What is a Watering Hole Attack and How does it Work?
They contend that when it comes to security, people are the weakest link. Even with the strongest security hardware, software, and procedures in place to guard against cyber assaults, it only takes one person to click on a phishing link they have recently received in an email, and suddenly the entire business is compromised and attackers have access to the system. What do you mean when you say "social engineering"?
Social engineering refers to the psychological persuasion of individuals into taking certain activities or disclosing sensitive information in the context of information or cyber security. Social engineering employs a number of different methods, including phishing, vishing, baiting, scareware, spear phishing, pre-texting, and whaling campaigns, among others. The watering hole attack is one particular social engineering tactic that will be the subject of this article.
In this article, we discuss the following topics related to watering hole attacks.
-
What is a watering hole attack?
-
How do watering hole attacks work?
-
What are some common targets for watering hole attacks and why are they vulnerable?
-
How can you detect and prevent a watering hole attack?
-
What are some real-life examples of successful watering hole attacks?
-
How do attackers choose which websites to use as a watering hole?
-
What are some of the risks associated with a watering hole attack for both individuals and organizations?
-
How can employees be trained to avoid falling victim to a watering hole attack?
-
What role do social engineering and spear phishing play in watering hole attacks?
-
What are some recommended best practices for organizations to protect themselves against watering hole attacks?
-
What is the relationship between watering hole attacks and supply chain attacks?
What is a Watering Hole Attack?
A cyberattack known as a "watering hole" targets particular user groups by infecting websites that they often visit. This concept of a watering hole gets its name from the predatory animals that lurk about them and wait for a chance to ambush victims while they are unaware. Similar to this, watering hole attackers watch specialty websites for opportunities to infiltrate them with malware so that they may then infect their victims.
A watering hole attack is distinct from phishing and spear-phishing attempts, which usually aim to steal data or infect users' devices with malware but are frequently similarly focused, efficient, and difficult to avoid. An alternative strategy is a watering hole assault, which seeks to infect users' laptops before breaking into a nearby corporate network. With this attack vector, cybercriminals can get unauthorized access to crucial enterprise networks and steal intellectual property, financial data, and personal information.
Watering hole attacks are still quite successful despite being extremely infrequent. When cybercriminals utilize zero-day exploits that antivirus detectors and scanners would not discover, they target lawful websites that cannot be banned. Attacks known as "watering holes" put people and businesses in considerable danger if they don't follow security best practices.
How do Watering Hole Attacks Work?
Threat actors must properly plan and carry out their cyberattacks in order to launch a successful watering hole operation. It is critical to understand how such assaults are carried out if you want to defend yourself and your companies against them. Hence, the following is how a watering hole attack operates:
-
Intelligence gathering: The threat actor follows the web surfing patterns of their target in order to acquire intelligence. Search engines, social networking platforms, website demographic information, social engineering, malware, and keyloggers are often used techniques for intelligence collection. Common knowledge is quite useful at times. The thieves have a shortlist of websites they may utilize for a watering hole cyberattack at the conclusion of this phase.
-
Analysis: The list of websites is examined by cybercriminals for domain and subdomain vulnerabilities. Instead, the attackers make a replica of a malicious website. Sometimes they breach a trustworthy website in order to direct targets to a fake one.
-
Preparation: In order to infect their targets, the hackers introduce web-borne vulnerabilities into the website. In order to compromise browsers, such programs take use of online technologies including ActiveX, HTML, JavaScript, pictures, and more. The threat actors employ exploit kits, which give them the ability to infect visitors from certain IP addresses, for more specialized attacks. While concentrating on an organization, these exploit kits are quite helpful.
-
Execution: The attackers wait for the malware to finish its job after preparing the watering hole. If everything goes as planned, the malicious software will be downloaded and run by the target's browsers. Since they frequently indiscriminately download code from websites to local computers and devices, web browsers are exposed to web-borne attacks.
