A Chain is As Strong As The Weakest Link: Supply Chain Attack explained.
The supply chain is defined as the entire process of creating and selling commercial products, including every stage from the purchase of materials and the production of the items to distribution and selling them. Every phase of the supply chain must run smoothly, without interruption or exploitation, and it must be secure for the system to operate as a whole.
As the phrase states, a chain is only as strong as its weakest link. Multiple parties further along the supply chain may be impacted by the disruption of a single supplier. As a subtler entry point into the network, cyber attackers frequently choose to attack the vulnerable areas of their final target-the vendors of a corporation.
Research in 2020 has shown that big companies have around one thousand vendors on average, and more than 80 percent of companies have experienced a data breach in the past year as a result of supply chain attacks. In addition, In early 2021, more than 90 percent of the Forbes 1000 companies reported pandemic-related impacts on their supply chain.
In this article, we are going to cover the following topics;
-
What is a supply chain attack?
-
How do supply chain attacks work?
-
What are the Impacts of Supply Chain Attacks?
-
How do you detect a supply chain attack?
-
What are the types of Supply Chain Attacks?
-
Best practices to counter supply chain attacks?
-
Some examples of supply chain attacks?
What is a Supply Chain Attack?
A supply chain attack is a particular kind of cyber attack that aims at a dependable third-party provider of goods or services that the supply chain depends on, by taking advantage of breaches in its supply chain network.
A supply chain attack comprises persistent network hacking or infiltration techniques to penetrate a company's network to disrupt operations or cause outages, which ultimately hurt the target company. While hardware supply chain attacks affect physical components for the same reason, software supply chain attacks insert malicious code into an application to infect all users.
Supply chain attacks are a type of threat that targets suppliers and software developers. The intention is to spread malware by infecting trustworthy programs to gain access to source codes, development procedures, or update mechanisms.
Supply chain attacks are intended to take advantage of the trust that exists between a company and its customers. These connections could include alliances, connections with vendors, or the use of third-party software. Using these trusted connections to their advantage, cyber threat actors will breach one firm before moving up the supply chain and gaining access to the environments of other businesses.
