What is Command and Control (C&C or C2) in Cybersecurity?
The rise of targeted attacks done by adversaries with access to sophisticated tools, commonly referred to as Advanced Persistent Threats (APTs), is one of the top concerns in cyber security today. These assaults target particular organizations or persons and try to create a persistent and undetectable presence inside the infrastructure of the target. The objective of these assaults is often espionage, which involves the theft of valuable intellectual property and secret information. The key to achieving all of these objectives is a solid Command and Control Infrastructure. Command and control, commonly known as C2 or C&C, is one of the most destructive attacks.
The Command and Control Infrastructure is crucial to attackers, and a potential vulnerability for defenders. Blocking C&C communications or destroying the C&C infrastructure of an enemy stops a cyberattack in its tracks. C2 should never be the main emphasis of an organization's information security program, which should also include appropriate "cyber hygiene" practices, security awareness training for staff, and well-written rules and procedures. These measures significantly reduce the danger presented by command and control infrastructure.
Zenarmor NGFW is one of the most effective solutions to prevent C2 attacks. Zenarmor allows you to easily upgrade your open source firewall to a Next Generation Firewall in seconds. NG Firewalls empower you to combat modern-day cyber attacks that are becoming more sophisticated every day.
Some of the capabilities are layer-7 application/user aware blocking, granular filtering policies, commercial-grade web filtering utilizing cloud-delivered AI-based Threat Intelligence, parental controls, and the industry's best network analytics and reporting.
Zenarmor Free Edition is available at no cost for all OPNsense users.
In this article, will explain in detail what a command and control attack is, how it works, the methods used for C&C attacks by hackers, and what can be done to protect against it. We will also examine both open-source and commercial command and control frameworks for read-teaming purposes.
What is Command and Control (C&C) Attack?
Command and control attacks, also known as C2 and C&C attacks, are a form of cyber attack in which a cybercriminal uses a rogue server to deliver orders to computers compromised by malware via a network and to receive data stolen from the target network. The server of the attacker is commonly referred to as a Command and Control server, C&C server, or C2 server. This attack server leverages the constructed backdoor to perform a variety of malicious actions on the victim's PC, such as data exfiltration through DNS tunneling.
The command and control(C2 or C&C) server receives the necessary payload from the hacked network. The malware can identify and spread to more vulnerable hosts on the network, a process known as pivoting, given sufficient time. The entire system is swiftly placed under the control of an attacker if the initial compromised device automatically infects any other devices with which it connects. As additional systems are recruited, a botnet, a network of zombie systems, is formed. Then, these botnets get instructions to carry out more destructive operations, such as initiating Distributed Denial of Service(DDoS) attacks.
What is a C2 Server?
C2s (Command-and-Control servers) are tools utilized by threat actors to launch and coordinate cyber attacks by transmitting instructions to their malware as well as distributing malicious programs, malicious scripts, and more. In addition, cybercriminals use them to receive data seized from target servers, devices, websites, and forms. C2s are the technical brains behind the malicious operations of threat actors.
A C2 enables communication between the attacker and the target, whether for directing a botnet or transmitting stolen output to the end-user. The target could be a single device, hundreds within a single system, or millions.
Establishing and sustaining a C2 connection is a crucial step for threat actors. Without it, they could only perform half of their filthy work. Attackers must issue commands to exert control over the outcome.
Command and control servers often use trusted and seldom monitored traffic, such as DNS, to deliver instructions back to the infected host. Today, C&C servers often have a brief lifespan. They frequently reside in reputable cloud services and use automatic domain generation algorithms (DGAs) to make it harder for law enforcement and cyber threat hunters to discover them.
Today, there are four primary types of C2s in use:
- Centralized server under the attacker's physical control
- Bulletproof hosting
- Social networks
- Cloud services
In each of these environments, C2s typically exert control over botnets.
What is a Zombie?
A Zombie is a computer or other connected device infected with malware and capable of being remotely controlled by an adversary without the owner's knowledge or permission. While some viruses, trojans, and other undesirable applications undertake particular operations after infecting a device, the primary purpose of many varieties of malware is to provide access to the C2 infrastructure of the attacker. These "zombie" computers are then commandeered to do a variety of functions, from forwarding spam e-mail to participating in large-scale Distributed Denial-of-Service Attacks (DDoS).
What is a Botnet?
A botnet is a network of zombie computers used for a single illegal purpose. This might be anything from mining cryptocurrencies to launching a Distributed Denial of Service (DDoS) attack on a website. Typically, botnets are joined by shared C2 infrastructure. It is typical for hackers to offer other criminals access to botnets as a form of "attack as a service".
What is Beaconing?
Beaconing is the process of an infected device calling the C2 infrastructure of an attacker to check for instructions or more payloads, often at regular intervals. Some varieties of malware signal at random intervals or remain inactive for a length of time before calling home to escape detection.
What are the Targets of Command and Control Attacks?
According to Mandiant and Symantec, any key economic sector might be the target of a Command and Control (C2) attack. Also important is the fact that the size of an organization is not a predictor of whether or not it will be targeted: organizations of all sizes, from tiny companies to multinational corporations, have been attacked in the past. A command and control attack targets almost any computer system including:
-
Mobile devices, such as tablets, smartphones, and laptops
-
Desktops
-
IoT devices
Especially IoT devices are the main targets of the C2 attacks since these gadgets are often insecure. IoT devices are difficult to manage due to their relatively restricted user interfaces. They are not often updated frequently with security fixes. And they often exchange information over the Internet.
How Dangerous is Command and Control Attack?
Command and Control channels are a backdoor to the infected machine and/or network, and their destructive power is limited only by the imagination of the attacker. Some common types of attacks being executed using a Command and Control server are explained below:
-
Lateral Movement: Once an attacker has gained a foothold, they often move laterally across the business, utilizing their C2 channels to transmit information about additional hosts that are susceptible or improperly configured. The first infected system may not be a lucrative target, but it acts as a springboard to more vulnerable network areas. This procedure is performed several times until an attacker gets access to a high-value target, such as a domain controller or database server.
