Holistic View of Operational Technology Security
The term "operational technology" (OT) refers to hardware and software that detects or causes a change in the enterprise by directly monitoring and/or controlling physical devices, processes, and events. OT is widely used in industrial control systems (ICS), such as a SCADA systems. Computer systems designed for deployment in critical infrastructure (power, water, etc.), manufacturing, and similar industries are examples of operational technology (OT). They automate, monitor, and manage industrial machinery operations by utilizing custom protocols and software to communicate with legacy and proprietary systems.
The high availability requirements of OT make system downtime for updates and malware removal difficult. According to popular belief, it is more important for a system to run continuously than it is for it to be completely secure. As a result, these systems are vulnerable to targeted attacks and malware infections. As a result, and as this technology advances and converges with networked technology, the demand for OT security grows exponentially.
We will cover all aspects of operational technology (OT) security in this article.
The following headings are also included in the article.
-
What is Operational Technology Security?
-
What are the Components of Operational Technology?
-
What is the relationship between I0T and OT and IIOT
-
What is the Difference Between IT and OT Security?
-
Why is OT Cybersecurity Important?
-
Operational Technology (OT) Security Best Practices
-
What are the Common Security Challenges that Require OT Security?
-
Case studies and examples of OT security in action?
-
What are the Significant OT Cyberattacks?
-
Choosing the right OT Security Vendor: What to Look For?
-
Future developments and trends in OT security
-
Operational technology security history
What is Operational Technology Security?
Stacks of hardware and software that carry out security measures are referred to as "operational technology" (OT) security. Operational technology (OT) security is tailored to the specific security requirements of OT environments. This includes safeguarding system availability, comprehending OT-specific protocols, and preventing attacks on legacy systems commonly used in OT environments. OT security aids in the monitoring, detection, and control of changes in industrial network devices, events, and processes. OT security is used to safeguard these networks and systems from malicious attacks. Operational technology security services include smart city appliances, power plants, and transportation networks.
What are the Components of Operational Technology?
Industrial control systems (ICSs) like programmable logic controllers (PLCs), distributed control systems (DCSs), and supervisory control and data acquisition (SCADA) systems are included in operational technology (OT).
Operational technology is primarily composed of industrial control systems (ICS). Devices, systems, controls, and networks of various kinds are included in ICS and are used to manage a range of industrial processes.
Industrial Control Systems (ICS) refers to the physical operations of all machinery, equipment, and devices as they cooperate with one another, whereas OT refers to the hardware and software components of an operational industrial facility (think of a flavor manufacturing facility, wastewater treatment plant, and so on). Machine performance and employee safety are given priority in industrial control system security.
Supervisory control and data acquisition (SCADA) systems and distributed control systems (DCS) are the most prevalent ICSs.
SCADA systems gather data from sensors, frequently at dispersed sites, and transmit it to a centralized computer for management and control. DCS is used to centrally manage local controllers or production system devices.
Additionally, a variety of sensors, monitors, actuators, and other technologies that are installed on or close to OT equipment make up the smallest parts of operational technology. This equipment is widely used and includes things like pipelines, fans, programmable logic controllers (PLC), industrial robots, and remote processing units (RPU). IIOT uses these sensors as an example.
What is the Relationship Between I0T, OT, and IIOT?
In the context of Industry 4.0 and digital transformation, various acronyms like IT, OT, IoT, and IIoT are commonly employed. At its most basic, "Industry 4.0" refers to the fourth industrial revolution, in which all equipment, machinery, and factories are linked, and (big) data is generated, analyzed, and used to improve processes. The use of digital technologies to improve an industry's procedures and customer experience is known as "digital transformation".
The "Internet of Things" (IoT) refers to the act of connecting ordinary physical objects to the internet. Wearables and smart gadgets are included, as are typical household products like lightbulbs and healthcare equipment like medical devices. All have a wide range of applications, and some even have their own apps. These IoT-enabled devices connect to, receive, and transport data across wireless IT networks, maybe with the assistance of a data center, with little to no human intervention.
The Industrial Internet of Things (IIoT), a subset of the Internet of Things, refers to linked equipment used in manufacturing, energy production, and other industrial settings. IIoT is frequently connected to OT and is important for increasing automation and enabling self-monitoring in industrial machines. IIoT improves operations, helps end users make business decisions, and increases plant productivity for manufacturers when used in conjunction with edge computing.
Many aspects of OT and IT settings, including the use of IoT and IIoT devices, are converging as OT systems are increasingly regularly connected to networks and, with a new level of bandwidth, are able to generate and utilize increasing volumes of data.
The biggest contribution that IIoT technology's arrival makes to IT/OT convergence is that it serves as a bridge between the two. It accomplishes this by minimizing time delays, allowing both OT and IT components to access data as it is being generated.
