How to Block Websites on pfSense® Software?
The primary purpose of blocking websites for residential use is the protection of small children. Hardware or software web content filtering systems are essential for limiting access to unwanted web content. Adult sites, sites infected with malware, and sites that could be detrimental to employees or students are examples of objectionable content.
Despite the fact that the benefits to the company may not be as obvious, they are significantly more numerous. Hacking, phishing, infections, and malware are some of the greatest threats to any organization. Phishing, for instance, is when hackers acquire sensitive information through deception, such as by luring employees into logging in to fictitious companies to obtain login credentials. The loss or corruption of sensitive data, such as login credentials, accounting data, personal information, and legal documents, can be catastrophic for any organization.
In this tutorial, we will explain how to block websites on the pfSense software firewall and the importance of web filtering.
What are the Methods For Blocking Websites on pfSense?
pfSense® software provides several alternatives for blocking websites. You may use one of the following techniques to block certain websites or web categories on your network depending on your requirements:
-
Deploying Zenarmor
-
Deploying pfBlocker NG
-
Deploying Squid Proxy
-
Configuring DNS
-
Defining Firewall Rules
1. Deploying Zenarmor
Zenarmor is a plug-in that upgrades your pfSense firewall to a next-generation firewall (NGFW) in a matter of seconds. Some of the available Zenarmor features are as follows: - Application/User based blocking
-
Web/Content Filtering
-
Enterprise-grade Network Analytics
-
Policy-based filtering
-
Ad Blocking
-
Real-time Cloud Threat Intelligence
-
Active Directory Integration
-
Cloud-managed central policies and many more.
You can easily install and configure the Zenarmor Free Edition extension forever for blocking websites on your pfSense firewall by following these steps:
-
Install zenarmor by running the next command on pfSense CLI:
curl https://updates.sunnyvalley.io/getzenarmor | sh -
Add a Zenconsole account at https://dash.zenarmor.com/register/newuser. No credit card is required.
-
Register your Zenarmor node to the Zenconsole Cloud Management Portal by running the following commands on pfSense CLI:
rehash
zenarmorctl cloud register -
Complete the Initial Configuration of your firewall for the cloud.
-
Navigate to the Policies > Default to edit the default policy of your newly added firewall on Zenconsole.
-
Click on the Web Controls tab
-
Select one of the existing Web profiles, such as
High Control. There are four different types of predefined Web Profiles on Zenarmor:- Permissive: There are no restrictions on web browsing in this profile.
- Moderate Control: Only dangerous/highly risky web categories such as Illegal Drugs, Adult, Pornography, Violence, and Advertisements are blocked in this profile.
- High Control: Forums, Alcohol, Blogs, Gambling, Chats, Dating, Games, Job Search, Online Storage, Social Networks, Software Downloads, Weapons, Military, Swimsuits, Tobacco, and Warez Sites are among the categories blocked in this profile, in addition to the ones blocked in the Moderate profile.
- Custom: By creating a new profile, you can perform fully customized web filtering.

