What is MITRE ATT&CK and How is It Used For Understanding Attack Methods?
Successful and thorough threat detection needs an awareness of common adversary strategies, which ones represent the most risk to your business, and how to identify and counteract these cyber attacks. Unfortunately, the number and range of assault techniques make it practically difficult for a single business to monitor every attack type, and document and communicate these results to anybody outside their organization. As a result of these considerations, MITRE decided to build the ATT&CK framework in 2013.
MITRE ATT&CK is a framework that is used all around the globe in a variety of contexts, including threat hunting, intrusion detection, security engineering, threat intelligence, red teaming, and risk management.
MITRE ATT&CK is a comprehensive and cross-referenced repository of information about real-world threat organizations and their known behaviors; their activities; and the software and tools they employ in their attacks. The ATT&CK knowledge base serves as a basis for the creation of specialized threat models and approaches in government, the business sector, and the cybersecurity product and service community.
All information collected by ATT&CK is derived from publicly accessible data and reports, as well as from the community, which consists of threat researchers and security teams that experience or analyze attacks every day.
MITRE ATT&CK is accessible to all individuals and organizations at no cost.
Due to its attacker-centric design, MITRE ATT&CK is distinct from existing risk-based and defender-focused threat modeling and cyberattack lifecycle models. This makes it a particularly important tool for helping security teams acquire insight into the behavior of attackers to enhance their defenses.
In this article, we'll explain what the MITRE Att&CK framework is, the primary components(TTPs) and importance of Att&CK, and the challenges that you might encounter when using this application, MITRE Att&CK history, and the main differences between MITRE Att&ck and Lockheed Martin Cyber Kill Chain.
What is the Mitre ATT&CK Framework?
MITRE Adversarial Tactics, Techniques, and Common Knowledge(ATT&CK) is the abbreviation for the MITRE ATT&CK® software. The MITRE ATT&CK framework is a curated knowledge base and model for the behavior of cyber adversaries. It takes into account the different stages of an adversary's attack lifecycle as well as the platforms that they are known to target. A common taxonomy of specific adversary behaviors is provided by the model's strategy and method abstraction, which is understood by both the offensive and defensive sides of cybersecurity. In addition to this, it offers a suitable degree of classification for antagonistic activity as well as certain strategies for countering this action.
The following essential components are included in the ATT&CK behavioral model that has been presented:
Techniques defining the ways in which adversaries attain tactical objectives (the individual cells), and tactics expressing the short-term, tactical opponent goals that are intended to be accomplished during an attack(the columns). As well as documentation of the tactics and other information used by the opponent (linked to techniques).
ATT&CK covers Enterprise IT systems such as Windows, macOS, Linux, Network infrastructure devices (Network), and Container technologies (Containers); cloud systems such as Infrastructure-as-a-Service (IaaS), Software-as-a-Service (SaaS), Azure Active Directory, Office 365, and Google Workspace; and mobile devices such as iOS and Android.
MITRE ATT&CK collects their observations about attack behaviors in matrices. Each matrix addresses a distinct target. There are now three matrices of MITRE ATT&CK available:
-
ATT&CK for Enterprise: This edition focuses on malicious behavior across many operating systems, including Windows, Mac OS X, Linux, and the cloud. Enterprise Att&ck also provides a PRE-ATTACK matrix. Many of the operations that bad actors do before an enterprise is penetrated are often performed outside the organization's awareness, making it exceedingly difficult to identify these pre-attack tactics and approaches. For instance, cyber-attackers may use information publicly accessible on the internet, connections the business has with other organizations that have already been penetrated, or other techniques to seek access. PRE-ATT&CK enables defensive businesses to better monitor and comprehend pre-attack activity occurring beyond their network perimeter.
-
ATT&CK for Mobile: This version focuses on malicious activity that may occur on mobile devices using the iOS and Android operating systems.
-
ATT&CK for ICS: In this edition, the emphasis is placed on elaborating on the behaviors that an adversary may exhibit while functioning inside an ICS( industrial control systems) network like SCADA.
