Smishing Meaning: Scams and Attacks
As mobile device usage increases, so does cybercrime targeting mobile devices. In addition to being the most popular usage of cellphones, texting poses a particularly pernicious security risk for a few additional reasons.
Any number on the globe may send text messages to the majority of the 3.5 billion cellphones in use globally. Many consumers are aware of the risks associated with opening links in emails. Fewer individuals are conscious of the dangers of clicking links in text messages, though. Smishing is frequently profitable for attackers who are phishing for passwords, financial information, and private data, since users are far more trusting of text messages.
One type of cybercrime that is becoming more and more common is smishing. Smishing has increased due to several variables. For starters, the hackers that carry out these attacks, sometimes referred to as "smishers", are aware that victims are more likely to click on text messages than links. Meanwhile, other types of phishing, such as emails and phone calls, have had a tougher time reaching their targets due to improvements in spam filters.
Under the following topics, we shall give a broad overview of smishing in this article:
- What is Smishing?
- How does Smishing Work?
- What does Smishing Mean in Cybersecurity?
- What is the Difference Between Phishing and Smishing?
- How do Smishing Attacks Exploit SMS Messages?
- What are Examples of Smishing Scams?
- How does Social Engineering Play a Role in Smishing Attacks?
- What are the Most Common Tactics Used in Smishing Text Messages?
- Why are Smishing Attacks Particularly Effective Against Mobile Users?
- What are the Risks of Falling Victim to a Smishing Scam?
- How can You Protect Yourself Against Smishing Attacks?
- What are the Key Indicators of a Smishing Attack?
- How can I Report a Suspected Smishing Attack?
- What are the Legal Consequences of Falling Victim to a Smishing Attack?
- How can I Improve My Mobile Security to Avoid Smishing?
- What are the Psychological Tactics Used in Smishing Attacks?
What is Smishing?
Smishing, also known as SMS (Short Message Service) phishing, is a type of phishing attack using mobile text messages. The phrase combines the words "SMS" with "phishing." When hackers "phish," they send phony emails with the intention of fooling the receiver into clicking on a hyperlink that is harmful. Smishing merely substitutes text messages for email.
This type of phishing involves tricking victims into providing private information to a disguised attacker. Fraud websites or viruses might help in SMS phishing. Mobile text messaging platforms may include data-based mobile messaging applications and other non-SMS channels.
Smishing is further defined as a form of social engineering assault that depends more on taking advantage of human trust than on technological exploitation.
In order to trick you into clicking or contacting, a typical smishing scam message may appear to be from a bank, maybe your bank, and contain a link or phone number. If you click or contact, you run a significant risk of becoming a victim. The con artists then go to work, altering your personal data so they may sell it or utilize it in other frauds. Additionally, smishers could attempt to trick you into installing malware on your device.
Why Smishing is Important?
Smishing schemes are harmful to both individuals and businesses. When this happens to a company, the brand suffers, there are compliance difficulties, and customers begin to doubt your security. On the other hand, many people are aware of the perils of email phishing, but fewer are aware of the emergence of SMiShing, phishing's deadly and enticing relative.
SMiShing is a term used to describe fraudulent messages delivered over text messaging rather than email. This is generally in the form of a message that instructs the receiver to click on a link. When they do, malware is placed on their device, allowing the attacker to steal sensitive information like their Social Security or credit card details.
Smishing is nothing more than the same type of effort that attackers will employ in phishing expeditions directed at individuals on mobile devices through SMS, but there are a handful of practical ramifications that make smishing risky, if not more harmful.
People are particularly vulnerable to smishing because of their lack of awareness; they aren't aware that fraudsters may have their mobile number, and there is a propensity to already assume the messages they're getting are approved.
Another reason for being trapped in a smishing scam is the size of your mobile device's screen, which is quite large. There are techniques to assess the veracity of an email phishing message, such as lingering over hyperlinks before clicking them to discover the real destination. This is not available with URLs received over SMS, since the lower screen size hides or misses certain information that may be a signal that [a link] is dangerous.
The final reason is that it is more convenient. Messages, unlike emails, find their way into people's daily lives. Text messages, are an "interruption" in people's hectic lives, causing them to halt and pay instant attention to them. Because of this propensity, consumers are more likely to click potentially fraudulent links from unknown senders in smishing messages because they are urgent and panic-inducing.
How Does Smishing Work?
Malware is frequently avoided by using basic iOS and Android security measures. However, no security measure can stop users from voluntarily sending their data to an unknown number, even with strong security measures on mobile operating systems.