-
Service Interruption: Attackers may regularly restart an infected system or set of compromised computers inside an enterprise while a crucial job is in progress. For instance, a business migrates data or backs up its whole database of information and files to numerous external storage devices for redundancy. Or a manufacturing process involving the transformation of materials from one form to another, which may take many hours or days to complete. By continuously restarting the system(s) at scheduled intervals, attackers may prevent the work from ever being finished.
-
Multi-stage Attacks: Frequently, the most intricate cyberattacks consist of several different processes. Typically, the first infection is a "dropper" or downloader that communicates with the adversary's C2 infrastructure and downloads more malicious payloads. This modular design enables an adversary to conduct campaigns that are both broadly dispersed and highly targeted. The dropper may infect thousands of businesses, enabling the attacker to be selective and develop second-stage malware specifically for the most profitable targets. This paradigm also permits a decentralized cybercrime business. For instance, an initial access group may sell access to a prime target, such as a bank or hospital, to a ransomware ring.
-
Malware/Ransomware: Once an attacker compromises a system on your network, they have access to the whole system. Depending on the rights they obtained, they can initiate the download of malware or encrypt sensitive data. This may be used to demand a ransom before the data is disclosed or to damage the operations of an organization.
-
Shutdown Systems: In the event that a virus has traversed a section or all of an organization's systems, an attacker may simply shut down all of the systems to halt all corporate activities. The attacker might then threaten to halt company operations unless their demands are satisfied.
-
DDoS: Sometimes, compromised computers are utilized as foot soldiers to launch DDoS assaults against a separate organization or service. With sufficient compromised workstations on the network, the attacker has access to a botnet. DDoS attacks are a typical usage for botnets. An attacker in possession of a C2 server that delivers orders to a group of zombie systems may tell the infected systems to flood a server with repeated requests to deplete its capacity. This then results in the denial of access to the website or service to genuine users.
-
Data Theft: Data exfiltration is one of the most prevalent applications of a C2 channel. Confidential firm data, such as financial papers or trade secrets, might be stolen or sent to the command and control server. Using the built backdoor, attackers extract sensitive data recursively from an organization's system. This sensitive information might include bank records, trade secrets, private information that can be exploited for insider trading, or other high-value information that would generate a substantial profit on the dark web.
How Does Command and Control Attack Work?
To perform a command and control attack, the attacker infects a machine that may be protected by a firewall. Attackers must establish C&C connections in order to move laterally inside a network. Establishing a C&C connection is accomplished in many ways:
-
By malvertising
-
Through browser plugin security flaws.
-
Through a phishing email that convinces the recipient to visit a malicious website or open an attachment containing harmful malware.
-
By the installation of malicious software.
Once connectivity is established, the infected system sends a signal to the attacker's server in search of further instructions. The infected machine executes orders from the cybercriminal's C2 site and installs other malware. The attacker may now run any code on the victim's machine. Typically, the malicious malware spreads to more computers, forming a botnet - a network of compromised workstations. In this manner, an attacker with unauthorized access to a company's network may seize complete control of that network.
Command and Control attacks are executed by the procedures outlined below.
-
Reconnaissance: This is when the attacker gathers additional information about the target and discovers the vulnerabilities that will be exploited during the actual assault. The activity of reconnaissance includes both computer systems and people. Using classic techniques like port scanning and service enumeration, attackers check their target's networks and systems for vulnerabilities and misconfigurations that might give an entry point into the organization. In addition, attackers acquire information on important personnel in the targeted organization, for instance by scouring social networking platforms; this data will be utilized to help subsequent phases of the assault.
-
Initial compromise: This phase reflects the real intrusion, in which the attackers successfully access the network of the target. Most typically, spear phishing is the technique of compromise. A spear-phishing email may include a malicious attachment or a link to a malicious website. Typically, the content of spear phishing messages is customized depending on the information gathered during the reconnaissance phase, so that they look believable and authentic.
The strategic compromising of websites of interest to the target (or "watering hole" attack) is a second popular type of infiltration. In these assaults, attackers plant malicious code on websites that the intended target is likely to visit; when the victim visits the compromised website, he/she is exposed to one or more vulnerabilities. Watering hole attacks are an outgrowth of classic, opportunistic drive-by-download assaults, in which users are lured to a malicious web page by various ways. The web page includes code, generally written in JavaScript, that exploits browser or plugin vulnerabilities. If successful, the exploit installs malware onto the victim's computer, which then falls completely under the attacker's control.
-
Command & Control: In the Command and Control phase of an assault, attackers exploit the breach of a system. Specifically, hacked systems are compelled to create a communication channel via which they are directly controlled by the attacker. The C2 channel permits an attacker to establish a "hands-on-keyboard" presence on the infected system (via so-called remote access tools), install additional specialized malware modules, and perform additional malicious actions such as spreading to other machines or initiating a denial-of-service(DoS) attack.
-
Exfiltration: The attackers extract, gather, and encrypt information taken from the victim's environment during this phase. The information is then often provided to the attackers over the same C2 channel established previously.
Obviously, data exfiltration has also been a crucial stage in opportunistic attacks, and this has been widely reported. For instance, examinations of the data stolen (or "dropped") by the key loggers utilized by banking trojans have reported on the volume of data being sent, its estimated worth, and their operators' mode of operation.
Moreover, researchers have sinkholed or hijacked whole botnets in order to acquire an insider's perspective on the data taken from infected devices and the botmasters' activities. Regarding the exfiltration strategies seen in these conventional assaults, we anticipate that targeted malware will make more efforts to conceal its exfiltration activities and infrastructure.
What are the Command and Control Techniques Used By Hackers?
Command and Control include many tactics attackers use to connect with victim network systems under their control. To escape detection, adversaries often seek to imitate regular, anticipated communications. Several methods an adversary might use to establish command and control with varying degrees of stealth, depending on the structure and protections of the victim's network.