Figure 1. Selecting Web Control Profile for Blocking Websites on Zenarmor
-
You may need to define Application Control for blocking some large business websites, such as
YoutubeorTwitter. Click on the App Controls tab. -
Select the Application Category, such as
Gaming, that you want to block and click on the toggle button located on the right side of the application category.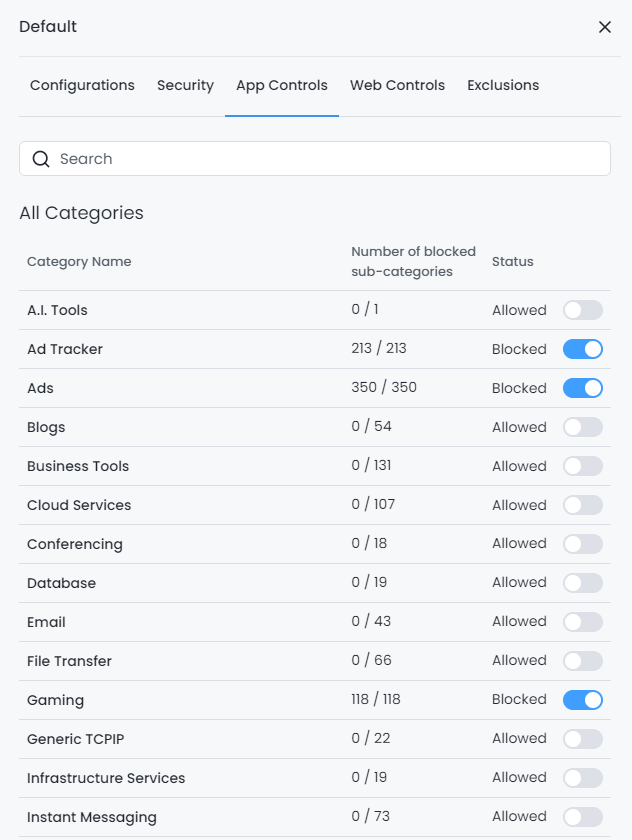
Figure 2. Blocking Entire Application Category on Zenarmor
-
You may block individual applications. Use the Search field to look for and locate a specific application. To find an application in the list, simply type its name into the search form.
-
Click on the toggle button located on the right side of the application you want to block.
Figure 3. Blocking Specific Application Individually on Zenarmor
Now, Zenarmor will automatically block the websites and applications that you selected on the Default policy configuration. You may view the blocked connections by navigating to the Live Sessions > Blocks page on the Zenconsole.
What is the advantage of Zenarmor over other web-blocking options on pfSense?
Zenarmor® provides threat intelligence powered by artificial intelligence to protect your network against more than 300 million websites and domains. included in all Zenarmor subscriptions, from the Free Edition to the Business Edition.
Zenarmor provides the following capabilities:
-
Real-time cyber threat intelligence
-
Web site categorization
-
Site Reputation and Classification (to be used with TLS Inspection Whitelisting/Blacklisting).
Zenarmor Business Edition provides enhanced protection for users, including an additional 1+ billion categorized domains and 4+ billion recorded IPv4/6 addresses. In addition, Business Edition users receive access to a global threat intelligence network constituted of more than 140 top cyber security vendors utilizing BrightCloud® Threat Intelligence to enhance and expand their threat detection solutions. You can therefore rest comfortably knowing you have access to the highest quality threat intelligence available. BrightCloud® has evaluated over 48 billion domains to date and adds to this database every day by analyzing approximately 25,000 threats and URLs.
Subscribers to Zenarmor Business Edition receive automated access to the BrightCloud® Threat Intelligence database, which is fueled by sixth-generation machine learning and offers their businesses the highest level of protection at all times. Zenarmor provides superb threat intelligence regardless of whether you have a Free, Home, or SOHO subscription.
2. Deploying pfBlocker NG
pfBlockerNG is a free and open-source application developed for pfSense software that blocks advertisements, malicious content, and geo-locations. BBCan177 generates it for IP/DNS-based filtering. It is based on Marcello Coutinho and Tom Schaefer's previous work. The objective of the project was to extend the primary firewall functionality of pfSense by enabling users to control and administer inbound and outbound access through the firewall using IP and DNS control lists.
Installing pfBlockerNG will allow you to block not only advertisements, but also web surveillance, malware, and ransomware. Using pfBlockerNG increases your security and privacy. Using DNSBL (short for Domain Name System-based Blackhole List) will accomplish this for your entire network. Additionally, pfBlockerNG allows you to block traffic from specific IP addresses. These IP addresses may pertain to specific countries and regions, which can be very useful for safeguarding your network from intruders endeavoring to gain entry.
3. Deploying Squid Proxy
It is possible to block access to such sites if web traffic is routed through a proxy server. Squid's SquidGuard add-on, for instance, enables the barring of websites based on URL or other similar criteria. You can easily configure Squid and SquidGuard on the pfSense platform for web filtering.