When combined with smishing, social engineering creates a potent attack. Before sending a text message, the attacker may phone the user and request confidential information. The attacker then utilizes the disclosed information in their text message attack. Several telecom companies have attempted to combat social engineering calls by alerting users to "Spam Risk" when they receive a call from a recognized scam number.
The smisher could address you personally by using your name and location. The message is strengthened by these specifics. A link to a server under the control of the attacker is then shown in the message. The link could take users to malware intended to compromise the phone itself or a credential phishing website. The virus is then used by the smisher to secretly transmit private information to a server under the control of the attacker or to eavesdrop on the user's smartphone data.
Email phishing is how most smishing attacks operate. To trick victims, these attacks combine psychological tricks with technology manipulation. The following steps outline the overall smishing attack procedure.
- Selecting Targets: Cybercriminals pick their victims. This selection can be more targeted, focusing on specific people based on information sold on the dark web or data gathered from prior breaches, or it might be random, utilizing a large list of phone numbers.
- Message Crafting: The attackers craft a misleading SMS message that elicits a certain response or feeling, such as urgency, fear, or curiosity. A call to action, such as clicking a link or dialing a number, is usually included in this message.
- Message Delivery: The attacker distributes the smishing message to their chosen targets via SMS gateways, spoofing tools, or compromised smartphones.
- Interaction: The victim is prompted to act after getting the message. This might include phoning a designated phone number, responding with personal information, or clicking on a link that has been supplied.
- Data Collection or Malware Deployment: If the victim responds as the attacker intends, a number of things might happen. They may enter money or personal information on a bogus website. Or they can inadvertently infect their gadget with harmful software. They might be tricked into giving information orally or face prosecution if they phone a number.
- Use of Stolen Information: Once the attacker has the information they want, they may use it for a number of nefarious activities, including identity theft, unauthorized transactions, black market data sales, and more focused attacks.
- Evasion: Attackers usually switch up their strategies, use multiple phone numbers, and utilize a variety of methods to conceal their identity and location in order to carry on their activities unnoticed. Smishers deceive users into sending sensitive information in a number of ways. To trick the target into believing the communication is from a reliable source, they could, for instance, utilize publicly available web resources to obtain basic information about the target, including name and address.
What does Smishing Mean in Cybersecurity?
A social engineering technique known as "smishing" employs phony mobile text messages to fool victims into installing malicious software, disclosing private information, or giving money to online criminals. Cybercriminals use smishing attacks to trick victims into divulging financial or personal information, clicking on nefarious links, or downloading dangerous software or apps. Similar to email-based phishing attacks, these fraudulent communications frequently seem to be from reliable sources and employ social engineering techniques to incite fear, curiosity, or a feeling of urgency in order to trick the receiver into doing something they don't want to.
These cybercriminals are essentially trying to obtain your personal information so they may use it to perpetrate fraud or other online crimes.
Smishing SMS messages frequently solicit personal or financial information, including your account or ATM number, and pose as correspondence from your bank. Giving burglars the information is the same as giving them the keys to your bank account.
Smishers frequently assume the identity of someone you know or have permission to seek private information from, such as government employees, tech support agents, banks, or other financial institutions. Cybercriminals typically employ one of two techniques to steal this data:
- Malware: You may be duped by the smishing URL link into downloading harmful software, or malware, which would then install itself on your phone. In order to fool you into entering private information and transferring it to the crooks, this SMS virus may pose as trustworthy software.
- Malicious website: The smishing message's link may take you to a phony website that asks for private information. To make it simpler to steal your information, cybercriminals create rogue websites that seem like legitimate ones.
How do Smishing Attacks Exploit SMS Messages?
Cybercriminals use smishing attacks to trick victims into divulging financial or personal information, clicking on nefarious links, or downloading dangerous software or apps. Similar to email-based phishing attacks, these fraudulent communications frequently seem to be from reliable sources and employ social engineering techniques to incite fear, curiosity, or a feeling of urgency in order to trick the receiver into doing something they don't want to. Smishing attacks exploit SMS messages by applying the following methods.
- An SMS message is the first step in a smishing attack. Attackers craft communications that seem to originate from reliable sources. These communications frequently instill a feeling of urgency and are typically intended to take advantage of trust. For instance, "Your account is locked." To unlock it, click this link.
- Attackers usually include a harmful link in their SMS messages or request personal information from the victim. Usually, when you click on the link, a phony website imitating a genuine service appears. Sensitive information is requested from victims, including financial details, two-factor authentication codes, and login credentials.