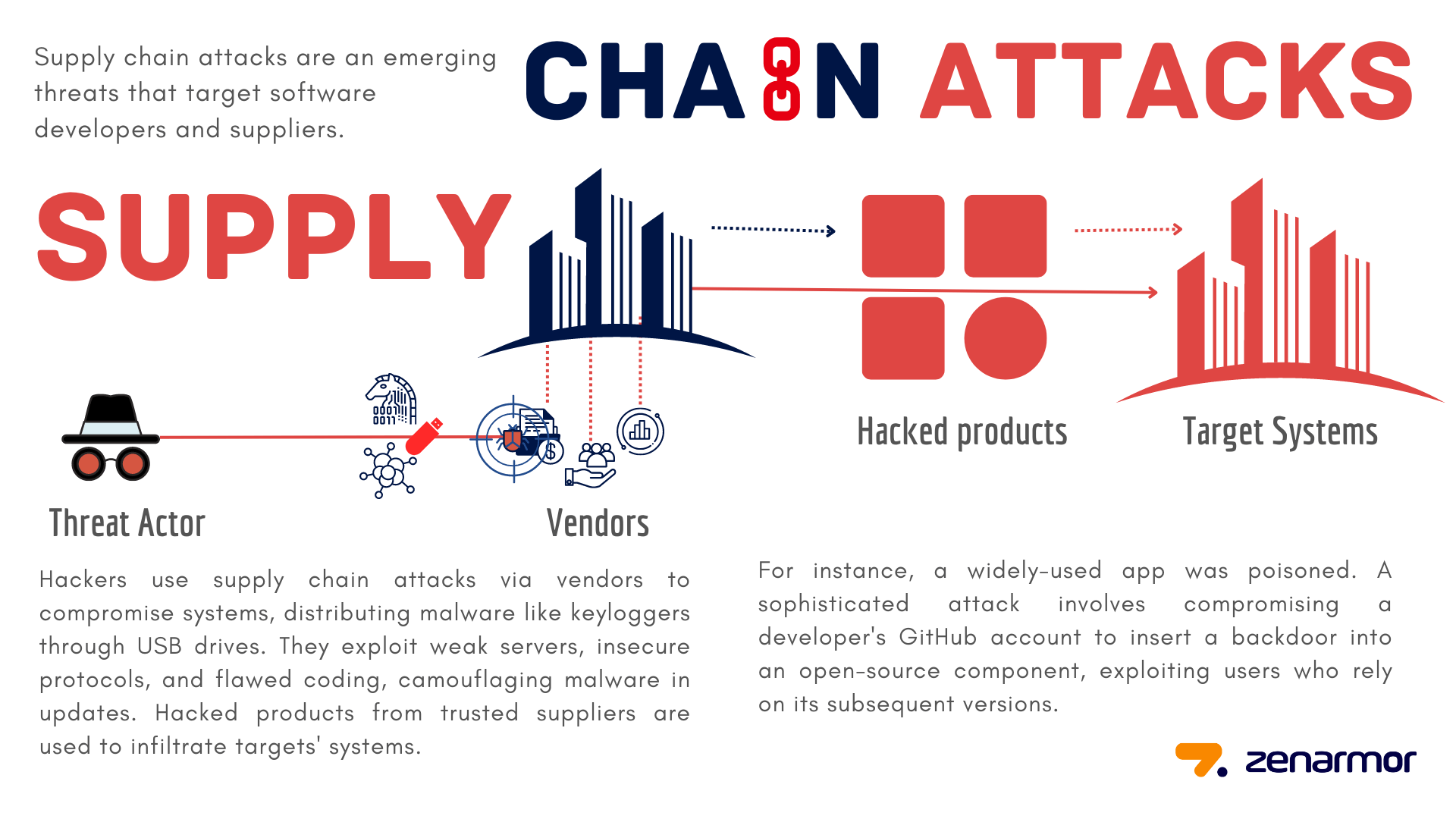
Figure 1. What is a Supply Chain Attack?
How Do Supply Chain Attacks Work?
To carry out a supply chain attack, hackers must find a technique to compromise network protocols or system components. This is accomplished by using a provider or vendor to spread viruses or other harmful software. For instance, a keylogger installed on a USB drive can infiltrate a major retail organization, where it records keystrokes to extract passwords for particular accounts. Then, attackers have access to private company data, client records, payment information, and more. When they come upon a hacking chance, they seize it and acquire access to vital digital resources.
Attackers look for vulnerable server infrastructures, insecure network protocols, and improper coding techniques. They breach systems, alter source codes, and camouflage malware in update and build procedures. The fact that many hacked products come from reliable suppliers makes it simpler for supply chain attackers to access the targets' computer systems. These apps and updates are signed and certified because the software is created and distributed by reputable suppliers. Vendors in software supply chain attacks are probably not aware that their applications or updates contain malicious malware when they are made available to the public. The malicious code then uses the same trust and access rights as the application. In a previous case, a top-used application for file completion was poisoned and the number of affected users was significant. Another example may be given for a sophisticated supply chain attack, by adding malicious software to the GitHub account of a developer, who is part of building an open-source component for a project which is widely used. The compromised developer doesn't have to be working on the project at that period. The attacker waits until the compromised component with a backdoor is in use for the following version. They achieve this by utilizing a program or one of its upgrades, which paradoxically are frequently made to close security flaws.
What are the Impacts of Supply Chain Attacks?
The results of a supply chain attack rely on the motivation, resources, and expertise of the bad actor. They don't just apply to parts of the government or companies that provide essential infrastructure. Advanced threat organizations attempt to sabotage infrastructure, steal governmental secrets, steal the personal information of citizens, and carry out industrial espionage.
