture Management (CSPM) instruments, Cloud Workload Protection Platforms (CWPP), and Cloud Access Security Brokers (CASB), provide limited visibility and control on cloud infrastructure entitlements. The remedy for this problem is cloud infrastructure entitlement management (CIEM). Cloud Infrastructure Entitlements Management solutions are intended to handle privileges in complex and dynamic settings with precision and consistency.
In this article, we will describe what cloud infrastructure entitlement management (CIEM) is, the importance and benefits of CIEM, the cloud security challenges solved by CIEM, the limitations of CIEM, the main components of CIEM, how CIEM works, things to consider when selecting a CIEM solution, top CIEM vendors, and the differences between CIEM, PAM, and IAM.
What Does CIEM Mean?
Cloud infrastructure entitlement management (CIEM) is a category of automated cloud security solutions that mitigate the risk of data breaches in public cloud environments. CIEM solutions prevent excessive entitlements by continuously monitoring the permissions and activity of human and nonhuman entities to ensure they're operating within appropriate access controls.
The inclusion of CIEM in Gartner's Hype Cycle for Cloud Security, 2020, elevated its visibility as a cloud security technology relative newcomer. Gartner presents the following definition in this report:
"Cloud infrastructure entitlement management (CIEM) offerings are specialized identity-centric SaaS solutions focused on managing cloud access risk via administration-time controls for the governance of entitlements in hybrid and multi-cloud IaaS."
CIEM solutions apply the Principle of Least Privilege (POLP) to cloud infrastructure access, providing IT and security companies granular control over cloud rights and complete visibility into entitlements. They help organizations increase security, decrease risks, and expedite the adoption of cloud-native apps and services by finding and deleting unnecessary permissions.
The majority of CIEM systems provide a single dashboard for monitoring and controlling access rights to resources, services, and administrative accounts dispersed across public clouds such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Leading CIEM systems deliver AI-powered analysis and evaluation tools to intelligently detect and prioritize risks related to configuration issues, shadow admin accounts, and excessive permissions for human, application, and machine identities. This enables cloud security teams to prioritize remedial efforts and establish a proactive, well-informed phased strategy to reduce risk.
An effective CIEM solution provides comprehensive, automated reporting that enables an organization to streamline access management, strengthen overall cloud security posture, and minimize DevOps disruption.
What are the Components of CIEM?
There are a variety of CIEM systems available on the market, none of which share the same components or functionality. Nonetheless, they all share the following fundamental elements:
-
Centralized Management: A dashboard that enables your team to manage your whole multi-cloud environment from a centralized location.
-
Governance of Identity: the rules that define which human and nonhuman entities are subject to certain regulations.
-
Rules: Rules governing the who, what, when, where, and why of cloud and workload access.
Why Do You Need CIEM?
Modern enterprises continue to expand their processes, applications, workloads, and data across platforms from cloud service providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) as they shift more of their core activities to the cloud.
There is a large number of unique rights issued to individuals, systems, and cloud services inside the cloud ecosystem of a single business, including non-federated accounts, default and incorrect permissions, and even unused permissions. Unchecked, they significantly enlarge your attack surface, making it simpler for attackers to penetrate cloud installations. Gartner predicts that by 2023, 75% of cloud security problems would be attributable to insufficient management of identity, access, and privileges.
Widespread legacy security solutions, such as privileged access management (PAM), do not adequately address modern entitlement issues; they either cannot keep up with the ephemeral, flexible nature of the cloud, or they concentrate on cloud configuration without providing visibility into enterprise entitlements. CIEM tackles these challenges by offering a comprehensive insight into cloud entitlements as well as automatic correction to assist organizations in maintaining least-privileged access.
Managing cloud access risk for a typical contemporary firm requires more than knowing who has access to what. In reality, in many situations, there is no "person" to manage. Over fifty percent of cloud rights are now issued to computers, apps, and service accounts. OT (Operational Technology) and IoT (Internet of Things) devices link to applications and databases that are also interconnected and continuously exchange data. To avoid unauthorized data sharing, privileges must be well specified. With possibly thousands of users and services, tens of thousands of resources, and tens of millions of individual entitlements to manage, a human team cannot act fast or precisely enough to keep up with changing needs. In modern contexts, only CIEM and automation can do this.