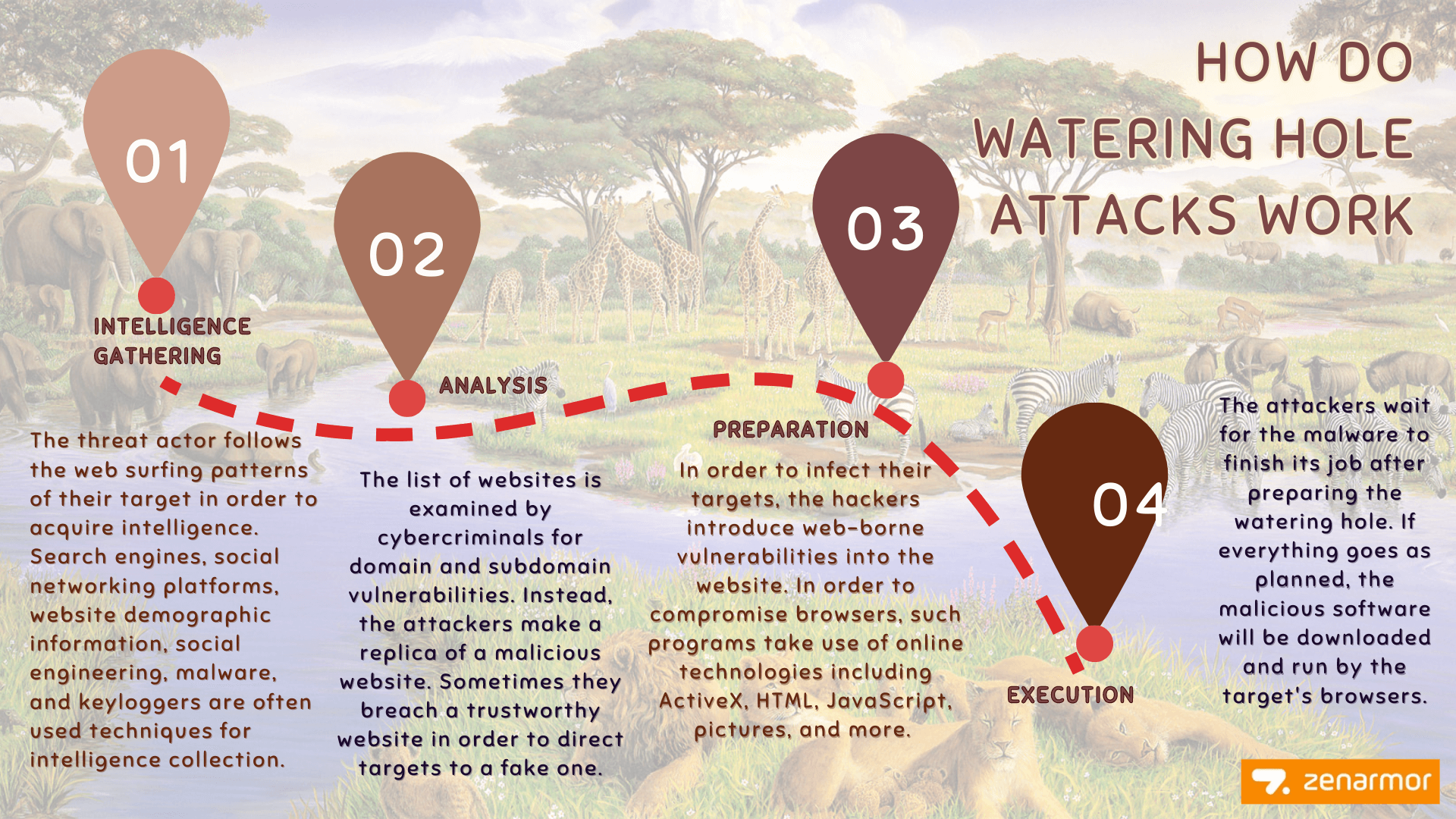
Figure 1. How Watering Hole Attacks Work
What are Common Targets for Watering Hole Attacks and Why are They Vulnerable?
Government entities, human rights organizations, public authorities, and financial institutions are the groups that are most frequently the targets of watering hole attacks. This is because the data obtained from these targets really enables attackers to launch more assaults.
How can you Detect and Prevent a Watering Hole Attack?
Watering hole assaults are challenging to spot due to the following reasons:
-
It could take days or months before anybody recognizes something terrible has transpired since the websites that victims visit appear secure and reputable. By that time, your entire business network may be compromised by malware that secretly leaks sensitive data from your company.
-
The kind of website that visitors arrive at is quite important. A watering hole has to be a location frequented by employees of your business or organization for a targeted attack to be successful.