As a result of their lack of familiarity with how supply chain attacks operate, many firms are ill-prepared should they become a target. A supply chain attack has catastrophic effects on business revenue, brand reputation, and vendor relationships. In addition to causing significant system and operational disruptions and long-term reputational harm, these attacks harm businesses and organizations.
Following are some examples of the main harm that supply chain attacks cause:
-
Data leaks and data release: Many supply chain attacks, particularly those based on hardware, spy on data and send it to a server under the control of the perpetrator. Any information that flows through a system containing malicious code may be compromised, possibly resulting in the theft of high-privileged account credentials for use in later intrusions.
-
Installation of malware: An application's malicious code is used to download and install malware on the company network. Using supply chain attack code, injection, ransomware, rootkits, keyloggers, viruses, and other malware could be set up.
-
Financial loss: A targeted company could lose millions if an employee is misled into wiring money to a bank account or paying fictitious bills.
Due to the importance of all of these factors for efficient and successful operations, businesses must make sure that their cybersecurity is as tight as possible, including safeguarding against attacks on the companies that are a part of their supply chain.
An effective supply chain attack is very damaging. The widespread repercussions of supply chain attacks can have been illustrated by several significant cases. In late 2020, one of the biggest cybersecurity incidents in recent, occurred when hackers compromised updates from networking tool and IT services provider SolarWinds that had been downloaded by 18,000 customers. The hackers then went on attack to about a hundred of those customers, including several government agencies, in one of the biggest cyber incidents in recent years.
Most likely, some of these adversaries are already present in the ecosystems of important supply chain targets and are watching for a chance to breach high-value targets. To gain access to their genuine targets of interest in the private sector, such as universities, pharmaceutical companies, hospitals, technology vendors, and others, these opponents are constantly exploring government organizations for flaws. Profit, sabotage, and espionage are typical motivations.
The expense of looking into, addressing, and recovering from software supply chain breaches is catastrophic for private enterprises. The actual effects of software supply chain attacks, however, can be much more serious and include severe disruptions to crucial infrastructure, public services, and/or federal institutions. Confidential government data is being misplaced, stolen, or interfered with by bad guys or other countries. Theft of data or digital assets that poses an obvious threat to national security by giving adversaries an advantage over the government in trade, intelligence, or military action.
How Do You Detect a Supply Chain Attack?
You must perform a methodical verification procedure of all assets and their entry points into your company to efficiently detect supply chain attacks. Here are some basic strategies for detecting threats to the supply chain.
-
Create an Asset Inventory: Every cybersecurity strategy needs an asset inventory, but a supply chain security strategy in particular. Map out the various data paths and identify all assets used by your firm. Make clear all software update sources and times. Locate the destination of each update. Define what means normal traffic in your enterprise network. Make sure your firewall is tuned up to all incoming traffic. You can detect all systems and current vulnerabilities that could result in a supply chain attack with the help of asset inventory analysis.
Understanding the threat landscape may also help you to narrow down and detect a possible supply chain attack. Identifying the kind of threat, breach, data leak, or malware that can most likely affect your supply chain, and its probability, including a catastrophic one.
-
Assign a Threat Actor Profile to Every Asset: The following stage is to develop a threat model that takes into account your environment after you have identified all the assets, systems, and pathways within your network. Reviewing your assets is essential at this point to identify the kinds of adversaries that any system could reasonably expect to face.
Some examples of threat actor profiles may be amateur attackers who cause disruption using open-source malware and harmful codes. Security breaches include staff members who leak or share confidential information for business, personal, or competitive reasons. Attacks using ransomware were carried out either by lone hackers or by teams of hackers looking for a ransom. A political or activist group pursuing a particular organization in order to make a statement.
Some of these attackers may not be interested in your organization because you do not fit the purpose. The categorization and scoring systems help your organization create a priority system for attack detection.