At the time of writing, the MITRE ATT&CK architecture enumerates 16 distinct command and control methods, each with some sub-techniques found in previous hacks. Command and control techniques defined by MITRE ATT&CK are explained below:
-
T1071 Application Layer Protocol: By blending in with current traffic, adversaries may communicate using application layer protocols to circumvent detection and network filtering. Commands to the distant system and often their results will be incorporated in the protocol flow between the client and server. Attackers use the following application layer protocols:
- HTTP(S)
- FTP/SFTP
- Mail Protocols
- DNS
-
T1092 Communication Through Removable Media: Using removable media to convey commands from system to system, an adversary may conduct command and control across hacked computers on possibly unconnected networks. Both systems would need to be hacked, with the possibility that an Internet-connected system would be compromised first, followed by a Replication Through Removable Media. The unconnected system would send commands and data to the Internet-connected system to which the enemy had direct access.
-
T1132 Data Encoding: The adversary may encrypt data to make it more difficult to discern the substance of command and control transmission. Information about command and control (C2) may be represented using a conventional data encoding technique. In addition to ASCII, Unicode, Base64, MIME, and other binary-to-text and character encoding systems, the usage of data encoding may conform to current protocol requirements. Some data encoding schemes, such as gzip, may also result in data compression. Attackers use standard encoding or non-standart encoding techniques.
-
T1001 Data Obfuscation: To make command and control communication more difficult to identify, adversaries may obscure it. Command and control communications are concealed (though not always encrypted) to make the information harder to find or understand, to make the transmission less noticeable, and to conceal directives. This involves a variety of techniques, including the addition of garbage data to protocol traffic, the use of steganography, and the impersonation of valid protocols. Attackers use the following data obfuscation techniques:
- Junk Data
- Steganography
- Protocol Impersonation
-
T1568 Dynamic Resolution: It is possible for adversaries to dynamically create links to command and control infrastructure to escape conventional detections and countermeasures. This may be accomplished by using malware with a shared algorithm with the infrastructure used by the adversary to receive the malware's messages. These computations may be used to dynamically alter factors such as the malware's command and control domain name, IP address, and port number. Attackers use the following dynamic resolution techniques:
- Fast Flux DNS
- Domain Generation Algorithms (DGAs)
- DNS Calculation
-
T1573 Encrypted Channel: Instead of relying on any inherent safeguards offered by a communication protocol, adversaries may apply a known encryption technique to disguise command and control communications. Even though these implementations use a safe technique, they may be susceptible to reverse engineering if secret keys are encoded and/or produced inside malware samples/configuration files. Attackers use symmetric cryptography or asymmetric cryptography techniques.
-
T1008 Fallback Channels: If the primary channel is hacked or unavailable, adversaries may utilize backup or other communication channels to retain command and control and evade data transfer limits.
-
T1105 Ingress Tool Transfer: An adversary may transfer tools or other files from an external system into a compromised environment. Tools or data may be sent from an external adversary-controlled machine to the victim network using the command and control channel or other protocols, such as FTP. Once present, attackers may transfer/spread tools across victim devices inside a hacked environment (i.e. Lateral Tool Transfer).
-
T1104 Multi-Stage Channels: Multiple phases of command and control may be deployed by adversaries under various situations or for specific purposes. Multiple stages may be used to disguise the command and control channel, making detection more challenging.
-
T1095 Non-Application Layer Protocol: Adversaries may use a non-application layer protocol for communication between the host and C2 server or between infected computers inside a network. The number of potential protocols is vast. Network layer protocols, such as Internet Control Message Protocol (ICMP), transport layer protocols, such as User Datagram Protocol (UDP), session layer protocols, such as Socket Secure (SOCKS), and redirected/tunneled protocols, such as Serial over LAN, are specific instances (SOL).
-
T1571 Non-Standard Port: Adversaries can communicate using a protocol and port pairing that is not commonly associated. For instance, HTTPS via port 8088 or port 587 instead than the standard port 443. An adversary may alter the standard port used by a protocol to circumvent filtering or confuse the analysis/parsing of network traffic.
-
T1572 Protocol Tunneling: Adversaries may tunnel network communications to and from a victim system using a distinct protocol to evade detection/network filtering and/or get access to otherwise inaccessible systems. Tunneling requires embedding a protocol explicitly inside another. This behavior may disguise harmful communication by mixing it with legitimate traffic and/or providing an additional layer of encryption (similar to a VPN). Tunneling might also permit the routing of network packets that would not reach their intended destination otherwise, such as SMB, RDP, and other traffic that would be censored by network appliances or not routed through the Internet.
-
T1090 Proxy: To prevent direct connections to their infrastructure, adversaries may employ a connection proxy to route network traffic between systems or to act as an intermediary for network communications to a command and control server. Many programs, like HTRAN, ZXProxy, and ZXPortMap, provide traffic redirection using proxies or port redirection. These sorts of proxies are used by adversaries to manage command and control communications, limit the number of simultaneous outbound network connections, offer connection failure resilience, and ride over existing trusted communications pathways between victims to escape suspicion. Multiple proxies may be chained together by adversaries to further conceal the source of harmful communications. Attackers use the following proxy techniques:
- Internal proxy
- External proxy
- Multihop proxy
- Domain Fronting
-
T1219 Remote Access Software: An attacker may use genuine desktop assistance and remote access software, such as Team Viewer, AnyDesk, AmmyyAdmin, Go2Assist, etc., to create a command and control channel to target devices inside networks. Commonly employed as authorized technical assistance software, these services may be permitted by application control in the target environment. The usage of remote access programs such as Ammyy, VNC, and Teamviewer is prevalent in comparison to the use of other lawful software by adversaries.
-
T1205 Traffic Signaling: Traffic signaling may be used by adversaries to conceal open ports or other malicious functionality used for persistence or command and control. Traffic signaling includes the use of a magic number or sequence that must be provided to a system in order to elicit a certain reaction, such as opening a closed port or performing a malicious job. This may include sending a sequence of packets with certain characteristics prior to opening a port that an adversary may exploit for command and control. This series of packets often consists of attempted connections to a specified sequence of closed ports (i.e. Port Knocking), but it may also include strange flags, special strings, and other distinctive properties. The host-based firewall or custom software might open a port after the completion of the sequence.