- To deceive targets, social engineering techniques are employed. Social engineering tactics are a major component of smishing. Psychological manipulation is used by attackers to coerce victims into acting immediately. One is less inclined to examine the dubious message the faster they take action. Messages frequently avoid the usual precautionary measures by invoking fear or haste. For instance: "Your account will be suspended if you do nothing within the next 24 hours."
- Mobile devices can be infected with malware, which allows hackers to take over the device and access private information like company emails. Targets might potentially become the target of sensitive data breaches, network intrusion, or intellectual property theft.
What is the Difference Between Phishing and Smishing?
Cyberattacks that utilize social engineering to deceive victims into paying money, divulging private information, or installing malware are collectively referred to as phishing. One of the most prevalent types of fraud is phishing, in which con artists use an email address that looks authentic but really contains a link that asks for personal information, such as your credit card number, social security number, and complete name.
Hackers can employ a variety of phishing techniques on their targets, including vishing and smishing. Smishing is the practice of contacting unwary people via text messages or popular chat applications like Slack. Typically, the messages include a link or website URL where scammers would request your financial and personal information.
The media utilized to execute the assaults is the primary distinction between the various phishing attack types. Hackers use text messages, or SMS, to target their victims in smishing attacks. Smishing attacks take advantage of the immediacy and ubiquity of mobile devices and text messaging. Phishing attacks mostly take place via phony websites or emails.
In order to fool readers into taking action, scammers typically craft extremely complex emails with rich text formatting, official-looking branding, and top-notch images. Because consumers get so many emails every day, phishing efforts can easily blend in because scammers take advantage of the belief that compelling communications are seldom questioned.
The attack vector for smishing, on the other hand, is text messages sent through Facebook Messenger, WhatsApp, Telegram, SMS, and other instant messaging platforms. Smishing attacks use brief, attention-grabbing text nibbles to persuade the target to click on a malicious link or divulge private information without giving it much consideration, since text messages seem more immediate and intimate than emails.
Knowing the distinctions between phishing and smishing is essential for awareness and defense against a variety of online dangers. Each phrase describes dishonest methods used by cybercriminals to fool people into disclosing private information. However, the attack is carried out in different ways and through different channels in each strategy.
| Criteria | Smishing | Phishing |
|---|---|---|
| Moderate | Text communications or SMS (Short Message Service). | Mostly emails, but social media and rogue websites may also be included. |
| Approach | Cybercriminals send misleading text messages in an effort to trick victims into installing dangerous software, clicking on nefarious links, or disclosing personal or financial information. | Hackers create phony emails that seem like they are from reliable sources. These emails are intended to deceive recipients into divulging private information, including credit card numbers or login passwords, and frequently include harmful links or files. |
| Example | A text message asking the receiver to visit a link to confirm their account and warning them of questionable bank activity. | A phony login page that seems to be from a well-known e-commerce website and requests that customers change their passwords because of a security breach. |
Table 1. Smishing vs. Phishing
What are the Examples of Smishing Scams?
The majority of smishing attack types, like other social engineering techniques, rely on pretexting, which is the use of false narratives to influence victims' emotions and fool them into complying with a scammer's instructions. The following are typical instances of smishing attacks.
- Scams involving account verification: A text message purporting to be from a respectable business or service provider, such as a bank or shipping firm, is sent to the victim in this kind of attack. Usually, the notification asks users to confirm their account information or alerts them to illicit behavior. Users' credentials may be taken when they click on the given link, which takes them to a phony login page.
- Bank Fraud Alerts: These alerts, which seem to be from the victim's bank, warn of suspicious activity or unlawful transactions. The user is then asked to phone a number that is under the attacker's control or click on a website to confirm their transactions.
- Lottery or Prize Scams: In these scams, the perpetrator tells the victims they have won a prize, a lottery, or a sweepstakes. They have to click on a malicious link, pay a tiny fee, or disclose personal information in order to get their prize. Either money or sensitive information theft is the aim.
- Scammers may impersonate the IRS, police, or other government agencies: The victim is frequently told in these smishing SMS that they must act to obtain a government benefit or that they owe a fee.
- Service Cancellation: The attacker notifies the victim that a subscription or service (such as a software or streaming service) is about to be terminated because of a payment problem. To "fix" the problem, they are encouraged to click on a link, which typically takes them to a phishing page.
- Tech Support Scams: Consumers are notified that there is an issue with their account or equipment and are asked to call a tech support number. Charges may result from calling this number, or the "technician" may ask for remote access to the device, which might result in data theft.