-
Update Risk Scores: Assigning a risk score based on the adversary and looking at the history of vulnerabilities within your software. Analyzing the density of the defect and sophistication level of the attack and the taken steps against the attack is helpful. Order assets according to risk potential and adjust the security controls when required. The scoring system will be updated and adjusted according to incoming alerts from vendors.
-
Regularly Test New Updates: Potential supply chain threats are identified before they materialize by testing new upgrades in a test environment or sandbox. Before deploying any updates, even those that appear to be legal and come from reliable applications, testing is essential to ensure that there are no open vulnerabilities that could enable an attack. New upgrades aren't always trustworthy when it comes to not destroying your software, even if the asset is not a threat to your network.
-
Analyze Malware: Another significant and efficient technique to find this serious supply chain threat is malware analysis. Here is some steps that can be taken:
- Fully automated analysis to create general reports, static properties analysis that gains access to executable files, interactive behavior analysis where a malicious program is implemented in a sheltered environment, and manual code reversing to decrypt hidden data and reveal a potential attack's methodology.
- Each task builds a solid basis for the security of your network and its valuable assets as it acquires knowledge and informs the subsequent level of analysis.
The volume of attacks on software supply chains in particular is increasing year over year as increasingly skilled attackers continue to get beyond traditional techniques of cyber protection. It's critical to identify supply chain threats to avoid potential harm to your systems.
What are the Types of Supply Chain Attacks?
Attacks on the supply chain take many different forms, such as software, hardware, or firmware supply chain attacks, but they are all intended to take advantage of security flaws in products that businesses rely on.
-
Software Supply Chain Attack: With the increase in the use of all kinds of software in recent decades, software supply chain attacks have become a frequently used method preferred by attackers. One compromised application or another piece of software is all that is needed for a software supply chain attack to spread malware throughout the entire network. Attackers frequently aim for the source code of an application to inject malicious code into a reliable program or computer system. Updates to software or applications are frequently used by attackers as entry points. The difficulty in tracking software supply chain attacks stems from the fact that hackers frequently sign code with stolen certificates to make it appear real.
-
Hardware Supply Chain Attack: Attacks on the hardware supply chain rely on physical components being compromised, including USB drives, phones, tablets, and keyboards. To maximize its impact throughout the supply chain, this kind of supply chain attack aims to infiltrate a device at an early stage of its production and utilize it as a backdoor into larger network systems. A USB keylogger can be given as a simple example of this.
-
Firmware Supply Chain Attack: Firmware fundamentally controls digital devices to maintain their functionality. By inserting malware into a computer's firmware, such as booting code, a firmware supply chain takes advantage of this, making it easy and quick to launch and difficult to stop such attacks. The malware starts to run as soon as a computer starts up, compromising the entire system. Attacks on firmware are swift, frequently unnoticed if you're not looking for them, and can be very destructive.
Best Practices to Counter Supply Chain Attacks
The recent supply chain attacks revealed alarming weaknesses in traditional defense strategies as well as showing the potential of its catastrophic effects. Despite the fact that some of the breaches that occurred were highly sophisticated cyberattacks, companies can still adopt security strategies to considerably fortify their digital supply chain. Best practices for preventing supply chain attacks are explained below:
-
Audit Unapproved Shadow IT Infrastructure: All IT equipment that has not been vetted by a company's security staff is known as Shadow IT. After the global pandemic forced organizations to switch to a remote-working model, which has resulted in many employees incorporating their own private IT devices while establishing their home office environments. All IT equipment should be registered, and there should be clear rules regarding what can and cannot be accessed, according to IT security services. It is important to keep an eye on all approved devices, particularly the ones connected to the internet, to spot DDoS attacks coming through the supply chain and stop them.