-
T1102 Web Service: A legal external Web service may be used by adversaries to transmit data to/from a compromised machine. Due to the possibility that hosts inside a network are already connecting with popular websites and social media platforms before a breach, using them as a C2 technique may provide a substantial degree of cover. Using ubiquitous services, such as those provided by Google or Twitter, makes it simpler for enemies to conceal themselves in anticipated background noise. Commonly, Web service providers use SSL/TLS encryption, affording opponents an additional layer of security. Attackers use the following web service techniques:
- Dead Drop Resolver
- Bidirectional Communication
- One-Way Communication
What are the Types of Command and Control Architectures?
In order to construct reliable and durable command and control infrastructures and to design covert communication mechanisms, attackers experiment with diverse methodologies. As a result, numerous C&C structures and communication approaches have evolved. For instance, attackers have used centralized designs based on IRC and HTTP protocols. Recently, they have implemented decentralized systems based on P2P protocols that are more difficult to shut down. Similarly, direct ways of communication have been replaced by encrypted channels, which make it difficult to retrieve an attacker's orders and stolen data. In order to make channel discovery and blockage more challenging, attackers often use covert communication techniques that imitate normal traffic patterns. C&C traffic may occur, for instance, through pages and photos on Online Social Networks (OSNs), covert DNS traffic, and anonymous communication networks such as Tor.
The common command and control architectures are explained below:
-
Random: This approach was created to guarantee that cybersecurity professionals cannot discover a botnet's chain of command or track and disable the C2 server. This is accomplished by transmitting directives from random sources to the infected host or botnet. These include links in social media comments, IRC chat rooms, Gmail, CDNs, and other leased platforms. The Twittor project seeks to create a fully working command and control platform utilizing just Twitter direct messages. A typical characteristic that attackers search for in these sources is that they are generally trusted and often used.
-
Centralized: This centralized paradigm closely resembles a client-server transaction mechanism. A compromised host polls its C2 server to receive instructions for actions to be carried out. It is common for attackers to host C2 servers using mainstream websites and hosting providers. This approach is often simple to discover and prevent since the instructions originate from a single source whose IP address can be easily found and banned. However, some attackers make detection more difficult by configuring their C2 servers with proxies, redirectors, and load balancers. Public cloud services and Content Delivery Networks (CDNs) are frequently utilized to host or conceal C2 activities. It is also typical for hackers to breach reputable websites and utilize them without the owner's knowledge to host command and control servers.
Typically, C2 activity is found rather quickly, and the domains and servers involved with a campaign are taken down within hours after their initial usage. To overcome this, contemporary malware is often encoded with a long number of C2 sites to contact. The more advanced assaults add additional obscuring layers. Malware has been seen retrieving a list of C2 servers using GPS coordinates included in Instagram photographs and Instagram comments.
-
Peer-to-Peer: This model is decentralized, with botnet members sending messages from one node to the next. This removes the requirement for a "central" or "primary" server, making it harder to identify. You are only able to take down one node at a time, even while detected. This approach is often used with the centralized model to create hybrid systems. In the hybrid architecture, P2P communication acts as a backup in the event that the central server goes out.
What are the Examples of Command and Control Attacks?
There are many case studies of Command and Control attacks. Some of the C2 attacks that affected high-profile organizations and had egregious impacts are listed below:
-
US Missile Systems: The Washington Post obtained the private version of a study produced by the Defense Science Board for the Pentagon in May 2013. The study stated that Chinese hackers hacked the plans for some modern US missile systems. According to the report, the broad theft targeted paperwork for many missile systems, combat aircraft, and vessels. While there are currently little specifics detailing how the actual penetration happened, it seems that the assaults specifically targeted significant military contractors engaged in the design and manufacturing of military hardware. This case study is a convincing illustration of assaults intended at stealing valuable intellectual property: Washington Post sources stated the stolen blueprints were the culmination of 15 years of research.
-
Bit9: Bit9 disclosed that it had been hacked in February 2013. Bit9 manufactures a whitelisting solution that defines the list of software that should be permitted to operate in a network; all other software is deemed harmful. As a result of the penetration, the attackers stole the private certificate used by Bit9 to sign its software releases. Additionally, the business disclosed that some customers had received malware digitally signed with the stolen certificate.
In this instance, the specifics of the infiltration remain unclear. Nonetheless, there are some intriguing features to this attack. First, the attackers hacked Bit9 intending to get the necessary capabilities to attack downstream targets protected by the company's products effectively. These are commonly referred to as "supply chain attacks" because they target a link in a chain that ultimately leads to the targeted organization.
-
The New York Times: In January 2013, The New York Times announced publicly that it had been the victim of four months of targeted attacks. The attacks were related to Chinese hackers and an ongoing inquiry at the publication that was strongly critical of the Chinese political elite. The hack was part of a broader offensive effort that targeted journalists and media businesses, including Bloomberg News, which was penetrated the year before. An investigation revealed that the attack activity exhibited characteristics typical of Chinese targeted attacks: attackers used compromised accounts at US universities to conceal their identity and complicate the investigation, and they were suspected of using spear phishing to gain initial access to the Times' network.
The subsequent phases of the assault disclose the targeted nature of the event in full: the attackers gained the passwords of all 53 Times workers and used them to access their personal computers. Then, they used code to hunt for and steal reporters' papers related to the ongoing probe of Chinese leaders.
The Times story provides two instructive examples of the limits of typical security measures predicated on the detection of first incursion activities. The paper states that the spear phishing attack fully circumvented perimeter defenses: "Attackers no longer target our firewall. They target certain persons." The Times also reported that, of the 45 malware samples used during the intrusion, only one was identified by the journal's anti-virus tool, whose vendor later issued the following statement: "We encourage customers to be very aggressive in deploying solutions that take a combined approach to security. The antivirus software by itself is insufficient."