In contemporary environments, this is ineffective because HTTP, and not HTTPS, is optimal. HTTPS can sometimes be filtered using peek/splice to inspect SNI and other aspects of connections, but modern security practices such as encrypted SNI render this technique ineffective. A non-transparent proxy configuration is more likely to function accurately, but more difficult to configure and maintain.
4. Configuring DNS
You can input an override to resolve the objectionable website to an invalid IP address, such as 127.0.0.1 if the built-in DNS Resolver or Forwarder is active.
Do not rely solely on DNS override functionality to block access to websites. When DNS blocking is enabled, local clients must use the firewall as their sole DNS source. It will deter non-technical users but can be easily circumvented by those with greater technical proficiency.
You may quickly block a website using DNS resolver on the pfSense software firewall by following the next steps given below:
-
Navigate to the Services > DNS Resolver > General Settings on your pfSense software.
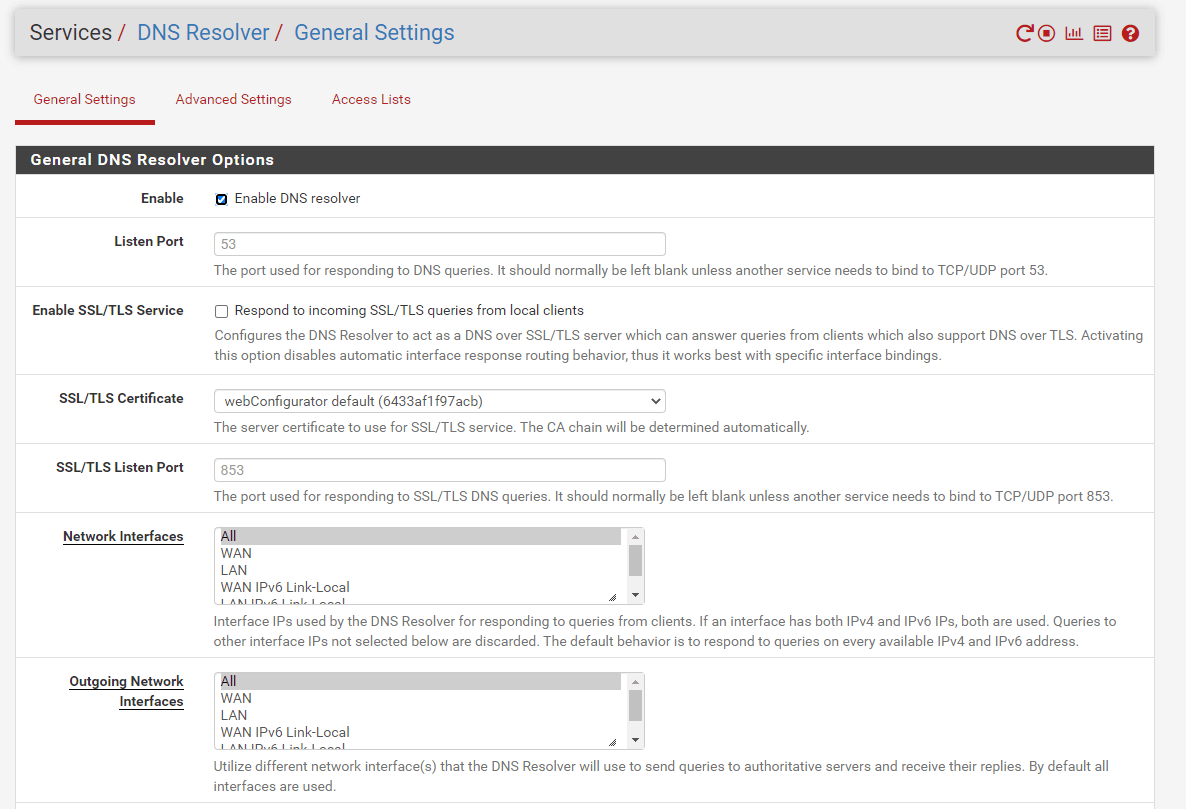
Figure 4. DNS Resolver General Settings on pfSense
-
Scroll down to the DNS Overrides pane.