What are the Challenges Addressed by CIEM?
The classic IAM strategy for static cloud environments is unsuitable when applied to today's dynamic, multi-cloud systems. Moreover, a manual method used at the scale of modern settings with possibly hundreds of resources and much more organizations requiring access to those resources is impractical and would result in accidentally excessive permissions, hence increasing the danger of a security breach.
The answer to this problem is cloud infrastructure entitlement management. A successful CIEM system comprises generic identity and access management (IAM) settings in addition to privileged access management, offering automated governance to enable you:
-
Maintain visibility and maintain compliance across many cloud infrastructures with varying security standards, governance needs, etc.: Numerous businesses utilize a multi-cloud strategy, opting to host their resources in distinct clouds due to cost, availability, or other considerations. AWS, Azure, and GCP have distinct IAM strategies, as do all other cloud providers. This leaves businesses without a single, uniform method for controlling rights across their whole cloud resources. Instead, they must distribute and manage numerous strategies for multiple cloud service providers.
-
Control excessive permissions to avoid misuse or abuse by human and nonhuman accounts, especially privileged accounts, in dynamic multi-cloud setups that may span the globe: People or processes may provide or deprovision resources at any time in modern cloud systems. The management of access to these resources necessitates a dynamic strategy. Similarly complicated is the monitoring of access to these ephemeral resources. As different users, programs, and devices are granted different rights to access cloud resources, monitoring access is essential for guaranteeing security and enhancing an organization's security posture. However, at the size of hundreds or thousands of resources, it is quite difficult to establish this kind of tracking.
-
Remove obstacles to rapid, agile DevOps so that developers may continue to deliver code quickly and safely.
What are the Advantages of CIEM?
An efficient CIEM solution allows you to view entitlements across your organization's users, nonhuman identities, and cloud resources; evaluate the entitlements landscape to reveal risk; identify threats, and preserve the least privileged access. The main benefits of CIEM implementation are explained below:
-
Enhanced General Security: A well-designed CIEM solution decreases your public cloud risk by allowing you to:
- Implement the notion of least privilege, an essential element of zero trust
- Identify cloud transactions that may represent internal or external dangers, such as hostile activity, human mistakes, or security policy violations.
- Implement standard stipulations across numerous cloud environments with distinct security settings.
- Create and maintain a comprehensive inventory of existing entitlements.
- Identify high-priority problems and provide remediation strategies to address them.
- Identify and automatically correct entitlements that are misconfigured, underutilized, policy-violating, or otherwise problematic.
-
Visibility via a Single Display: CIEM offers a consolidated view of entitlements across numerous cloud platforms so that "who sees what" in the cloud can be governed more simply. This summary of rights assists your team in assessing risk and developing mitigation plans. In addition, CIEM enables your security team to control which human and nonhuman users have access to which resources across numerous clouds, services, users, and organizations, supported by automated, comprehensive reporting.
-
Acceleration and Flexibility for DevOps: Your DevOps team oversees the setup of access to your cloud infrastructure, but creativity and speed, not security, drive the team. Granular, manual permissioning required to ensure least-privileged access is too time-consuming for DevOps to manage, hence it is typical for DevOps to provide excessive rights to speed a rollout or deliver services more effectively. CIEM technologies instantly fix excessive permissions without damaging apps or affecting DevOps, allowing your engineers to focus on their core competencies.
-
Compliance: Monitoring and safeguarding entitlements across your cloud platforms enable you to comply with compliance requirements and standards pertaining to user permissions.
-
Productivity and Innovation Enhancement: When businesses deploy new apps and workloads, CIEM technologies handle problems resulting from excessive permissions. Consequently, firms are able to increase output while avoiding interruptions.
-
Business Continuity: Organizations are better equipped to prevent business interruptions with CIEM monitoring the whole infrastructure for access and entitlement abnormalities.
-
Reduced Expenses: CIEM gives total insight into application use. This knowledge provides more educated choices on capacity needs, cloud subscription management, or upgrading to new cloud environments, hence enhancing the cost-effectiveness of cloud computing resources.