Because a new analytics platform employing IIoT does not necessitate the procurement of new equipment to bring all physical equipment under the same system umbrella, this bridge enables the organization to gain a higher ROI on equipment.
Finally, its programming and processing flexibility play a key part in its function as a bridge. This entails that businesses can buy full platforms with software interoperability built-in or able to be paired with APIs to access information that has been segregated and have all functional areas connected to the same analytics platform.
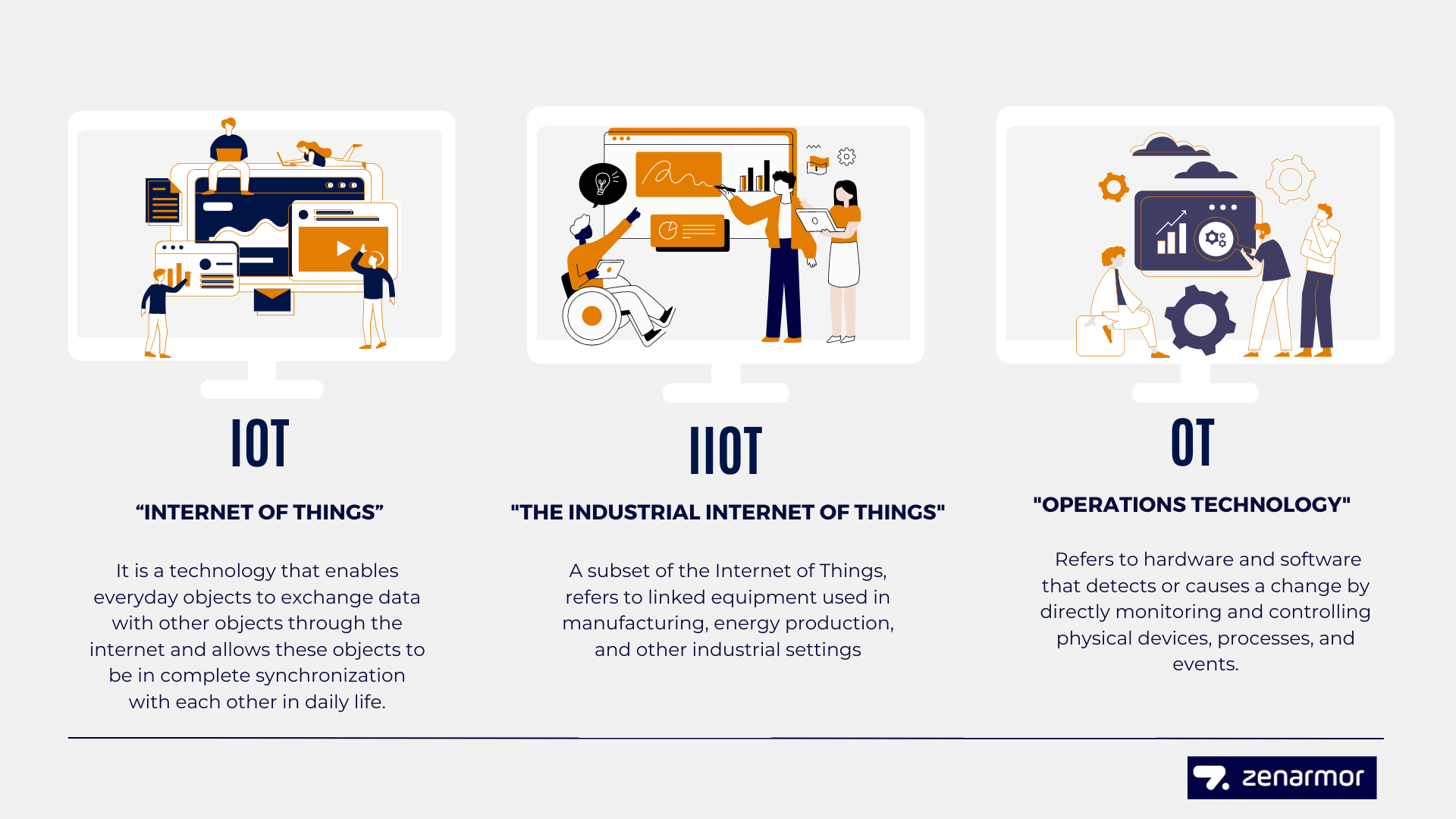
Figure 1. IT vs IIOT vs OT
What is the Difference Between IT and OT Security?
Information Technology (IT) refers to hardware, software, and communication technologies that focus on data storage, recovery, transmission, manipulation, and protection. The term "operations technology" (OT) refers to hardware and software that detects or causes a change by directly monitoring and controlling physical devices, processes, and events.
Despite the fact that operational and information technologies are becoming more intertwined, there are several key differences that both IT and OT personnel must be aware of.