Each matrix contains detailed technical descriptions of each technique used for each tactic throughout the adversarial attack lifecycle, the assets, and systems that each technique targets, as well as mitigation and countermeasure approaches, the detection analytics used to uncover the technique, and real-world usage examples.
When examining the matrix, strategies are provided in a linear manner outlining the attack lifecycle, beginning with reconnaissance and ending with the ultimate objective, whether that objective is information exfiltration, file encryption for ransomware purposes, both, or other harmful activity.
The following is a list of tools and resources that may be used in the ATT&CK Framework:
-
Red Canary Atomic Red Team: This open-source software is capable of simulating hostile conduct in accordance with the MITRE ATT&CK Framework. It is a basic library of tests that security teams may execute to test their security policies. These tests are focused, have minimal dependencies, and are specified in a structured way that automation systems may exploit.
-
Red Team Automation: This is another open-source application capable of simulating malicious activity based on MITRE ATT&CK methods and techniques. It consists of a Python script capable of simulating over 50 strategies and a built-in binary program capable of injecting processes and simulating beacons, among other activities.
-
MITRE Cyber Analytics Repository (CAR): This is a knowledge base on analytics supplied by MITRE. It includes a huge dataset of hypotheses, information domains that characterize the context of the analytics, references to certain ATT&CK TTPs, and pseudocode demonstrating how the analytics may be implemented.
-
ATT&CK Navigator: This is a free mapping tool between security restrictions and ATT&CK procedures. Specifically, it is possible to add investigative controls, preventative controls, and layers of observed behavior. The Navigator can be used online for simple models and scenarios, or it can be downloaded and installed locally for more permanent use.
-
Caldera: An open-source network security platform intended to simulate threats and automate security responses. It may be used by both red teams and incident responders. It bases its automatic activities on the MITRE ATT&CK Framework.
What is TTP in MITRE ATT&CK?
MITRE ATT&CK is a collection of recorded information on the harmful behaviors used by advanced persistent threat (APT) organizations at different phases of actual intrusions. ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, contains detailed descriptions of these groups' observed tactics (the technical goals they're attempting to achieve), techniques (the methods they employ), and procedures (specific implementations of techniques), also known as TTPs.
MITRE ATT&CK defines adversary TTPs, advices on detection and common mitigations for particular tactics, and profiles the known behaviors, features, and attack attributions of APT organizations. ATT&CK also gives a comprehensive list of attack software (both malware and commercially available and open-source code that can be used legitimately or maliciously).
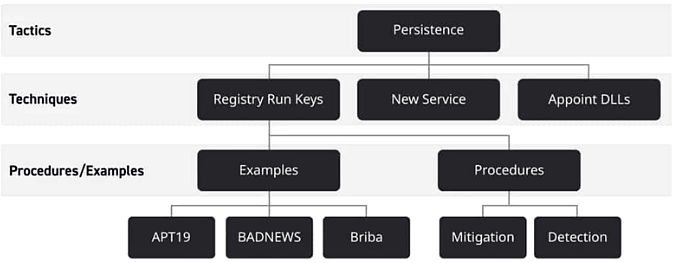
Figure 1. Hierarchal model of ATT&CK tactics, techniques, and procedures.
Typically, implementing MITRE ATT&CK requires manual mapping or integration with cybersecurity solutions, such as Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Cloud Access Security Broker (CASB).
Using MITRE ATT&CK in conjunction with a SIEM requires gathering log data from endpoints, networks, and cloud services, detecting risks, and mapping them to MITRE ATT&CK. Then, modifications to the security posture are made in the security tools supplying their log data (i.e., EDR or CASB).
Using MITRE ATT&CK with EDR includes mapping events detected by the endpoint agent, which enables defenders to discern the stages of a threat event, estimate the risk associated with it, and prioritize action.
What are the Tactics of the ATT&CK Framework?
Tactics of the ATT&CK framework describe the attackers' immediate technical goals (the "what"), such as obtaining Initial Access, sustaining Persistence, and establishing Command and Control. Inevitably, attackers must use many strategies to finish an assault effectively.