What are the Limitations of CIEM?
The CIEM industry in cloud security is still very young, hence the technology is not yet completely developed. Numerous solutions are not created holistically, but rather piecemeal, to solve certain gaps in goods controlling access and identity governance. In addition, CIEM systems need a substantial initial commitment of money and resources as teams adopt the solution and understand how it functions. Because CIEM is designed for complicated cloud settings, installing the solution without the proper assistance is daunting.
CIEM is quickly becoming a best-practice cloud security technique despite these early shortcomings. When properly implemented, CIEM replaces and enhances human interventions and disparate security solutions. The result is a simplified, centralized access management platform that allows teams to automatically and continuously scale their rights across dynamic, multi-cloud environments without interruption.
How Does CIEM Work?
Today's CIEM solutions provide business security teams with dashboards that facilitate the viewing of all their resources across all clouds. Incorporated within these dashboards are controls for managing access to the cloud infrastructure resources in question. In modern cloud systems, CIEM solutions manage both the huge volume and ephemeral nature of resources.
The usual strategy of CIEM solutions is to apply the Principle of Least Privilege (POLP), which is the method of allowing a user (or any entity) the bare minimal rights required for them to accomplish their task. By adopting this stance, CIEM solutions prevent the risks associated with excessive permissions.
Additionally, CIEM solutions standardize the vocabulary and use of security across all clouds, reducing the requirement for teams to adjust context across numerous cloud providers.
Lastly, many CIEM systems leverage machine learning to assess an enterprise's possible access risks by analyzing access logs and settings. By doing so, a CIEM may assist in identifying excessive entitlements and reducing the danger of a security compromise.
What is CIEM Lifecycle?
All successful CIEM systems should adhere to the CIEM lifecycle to ensure scalable enforcement of the principle of least privilege (POLP) across cloud deployments. The framework allows enterprises to manage and monitor the entitlements of all identities in multi-cloud settings with ease. Effective CIEM systems adhere to a five-stage lifecycle for cloud IAM functionality:
-