-
Maintain an Effective and Current Software Asset Inventory: Every cybersecurity strategy needs an asset inventory, but a supply chain security strategy in particular. The number of apps installed on devices connected to the network can reach high numbers, for even a small business. Tracking the installed software is not always easy, but important for an organization. Map out the various data paths and identify all assets used by your firm. You can detect all systems and current vulnerabilities that could result in a supply chain attack with the help of asset inventory analysis.
Not knowing what software asset you have is an additional issue to keep track of inventory. Keeping track and following the rules of the contracts and license agreements, is going to save your company from paying penalties or not having enough licenses in case you have a sudden growth. Another benefit is not to pay more money for licenses your organization does not need, while you benefit from upgrades.
Instead of using an employee to manually keep track of the assets and licenses etc., using some tools that track software installs and utilization throughout a business, is wise. In this situation, all that is required is the installation of a simple software agent on each machine that has to be viewed. The system will then keep track of how many licenses have been installed and how many have been purchased automatically. If the maximum number of installations is ever reached, alarms are triggered.
-
Assess a Vendor's Security Posture: Because most of the time your vendor is not protected against supply chain attacks as you do, the security posture of each vendor is made clear through third-party risk assessments, along with any problematic flaws that require fixing.
You and the vendor must develop a certain level of trust and transparency regarding the information that is available, who has access to it, and how it will be utilized before engaging third-party service providers that have virtual access to your organization's information systems.
To ensure that all cyber risk assessment responses can be independently validated, third-party risk management assessments should ideally be utilized in conjunction with a vendor security rating system.
Assessing and comprehending your vendor network, keeping an eye out for vulnerabilities, and spotting potential vendor data leaks are important. Make sure that every supplier who participates in your extended supply chain is aware of your company. Visibility of the vendors enables more effective tracking and security management. Conduct security awareness training sessions to educate staff on all aspects of security, including company policies, password security, and social engineering attack techniques.
Keep in mind that supply chains aren't always clear. For instance, if your heating and ventilating system is connected to the internet, the vendor might frequently update the firmware. Even if you haven't considered the vendor and its updates as part of your supply chain, they are.
-
Consider Supplier Risk Validation an Ongoing Process: A supplier may be safe in stage one, but the source of an attack is in stage two. The risk presented by each supplier should be assessed and the safety of each one should be regularly confirmed in terms of security, accountability, and visibility.
Engaging suppliers at crucial points in the supply chain is helpful. Anyone that produces, manufactures, changes, or delivers products in the supply chain is collaborating with vendors at important stages. With open-source technologies, you may start implementing continuous monitoring for the entire product lifecycle, carry out in-depth multi-dimensional analytics, and eventually broaden your vetting process to include subcontractors.
Suppliers should be regularly consulted, their security practices reviewed, and if necessary, audited by organizations. Root causes need to be identified. Reducing the threat might require digging deeper into some supply chains. The risk plan should be carried out periodically rather than just once.
-
Use Client-side Protection Tools: Client-server models let users download content from a server. You can filter downloaded material using client-side protection technologies to look for and prevent harmful software from being installed on a system in your network. Client-Side Protection defends against client-side threats like digital skimming, supply chain attacks, etc. that could steal your clients' data. You should be able to identify and control third-party services utilized by your website or application, permit authorized domains, restrict prohibited domains, and continue to monitor and manage third-party services as your application matures with client-side protection.
-
Use Endpoint Detection and Response (EDR) Solutions: Supply chain attacks frequently take advantage of endpoints with insufficient security. Many different supply chain attacks can be stopped using an endpoint detection and response (EDR) system since the endpoint is guarded against infection. As a result, an attack cannot be launched from the endpoint and propagated to other parts of your network. EDR can defend your business from threats whether you utilize an entirely internal system or a cloud platform. By confining the problem and preventing its spread, it can enhance the security of both the devices connected to your network and your entire IT system. It employs algorithms that examine the behavior of the many users on your system.