The Enterprise ATT&CK Version 11 matrix lists fourteen tactics in a logical order, outlining the stages of an attack. They consist of:
-
Reconnaissance: Collecting of intelligence before an attack.
-
Resource Development: Creating, purchasing, compromising, or stealing the resources required for an attack.
-
Initial Access: Acquiring network or system access to the victim.
-
Execution: Executing malicious code on a compromised system or network.
-
Persistence: Maintaining network or system access persistently.
-
Privilege Escalation: Attempting to get a higher degree of privileges.
-
Defense Evasion: Acts used to avoid being detected
-
Credential Access: Attempting to access credentials by stealing account names and passwords.
-
Discovery: Obtaining data about the deteriorating environment
-
Lateral Movement: Going from one compromised system to another compromised system
-
Collection: Collecting data to assist the high-level assault objective
-
Command and Control: Establishing control over the victim's network systems and/or connecting with compromised systems from outside the victim's network.
-
Exfiltration: Data theft from a victim
-
Impact: Damaging, destroying, or otherwise rendering the victim's networks, systems, and/or data inaccessible.
Each tactic is fundamentally an attacker's objective. If cybercriminals achieve these specific objectives, they will be one step closer to achieving their ultimate purpose. In certain instances, the attacker will not attempt to implement every possible tactic since some may exceed his or her objectives. For instance, an attacker may not desire lateral movement if all they want to do is take information from a given machine. In this instance, the MITRE ATT&CK matrix may not have entries for "Lateral Movement".
What are the Techniques of the ATT&CK Framework?
Techniques are a description of the "how," or the means by which an attacker will accomplish a strategy. Under each "tactics" category, a variety of techniques are described. This is due to the fact that adversaries may use various approaches based on criteria like their skill sets, the system setup of their targets, and the availability of compatible tools.
Each technique contains a description of the method, the systems and platforms it affects, the adversary organizations that use it (if known), mitigation strategies, and references to its actual usage. Every approach in every matrix has a number of methods associated with it, and the Enterprise matrix even divides some of those techniques further into sub-techniques. Sub-techniques are a more particular way of describing the hostile activity that is used in order to accomplish an objective. They are a more fundamental level of behavior description than techniques. Spear Phishing Attachment, Spear Phishing Link, and Spear Phishing through Service are the three connected sub-techniques that are linked with phishing.
MITRE ATT&CK Enterprise presently defines 191 techniques and 386 sub-techniques for business. MITRE continuously updates the techniques uncovered in the field by cybersecurity researchers and hackers.
To demonstrate how the techniques and tactics of ATT&CK come into play, say an attacker wishes to install mining software on a network. Their goal is to infect as many workstations inside the network as possible, hence increasing the amount of mined cryptocurrency. The ultimate objective requires multiple intermediate stages. The attacker must first get access to the network. For instance, they may send spear-phishing links to one or more individuals on the network. Then, to raise privileges, they may utilize process injection, which includes injecting code to circumvent security and elevate privileges. Once on the network, the miner may attempt to infect further computers.
In this attack, the miner had to use a range of tactics. They used spear-phishing to get "Initial Access". This allowed them to enter the network. Then, by using process injection, they attained the "Privilege Execution" tactic. In addition, when the miner infects other computers, they use lateral execution. The ATT&CK report would include how the miner executed each approach as well as the techniques used.
What are the Procedures of the ATT&CK Framework?
The procedures of the ATT&CK framework describe the specific implementations of techniques and sub-techniques that APTs have used, or it can refer to specific malware or other tools that attackers have used.
An example of a technique would be an adversary utilizing PowerShell to inject malicious code into lsass.exe on a victim's computer to scrape credentials from LSASS memory. Within the ATT&CK framework, procedures are classified as methods seen in the wild and may be found in the "Procedure Examples" section of pages devoted to certain techniques.
Why is Mitre ATT&CK Important?