-
Twitter: Twitter identified a sophisticated attack on its corporate network in February 2013. It was a C&Cl attack carried out by the hacking organization Wild Neutron or Morpho who would deploy the same technique against Facebook, Apple, and Microsoft in the coming weeks. The hack on Twitter compromised over 250,000 user accounts, giving the attackers access to user names and email addresses, among other information.
-
Facebook: A few weeks after the Twitter breach, a similar command and control attempt was launched against Facebook. However, maybe as a result of forethought after the Twitter breach, the assault did not disclose any consumer data, and the virus did not propagate over the network. A tiny number of Facebook engineers' computers possessed the information.
-
Apple: Similar to Facebook and Microsoft, Apple was attacked in February. According to Apple, the same organization successfully hacked a limited number of machines at their Cupertino headquarters at the time. A Java vulnerability was used to compromise the computers. Apple told Reuters that "there is no indication that any data departed Apple."
-
Microsoft: A few weeks after the Twitter hack, the same organization launched a similar attempt against Microsoft. The attackers were able to infiltrate Microsoft's database of unpatched vulnerabilities. The assault might have been catastrophic. Microsoft published a statement stating, "We have no indication that user data were compromised, and our investigation is continuing."
How to Detect and Prevent Command and Control Attacks?
Command and Control assaults are conducted silently to prevent the attacker from being stopped from carrying out their harmful operations and to prevent the organization from mitigating the damage. Therefore, it is essential to avoid malware assaults that use Command and Control servers rather than relying on damage control techniques. By severing the communications route to the command-and-control server and monitoring suspicious activity, a business can thwart even the most sophisticated malware.
Numerous strategies have been developed for the identification and interruption of C&C channels. Typically, they depend on automated monitoring and analysis of network data to detect signs of penetration, malicious activity, and atypical communication.
The significance of human participation in this endeavor cannot be emphasized.
As attackers continually alter their techniques, it is essential to get a comprehensive knowledge of traffic flow patterns, followed by frequent human tweaking of monitoring, detection, and response infrastructure.
Following is a list of methods that aid in recognizing and rejecting Command and control attacks inside your organization.
-
Filter and Scan All Traffic: This is the most crucial measure a company can take to avoid and identify Command and Control operations. Both incoming and outgoing traffic must be monitored in order to identify suspicious actions such as unlawful encryption of network communication (often employed in DNS tunneling operations), traffic to unfamiliar destinations, etc. Organizations should establish robust egress firewall rules such as restricting all outbound traffic except HTTP(S) traffic. This prevents automated beaconing on nonstandard ports and protocols, including dynamic DNS since modern malware communicates with command-and-control servers using web ports. Moreover, application control and web filtering technologies should be deployed. This should impair Tor and other encrypted avenues of communication.
-
Obtain Threat Intelligence: Organizations should ideally have access to current threat intelligence that gives information on known command-and-control IOCs. Cyber threat intelligence may be obtained from vendors as a service in the form of a raw data dump or as a data feed to an enterprise-level security solution. Establish a method for consuming the current data, since the information is continually evolving. Utilize prudence while picking a threat intelligence solution. The quality and timeliness of threat intelligence is the most important factor to examine when evaluating the efficacy of a security vendor's services.
-
Observe Beacons: Beacons are indicators of command and control activities inside your network, but they are generally difficult to detect. Most IDS/IPS systems identify beacons associated with commercial frameworks like Metasploit and Cobalt Strike, but attackers may readily modify these beacons to make detection far more difficult. In some circumstances, cyber threat hunting teams will manually review packet dumps using Wireshark or tcpdump.
-
Design Your Network Securely: Design and administer the network such that C&C activity is effectively blocked or severely hindered. Implement network segmentation to separate devices with varying levels of trust and risk (e.g., public-facing servers vs internal hosts that store sensitive data). You should implement rate-limit restrictions to decelerate traffic destined for disreputable or untrustworthy destinations. Lastly block undesirable or underutilized communications techniques that might be exploited to piggyback C&C activities, such as anonymization networks, P2P overlays, and social networks.
-
Continuously scan your system using antivirus software: Using battle-tested antivirus software, you may continuously scan your host computers to identify and eradicate malware activity. Using antivirus eliminates the malware used to communicate with C2 servers, hence closing the hidden channel.
-
Detect abnormal network behavior: Collect and analyze network data to discover behavior that deviates from the profile of regular, anticipated network traffic. Establish traffic baselines in order to define the "typical" network profile (normal communication patterns, data exchange volumes, etc.). This metric may be achieved by establishing baselines for various time intervals (e.g., hour, day), internal devices, and network services. You should compare the present network activity to the established baselines in order to find differences that might be indicative of C&C activity. Pay close attention to abnormalities such as periodic beaconing, an increase in the volume of communication exchanged, and strange network behavior. For instance, C&C activity that relies on fast-flux techniques can be detected by searching DNS data for patterns of rapidly changing associations between domain names and IP addresses; DGA-based C2 activity is revealed in DNS data by use-and-discard patterns of domain names; data exfiltration can be detected in Net-Flow data by unusually high volumes of data exchanges.
-
Develop a detection and response solution: The organization must be able to generate notifications for suspicious traffic or IOCs. Depending on the technology, this may be accomplished by configuring alerts in security information and event management platform or via the administrative interface of a tool. Develop a response that is available 24 hours a day, seven days a week, 365 days a year for systems and network administrators during off-hours. Also targeting companies on vacations and weekends are attackers.
-
Collect Logs: It is essential to collect log files from as many sources as possible while searching for indications of command and control communication. Frequently, a thorough investigation is required to separate C2 traffic from legal applications. Security analysts are required to search for anomalous patterns, inspect the payloads of ostensibly innocent HTTPS or DNS queries, and do further statistical analyses. The higher the quantity of data available to an analyst or threat hunter, the better. Remote logging and SIEM technologies may be used to assist with this process.