- Acting as if you are customer service: Attackers impersonate customer care representatives from reputable companies and merchants, such as Microsoft, Amazon, or even the victim's cellular service provider. They often say that there is an unclaimed award or reimbursement, or that the victim's account is faulty. These SMS messages usually direct the victim to a fraudulent website where their banking or credit card details are stolen.
- Acting like a shipper: These smishing communications purport to be from the US Postal Service, FedEx, UPS, or another shipping organization. They inform the victim that a parcel delivery issue occurred and request that they either pay a "package delivery fee" or log into their account to fix the problem. The fraudsters then flee after stealing the funds or account details. Around the holidays, when a lot of people are waiting for deliveries, these frauds are prevalent.
- Posing as a manager or coworker: Similar to business email compromise, business text compromise involves hackers posing as a supervisor, coworker, or colleague; a vendor or lawyer; or an attorney in need of assistance with an urgent need. These scams frequently ask for quick action and conclude with the victim paying the hackers money.
- Downloading malicious apps: Users get a message advertising a fun or helpful program. Malicious software is installed on the user's device when they click on the download link.
Real World Smishing Attacks
Some real-world smishing attack examples are given below.
-
Apple iPhone 12 Early Access Scam- Order Confirmation & Gift Smishing: A smishing attempt appeared in September 2020, luring individuals into supplying credit card information in exchange for a free iPhone 12. The strategy is based on the order confirmation premise, in which a text message says that a product delivery was delivered to the wrong address. The in-text URL link redirects victims to a phishing site impersonating an Apple chatbot. The gadget walks the victim through the steps of claiming their free iPhone 12 as part of an early access trial program, but it will eventually ask for credit card information to cover a tiny shipping price.
-
Scams using the USPS and FedEx - Order Confirmation and Gift Smishing: Reports of a fake USPS and FedEx package delivery SMS scam started spreading in September 2020. This smishing attack might try to steal your credit card information or your account credentials for multiple services. The communications began with a claim of missing or wrong package delivery, followed by a link to a website phishing tool masquerading as a FedEx or USPS giveaway survey. While the motive behind these phishing sites varies, several have been recognized as seeking to collect account logins for services such as Google.
-
COVID-19 Smishing - Mandatory Online COVID-19 Test Scam: The Better Business Bureau reported an increase in instances of U.S. government impersonators sending text messages requesting that individuals take a necessary COVID-19 test via a connected website in April 2020. Because there is no online test for COVID-19, many people have immediately recognized this hoax. The concept of these smishing attacks, on the other hand, may readily develop, as playing on public concerns of a pandemic is a successful means of victimizing the public.
How does Social Engineering Play a Role in Smishing Attacks?
Social engineering is an attack vector that primarily depends on human interaction. It frequently entails psychologically coercing people into violating standard security protocols and best practices in order to obtain unauthorized access to networks, systems, or physical locations (such as evading firewalls) or for financial gain.
By posing as reliable people or information sources, threat actors utilize social engineering tactics to hide their actual identities and intentions. The goal is to persuade, coerce, or deceive users into giving up access to or sensitive information inside an organization. Many social engineering scams exploit people's willingness to help or their fear of punishment.
In order to get individuals to comply with their requests, the offenders usually display a feeling of urgency. As part of vishing attempts, the scammer may use a phone call to initiate a cybercrime in order to get login credentials and financial information, pursue identity theft, and induce a human mistake that leads to a successful cyberattack.
Smishing scams, one of the most common forms of social engineering attacks, are campaigns using SMS and text messages that try to make victims feel frightened, curious, or pressed for time. After that, it coerces victims into disclosing private information, opening malware-containing attachments, or clicking on links to dangerous websites.
What are the Most Common Tactics Used in Smishing Text Messages?