The MITRE ATT&CK framework may assist a company in several ways. It is a free tool that has been extensively embraced by commercial and public organizations of all sizes and sectors. Users include security defenders, penetration testers, red teams, cyber threat intelligence teams, and any internal teams interested in constructing safe systems, applications, and services. The abundance of attack information it includes may assist security teams in determining whether they are gathering the appropriate data to efficiently identify attacks and assess the efficacy of their present defenses.
ATT&CK deliberately adopts an attacker's perspective to assist businesses to comprehend how attackers plan, prepare and execute attacks. This also makes ATT&CK an ideal resource and teaching tool for people interested in joining the fields of cybersecurity or threat intelligence, as well as those who want to learn more about attacker behavior.
Threat hunters use the ATT&CK methodology to identify connections between the precise strategies that attackers are using against their defenses and to comprehend the visibility of assaults aimed at their defenses at endpoints and across the network perimeter.
Red team members utilize the MITRE ATT&CK methodology as a guide to assist in identifying the attack surfaces and vulnerabilities in corporate systems and devices, as well as to enhance the capacity to mitigate attacks by gaining knowledge. This covers how attackers acquire access, how they navigate inside the compromised network, and how they avoid discovery. This suite of tools helps businesses to acquire a better understanding of their entire security posture, discover and test protection holes, and rank possible security gaps based on the risk they provide to the enterprise.
Security platform developers and engineers use MITRE ATT&CK to analyze the efficacy of their products, discover previously undisclosed vulnerabilities, and simulate how their solutions would behave throughout the lifetime of a cyber attack.
In general, using MITRE ATT&CK offers the following advantages:
-
Enrichment of Cyber Threat Intelligence: Enriches information regarding threats and threat actors. ATT&CK enables defenders to evaluate their ability to defend against particular Advanced Persistent Threats and common threat actor behaviors. Numerous businesses may choose to prioritize the monitoring of enemy group actions that pose a significant danger to their sector or vertical. The ATT&CK framework paper is not static. MITRE continues to improve the framework as new and evolving threats arise, making it a helpful source of truth for tracking the actions of hacker groups and understanding the strategies they use.
-
Adversary Emulation: The technique of evaluating the security of a technological domain by using cyber threat data about particular adversaries and how they operate in order to replicate that threat. Adversary emulation focuses on an organization's capacity to validate the detection and/or mitigation of hostile behavior at all relevant times in its lifetime.
ATT&CK is used to construct adversary emulation scenarios that can be used to test and validate defenses against common adversary tactics. The information provided in ATT&CK may be used to create profiles for particular enemy groups. Defenders and hunting teams may also utilize these characteristics to align and strengthen defensive tactics.
-
Behavioral Analytics Development: Behavioral detection analytics, which goes beyond standard indicators of compromise (IoCs) or signatures of malicious activity may be used to discover possibly hostile activity inside a system or network that does not depend on previous knowledge of adversary tools and indications. It is a method of identifying and linking suspicious behavior that is agnostic or independent of certain tools that may be employed by exploiting how an adversary interacts with a given platform.
ATT&CK is used to build and test behavioral analytics to identify hostile behavior in a given environment. One example of analytic development that might be utilized as a starting point for an organization to generate behavioral analytics based on ATT&CK is the Cyber Analytics Repository (CAR).
-
Red Teaming: Red teaming is acting as an enemy to highlight the consequences of a security violation. Red teaming focuses on achieving the final goal of an operation without being noticed to demonstrate the mission or operational effect of a successful breach.
ATT&CK is used to construct red team plans and arrange activities to circumvent specific defensive measures that may be in place inside a network. It may also be used as a research roadmap to discover new methods of carrying out acts that are not detectable by standard defenses.
-
Prioritization of Detections: ATT&CK is helpful in prioritizing the detections depending on the particular context of your business. Even the most resourceful teams cannot guard equally against all attack vectors. The ATT&CK framework provides teams with a guide on where to concentrate their detection efforts. For instance, several teams may prioritize threats earlier in the attack chain. Other teams may choose to prioritize particular detections depending on the prevalence of strategies used by attacker groups in their respective sectors. Teams may educate themselves on the methodologies, targeted platforms, and risk to shape their security strategy, then use the MITRE ATT&CK methodology to monitor their progress over time.