Detection, confinement, analysis, and elimination are the steps used in EDR. This makes it possible for EDR to store data on the activities occurring on each endpoint. An EDR can detect when something about a person's behavior is off in this way. It can identify the anomaly and take appropriate action when acting on an endpoint that deviates from a predefined pattern of behavior. It can assess the threat's nature and provide your IT team with details on how the attack began, which elements of your network it attacked, what it is doing presently, and how to eliminate it.
The data is processed and grouped into smaller categories to make it simpler for analysts to analyze. The user is informed of the next measures after it has been confirmed that a threat has affected an endpoint. The alarm is deactivated if the system detects a false positive, and the information is recorded to assist more precisely in addressing potential risks in the future.
-
Implement Robust Code Integrity Policies So That Only Authorized Applications Can Run: Code dependency policies are a set of guidelines that specify when and how a program may be used. The system blocks an application whose code raises a red flag. The number of supply chain attacks your business experiences can be reduced by following a stringent set of code dependency restrictions. Setting up rigorous criteria may occasionally identify legitimate apps, but it is always preferable to be safe first. Spending some time looking through tagged apps is not much of a loss compared to letting a backdoor open for a storm of a supply chain attack.
One example of a code integrity policy can be Windows Defender Application Control. The purpose of Windows Defender Application Control is to defend computers from viruses and other malicious programs. It ensures that only approved code can be executed and prevents malicious code from being executed. An explicit list of programs that are permitted to run on a PC is enforced by the software-based security layer known as Application Control. Application Control is independent of any hardware or firmware requirements.
-
Maintain a Highly Secure Build and Update Infrastructure: Over time, maintaining software security has become more critical for enterprises. Software security is now an absolute requirement and is no longer an option. Your ability to concentrate on your core company operations will increase as a result of efforts put into improving and maintaining your software security.
It's crucial to have a strategy in place for routinely installing security patches for your operating systems and the software you use to ensure that the builds and upgrades of your system are secure. Additionally, be sure that your system can only run reputable tools. Add a requirement for multi-factor authentication for administrators. Single sign-on security steps can also be taken. Some main steps to maintain a highly secure build can be seen below:
-
Preventive Company Practices: By only allowing internet traffic that is specified in your firewall policy, firewalls should be used to secure the network of your business. To stop, identify, and get rid of any harmful software and other risks, antivirus software should be utilized. All software needs to be patched and updated correctly. And to keep your software infrastructure secure and your clients protected, user access rights should be checked periodically.
When working remotely or connecting to your servers from mobile devices like smartphones or tablets, VPNs (virtual private networks) should be used. When not in use, company property should be kept locked and safe. Establishing secure passwords is essential. Any type of important audit should be conducted, documented, and periodically reviewed. Access by outside parties to the computer systems used by your business or to the building should be restricted and periodically evaluated.
Staff members are the main entry points for malicious code injections since they are frequently deceived into giving hackers access to an ecosystem. All employees must receive training on typical cyber attack techniques and stick to best practices, so they can recognize and report hack attempts like scam emails or phishing attacks, which frequently lead to the theft of internal login credentials.
-
Internal Data Encryption: Using suitable data encryption on customer data, personnel files, financial accounts, and other sensitive data is a simple and efficient method to protect data, considering the worst-case scenario, if an attacker physically enters your network or uses it to access files. For instance, using the Advanced Encryption Standard (AES) algorithm makes it more challenging for attackers to create the backdoor needed to decrypt data during a supply chain attack.
-
Testing: A proactive approach should be taken to prevent them by carrying out various forms of testing to make sure your software is not vulnerable to typical types of attacks. These ought to comprise accessibility testing, load testing, end-to-end testing, integration testing, penetration testing, and specification testing.
-
Disaster Recovery Plan: To minimize downtime or, in the worst-case scenario, prevent harm from a security breach or attack, a comprehensive disaster recovery strategy should be in place. This needs to be put to the test regularly, with the results evaluated and utilized as a basis to make improvements and guarantee that your personnel are in the best possible position during a disaster recovery scenario.