Because cybercriminals know how frequently individuals check their phones, they are taking advantage of SMS messages. Take a look at the recent SMS marketing statistics. Text messages are read and opened in 98 percent of cases. Within three minutes, 90% of all text messages are read. Emails, phone calls, and Facebook messages all had a response rate of 209% lower than text messages. People are just unaware of smishing cyberattacks, which makes things simpler for fraudsters. This lack of understanding creates a risky situation in which victims click embedded links, provide information, or react to the texting cybercriminal without hesitation. Scammers have evolved a variety of techniques for smishing smartphone users. Here are a few well-known methods to be aware of:
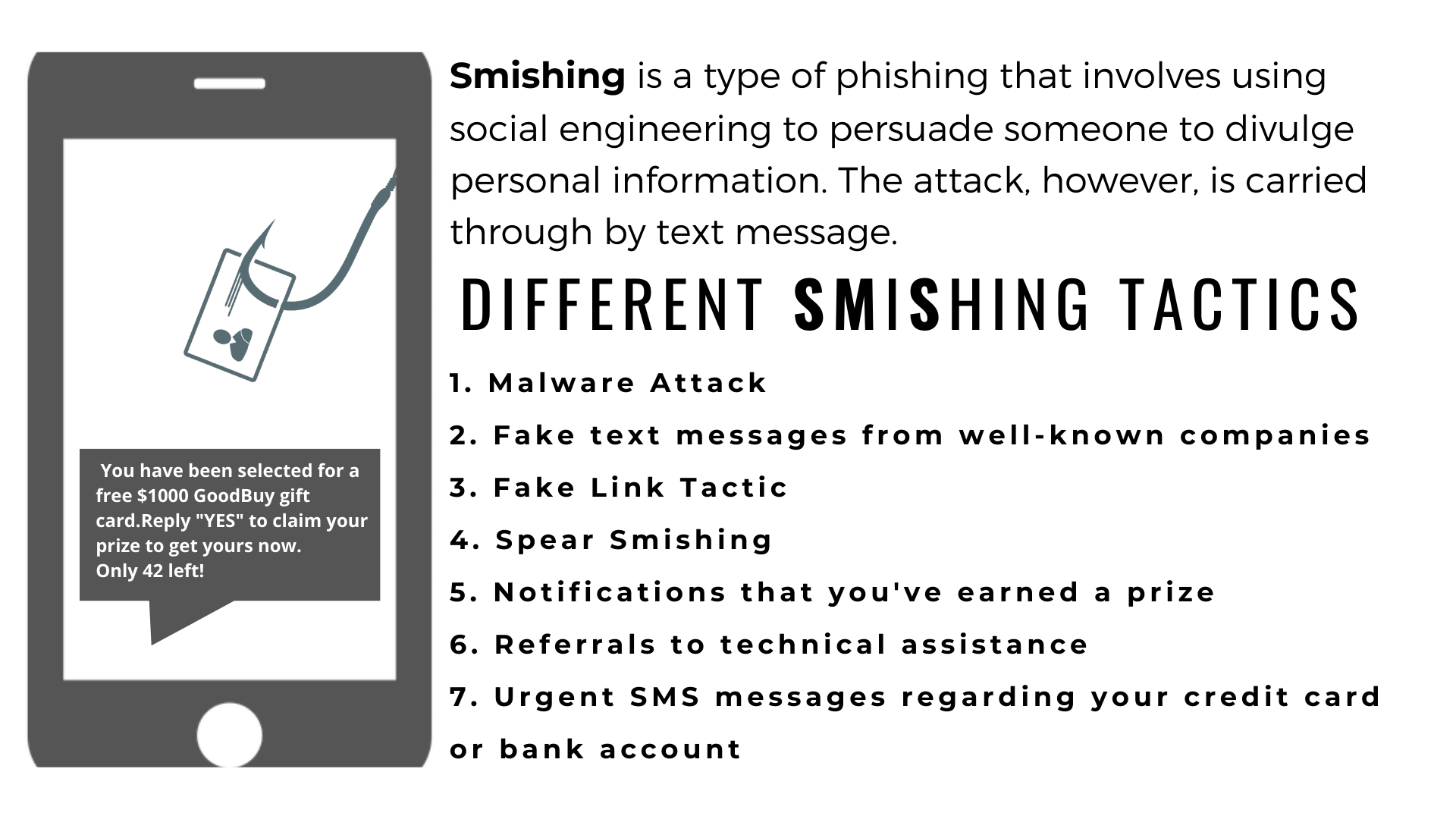
Figure 1. What are the Most Common Tactics Used in Smishing Text Messages?
-
Malware Attack: Fraudsters send a link that causes malicious software to be downloaded. On smartphones, clicks can initiate automated downloads in the same way they do on desktop browsers. These applications are frequently used in smishing campaigns to track your keystrokes, steal your identity, hand over control of your phone to hackers, or encrypt your phone's information and hold them for ransom.
-
Fake text messages from well-known companies: More organizations are starting to send out alerts for delivery or when there is unusual activity on their customers' accounts because they want to portray themselves as helpful. Businesses want their consumers to feel safe with their data, whether it's a login from a new device or a purchase from a foreign area. While this is beneficial in many ways, it also makes it easier for smishers to blend in.