-
Correlate Information from Different Sources: The purpose of maintaining a command and control infrastructure is to execute a specified operation, such as accessing vital data or infecting other systems. Searching for C&C activity from both a data and network viewpoint enhances the probability of detecting well-hidden intrusions.
-
Isolate infected hosts from other hosts on the network: As soon as an infected computer is identified, it should be removed from the network to prevent it from infecting other hosts. This stops the infection from manipulating the network and seizing control of it.
-
Enforce a list of permitted programs that may be installed on the system: Your computer system should not permit the execution or installation of any program. By preventing the installation of apps from unknown sources, you prevent the installation of malware used to construct C2 channels.
-
Educate Users: Organizations should offer all workers security awareness training so that they understand what a Command and Control attack is and how it might be executed. Security awareness training reduces the likelihood of an adversary hacking a system. By providing your personnel with the proper training, you reduce the likelihood of a C&C attack.
-
Implement Access Control: Limiting user rights is an effective way to defend against Command and Control attacks. Assign your staff just the permissions necessary for them to do their duties. Additionally, implement two-factor authentication (2FA) on the accounts of all your workers. Two-factor authentication provides an extra degree of protection. Therefore, it is an excellent method for safeguarding user credentials.
How to Prevent Command and Control Attacks on Open Source Firewalls?
You will have effective protection against command and control attacks by installing Zenarmor NGFW on your open-source firewall. Zenarmor is compatible with major BSD-based open-source firewalls such as OPNsense and pfSense software and the most widely used Linux distributions like RHEL, Ubuntu, Debian, CentOS, and Alma Linux.
Zenarmor provides AI-based cloud threat intelligence to stop zero-day malware and phishing attacks in real time. It detects and blocks new Botnets in an instant. It offers deep content inspection to prevent evasive threats that otherwise would bypass IP, port, and DNS-based filtering.
You can easily prevent command and control attacks on your open source firewall powered with Zenarmor NGFW by following the steps given below.
-
Login Zenconsole, Sunny Valley Networks Cloud Management Portal.
-
Launch Zenconsole by navigating to Firewalls > My Firewalls.
-
Select your firewall.
-
Navigate Policies > Default > Security
-
Block Botnet C&C option under the Advanced Security.
-
Synchronize the Policy.
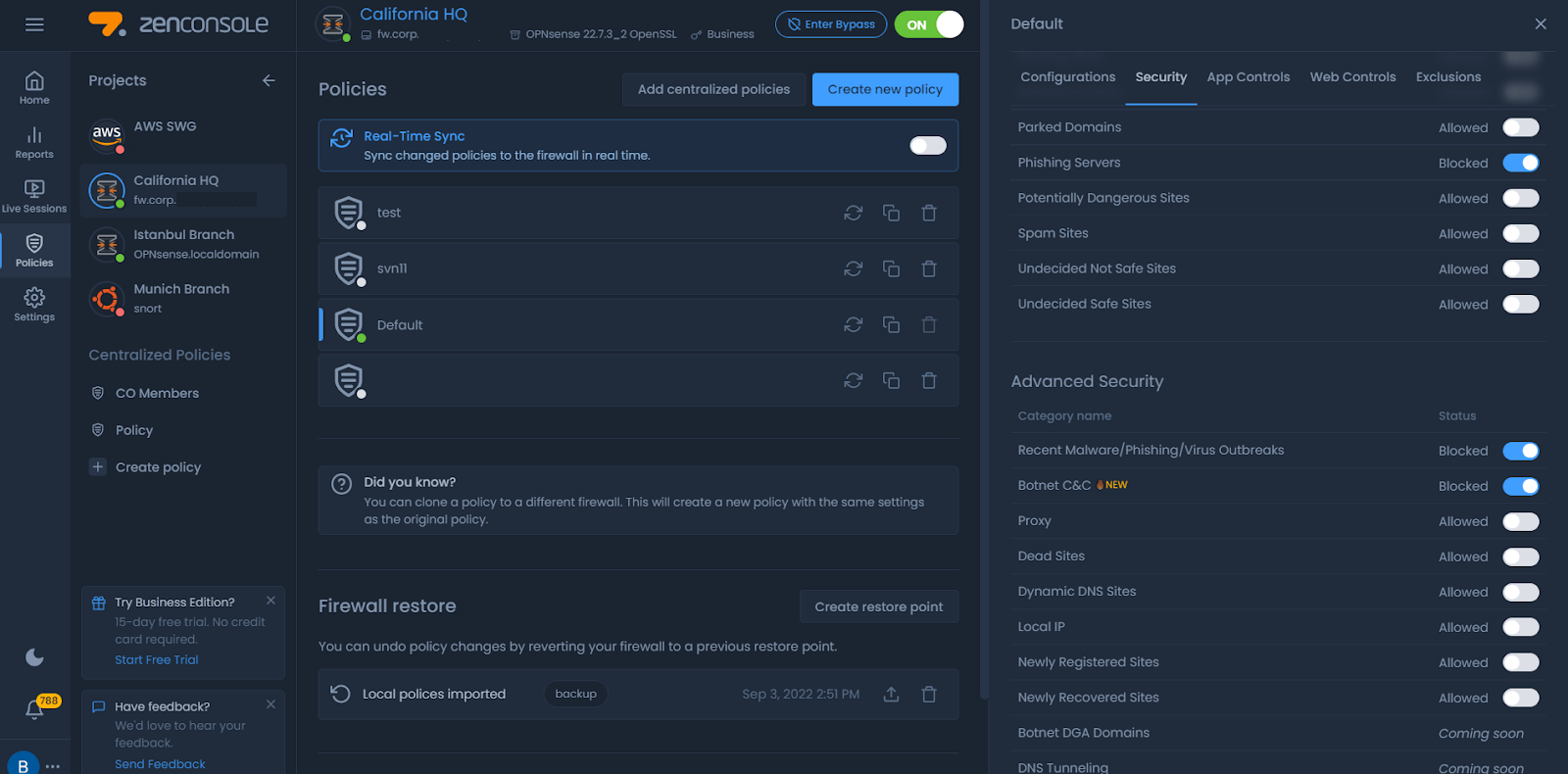
Figure 1. Preventing C2 attacks on open source firewall with Zenarmor
What are C2 Frameworks?