Account and Entitlement Discovery: Offers granular visibility of cloud identities and associated entitlements, consistent with cloud-based activities.
-
Entitlement Optimization: Utilizes the principle of least privilege to enforce stringent access restrictions for entitlement optimization.
-
Cross-Cloud Entitlement Correlation: Enables consistency of entitlement rules across cloud installations.
-
Entitlement Visualization: Converts data points into succinct, actionable insights, allowing security and DevOps teams to monitor cloud security posture and user access to cloud resources efficiently.
-
Remediation: Identifies vulnerabilities associated with access rights, such as excessive permissions, and gives security and DevOps teams notifications and automatic solutions when hazards are found.
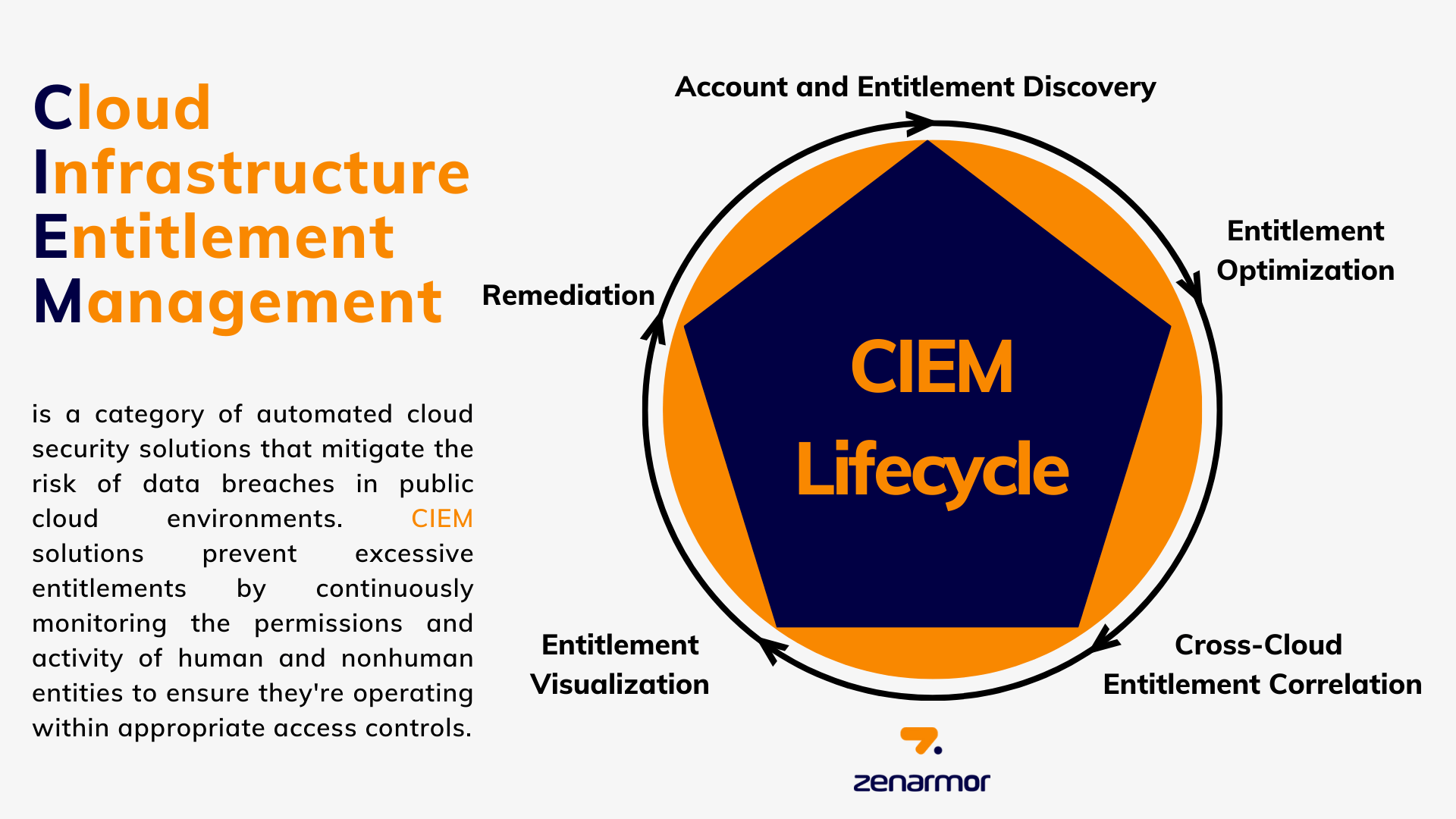
Figure 1. What is CIEM Lifecycle?
Does Your Organization Need CIEM?
Not every organization or cloud environment needs CIEM. You may be able to get away with CSPM and manual examination of your cloud entitlement setups, if your cloud environment is quite modest, consisting of only one cloud platform, one cloud account, and a few cloud services. However, if you utilize numerous clouds or various access control frameworks, CIEM is critical for tracking entitlements and recognizing excess entitlement concerns across all of them. In fact, you benefit from CIEM as an efficient and automated way of verifying that each entitlement is correctly described, even if you just use a single cloud platform and a single access control framework, but have specified hundreds or thousands of entitlements.
How to Select the Appropriate CIEM Solution?
CIEM is a new market that is expanding. The capabilities of vendor solutions differ greatly, thus it is essential to assess alternatives thoroughly. You should consider the following capabilities when choosing a CIEM solution for your organization:
-
Encompassing visibility
-
A straightforward interface
-
Remediation and mitigation
-
Robust intrusion detection
As CIEM technology is still relatively new, seek a solution that combines cloud support and installation help to guarantee a smooth transition and seamless integration with your existing architecture and security stack. The finest suppliers should have already migrated and provisioned cloud-based security solutions. Select a platform that specializes in integrating cloud security solutions to get cutting-edge knowledge.
What are the Best CIEM Providers?