To spot scam text messages;
- A mail that appears to be from your bank informing you of a problem with your account. A phone number is supplied for you to contact right away, or a link is provided to swiftly transport you to a specific website to update personal information
- A message requesting personal information, such as a social security number or an online account password
- A message prompts you to click on a link in order to solve an issue, win a prize, or gain access to a service
- A message purportedly from a government agency
- A message offering coronavirus testing, treatment, or financial assistance, or requesting personal information for contract tracking
- To opt out of future messages, respond "Stop" to a message that reads "click here and enter
-
Fake Link Tactic: This approach, like many email phishing attacks, employs text messages to lure victims to internet forms where their personal information may be taken. Scammers can view and exploit any information submitted into the form once a user clicks on the link and is redirected.
-
Spear Smishing: Committed smishers may analyze a user's social media activities in order to attract their target with highly tailored bait text messages in a version of spear phishing. The eventual aim is the same as with any phishing attempt, but it's crucial to note that these con artists may come equipped with your personal information to make their hoax feel more genuine.
-
Notifications that you've earned a prize: You may receive text messages informing you that you have won something and that you must click on a link to collect your prize. While this may appear to be a good deal, these con artists are easy to spot. For starters, if you didn't enter, you very certainly didn't win. Second, sharing links is far too simple. People would share links if all they had to do to win a reward was click on them, so their friends could win as well.
-
Referrals to technical assistance: This strategy is a version of the traditional tech support scam, or the "vish through smish," as it is known. An SMS message will instruct the receiver to call a customer service number supplied in the message. Once on the line, the scammer will appear to be a professional customer care agent and try to elicit information from the caller.
-
Urgent SMS messages regarding your credit card or bank account: Many hackers may send text messages pretending to be your bank or credit card provider in order to persuade you to click on a link or disclose critical information. They may inform you that your account has been locked and provide a link to unlock it, or they may fabricate a fraudulent transaction and request that you prove your identity to have it removed.
While banks and credit card firms may occasionally send text messages to their customers, it's generally for authentication codes or a notice that a questionable purchase has been made on their account. These genuine letters, on the other hand, hardly seldom include links.
Why are Smishing Attacks Particularly Effective Against Mobile Users?
As the challenges to cybersecurity keep changing, smishing attacks have become a powerful tool for hackers. It's critical for both individuals and companies to comprehend why smishing attacks work so well; users fall for them 6-20 times more frequently than they do for email-based attacks.
The skillful use of psychological manipulation in smishing attacks is one factor contributing to their efficacy. Attackers use human emotions by designing communications that arouse fear, curiosity, or excitement, which increases the possibility that receivers may fall for the fraud. These communications' personalization heightens the appearance of validity.
Additionally, social media has taught us to react quickly to alerts on our phones in order to get a tiny dopamine boost. When we are aware that we have a text message, we usually check it right away. Unlike emails, they are not censored or lost in the inbox.
Smishing takes advantage of flaws in mobile devices. Since more individuals depend on smartphones for personal, professional, and communication purposes, there might be serious consequences if these devices are compromised. Smishing campaigns are successful in part because of a lack of knowledge about mobile security concerns and the exploitation of device vulnerabilities.
Smishing attacks are very effective against mobile users for the following reasons.
- SMS texts are frequently trusted by people: Text messages are often more trustworthy than emails. We are therefore less inclined to be wary of such dangers.
- Fear and urgency: Attackers frequently employ urgency (such as "act now" messages) to incite fear and compel victims to take action without giving it much thought. Due to screen size or being out and about, people are less lik
- High open rates: Compared to emails, SMS messages have a significantly greater open rate. Additionally, the likelihood of employees engaging with harmful information increases with the number of employees viewing a message.ely to check URLs in texts.
- Bypassing security: Smishing is made easier by the fact that mobile devices frequently lack sophisticated security features like anti-phishing filters. The fact that most organizations' employees will be utilizing their own devices doesn't help either.
What are the Risks of Falling Victim to a Smishing Scam?
Smishing is becoming a problem for both consumers and businesses as more individuals use their smartphones for work (a practice known as "bring your own device," or BYOD). Therefore, it is not surprising that the most common type of harmful SMS message is now smishing.
As mobile device usage increases, so does cybercrime targeting mobile devices. In addition to being the most popular usage of cellphones, texting poses a particularly pernicious security risk for a few additional reasons.
These are the dangers of being a smishing scam victim.
- Malware: The smishing URL link may trick you into downloading harmful software, also known as malware, which will then install itself on your phone. In order to fool you into entering private information and transferring it to the crooks, this SMS virus may pose as trustworthy software.