Five key differences between IT and OT are outlined below:
-
Each IT and OT offer different functions in different environments: The two technologies operate in distinct environments and serve distinct functions. OT systems, in a nutshell, are autonomous, isolated, self-contained, and run proprietary software. IT systems, on the other hand, are networked, lack autonomy, and typically run on popular operating systems such as iOS and Windows.
-
IT prioritizes confidentiality, while OT prioritizes safety: Data and confidentiality are top priorities in IT because it primarily involves the storage, retrieval, manipulation, and transmission of digital information. IT security is critical in any organization to keep data secure and under control.
The safety and availability of equipment and processes are paramount in OT. Working with physical systems that must maintain constant values, such as temperature and RPM, necessitates precise control. Lack of control results in significant financial losses due to temporary production halts or even direct physical harm.
-
IT incidents are more common, while OT incidents are more destructive: Simply put, IT has more internet connections. These gateways pose greater security risks because each one could be a hacker waiting to strike.
Because there are fewer gateways in OT, it is considered safer. The potential impact of compromised physical equipment, on the other hand, is greater than that of a data breach. Even minor OT cyber-incidents result in massive financial losses and have far-reaching consequences for the general public, such as water contamination and power outages.
-
They have different security patching approaches: Every week vs. every ten years Because IT components advance so quickly and have such short life spans, a network can look completely different after only a few years.In fact, IT vendors often have a set "update day of the week" or "Patch Tuesday" because security updates are released so frequently.
In OT, security patching functions differently. Vendors operating OT networks rarely, if ever, patch their components because doing so necessitates total shutdowns that halt production. OT components have many more publicly accessible vulnerabilities than IT computers because they are rarely updated. As a result, an OT system has an exponentially higher chance of a successful exploit than an IT system.
-
They may use the same tool for different aims: Despite being made to be used in various ways, operational technology systems share many tools with IT environments. OT devices interact primarily with other machines, such as industrial control systems (ICS), rather than functioning primarily as a tool for humans. They are there to make sure the ICS assets are working properly and that they meet the high availability and uptime standards that these devices demand.
Why is OT Cybersecurity Important?
As a result of their greater connection, industrial systems are more vulnerable. The enormous cost of industrial equipment and the potential harm that an assault could wreak on communities and economies are critical factors for businesses looking to defend their industrial networks.
Security measures are crucial because they protect crucial business data. Attacks are carried out to obtain sensitive information or to impede business operations. Attacks like this one could cost a company a lot of money and resources, whichever way they happen. Deploying security measures like OT security is essential if you want to protect your company from breaches.
As they dealt with issues like transportation and communications, businesses could not afford to stop operating. The inconvenience to customers could result from even a brief pause in operations.
Because of OT security, these enterprises are guaranteed to continue running. This security precaution allows the business process to continue uninterrupted. This way, they avoid losses and client unhappiness.
Operational Technology (OT) Security Best Practices
Security in operational technology environments frequently lags behind that of their IT counterparts. OT security best practices must be implemented in order to protect these OT environments and systems from cyber threats.
Among the OT security best practices for putting in place a trustworthy defense system are as follows:
-
Full visibility and management of OT asset inventory through automatic discovery: Utilizing a tool that performs continuous updates and provides details about potential vulnerabilities, the asset inventory process should be automated. OT security managers are more effective because they have access to more precise information thanks to automated asset inventory. Additionally, it eliminates the danger of unreported shadow OT devices that could develop into undetected attack vectors.
-
Maps of networks and analyses of connectivity: OT security managers must be aware of where each device is located on the network and which devices it is connected to. OT managers must be informed immediately if a PLC communicates with another PLC without authorization rather than learning about it after production is harmed or there is potential for downtime.
-
Finding suspicious behavior, security breaches, and malware attacks: A security information and event management (SIEM) system frequently handles the detection of these kinds of activities and threats. It is simpler for the technology and personnel involved in SIEM systems to evaluate the types of cyber attacks and activity that have an impact on your operational technology because they are deeply familiar with the threats on the landscape. Next-generation firewalls (NGFWs), like Zenarmor, which scan data packets streaming into your network from the internet, can also be used to detect threats. Your system and its assets can be protected if a threat is identified and the data packet associated with it is discarded.
-
Proactive, actionable alerts about threats and weaknesses in the OT network: Before they are used by malware or potential attackers, OT security managers must assess the criticality of their assets, their vulnerable hosts, and their exposed network areas. Instead of having to respond to a cyberattack, gathering this information will assist teams in preventing the next one. By being proactive, businesses can avoid losses of hundreds of millions of dollars and recovery times for production processes that are weeks or even months long.