-
Assessment of Defensive Gaps: The MITRE ATT&CK paradigm is also useful for analyzing existing tools and coverage depth for important attack tactics. ATT&CK may be used to evaluate current tools or test new tools before purchasing them to identify security coverage and prioritize investments. Many telemetry levels may be applied to each detection. In certain areas, teams may determine that they require great confidence in the depth of detection, while in others, a lesser degree of detection may suffice. By identifying the dangers that are a top priority for the company, teams may assess the effectiveness of their present protections. The matrix may be used to determine the scope of a red-teaming exercise or penetration test and then as a scorecard during and after the test.
-
SOC Maturity Assessment: The Security Operations Center(SOC) of an organization is a crucial component of many small to big corporate networks that constantly monitor for active threats against the network. Understanding a SOC's maturity is critical for determining its efficacy.
ATT&CK is one metric that may be used to assess how successful a SOC is in detecting, analyzing, and responding to intrusions. A SOC Maturity evaluation, like a defensive gap assessment, focuses on the procedures that a SOC utilizes to identify, analyze, and react to evolving threats to their network over time.
Challenges When Using ATT&CK
Utilizing ATT&CK is not without its share of difficulties. As the quantity and size of ATT&CK matrices continue to expand, they have gotten more complicated. Although the number of variations and permutations of strategies and procedures in the framework is very exhaustive, the sheer volume of data to absorb and analyze may be daunting.
For example, the fourteen strategies mentioned in ATT&CK for Enterprise detail more than 400 distinct approaches or attack patterns. Many of these approaches have sub-techniques that boost the number of permutations even more. Numerous firms have not yet automated the mapping of all this data to their present security architecture, which is a daunting process.
In recent research, it was shown that although virtually all organizations utilize the framework to identify network events with different network security devices, less than half of respondents have automated the framework-indicated security policy adjustments.
Other obstacles include the inability to correlate information from mobile devices and endpoints or the difficulty of linking cloud-based and on-premises events.
When using ATT&CK, it is important to keep the following considerations in mind.
-
Not all tactics are necessarily malicious: File Deletion is a tactic described under Defense Evasion, which makes perfect sense. Data taken from a Network Shared Drive (T1039) is another example. The question of how this approach is being used is essential to the detection process. How will you differentiate between routine file deletions and an attacker's efforts to elude detection?
-
It is not always simple to identify certain methods: Detecting brute force attacks is quite simple if you know what to look for. Exfiltration over Alternative Protocol, such as a DNS tunnel, is notoriously tough to discover, even if you're actively searching for it. The key to any long-term data security plan is the capacity to identify difficult-to-find procedures.
-
Certain procedures may be carried out in a variety of different ways: Dumping of Credentials(T1003) is an example of this case. The most important step in detecting the approach is to compile all of the known ways to invoke it and designate them all as credential dumping.
-
Some strategies are mentioned under numerous tactics: For example, DLL Search Order Hijacking (T1038) appears as a technique under the headings of Persistence, Privilege Escalation, and Defense Evasion. Certain methods have many applications and may be helpful at various points during an assault.
MITRE ATT&CK vs. Cyber Kill Chain
Another well-known framework for comprehending the actions taken by an adversary during a cyberattack is called the Lockheed Martin Cyber Kill Chain®. The following are the phases that make up the Kill Chain model:
-
Reconnaissance: Harvests conference details, email addresses, etc.
-
Weaponization: Weaponization combines an exploit with a backdoor to turn a payload into something that can be delivered.
-
Delivery: Sends the package containing the weapon to the target via various delivery methods like email, USB drives, etc.
-
Exploitation: The term "exploitation" refers to the process of taking advantage of a system flaw in order to run malicious code on a victim's computer.
-
Installation: This step infects the asset with malicious software.
-
Command and Control (C2): It entails having a command channel for performing manipulations remotely.
-
Actions on Objectives: The invaders are successful in achieving their primary objectives by gaining access through the "Hands-on Keyboards" exploit.