-
When users' browsers contact the targeted websites to load certain material, a real exploit may take place. Following that, the attackers infect the genuine website with malware, causing visitors to drive-by-download malware when they visit it. An attacker can infect other sites that potential victims could visit in addition to one site they have already targeted with malware. Just hosting the malicious files on any of these domains and ensuring that the server hosting those websites redirects users to any of the target URLs is all that the attackers need to do. This method is frequently referred to as a redirection assault.
-
It may take some time before you become aware of an occurrence and comprehend how it occurred. On computers, malware can be disguised; after being infected, it can not activate right away or might hide for a while. Attackers will attempt to enter your network laterally through weak servers or workstations, which can go unnoticed for a period as well. It's crucial to protect your endpoints, but it's also crucial to keep your servers and systems updated as frequently as feasible.
-
Attackers that employ a watering hole attack approach are attempting to access any devices that are connected to the target victim firm via an unprotected wireless connection. These connections are utilized by people who might not be aware of the dangers of relying on untrusted hotspots and accessing open Wi-Fi in public locations (such as coffee shops, airports, etc.).
Sadly, there isn't just one strategy to stop a watering hole attack. So don't worry, that doesn't imply you have no options. These are the five measures you may follow to protect yourself from a watering hole attack:
-
Raise Awareness of Watering Hole Attacks and Similar Threats: These assaults include hackers building counterfeit websites that contain malware. The genuine, whitelisted websites that employees are likely to visit are imitated by these websites. By tricking users into providing their usernames and passwords or installing malware, counterfeit websites can infect their users' devices.
Companies that maintain rigorous security on their employees' email accounts and Internet access are frequently the targets of "watering hole" assaults. The assault tactic makes advantage of social engineering to avoid any systems and tools you may have in place for detection. Because of this, preventing the threat altogether by spreading knowledge is one of the greatest strategies to guard against it. You may achieve this by using a security awareness program to educate your workforce.
-
Keep Your Systems Up-to-Date: A database of signatures is used by many conventional security systems, including firewalls and anti-virus software, to identify malware and other threats. These databases are regularly updated to provide defense against the most recent threats. Run these updates as soon as possible. It's also a good idea to keep all other software that connects to the Internet up to date. This is crucial for web browsers and browser add-ons in particular, as they are frequently the means through which malware from the internet infects a user's computer. To cause a malware download, malicious code frequently takes use of flaws in the user's web browser or a web-based application. Security updates from browser makers often address these flaws, lowering the likelihood of successful malware infection. As soon as these fixes are published, be sure you install them.
-
Monitor Your Network and Web Traffic: Watering hole attacks are avoided by keeping an eye on network activity and any external site traffic. It can spot malicious behavior and irregularities that can point to an assault. Obtaining antivirus software or other cutting-edge technologies like endpoint detection and response (EDR) tools can help you do this.
-
Use a Virtual Private Network (VPN): A VPN can mask internet activity coming from outside sources, making it more difficult for attackers to identify potential targets inside your company. To prevent your employees from using unprotected websites like social media and message boards, a VPN is occasionally required.
-
Get a Security Audit from Experts: Having your computer network inspected by reputable cybersecurity professionals is the best way to maintain it worry-free. They can identify weaknesses you might have overlooked and provide solutions. A regular security review is a wise investment that might aid in thwarting future threats.
What are Real-life Examples of Successful Watering Hole Attacks?
Some well-known real-life examples of watering hole attacks are explained below:
-
Twitter, Microsoft, Apple, Facebook: In 2013, hackers were able to access systems at Facebook, Twitter, Microsoft, and Apple as part of a broad operation utilizing websites that drew staff from several well-known corporations. Two websites for developing mobile applications, one of which being
iPhoneDevSDK.com, were among the watering holes utilized by the attackers. The Java browser plug-in, which is available for both Windows and Macintosh computers, has a zero-day vulnerability that was exploited by websites that had been infiltrated. In addition to the four big enterprises listed, additional companies including automakers, government organizations, and numerous other companies were also impacted by similar watering hole attacks. -
LuckyMouse: Throughout 2017 and 2018, a Chinese threat actor collective known as LuckyMouse organized a cyber espionage operation against one of the nation's data centers in a central Asian nation in order to launch watering hole attacks with the goal of gaining access to multiple government resources. In order to compromise accounts belonging to data center staff, the gang inserted malicious JavaScript code into official government websites linked to the data center. The victims were infected with the HyperBro RAT (Remote Access Trojan), which gave the perpetrators access to remote administration.