-
Introduce a Zero-Trust Framework: Never trust, always verify is the foundation of a zero-trust framework. Every user, device, application, and network is considered a potential threat within this type of system. Therefore, before being given permission to connect, each of these entities must demonstrate its legitimacy. Multi-factor authentication (MFA) tools, which demand multiple methods of identity verification, are frequently used in this.
-
Set the Proper Remote Access Tools Up: It's crucial to make sure the appropriate individuals and groups have access to your operational technology, particularly because they might be crucial to the operation of your business. Because an OT system typically lacks a comprehensive array of tools that can be precisely configured to enable remote access, it frequently differs from an IT system. Administrators should make sure to pay attention to the following in order to account for this difference:
- Managing credentials and identities
- Regulating security and passwords
- Ensuring the appropriate individuals have the access they require
- Keeping an eye on and controlling the access rights of both current and former employees
-
Maintain control over identity and access management: Controlling who has access to your system is crucial for maintaining a strong cybersecurity posture, especially since allowing the wrong person access could make it simple for an attacker to break in. Sometimes a well-intentioned employee will leave their login information exposed or insecure, giving a hacker access to a vital system. As a result, you should think about the following:
- Teaching staff members how to protect their access credentials
- Ensuring that an organization-wide least-privilege policy is upheld, which restricts
- Access rights to those who genuinely need them
- Removing former employees' access rights as soon as possible
- Rescinding temporary access granted to visitors and other guests
- Although it is possible to prematurely revoke access privileges, fixing this is typically simpler than recovering from a cyberattack.
-
Complete, in-depth packet analysis of industrial equipment and network activity: Sadly, the majority of OT security vendors today analyze OT networks by "sampling". They do this by picking random OT network packets to feed into their OT security platform for examination. They do this because their systems are unable to handle the enormous amount of data that is being transmitted over the wires. As a result, they only look at a small portion of the data and use it to draw significant but occasionally incorrect conclusions. Since a significant portion of network traffic is not being analyzed, this is a serious issue because it gives OT network managers a false sense of security. You simply cannot leave this up to chance. An OT Security platform must be able to gather and analyze 100% of all packets that pass through the network and be 100% certain that the network is secure in order to be effective.
What are the Common Security Challenges That Require OT Security?
Internet connectivity makes things easier to use, but this change has made OT systems more vulnerable. Even worse, these extremely valuable OT machines could be destroyed by an attack on the physical systems. The most frequent OT security issues that an OT network faces are listed below:
-
Infiltration of Malware through external hardware and removable media: It is risky to use flash drives and external hardware in various locations and systems. It might result in unauthorized and unwanted access. Before entering your system, this external hardware was utilized in various networks. Once they are used to access yours, there is no guarantee that these devices are secure. Your database might be impacted if the hardware turns out to be vulnerable. Because of this, it's crucial that a company provide virus protection and carry out security awareness campaigns.
-
Human Mistake: Another issue that is frequently encountered, not just in the industrial sector but also in other businesses, is human error. Human errors are more difficult to prevent because no system can predict when they will happen. Organizations reduce or eliminate potential consequences by implementing security measures. Operational technology security, for instance, aids organizations in identifying device changes. This can assist management in identifying mistakes early on and preventing further harm to the organization.
-
Internet-based Malware Contamination: The prevalence of malware infection through the internet is alarmingly high right now. These days, a lot of malicious attackers use this to attack industrial databases. Important business documents are exposed to this risk and become vulnerable to leaks. It is crucial to regularly and promptly check the operating systems and applications in the office and back-end networks as a result. By doing this, you can stop malware from entering your system and prevent financial losses.
-
IoT Botnets and DDoS attacks: Different IoT technologies are connected to each organization's network. These consist of condition sensors, grid sensors, security sensors, and PS tracking. These all have unique communication protocols. An organization will have to deal with many different challenges as a result. In today's connected world, as businesses use more IoT devices, the threat of botnet DDoS attacks appears to be growing. For this reason, a company needs to be aware of cybersecurity solutions. This stops problems and malware attacks like these from happening.
Zenarmor NGFW is an effective cybersecurity solution against botnets. You can easily protect your OT asset from being a zombie in a botnet by enabling the Advanced Security features of Zenarmor NGFW. It offers a powerful AI-based cyber threat intelligence database that is updated constantly and frequently to prevent zero-day attacks and advanced threats.
-
Outdated Operating System: An operating system that is out of date and no longer gets security updates is very open to security threats. To avoid compromise, an inventory of all devices, including access points, must be made, and they must all be patched according to the most recent manufacturer guidelines.
-
A lack of Uniform Ownership: Establishing complete security and ownership of a company is crucial. In the case of an industrial unit, it is even more crucial. Ownership of security is split between the manager and the plant operations director, with sporadic support from the C-suite. Although this seems to lighten the load, it actually creates vulnerabilities and encourages threat actors. Monitoring and carrying out surveillance are made challenging by the sharing of security ownership across the hierarchy.