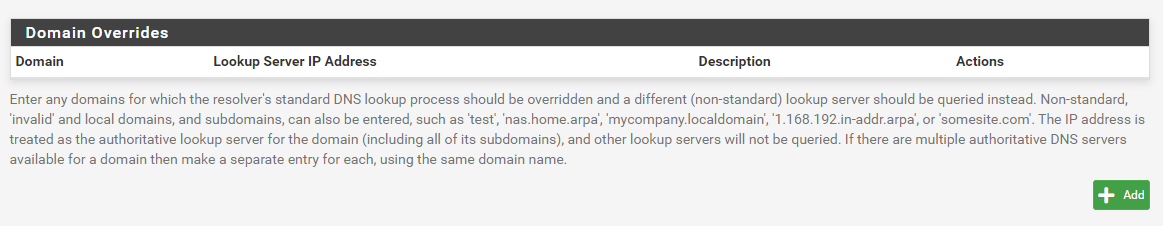
Figure 5. DNS Overrides on pfSense
-
Click +Add button to add a new DNS override.
-
Type the domain name that you want to block into the Domain field, such as
facebook.com. -
Type the lookback address,
127.0.0.1into the IP Address field. -
Fill in the Description field,
Blocking Facebook.
Figure 6. Adding DNS Overrides on pfSense
-
Click Save.
-
Click Apply Changes to activate the settings.
Through the DNS Resolver's custom options, additional methods are available.
This first example prevents clients from resolving any hosts within the specified zone:
server:
local-zone: "mycompany.io" static
When a firewall enforces DNS resolution in this manner, it must require clients to resolve DNS through the firewall. If not, clients could circumvent restrictions by utilizing alternative DNS servers.
This can be restricted using custom views. This example is similar to the previous one, but it restricts access to 10.0.0.10 only:
server:
access-control-view: 10.0.0.10/32 blocksites
view:
name: "blocksites"
local-zone: "mycompany.io" static
5. Defining Firewall Rules
You can block a website using an alias If it alters its IP address infrequently. You may easily create an alias comprising its IP addresses and use it in pfSense firewall rules.
This is not a feasible solution for Google and other large sites that yield minimal TTLs and distribute the burden across multiple servers and/or data centers. Most small to medium-sized websites can be effectively blocked with this method, as their IP addresses rarely change.
Hostnames can be contained within network aliases. Periodically, the pfSense firewall resolves the hostname and updates the alias as required. This is more efficient than manually looking up the IP addresses, but it still falls short if the website returns DNS records in a manner that changes frequently or randomizes results from a pool of servers for each query, which is typical of large websites.
Finding all IP subnet allocations for a site is another option. You may create an alias for these networks and block their traffic by adding a firewall rule on your pfSense. This is notably beneficial for websites like Facebook, which distribute a significant quantity of IP space but are limited to a few Internet blocks. Utilizing regional registry sites like ARIN can aid in locating these networks. Under "Related Networks" at http://whois.arin.net/rest/org/THEFA-3.html, you can find a list of all the networks used by Facebook in the region covered by ARIN. You should verify additional regional sites, such as RIPE, APNIC, etc., as companies may have multiple addresses in various regions.
As an alternative to manually searching for the IP blocks, locate the BGP Autonomous System (AS) number for the target organization by performing a whois query on one of their IP addresses. For example, Facebook's AS number is AS32934 and the command below will locate all of their allocations:
whois -h whois.radb.net -- '-i origin AS32934' | awk '/^route:/ {print $2;}' | sort | uniq
Copy the output of that command into a new alias, and it will encompass all of their currently assigned networks. Periodically check the results for updates.
How to Prevent Avoidance of Web Restrictions on pfSense?
There are numerous methods to circumvent the defined barriers if you use the aforementioned techniques. Utilizing proxy websites is the simplest and most prevalent method. It is impossible to find and block each of these individually and maintain an up-to-date list. Utilizing an external proxy or category-blocking content filtration is the most effective method for preventing access to these sites. Therefore, Zenarmor is the best solution that provides a rich web categorization and application database. You may easily block proxy services on Zenarmor.