Figure 2. Seven Phases of the Cyber Kill Chain
While the Cyber Kill Chain and another security framework known as the Diamond Model are still in use, the MITRE ATT&CK Framework is now the most extensively used. MITRE ATT&CK, unlike prior frameworks, it indexes every aspect of an attack from both the attacker and defensive perspectives. MITRE ATT&CK-mapped attack scenarios may be recreated by red teams and tested by blue teams.
ATT&CK and the Cyber Kill Chain work in tandem. ATT&CK describes adversary conduct at a lower degree of description than the Cyber Kill Chain. Because opponent tactical goals fluctuate during an operation, ATT&CK tactics are unordered and may not all occur in a single incursion, while the Cyber Kill Chain employs ordered stages to define high-level adversary objectives.
The distinctions between MITRE ATT&CK and Cyber Kill Chain are summarized below.
To begin, the MITRE ATT&CK framework provides a substantially more in-depth examination of how each step is carried out via the use of ATT&CK procedures and sub-techniques. MITRE ATT&CK is continually updated with feedback from the industry to ensure that it is current with the most recent security tactics. As a result, defenders should frequently update their procedures and attack models.
Second, the Cyber Kill Chain does not take into account the many strategies and procedures that are used during a cloud-native assault. The Cyber Kill Chain paradigm assumes that a threat actor, such as malware, would deliver a payload to the target environment. However, this tactic is far less important while operating in the cloud.
ATT&CK, unlike the Cyber Kill Chain, employs tactics rather than phases and consists of 14 tactics.
Utilizing Mitre ATT&CK to split the event into its distinct components is beneficial. It may help you identify where things went wrong and what you can do to prevent future occurrences.
However, it may be worth thirty minutes to go through the Cyber Kill Chain first. It might be beneficial to document the seven phases and how the organization's defenses correspond to them. Then, a high-level brainstorming session may be held to determine if any of these defenses could be strengthened or are due for replacement. If the issue is evident at this level, it may not be the most efficient use of everyone's time to go further.
History of MITRE ATT&CK
MITRE is a nonprofit organization based in the United States, Bedford, Massachusetts, and provides the federal government with engineering and technical advice. In 1958, the corporation was spun off from MIT and has been engaged in a variety of commercial and top-secret projects for several organizations. Among them was the creation of the FAA air traffic control system and the AWACS airborne radar system. The National Institute of Standards and Technology(NIST) funds a significant proportion of MITRE's cybersecurity practice.
ATT&CK was developed in response to a need to systematically classify the enemy activity as part of performing organized adversary emulation exercises at MITRE's Fort Meade Experiment (FMX) research facility. FMX was established in 2010 as a "living lab" that gave researchers access to a production enclave of the MITRE corporate network to install tools and test and develop concepts for enhanced threat detection. Under an "assume breach" approach, MITRE started studying data sources and analytic procedures inside FMX to identify advanced persistent threats (APTs) more rapidly. Periodically, cyber game exercises were undertaken to imitate adversaries inside a densely monitored environment, and hunting was done to test analytic hypotheses using the obtained data. Through telemetry sensing and behavioral analytics, the objective was to enhance post-compromise detection of threats infiltrating organizational networks. The major success measure was "How good are we at recognizing recorded hostile behavior?" To properly attain this purpose, it was advantageous to classify observed behavior across relevant real-world opponent groupings and then use this information to conduct controlled exercises imitating these adversaries within the FMX environment. ATT&CK was utilized by both the adversaries. emulation team (for scenario development) and the defender team (for analytic progress tracking), making it a significant factor in FMX research.
The first ATT&CK concept was developed in September 2013 and mainly targeted the Windows enterprise environment. It was enhanced further via internal research and development before being published to the public in May 2015 with 96 approaches divided into 9 strategies. Since then, ATT&CK's development has exploded due to donations from the cybersecurity community. Based on the technique used to develop the original ATT&CK model, a parallel knowledge base called PRE-ATT&CKTM was developed to concentrate on "left of exploit" behavior, and ATT&CK for Mobile was developed to focus on mobile-specific behavior.