Many manufacturing companies have been slow to recognize the impact of widely dispersed, carefully planned attacks on OT networks.The 'Detection and Recovery' time during a security breach is negatively impacted by a lack of homogenous security ownership.
-
Poor Lighting: Security and output are negatively impacted by the OT components' lack of centralized visibility. In a manufacturing facility, locating a component failure can take a few minutes, hours, or even days. Applying the fix is a completely different matter. This unplanned downtime could have a negative impact on the company's business opportunities and operating schedule. The enterprise's security risk is significantly increased as a result. Knowing which devices are joining and leaving the network in real-time is impossible without centralized visibility of the entire OT network.
-
Insecure Passwords: For easy network access, operators have been using insecure passwords. Due to this, it is simple for attackers to obtain operator access without authorization by using brute-force password discovery.
-
The Cloud and Internet: OT networks use the cloud to maximize efficiency and achieve optimal resource utilization. In order to meet hardware requirements and other needs, OT networks rely heavily on vendors. The cloud is regularly used by numerous outside vendors. Few third-party suppliers offer product warranties unless they have online access to the plant floor. Vendors use this access to remotely manage and control their machinery. Any vendor-side weakness could jeopardize the safety of the OT network. The majority of businesses have direct access to the internet. It is well known that malware can be introduced into OT networks using just one internet-connected device as a gateway by attackers.
-
The Sub-Components' Security Posture: Endpoints are protected by OT security systems on an industrial network. These endpoints include everything from computers that manage the CCTV setup to those that manage the safety operations for the entire production system. Although the visible endpoints are well protected, the sub-components and subsystems are not. Usually, these internal parts and systems don't adhere to the same security standards.
-
The Convergence of OT and IT: Every industrialist and SaaS provider finds the union of OT and IT exciting. However, a lot of people ignore the dangers of OT-IT convergence.The discussion shifts to outdated systems that could expose the entire scenario to risk. Additionally, any information delay through ICS networks, regardless of the cause, has the potential to bring the entire system to a halt.
What are the Significant OT Cyberattacks?
For corporations, governments, and other organizations, cyberattacks are a serious threat. The extent of the damage hackers can do has recently been highlighted by attacks on both large corporations and small businesses. Here are a few of the top OT attacks that occurred abroad and decimated private businesses as we watch the number of corporate IT attacks rise:
-
Dragon Night Attack (2006-2011): A simple attack called Operation Night Dragon used Trojan RATs to target crucial infrastructure. According to investigations, SQL injection was used to compromise websites with public-facing content and was later used to install RAT (remote administrative tools).
Night Dragon cannot spread by itself because it is a Trojan backdoor without the ability to infect computers with worms. Attackers installed Night Dragon on numerous computers using a Trojan dropper file (.exe) located on a Windows share. Through the use of spear phishing, remote control tools (RATs), Trojans, and active directory breaches, they were able to combine social engineering with planned, focused cyberattacks.
The attack sequence was carefully planned in order to obtain executive, and private information, including delicate competitive proprietary operations and project finance information regarding oil and gas field bids and operations. At least 71 organizations were targeted, including defense contractors, global businesses, the United Nations, and the International Olympic Committee. These attacks exposed the lack of cybersecurity and laid the groundwork for subsequent attempts to develop beyond simple information theft. As demonstrated by Night Dragon, hackers can now also compromise ICSs.
-
German Steel Mill (2014): Malware that allowed access to the corporate network and later the SCADA/ICS network was targeted in 2014 at a German steel mill. The Federal Office for Information Security (BSI) of the German government confirmed the incident in a security IT report.
Attackers who appeared to target industrial plant workers specifically caused the failure of plant control mechanisms, which led to an uncontrolled furnace and eventually physical damage to the steel factory.
The hackers attempted to access the steel mill network using spear-phishing, according to a study published by the SANS Institute. Most likely, the email had a document attached to it that, when opened, started the malicious malware on the computer.
The malware then created a remote connection point by taking advantage of flaws in a targeted operating system to build a bridge between the attackers and the targeted industrial network. At this point, the hackers were able to alter the programmable logic controllers (PLCAs), endangering the furnace's operation and increasing the damage it sustained.
-
Kemuri Water Company (2016): The alarm was raised long before there were numerous attacks on water/wastewater, oil pipelines, and the food and beverage industry's critical infrastructure that were used to identify threat actors.
Verizon's March 2016 data breach digest described an attack on the Kemuri Water Company, an unidentified water facility.
According to a Verizon valuation study, the hackers profited from a vulnerability in the web server hosting the payment application. The attackers are believed to have stolen 2.5 million records, including customer and payment information, from this server, which held the internal IP addresses and administrative passwords for roughly 400 systems. No proof of fraudulent activity on the hacked accounts has been found by experts.