During Red Teaming battles, command and control post-exploitation structures are vital. After the first step of exploiting a vulnerability or a user to obtain access to a system, they provide a more elegant method for privilege escalation, pivoting, and lateral movement.
There are both free and commercial frameworks; they vary in a number of ways, but the most significant is that premium frameworks are less likely to be identified by antivirus software. This does not imply that the free ones are terrible, but because they are open-source, it is simple to create signatures.
What are the Open Source C2 Frameworks?
Some of the open-source C2 frameworks are as follows:
-
Sliver: Sliver is an open-source, cross-platform adversary emulation/red team framework that is used by businesses of all sizes for security testing. Implants from Sliver are dynamically constructed with per-binary asymmetric encryption keys and enable C2 over Mutual TLS (mTLS), WireGuard, HTTP(S), and DNS. The server and client are compatible with MacOS, Microsoft Windows, and Linux. Implants are supported on MacOS, Windows, and Linux.
-
AsyncRAT: AsyncRAT C2 Framework is a Remote Access Trojan (RAT) intended to remotely monitor and manipulate other computers over an encrypted secure connection. Among its features are keylogging, audio/video recording, information theft, remote desktop control, password recovery, launching a remote shell, a camera, and injecting payloads. Spam/phishing email and spear-phishing are the infection vectors used by AsyncRAT. Various malware campaigns and threat actors have used AsyncRAT in recent vulnerabilities. As part of Operation Layover, which targeted the aviation sector, TA2541 exploited infected Word documents with aviation, transportation, and travel-related themes to facilitate the download of the AsyncRAT payload. More recently, a campaign using principles of social engineering targeted Thai pass buyers. Ultimately, the Follina Outbreak in Australia delivered the malware payload AsyncRAT.
-
Sillenttrinity: Sillenttrinity is a multi-server, asynchronous command and control system written in Python3 with.NET DLR. This platform utilizes embedded third-party.NET scripting languages and dynamically calls.NET APIs; the method is referred to as BYOI (Bring Your Own Interpreter). This solution employs a dedicated team server with several contemporary features integrated into a robust C2 architecture. The use of WebSockets enables efficient real-time communication between the team server and agents placed on the workstations of victims. To encrypt all C2 communication between the team server and its implant, SILENTTRINITY employs Ephemeral Elliptic Curve Diffie-Hellman Key Exchange. One of the most valued aspects is its modularity, which allows users to simply alter any module.
-
Koadic: Koadic, sometimes known as COM Command & Control, is a post-exploitation rootkit for Microsoft Windows comparable to Meterpreter and Powershell Empire. Koadic performs the majority of its activities using Windows Script Host (a.k.a. JScript/VBScript), with compatibility in the core to support a default installation of Windows 2000 without service packs (and maybe even versions of NT4) up to Windows 10. It is feasible to serve payloads entirely in memory from stage 0 and beyond, and to leverage cryptographically secure SSL and TLS interactions (depending on what the victim OS has enabled). This framework is developed in Python, and its payloads are encrypted using XOR using JavaScript. The agents are installed using the default mshta or the default mshta or Microsoft HTML Application stagers on the target computers.
-
Covenant: Covenant is a .NET command and control framework that attempts to emphasize the attack surface of.NET, simplify the usage of offensive.NET tradecraft, and provide a collaborative command and control platform for red teamers. Covenant is a cross-platform, ASP.NET Core application with a web-based interface that enables multi-user cooperation. It supports Windows, macOS, and Linux-based operating systems. Additionally, Covenant offers a preconfigured Docker image to assist its installation. The agent of the Covenant known as "Grunt" is designed in C# and may be directly configured via the C2 web interface. There are several features available, such as lateral movement tactics, Mimikatz, exfiltration scripts, etc.
-
C3: C3 (Custom Command and Control) is a tool that enables Red Teams to swiftly create and use specialized command and control channels (C2). It is a framework that extends existing red team tools, such as the commercial Cobalt Strike (CS) product through ExternalC2, which is now supported. It enables the Red Team to focus just on the C2 they want to develop, trusting in the robustness of C3 and the CS tools to handle the rest. This efficiency and dependability enable Red Teams to function securely in mission-critical client settings (by ensuring a professional level of stability and security) while allowing for the safe testing and quick deployment of bespoke Tactics, Techniques, and Procedures (TTPs). Consequently, Red Teams are enabled to imitate and replicate an adaptable real-world adversary.
-
Caldera: Caldera is a cybersecurity technology meant to facilitate the automation of adversary emulation, help manual red teams, and automate incident response. It is based on the MITRE ATT&CKT architecture and is an ongoing MITRE research project. The framework is comprised of two elements:
- The core system. This repository's contents constitute the framework's code. A command-and-control (C2) server with a REST API and a web interface is included.
- Plugins. These repositories enhance the capabilities of the core framework and provide extra functionality. Examples include agents, reporting, and TTP collecting, among others.
-
Metasploit: Metasploit framework is a popular tool that is available with the Kali Linux distribution that may be used to identify vulnerabilities in networks and servers. As an open-source tool, it may be modified by operators and used with a variety of operating systems, such as Android, iOS, macOS, Linux, Windows, Solaris, etc. Meterpreter is loaded with several capabilities, such as staged and non-staged payloads to facilitate port forwarding across networks.
-
Merlin: Merlin is a cross-platform HTTP/2 Command & Control server and agent built in the go programming language. Merlin is a C2 that uses HTTP/1.1, HTTP/2, and HTTP/3 to avoid detection and interact with its agents. Merlin is a cross-platform application built in Go that is compatible with several operating systems. Each merlin compilation yields unique payloads capable of evading AV detection from the detection perspective. It employs a client-server architecture and offers the most sophisticated red teaming capabilities of any C2 framework on the market. As it is an open-source project, administrators may modify Merling agents' mode of operation and memory loading.