-
Develop Secure Software Updates as Part of Software Development: There are many secure software development life cycle models in use, and one of the well-known is the Microsoft Security Development Lifecycle, which provides some practices that companies can use to increase the security of their software. The Secure Software Development Framework from the National Institutes of Standards and Technology is another organization, which focuses on security-related processes that companies can integrate into their existing SDLC.
Making secure sockets layer encryption mandatory, requiring that everything is signed with a digital signature, including scripts, files, packages, and Extensible Markup Language (XML) files, not letting software accept generic input or commands, maybe some steps to take to build secure software updates as a key element of SDLC.
-
Develop an Incident Response Process: A systematic incident response procedure should include the sharing of truthful, open information. This includes rapidly informing internal stakeholders and clients of any incidents, along with their causes and any preventative measures that have been taken.
A sequence of steps should be built into your incident response strategy to address a potential data breach. There are some mains of any particular areas of need that should be taken into account during each phase including preparation before the incident, identification of the breach, containment of the problem, mitigation, and documentation. In these steps, identifying and prioritizing the assets, identifying potential risks, putting measures in place, and setting up a response team can be done. Documenting the plan and also documenting the incident and the measures put in place is crucial for the current attack and also for further possible breach attempts.
Selling the plan to the management team and responsible team before the incident is helpful to be on the same page. Documentation can include the lessons learned, and it is helpful for training employees on data security. Testing the employees, on the other hand, using ethical social engineers for being able to better identify phishing emails, social engineering, etc., is helpful for them to practice what they've learned and be ready for the attacks and damage control.
What is an Example of a Supply Chain Attack?
Several high-profile events have recently resulted from hackers' supply chain attacks. The following are some of the several actual supply chain attack examples that all involved trusted vendors' systems or software being compromised.
-
SolarWinds, 2020 : SolarWinds is a software company specializing in providing IT specialists with systems management solutions. Orion, a network management system, is the SolarWinds product that has seen the most widespread adoption. Over 300,000 people use SolarWinds' services, and a large portion of them are large businesses, including the majority of US Fortune 500 companies and a large portion of the US Federal Government.
The supply chain attack that is known most by everybody is the SolarWinds attack. One of the biggest data breaches ever was the SolarWinds supply chain attack, which was carried out by inserting a backdoor known as SUNBURST into the Orion IT update tool and leaving corporate and government production systems vulnerable to remote access. These updates were distributed between March and June 2020, and just 18,000 of the 300,000 Orion customers were thought to have downloaded the backdoor and been affected by the update, according to the company. The US Department of Defense, the US Treasury Department, and numerous others were impacted by this attack.
The malware was digitally signed by a legitimate digital certificate displaying SolarWinds' name and was distributed as part of an update from their servers, which is a strong indicator of a supply chain attack. Symantec issued the certificate with the serial number. An identity-based supply chain attack of this complexity and sophistication went through systems protected by the most advanced cybersecurity solutions and services. Through the exploitation of ordinary users' identities, the attackers were able to get through multifactor authentication and roam the network. The software that the hackers left behind and the data they obtained from those systems will probably be used in subsequent operations, such as account takeover.
-
Passwordstate, 2021: A supply-chain attack was announced last year by ClickStudios, the creators of Passwordstate, which is based in Australia. Passwordstate is an on-premises password management solution used by over 370,000 security and IT professionals at 29,000 companies worldwide, according to the company. Government, defense, finance, aerospace, retail, automotive, healthcare, legal, and media are just a few of the many sector verticals represented on its customer list, many of which are Fortune 500 organizations.
The update server for Passwordstate, which is located on a third-party content delivery network, was reportedly accessed by an attacker. During that time, the malicious dynamic link library was probably downloaded by any customers who updated their software. Using encryption keys kept on the disk of the web server, the malicious program was able to decrypt all the data kept in the customer's SQL database. The attackers were able to decrypt the entire database and exfiltrate the unencrypted data to the attacker's server because Passwordstate software was not using client-side encryption.