The compromised systems ran valve and flow control applications used to manipulate the utility's hundreds of programmable logic controllers, which gave the hackers access to the software and allowed them to change settings relating to water flow and the number of chemicals used to treat the water (PLCs).
The amount of lye in the drinking water was reportedly significantly increased by an unknown hacker who connected to TeamViewer software on the computer connected to the water treatment controls. Fortunately, the attack was stopped when a sharp-eyed plant worker noticed the workstation's cursor moving by itself and carrying out unauthorized tasks.
-
Kudankulam Nuclear Power Plant (2019): The Kudankulam Nuclear Power Plant in Tamil Nadu was the target of a cyberattack in early September 2019, according to information released by the Nuclear Power Corporation of India Ltd. (NPCIL) on October 30.
"Domain controller-level access" had taken place at Kudankulam, according to Pukhraj Singh, a cybersecurity expert and former worker of India's signals intelligence agency, the National Technical Research Organization, who tweeted that "extremely mission-critical targets were hit".
The KKNPP, India's largest nuclear power plant, has two VVER pressurized water reactors from Russia that have a combined capacity of 1,000 megawatts. The southern Indian power system receives power from both reactor units. The facility is currently constructing four more identical-capacity reactor units, making Kudankulam a nuclear power plant in India.
A sizable amount of data from the KKNPP's administration network has reportedly been stolen, according to Virus Total. The nuclear power plant experience additional cyberattacks in the future if the latter is true.
Cyberattacks on nuclear power plants could have real-world repercussions, especially if the network that controls the hardware and software that controls the reactor is breached. In the worst-case scenario, this could be used to aid in sabotage, nuclear material theft, or a reactor meltdown. In a country like India with a large population, any radioactive spill from a nuclear facility would be a catastrophic disaster.
-
Dr. Reddy's Laboratories (2020): During Covid-19, when researchers around the world were working to develop vaccines to fend off the virus, pharmaceutical behemoth Dr. Reddy's Laboratories suffered a devastating data breach. The pharmaceutical company recently received permission from the Drug Controller General of India to conduct phase 2/3 trials of the Russian vaccine in India. According to reports, affected plants were located in Brazil, India, Russia, the United States, and the United Kingdom. The CIO of Dr. Reddy's Laboratories declared that the company intended to resume all services within the following day. "We anticipate that this issue won't have a material impact on our operations and that all services will be operational within 24 hours".
-
Colonial Pipeline (2021): The effects of a successful strike in the real world have been amply demonstrated by the ransomware attack that destroyed one of the largest pipelines in the United States.
On April 29, 2021, a ransomware outbreak affected Colonial Pipeline, a Houston, Texas-based oil pipeline system that primarily transports gasoline and jet fuel to the Southeast of the United States. The Colonial Pipeline Company halted all pipeline operations to stem the onslaught. The closure had an effect on both airlines and customers on the East Coast. It was determined that the intrusion posed a threat to national security because the pipeline carries oil from refineries to industrial markets. President Joe Biden subsequently proclaimed a state of emergency. According to reports, on April 29, hackers used a virtual private network account to access the networks of Colonial Pipeline Co.
The initial attack method is unknown. An old, unpatched system flaw, a phishing email that successfully duped a worker, previously disclosed access credentials obtained illegally from another source or any of a number of other tactics used by cybercriminals to breach a company's network could have been to blame.
The DarkSide is responsible for the assaults, according to the FBI. The DarkSide claims in a statement that "our purpose is to generate money [not to create] issues for society" and that it is apolitical, suggesting that it is not connected to any nation-states.Following the pipeline attack, DarkSide made an announcement about its closure.
-
Oil India Limited (2022): Recently, Oil India Limited was the target of a cyberattack, and on April 22, 2022. A spokesperson who confirmed the problem said drilling and production systems were unaffected, but the extent of the damaged systems was not immediately clear. More than Rs 57 crore in ransom has been demanded as a result of the attack.
An Oil India spokesperson claims that there has been no data loss or theft and that the affected systems have been shut down without compromising output. Additionally, he said that the IT team is working to restore the compromised systems.
Choosing the Right OT Security Vendor: What to Look For?
On OT networks, a lot of ports are readily available from the outside. Hackers can access networks and move laterally across infrastructures and locations due to a lack of network visibility and cyber hygiene.
Therefore, it is crucial to invest in stronger cybersecurity procedures and an OT security solution. Nevertheless, selecting such a method should preferably include a thorough investigation. Here are the seven factors to consider and the questions you must ask and respond to in order to assist you to make the best choice.
-
Does the supplier make its own goods?:
Ask a prospective OT cyber security vendor if they manufacture their own products. The rationale is that a business can OEM a product and put its logo on one made by another. This raises questions about the product's quality and the inability to locate new parts. The issue arises when considering how long it will take to fix or replace the item. You'll need to be concerned about bad software support and cyber attacks.