- Malicious website: The smishing message's link may take you to a phony website that asks for private information. To make it simpler to steal your information, cybercriminals create rogue websites that seem like legitimate ones.
- Use of abbreviated URLs: To make it more difficult to identify scams, scammers utilize URL shortening services to conceal the link's true location.
How can You Protect Yourself Against Smishing Attacks?
Because smishing attacks are so common, stopping smishing calls for a mix of organizational, technological, and personal measures. Let's examine a few solutions used for protection against smishing attacks.
- MFA: Multifactor authentication (MFA) is an extra layer of security, even if hackers manage to get certain credentials through smishing.
- SMS Filtering: To detect, block, or flag questionable texts, a lot of devices and carriers now provide SMS filtering features.
- Anti-phishing Tools: A few mobile security apps can assist in spotting phishing links in texts and stop users from visiting harmful websites.
- Education and Awareness: Employees or members of an organization can be empowered to identify and report strange communications by attending regular training sessions on cybersecurity issues, including smishing.
- Simulated smishing testing: Organizations may send phony smishing messages to see how recipients react, just like they do with email-based simulated phishing testing. These assessments pinpoint areas that may require more training.
- Reporting Procedures: Provide workers or other stakeholders with unambiguous avenues for reporting possible smishing attacks. The organization can use these reports to notify people if they are the target of a particular smishing effort.
- Frequent Updates: To protect against the most recent known threats, keep software, especially security tools and mobile operating systems, up to date.
- Never Click on Dubious Links: Avoid clicking on any links or downloading attachments in unexpected or dubious texts.
- Utilize the security features on your phone: Utilize integrated security mechanisms, such as frequent software upgrades and biometric authentication, to protect personal information.
- Never Text Personal Information: Unless you started the discussion and are positive of the recipient's identity, never text personal, sensitive, or financial information.
- Verify on Your Own: If a text purports to be from a certain company or person, get in touch with them directly using contact data you already have, not the information in the text.
- Keep Up: Recognize the latest dangers and smishing techniques. Your first line of defense may be awareness.
- Verify any official correspondence: Generally speaking, official organizations, particularly banks and government agencies, don't text people for personal information. Call the organization directly if you're unsure.
No precaution is completely infallible, even though these methods can greatly lower the chance of being a target of a smishing assault. Fighting these and other cyberthreats requires constant attention to detail and a strong dose of skepticism.
What are the Key Indicators of a Smishing Attack?
Always proceed with caution when responding to unexpected or questionable messages, confirm their purported source using established contact techniques, and refrain from opening files or clicking on unknown links from senders you are not acquainted with. The following are the main signs of a smishing attack. The primary indicators of a smishing attack are as follows:
- Urgent or Threatening Language: Messages frequently generate a sense of urgency, including notifications regarding account suspension, outstanding bills, or suspicious activity.
- Promises of Rewards or Prizes - Messages that offer free gifts, money, or discounts are frequently employed to entice victims.
- Requests for Personal Information - Smishing messages frequently request sensitive information, such as Social Security numbers, bank account numbers, or passwords.
- Suspicious Website Links The message may contain links that appear to be legitimate but are actually redirecting to fraudulent websites that are intended to take information.
- Unfamiliar Sender - The sender's phone number or name may be unfamiliar, or it may resemble a legitimate organization (e.g., a bank or government agency).
- Unsolicited Messages - A smishing attempt may be suspected when a message is received unexpectedly, particularly one that requests action.
- Inadequate Spelling or Grammar - Grammatical errors or clumsy phrasing are prevalent in numerous smishing messages, which may serve as a warning sign.
- Requests to Download Files or Applications - Potential attackers may request that you install malicious applications, which have the potential to compromise your device.
- No Official Branding - Legitimate organizations typically include contact information, logos, and appropriate branding in their communications.
How can I Report a Suspected Smishing Attack?
The following measures should be taken to notify of a suspected SMS phishing (smishing) attack:
- Refrain from responding to the suspicious SMS or acting on any links in the message.
- Capture a screenshot of the message. This aids in the preservation of evidence.
- Forward the suspicious SMS to the spam reporting number provided by your carrier (e.g., 7726 in the United States).
- Report the attack to authorities such as the Federal Trade Commission (FTC) in the United States and Action Fraud in the United Kingdom, depending on your location.
- Prevent additional communication from the suspected number by rejecting the sender.
- Share the experience with your family and colleagues to encourage them to remain vigilant.
What are the Legal Consequences of Falling Victim to a Smishing Attack?
The legal repercussions of a smishing attack can vary depending on the jurisdiction and the nature of the attack. Here are a few potential legal results of falling victim to a smishing attack.