-
Faction C2: Faction is a C2 framework for security experts that enables simple agent extension and interaction. It focuses on delivering a simple, reliable, and accessible communications infrastructure for C2 using well-documented REST and Socket.IO APIs. Instead of a single massive monolithic application, Faction is loosely based on a micro services architecture. Functionality is partitioned into distinct services that interact through message queues. This strategy has various benefits, the most significant of which is that it allows users to rapidly grasp how the system works.
-
Empire 4: Empire 4 is a post-exploitation framework that contains C# agents, Python 3.x Linux/OS X agents, and pure PowerShell Windows agents. The old PowerShell Empire and Python EmPyre projects have been merged. The framework provides communications that are cryptographically secure with a customizable design. On the PowerShell side, Empire provides the ability to launch PowerShell agents without powershell.exe, fast deployable post-exploitation modules ranging from key loggers to Mimikatz, and flexible communications to elude network detection, all within a framework geared towards usability.
-
Ninja: Ninja C2 is an open source C2 server created by Purple Team to perform stealthy computer and Active directory enumeration without being detected by SIEM and AVs. Ninja is still in beta, but when the stable version is released, it will contain many more stealthy techniques and anti-forensic to make it a real challenge for the blue team to ensure that all defenses are configured correctly and they can detect sophisticated attacks. Python is used by Ninja to provide payloads and control agents. The agents are built on C# and PowerShell and can circumvent top antivirus software. Ninja communicates with agents using a secure, AES-256-encrypted channel; the key is not hard-coded, but rather randomly generated at the start of the campaign; every agent that connects to the C2 receives the key; and if the C2 is restarted, all existing and new agents will use a new key. Ninja also uses randomized callback URLs for each campaign to circumvent static detection.
-
ibombshell: ibombshell is a Powershell-based program that provides a prompt with post-exploitation capabilities at any moment (and in some cases exploitation). It is a shell that is downloaded straight into memory and provides access to a multitude of penetration testing options. These features may be downloaded straight into memory as Powershell functions. This method of execution is referred to everywhere. In addition, ibombshell supports a second execution option called Silently, allowing the penetration tester to run an instance of ibombshell without being detected (called warrior). The infected machine will establish an HTTP connection to a C2 panel. Thus, it will be feasible to control the warrior and put helpful routines into memory for the pentester. This occurs during the post-exploitation period.
-
MacShellSwift: MacShellSwift is a proof-of-concept post-exploitation tool for macOS written in Swift and using encrypted sockets.
What are the Commercial C2 Frameworks?
Some of the commercial C2 frameworks available in the market are listed below:
-
Cobalt Strike: Cobalt Strike was established by Raphael Mudge in 2012 to allow threat-representative security testing. Cobalt Strike was one of the first public command and control systems for red teams. HelpSystems purchased Cobalt Strike in 2020 in order to expand its Core Security product and complement Core Impact. Cobaltstrike is one of the most often used platforms for deploying a beacon agent on the victim's computer. This kind of agent offers a wide range of capabilities, including keylogging, file upload and download, socks proxy, VPN deployment, privilege escalation methods, mimikatz, port scanning, and the most sophisticated lateral movements. The Cobalstrike beacon employs a fileless method using a stageless or multistage shellcode, which is often loaded by exploiting a vulnerability or a flaw and executes the final payload in memory without touching the disk. It supports HTTP, HTTPS, DNS, and SMB connections to C2. In addition, Cobalstrike offers Artifact Kit, a developer toolkit that supports bespoke shellcode loaders.
-
Brute Ratel: Brute Ratel is a powerful Red Team & Adversary Simulation Software currently available on the C2 Market. It may also give a systematic chronology and graph for each of the conducted assaults to assist the Security Operations Team in validating and enhancing the internal defensive systems. Brute Ratel is pre-built with a number of opsOpec features that allow a Red Team to concentrate more on the analytical aspect of an engagement, rather than relying on open source tools for post-exploitation. Brute Ratel is a post-exploitation C2, however it does not include exploit creation or vulnerability detection tools like Metasploit, Nessus, Acunetix, or BurpSuite.
-
INNUENDO: INNUENDO is a complex post-compromise implant architecture that simulates sophisticated data exfiltration attacks. INNUENDO may function in a variety of ways on your network. It simulates a broad range of exfiltration strategies and covert networking techniques in order to evaluate whether your intrusion detection system is functioning properly.
-
Scythe/ Purple Team Exercise Framework: A Purple Team Exercise is a comprehensive evaluation of information security in which participants cooperate to attack, detect, and react. Attendees are exposed, explained, and shown live attack activity, while defenders demonstrate how to identify and react. Purple Team Activities are "hands-on keyboard" exercises in which participants test, assess, and improve people, processes, and technology in real-time while engaging in an open conversation about each assault tactic and defensive expectation. Purple Team Exercises are Cyber Threat Intelligence-led simulations of Tactics, Techniques, and Procedures (TTPs) designed to discover and correct security posture deficiencies inside a business.
-
Voodoo: Voodoo is a framework for covert, interactive cyber operations that provides offensive operations with a force multiplier.
-
Nighthawk: Nighthawk is one of the most sophisticated and evasive command-and-control frameworks. Nighthawk is designed for legal red team activities and empowers red teams. Nighthawk is a highly flexible implant intended to defeat and avoid the contemporary security mechanisms often seen in mature, closely monitored workplaces.
-
OST Stage 1: Outflank Security Tooling (OST) is a comprehensive collection of tools developed by Outflank's red teaming professionals. With OST, they package their internal technologies and make them accessible as a service to other providers of high-end offensive security services, such as red teaming, adversary simulation, and sophisticated penetration testing. These tools enable you to imitate approaches comparable to those used by APTs and Organized Crime Groups but are not publicly accessible. In addition, they enable all of your team members to accomplish deep-technical and challenging jobs without difficulty, at a guaranteed level, and while maintaining OPSEC security. OST tools are designed to circumvent protective measures and detecting technologies.