When a vendor creates a product, they are aware of the process, the components, and the location of the assembly. Additionally, they are skilled at fixing it and have engineers on staff to handle any increasing issues. The vendor must be familiar with OT protocols. A vendor could be regarded as mature if they comprehend and support a variety of OT protocols.
-
Has the vendor lately acquired any further inorganic capabilities?:
The OT security sector sees a lot of mergers and acquisitions, so you should be wary of any solution coming from a vendor that recently purchased another security company because the integration of capabilities and features might not have been well-tested and bug-free. However, the solution can be taken into consideration after a lengthy POC.
- Does the solution support OT convergence and security?:
Despite a rise in IT and OT convergence, their networks and architecture differ. The two cannot be managed in cyber security in the same way due to their diversity. Therefore, the same level of security that IT environments provide cannot be provided in an OT context. Based on how well a product can protect both ecosystems, it should be chosen. Its capacity to integrate with other security systems is expanded by this.
- Do they provide vulnerability management and asset discovery?:
You might be shocked to learn that many OT security companies don't include these features in their standard offering. This is a glaring disadvantage because these talents are necessary to create a strong security posture.
- Where does the threat intelligence come from?:
Few manufacturers provide feeds for native OT threat intelligence. If a seller provides something, it needs to be viewed as a distinct benefit.
- Create a cybersecurity strategy for your company:
What exactly is cybersecurity then? It involves protecting networks and data against hostile cyber and electronic crimes.Create a policy to manage your security policies if you outsource security. These regulations cover data handling, access restrictions, and password security. The policies provide vendors the ability to manage anything, including the services they'll offer. Additionally, it's crucial to provide personnel with cybersecurity awareness training.
- Has the solution addressed particular security issues you can relate to?:
Check to see if the solution addresses actual issues rather than theoretical ones by reading some of their case studies.
- Is the solution a mixed one?:
It is a major red flag if the OT security vendor has exclusively picked detection or mitigation from another vendor. Such a security measure would result in a delay in detection and mitigation, and the vector might easily pass undetected through integration cracks. All of the modules in a perfect solution must come from the same supplier.
- Decision data accessibility and deployment simplicity. Does the solution allow for quick deployment and is it modular?:
Once you've chosen a solution, you'll want it to quickly fit into your surroundings. The data dashboards should be uncluttered and allow decision-making from multiple perspectives.
- Do they furthermore provide a thorough consultation and compliance services?:
As consulting services are frequently needed to create a security roadmap and develop OT security skills and knowledge within the workforce, vendors that provide security services for specific end needs perform well in the ratings. Businesses need assistance setting up their workflows, procedures, and systems for audit, reporting, or any other compliance requirement as new compliance mandates are added.
- Assistance with mixed-use situations:
It should be possible for the solution to operate in hybrid contexts with a variety of technologies and gadgets from all eras.
Future Developments and Trends in OT Security
In large part due to the pandemic's aftereffects, 2022 has pushed the Digital Transformation in OT and ICS environments even further: there is intense pressure to make supply chains more efficient (in light of the significant supply chain disruptions we experienced in the last few years) and more resilient, including the use of predictive analytics or even fully-fledged machine learning to predict failures.
As a result, data aggregation in the cloud has increased even more, which is clearly not the conventional or ideal setting for OT and ICS technology. Some patterns that will unavoidably persist beyond 2023 are the result of this pressure and worsening personnel pressures:
-
The Air Gap has mostly vanished: Devices directly connected to the company network have been introduced through new IIoT/IoT initiatives, enabling even more remote operations and opening up new access points. Gaps in industrial contexts have been filled by continuous monitoring and zero trust. A new generation of security solutions that continually protects connected devices dispersed across cloud, IT, and industrial settings is required.
-
Software as a Service and the Cloud Drive Digital Transformation: Vendors and integrators are now providing a variety of cloud implementations, including private, public, and hybrid clouds, each with its own advantages and disadvantages.
At the same time, new digital native firms appear in every market sector, intensifying the competitiveness of businesses that must combine the use of new technologies with their inherited past. Business executives are aware of the necessity to adopt a strategic strategy and integrate digital technology throughout the value chain in order to stay relevant and gain an advantage over competitors.
-
MSSPs are steadily gaining control: Organizations and their MSSPs are searching for technologies that offer the best level of efficiency in order to deploy and support their IT/OT integration with minimal human capacity.
- Playbooks and automation speed up response times by eliminating repetitive operations.
- Artificial intelligence and behavior pattern detection provide threat awareness that is impossible for humans to achieve.
- IT employees and systems are forced to share resources with their OT colleagues.