- Financial Liability: Unauthorized transactions or larceny may occur if assailants obtain access to your financial accounts. Consumers are safeguarded from liability for fraudulent transactions in certain jurisdictions, provided that they promptly report the issue.
- Identity Theft: Smishing attacks frequently seek to deprive individuals of their personal information. If your identity is used fraudulently, you may encounter legal complications, such as fraudulent credit card applications or loans submitted in your name, or criminal activities that are conducted under your identity.
- Data Breach: If the attack compromises sensitive data (e.g., company information), you may be held accountable if negligence is proved, particularly if you failed to adhere to the prescribed security protocols.
- Legal Investigations: In an effort to identify the perpetrators, victims may be required to participate in legal investigations. This may involve providing evidence and collaborating with law enforcement.
- Contractual Breach: In the event that the attack results in unauthorized access to systems or data that are subject to contractual obligations (e.g., client data), you may be subject to legal action for violating confidentiality agreements.
- Reputational Damage: If the attack involves the dissemination of fraudulent information or the compromise of professional systems, you may experience reputational injury, which could result in civil litigation.
- Compliance Penalties: In certain sectors (e.g., finance, healthcare), penalties may be imposed for noncompliance with data protection regulations (e.g., GDPR, HIPAA) by succumbing to a smishing attack.
In order to reduce these risks, victims should report the attack to the appropriate authorities promptly, notify the parties that are impacted, such as banks and employers, and seek legal counsel to ascertain their rights and responsibilities.
How can I Improve My Mobile Security to Avoid Smishing?
To avoid smishing on your mobile devices, make sure you are as safe as possible by taking these steps.
- Make use of encrypted end-to-end messaging applications. Make the switch to chat applications like Telegram, Threema, Signal, and WhatsApp that provide end-to-end encryption. Make sure to read the reviews because some are better than others.
- On your devices or services, enable encryption. While encryption is available on certain devices or services, it is not always the default setting. Don't forget to activate encryption. The following security measures are essential since encryption is only as good as the other security techniques it depends on:
- Make use of secure passwords. Use of a default password, a password that is easy to figure out, or a password that contains sensitive information, like the name of your pet, should be avoided. If someone can figure out your password, they can access your data regardless of how securely your device or application is secured.
- Stay up-to-date. No system is completely safe. Security flaws are constantly being found and patched through upgrades. Keeping up with updates for your devices, apps, and services is crucial because of this. You could be safer if the update fixes a vulnerability.
- Activate two-factor authentication (2FA). Two-factor log-in combines your standard login procedure (password and username) with an additional factor (such as a bank security fob). It becomes much more difficult for crooks to access your data when you add another element.
- Activate the erase-data features. Some businesses and cellphones include a feature that would delete your data after three or ten unsuccessful tries. To protect yourself from robbers or in the event that you misplace your phone, turn this on.
- Protect corporate devices against smishing attacks by implementing Mobile Device Management (MDM) solutions. You can protect, monitor, and manage staff devices that access corporate systems with MDM solutions.
- Monitor and filter messaging services. Work with telecom providers to detect and stop phishing text messages and message scams that target cell phones. Use spam filters and content monitoring tools to stop malicious, fraudulent, and scam messages from reaching mobile channels.
What are the Psychological Tactics Used in Smishing Attacks?
Attackers employ psychological manipulation in smishing to coerce victims into acting swiftly. One is less inclined to examine the dubious message the faster they take action. Messages frequently avoid the usual precautionary measures by invoking fear or haste. For instance, "Your account will be suspended if you do nothing within the next 24 hours."
Attackers frequently employ urgency, such as "act now" messages, to incite fear and compel victims to take action without giving it much thought. A call to action, such as clicking a link or dialing a number, is usually included in this message.
Furthermore, fraudsters frequently use social engineering techniques by sending texts that appear to be from reliable sources. To make their phony communications seem authentic, they may pretend to be banks, government organizations, or well-known businesses. These communications often use familiar logos and wording that replicate official correspondence to create the appearance of credibility.
One common tactic employed in smishing attempts to influence receivers is to instill a feeling of urgency. Text messages may warn you of serious problems, such as possible account suspensions or allegations of odd behavior, and may entice you to click on a link in a hurry or divulge private information without giving it enough thought, both of which might compromise your security.
Scenarios illustrating smishing fraud shed light on how dishonest they are. One classic case is getting a text message masquerading as an urgent need for financial aid from someone acting as an acquaintance, thus abusing trust and the felt need to respond swiftly.