-
OceanLotus: Many Southeast Asian websites were the focus of a watering hole effort in 2018 and 2019. Over 20 compromised websites, including the Ministry of Defense of Cambodia, the Ministry of Foreign Affairs and International Cooperation of Cambodia, and several Vietnamese news and blog outlets, were discovered during this campaign, which was thought to have been organized by the OceanLotus group. Only users from Vietnam and Cambodia have been exposed to the infection thanks to a little piece of malicious code that the attackers introduced to the hijacked websites.
-
ICAO: Once again, LuckyMouse. In 2016, the advanced persistent threat LuckyMouse was blamed for an assault on the International Civil Aviation Organization (ICAO), a special agency of the United Nations. The gang was successful in compromising two ICAO servers as well as the domain admin, administrator, and mail server accounts. Yet, because they were employed to contact the intended targets, United Nations members, ICAO was only a component of a watering hole attack. Following the ICAO cyberattack, at least one UN member state was affected.
-
Epic Turla: One of the most sophisticated and continuous cyberspying operations to take place between 2014 and 2016 was Turla. The "Epic" operation, which primarily targeted Middle Eastern and European governments, embassies, and military, research, educational, and pharmaceutical institutions, served as the initial stage of infection in the Turla campaign. Attackers infected victims through spear phishing emails as well as watering hole attacks, the latter of which relied on users being duped into installing phony Flash Player malware installers. Watering hole attacks leveraged an arbitrary code-execution vulnerability in Adobe Reader and Java vulnerabilities.
How do Attackers Choose Which Websites to Use as a Watering Hole?
Attackers frequently pick well-known websites that are frequently visited by their targets or that come highly recommended. Due to the site's popularity, the attacker has access to a sizable pool of prospective spear phishing and other attack targets. Compared to other forms of social engineering, using recommendations from friends and coworkers for reliable websites carries greater weight.
Watering hole attacks always target two different sorts of targets: the legitimate website or service that the attackers hack in order to embed their malicious infrastructure, as well as the users who are infected when they visit. Attackers have become more adept at leaving as little of a trace as possible, using the hacked website or service just as a conduit between victims and external malicious infrastructure and hiding their presence from users. Attackers won't have to construct anything on the infected location itself. This is convenient for hackers since it makes assaults simpler to set up and more difficult to track.
Hackers use the following techniques in watering hole attacks:
-
Cross-site scripting (XSS): With this injection technique, a hacker can embed malicious scripts into a website's content to direct users to adversarial websites.
-
SQL Injection: Hackers may employ SQL injection attacks to steal information.
-
DNS Cache Poisoning: DNS cache poisoning, sometimes referred to as DNS spoofing, is a trick used by hackers to send targets to harmful websites.
-
Drive-by Downloads: In a bar, potential victims could unknowingly, voluntarily, or actively download dangerous material.
-
Malvertising: In order to spread malware to their target, hackers insert malicious code inside advertisements at a bar.
-
Zero-day Exploitations: Threat actors might take advantage of browser or website flaws to give hackers a place to refuel.
What are the risks associated with a watering hole attack for both individuals and organizations?
The data of an individual or a group is compromised as a result of watering hole attacks, and in certain situations, their privacy and security are seriously violated. It affects a person's and a group's sense of security and safety on a personal level. A watering hole attack poses a risk to community trust, just like spear phishing, another sort of targeted attack that accesses private data. An organization, network, community, or movement suffers when there is a perception that their gadgets have been infiltrated and their security has been violated.
Community members cease taking part in the platforms and news sites they require to carry out their job if they feel they can't trust them. Even if a genuine ally initiates the connection, they could be wary of new ties created on these sites. The breakdown of social movements is frequently attributed to paranoia and a lack of trust, to the point that law enforcement and governments incorporate this into their strategies and methods. If an activist can't trust their contacts and the digital venues they have access to, they could be less inclined to call for assistance when they need it.
Those who have been infiltrated additionally face dangers to their physical security due to the nature of the data that surveillance ware collects. Geographical locations of people, their daily plans, and travel information are just a few examples of the sensitive data that surveillance ware may access. These details are exploited for physical surveillance and/or physical attack on a person.
How can employees be trained to avoid falling victim to a watering hole attack?