-
The quantity of vulnerabilities being published is skyrocketing: Asset vulnerability management should go beyond simple vulnerability screening so you can concentrate on flaws with a high potential of causing expensive disruptions:
- A continuous and real-time evaluation of vulnerabilities throughout the entire enterprise
- It is possible to prioritize which vulnerabilities need to be fixed first by categorizing the risk for all known vulnerabilities according to business criticality
- Continuous program management of the vulnerabilities and lifetime of gadgets
- Vulnerability analysts must cut to the chase every time a new high severity vulnerability, or CVE, is released and swiftly ascertain the overall risk it poses to the organization based on all the impacted assets
-
All governments are now completely dedicated to lowering the risk: Every organization eventually learns that proactive risk awareness, management, and mitigation are necessary for converged OT/IT/IIoT security. Now is the time to make strategic platform investments that secure and enable your organization as governments all over the world step up their efforts to eliminate risks. Any technological investment should strive to fulfill the following criteria in light of the current state of OT connection, the shortage of skilled OT SoC analysts, and the rate at which the attack landscape is evolving:
- Complete: full asset visibility throughout the attack surface of the enterprise.
- Constant: supplying required real-time awareness of asset relationships and behaviors
- Intelligent: To more effectively rank incidents and vulnerabilities
- Automated: Enables quicker reaction to threats and operational events
-
Requirement for improved OT systems management: OT must incorporate the fundamental components of IT systems and security management during the next five to 10 years. For their OT systems, the majority of industrial businesses have up until now depended on network security measures like firewalls or data diodes, the fabled "air gap", network anomaly detection, or IDS/IPS. In a defense-in-depth model, no one would question the importance of these activities. But over the following five years, these protections will become less and less effective, necessitating a drive for more OT security management programs.
Operational Technology Security History
The Stuxnet malware, which harmed Iranian uranium enrichment systems, is one instance of a reported incident in which a cybersecurity attack resulted in physical damage. Up to two years before it was finally identified and found, Stuxnet is believed to have been deployed on USB memory sticks. An incident that hurt a furnace in a German smelter is another illustration.
OT environments have experienced operational halts as well as physical damage as a result of cybersecurity incidents. For instance, in 2000, 800,000 liters of sewage were released into nearby waterways after Maroochy Shire in Queensland, Australia, allowing remote access to its sewage control system. Attackers gained remote access to the Kyiv Oblenergo power distribution operator's control systems in 2015, leading to a service interruption that lasted several hours and affected thousands of customers for days.
Attackers in the past were knowledgeable experts who had a thorough understanding of both the technology and the systems they were attacking. But as technology developed, tools were made to make attacks much simpler to execute. The fact that these tools are now more widely accessible and simpler to obtain only serves to complicate matters further. This issue is made worse by the fact that many of the legacy protocols used in IoT environments date back many years and were not originally designed with security in mind. This significantly increases the frequency of attacks and the overall threat to end operators because attackers with little to no technical ability can now launch cyberattacks. Operators have a significant advantage because they are more familiar with their environment and have a better understanding of their processes. As a result, they use a variety of technologies and capabilities to protect their networks from attack. This is crucial because attacks on networks will keep evolving and changing, making it harder to defend against them and respond to them.
For many years, local and geographically dispersed communication networks have been used in industrial settings. Examples of such OT networks include communications between semi-autonomous systems in manufacturing and remote monitoring of substations in the utility industry. In the same companies, these OT-specific communication systems have typically been physically separated from conventional IT enterprise networks and standalone systems. This method of network compartmentalization has resulted in the independent evolution of IT and OT networks, with interconnections between the environments, strictly segregated and monitored, even though it adheres to the conventional logic of "security through obscurity".
Industrial environments frequently involve capital-intensive projects with a long expected lifespan. Since OT-deployed solutions are created to fulfill specific (and frequently one-time) functions and have no requirements or incentives to be upgraded, they frequently have no reason to change, unlike IT-based enterprises. System uptime and high availability are huge priorities in OT, so changes are typically only made to address flaws or add new system capabilities in support of that objective. Deployed OT systems frequently have slower development and upgrade cycles as a result, and they can easily fall out of step with conventional IT network environments. As a result, OT technologies and the knowledge of those responsible for maintaining those operational systems have developed more slowly than their IT counterparts.
The majority of industrial control systems in use today, their parts, and the scant security components that go along with them were created in an era where standard compliance was uncommon. Because these systems were proprietary, threats from the outside world were unlikely to materialize and were rarely addressed. However, there has been a growing pattern of OT system vulnerabilities being identified and reported. Although there have been more reports in recent years, there is probably still a great deal more that has not been found or reported.
Industrial communication and computer technology security investments have historically lagged behind those for securing traditional IT enterprise environments due to the slow rate of change and prolonged upgrade cycles of most OT environments.