The following suppliers provide enterprises with efficient CIEM solutions:
-
Saviynt: The platform from Saviynt develops and enforces risk-based access restrictions for machine identities, enabling enterprises to expand governance, safeguard data, and comply with regulations. Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform are all compatible with Saviynt (GCP). Some features of Saviynt are given below:
- Identity and access management lifecycle
- Cross-application Separation of Duties (SoD)
- Real-time automated provisioning
- Manage exchange
- Governance of Data Access Based on Risk
- Fine-Grained Entitlement Visibility
-
Authomize: The platform of Authomize merges SaaS, Platform-as-a-Service (PaaS), Data, IT Service Management (ITSM), and (Identity Providers) IdPs Identity Providers to standardize and correlate an organization's identity and account entitlements, so producing a uniform access and authorization model. Authomize is interoperable with all of the leading cloud service providers (CSPs), such as Azure, AWS, and GCP. Principal attributes of Authomize are listed below:
- Detection of suspicious conduct
- Least privilege enforcement
- Crown Jewel security
- Cloud guardrail enforcement
-
CloudKnox Security: The CloudKnox Permissions Management platform from CloudKnox Security is a cloud infrastructure entitlement management (CIEM) system that gives visibility and control over cloud identity permissions. CloudKnox is compatible with Google Cloud Platform (GCP), Amazon Web Services (AWS), and Microsoft Azure. The main features of CloudKnox have listed below:
- Automatic least-privilege access
- Full visibility
- Comprehensive cloud access policies
-
Britive: Britive is a cloud-native technology that provides cross-cloud unified access. Britive is compatible with Azure, Amazon Web Services, Google Cloud Platform, Oracle Cloud, and Service Now. Principal attributes of Britive are given below:
- Secrets administration
- Just-in-time procurement
- Proactive threat surveillance
- Cross-cloud exploration
- Least privilege enforcement
-
Obsidian Security: Obsidian Security is interoperable with all major cloud service providers, including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). The primary features of Obsidian Security are listed below:
- User authorization and activity tracking
- Models based on machine learning to detect privilege creep
- User authorization and activity tracking
- Data analytics
-
Ermetic: Ermetic automates the administration of entitlements and risk mitigation. The platform is interoperable with all major cloud service providers, including Azure, Amazon Web Services, and Google Cloud Platform. The major features of Ermetic are as follows:
- Risk evaluation of identities, networks, and data
- Multi-cloud transparency and asset administration
- Automatic correction
- Anamoly and threat identification
- Proactive enforcement of policy and shift left
- Compliance and access management
-
SailPoint: Using AI and machine learning, SailPoint's Cloud Governance platform detects and secures cloud platforms and resources. Some features of SailPoint are given below:
- Automated provisioning and monitoring of access
- Full visibility
- Automated access control audits and report generation
- Policy modeling and administration
-
Zscaler: The Cloud Protection solution from Zscaler assures least-privilege access to cloud resources for users, apps, and machines using machine learning-recommended access controls. Zscaler Cloud Protection is interoperable with all major cloud service providers (CSPs), including Azure, Amazon Web Services, and Google Cloud Platform. Principal attributes of Zscaler are as follows:
- Risk-based prioritization
- "Safe to Remove" access policies
- Component of a broader data protection framework
What are the Differences Between CIEM and PAM?
Privileged access management (PAM) is an approach to information security that comprises the rules and technology an organization employs to govern, monitor, and safeguard elevated access to essential resources. The primary objective of PAM systems is to safeguard user access to privileged accounts.
Despite the fact that certain recent PAM systems can handle cloud identities and coarse-grained entitlements, they are incapable of giving granular insight, assessing permissions, or comprehending enormous numbers of configurations in scaled-up, complicated cloud settings. On the other hand, CIEM systems provide the visibility, monitoring, governance, and compliance required to enable full entitlement management and granular access control.
What are the Differences Between CIEM and IAM?
Identity and Access Management (IAM) is the framework of rules, procedures, and technology for controlling user identities and access to sensitive data. IAM systems include single sign-on, two-factor authentication, multi-factor authentication, and PAM. Traditional IAM solutions, on the other hand, were developed for self-hosted or on-premises architecture.
Existing cloud IAM solutions have limited applicability in a multi-cloud context. Each provider has its own set of regulations, and mapping rights across many platforms at scale introduces security and visibility gaps. As a cloud-native solution to enforce IAM regulations and implement least-privileged access, CIEM solves this access management need.