In a statement, the company provided a brief overview of the situation and advised clients to take action to reduce the risk. They noted that preliminary research suggests that a malicious individual who used sophisticated methods exploited the In-Place Upgrade feature. The first concession was given to the website's upgrade director at Click Studios. Before it was shut down, the compromise lasted for around 28 hours. Customers who conducted In-Place Upgrades between the aforementioned times were thought to be the only ones impacted. The company noted that their manual Upgrades were not compromised, but password information for affected clients may have been stolen. In further analysis, the company added that the initial compromise was not attributed to stolen or weak credentials.
-
Kaseya, 2021: Kaseya is an organization that provides IT solutions including VSA, unified remote monitoring, and a management tool for handling networks and endpoints. Kaseya is central to a larger software supply chain as the business also offers service desks, compliance systems, and a platform for professional services automation.
In 2021, The REvil ransomware, malware with a focus on file and drive encryption, infected MSP software used to manage thousands of customer environments, allowing attackers to demand $70 million from Managed Service Providers customers which was a program used to remotely monitor and administer IT services for customers. Over 1 million devices were infected, claimed by REvil group.
Customers were informed of the breach via email, phone, and online notices, and they were urged to shut down the related servers. Cyber forensic experts were pulled to assist and Kaseya developed a patch on short notice. One of the firms noted that the attack was started by an authentication bypass vulnerability in the Kaseya VSA web interface, which gave the attackers access to an authenticated session and allowed them to upload a malicious payload and use SQL injection to execute commands, leading to code execution.
Kaseya, CISA, and other parties quickly offered some steps to take to potentially harmed companies and customers. Shutting down on-premises servers is urged to avoid further compromise. Organizations were given access to download and run the latest version of the Compromise Detection Tool, which scans for data encryption and the REvil ransom note. Enabling multi factor authentication on all accounts was another piece of advice given by CISA and FBI, as well as limiting remote work and setting up administrative interfaces behind a VPN or a firewall. Finally, businesses must make sure that backups are current and kept in a location that is both accessible and separate from the primary network. Affected and interested enterprises can get daily updates on the ransomware outbreak by visiting Kaseya's helpdesk blog.
-
Dependency Confusion, 2021: A security researcher was able to access Tesla, Apple, Apple, Uber, and Microsoft. To give services to end users, the researcher, Alex Birsan, took use of the dependencies that programs require. Birsan was able to send phony but secure data packets to prominent users due to these dependencies.
Through the registration of a dependency with the same name but a higher version number on a public repository, dependency confusion attacks take advantage of private, internally developed software dependencies. The erroneous dependency is then probably included in the product build rather than the valid dependency.
-
Mimecast, 2021: Hackers were able to compromise a security certificate used to authenticate Mimecast's services on Microsoft 365 Exchange Web Services during the Mimecast attack. Only a small number of users were affected, but 10% of Mimecast's clients utilize apps that depend on the exposed certificate.
-
SITA, 2021: SITA is a significant aviation IT company providing IT and telecom services to around 400 members in the industry, claiming to serve around 90% of the global airline business. A coordinated attack on the supply chain affected multiple airlines and hundreds of thousands of passengers. SITA said that attackers had gotten into passenger data stored on its SITA Passenger Service System servers in the US. These servers run passenger processing systems for airline clients.
According to reports, the SITA data breach compromised more than 580,000 records from the frequent flier program of Malaysia Airlines. Several other airlines, including Finnair, Air New Zealand, and others, have revealed breaches that exposed tens of thousands of customer details for each airline. Singapore Airlines exchanged information with Star Alliance, which is thought to be the source of the attack. It then propagated across the entire supply chain from there.
SITA took immediate action to contact affected customers and all related organizations and acted fast to try and contain the threat and assigned incident responders and third-party experts to monitor and solve the issue.