Figure 7. Blocking Proxy Servers on Zenarmor
Additionally, you should use a restrictive set of egress rules and only permit traffic to specific services and/or hosts to maintain greater control. For instance, restrict DNS access to the firewall or the DNS servers used for LAN customers exclusively. You must disable direct HTTP and HTTPS access through the firewall and only permit traffic to and from the proxy server if a proxy server, like Squid, is in use on the network.
What is the Importance of Web Filtering on pfSense?
Applying web filtering on pfSense filtering offers a number of benefits to both individual consumers and enterprises. The main advantages of blocking websites are outlined below:
-
Increased Staff Productivity: It is well-known that social networking is a productivity drag because it is distracting, occupies a great deal of essential work time, and results in decreased production. Access restriction has been shown to significantly increase productivity. In contrast, some industries require social media expertise for daily operations. A subset of websites, such as online purchasing and streaming sites, are productivity drawbacks for these enterprises. There is no justification for employees to view movies when they should be working. In addition to limiting access to distracting websites, it is essential to evaluate other channels that may pose a security risk, such as downloading dubious files, reading questionable emails, and responding to unverified contacts.
-
Malicious Code Prevention: Malware is one of the most severe threats to the organization, and it must be protected against. Viruses and other types of hazards can enter a company's network in a variety of ways, which is one of the primary reasons why companies restrict internet access. Web filters are able to detect malware and block access prior to the completion of any installation. Exploit packages contain malware designed specifically to exploit web browser vulnerabilities through extensions and plugins. Unknowingly, a user visits a malicious URL containing an exploit kit that, when exploited, triggers a malware installation.
-
IT Policy Implementation: Too many business IT policies are essentially documentation that sits in a receptacle, only to be glanced over by new employees on their first day, and then largely forgotten by the rest of the staff. The second common scenario is that the IT policy is buried somewhere on the company's intranet, where it is largely ignored by 90 percent of the workforce. This is a difficult reality for businesses to face, and educating people about the dangers of phishing and browsing suspicious websites may be challenging. However, by implementing web filtering, the organization gains greater control over how its employees use the internet, thereby preventing a significant amount of misconduct from occurring.
-
Bandwidth Utilization: Internet usage that is unrelated to work utilizes a substantial quantity of network capacity. By restricting access to particular websites, you can improve network bandwidth utilization and obtain faster connections. To achieve network bandwidth efficiency, you may educate your employees on the advantages of a perpetually rapid network or implement restrictions on video streaming sites such as YouTube.
-
CIPA (Children's Internet Protection Act) Compliance: To be in conformance with CIPA, schools must restrict or filter Internet access to images that are obscene, pornographic, or harmful to children (for computers accessed by juveniles). Schools eligible for the CIPA must satisfy two additional certification requirements:
- As part of their Internet safety regulations, the web activity of minors must be monitored.
- They must include provisions for educating children on appropriate online behavior, such as interacting with others on social networking sites and in chat rooms, as well as cyberbullying awareness and response.
How to Perform URL Filtering on pfSense?
Zenarmor NGFW allows you to perform URL filtering on pfSense software firewall. Zenarmor offers blocking functionalities based on URLs and URL regular expressions, empowering users to enforce more rigorous security measures through the prohibition of access to specific websites or URL patterns. This safeguards their clients against recognized threats and unauthorized intrusion.
The TLS inspection function is intricately incorporated with the URL Blocking capability. URL Blocking allows for more precise restriction of URLs through the use of wildcard options (*) in the URL. This functionality enables the targeted manipulation of subdomains or pathways across the entire system.
You may easily block a URL via Zenarmor running on pfSense by following the next steps:
-
Navigate to the Web Controls tab on the policy configuration page of Zenarmor.
-
Click on the URL Blocking pane.
-
Type the URL into the URL field.
-
Type a descriptive name into the Description field.
-
Click Block.

Figure 8. Blocking URL on Zenarmor