Making sure all end users are aware of watering hole attacks and the fact that hackers infiltrate legal websites to carry out these assaults is a key first step. Users should be taught to see the telltale signals of fraudulent emails and to exercise caution when clicking any links, including those that appear to be coming from reputable sources.
Urge people to talk to their coworkers about any possible security risks that may arise. For instance, it can be a clue of a possible attack attempt if several members of the same team get a similar email that directs them to a specific website. Of course, the security team should be informed right away so they can take steps to stop an attack from happening or keep an eye out for indications of a current breach.
What role do social engineering and spear phishing play in watering hole attacks?
The relationship between social engineering and watering hole attacks is outlined below:
An attack known as a "watering hole" uses social engineering to target a particular set of end users by infecting websites they are known to frequent or by building new websites that would appeal to them. The intention is to either infect a victim's computer a
nd get access to the network at the victim's place of employment, or to steal login and password combinations in the hopes that the victim would reuse them. The term is derived from the wild predators that stalk about watering holes in search of possible food, waiting for an opening to strike.
In a Watering Hole attack, the "predator" (Attacker) plan looks for opportunities to infect weak targets with malware on certain websites that are popular with its "prey" (target). In other words, rather than luring victims with a spear phishing email campaign, hackers infiltrate susceptible websites that are relevant to their targets and then drive the victims to the attacker's website or application, which includes dangerous information like malware.
The relationship between spear phishing play and watering hole attacks is explained below:
Attacks at watering holes resemble spear phishing attempts. They both aim to accomplish the same thing: tricking a victim into doing something that will compromise their private information. This usually entails sending the target a personalized email or instant message asking them to open an attachment or click on a link in order to compromise their information in a spear phishing attack. There is no need to seduce the victim into compromising oneself in a watering hole assault scenario.
A targeted online assault tactic is a watering hole attack. The attacker chooses a target organization and either make an educated estimate or keeps track of the websites the organization's members regularly visit. The attacker then uses a zero-day vulnerability to infect one or more of these sites with malware. An organization member's device will eventually get infected, at which time the attacker has access to it and maybe the network of the organization. The objective of this attack is to steal key business systems and assets, as is the case with many, if not most, internet attacks, as well as intellectual property, financial information, and personal information. To increase their chances of success, the attacker will occasionally use both tactics (watering hole attack and spear phishing).
What are the Best Practices for Preventing Watering Hole Attacks?
You improve your organization's security and reduce risk by proactively addressing watering hole threats and giving preventative strategies a top priority. Start by training staff members on preventative techniques, such as avoiding the use of personal computers for business purposes and depending solely on secure internet connections, using anti-phishing tools. In order to spot any unusual behavior and quickly handle risks, continually monitor data and connections.
The following are the best methods to defend your business from watering hole attacks:
-
Training personnel through security awareness seminars to help them recognize suspicious activities more quickly. raising awareness of watering hole attacks.
-
Maintaining the most recent version of all software, including non-security applications. Regular vulnerability scans and security fixes are an essential first line of protection against watering hole attacks since they actively look for weaknesses.
-
Ensuring that all network traffic for the company is classified as suspect until it has been verified.
-
To defend your company against new malware threats, use endpoint detection and response (EDR) solutions.
-
Using secure web gateways (SWG) to impose acceptable usage guidelines and screen out web-based dangers. An SWG serves as a go-between for the user and the external website, filtering out dangerous network traffic and enabling secure browsing for personnel.
Best PracticeTo avoid data breaches and malware downloads as a result of social engineering attacks, such as watering hole attacks, you can easily install Zenarmor SWG Free Edition on your open-source firewall. It offers security against malware, botnets, phishing, and spam sites.
What is the relationship between watering hole attacks and supply chain attacks?
Watering hole attacks exploit the websites that users in a certain industry or user group frequently visit to entice them into a trap that gives them access to a company's corporate network. Watering hole attacks frequently result in data theft, financial loss, and reputational harm.
These dangers closely resemble supply chain assaults, but they are not the same thing. Hackers exploit a third-party service in both instances to infect additional computers. Nevertheless, whereas a watering hole attack hits unbiased websites, supply chain assaults often compromise a product that has been purchased or a service that is used by the target. In contrast, a supply chain attack spreads malware via the "weakest" network connection within a company, such as a partner, vendor, or supplier.