What Are The Best Open Source Firewalls?
A firewall is a network security device that monitors and regulates network traffic based on predefined security rules. It forms a vital part of the network security system separating the trusted network from an untrusted network, such as the Internet. You may need a firewall not only to protect your servers and clients against attacks that may come from the Internet but also to prevent the unprivileged user access to your mission critical systems.
After giving the firewall definition it may be better to summarize the evolution of it shortly.
A packet filter is a first-generation network firewall that inspects packets sent between computers. This firewall may filter the packets by source and destination IP addresses, protocol, source and destination ports on the network.
Second-generation firewalls, also known as stateful firewalls, not only filter packets but also keep track of particular communications between endpoints by remembering which port number the two IP addresses use for their connection at layer 4 (transport layer) of the OSI model. So that these firewalls allow examination of the overall exchange between the nodes.
Next generation firewalls provide application/Layer 7 filtering. The main advantage of application layer filtering is that it can detect certain applications and protocols. This feature allows next generation firewalls to detect if a permitted protocol is being exploited or to identify undesired applications or services using a non-standard port. Main features of the next generation firewalls are as follows.
-
Standard firewall capabilities like stateful inspection.
-
Web/content filtering
-
Application awareness and control to see and block malicious applications.
-
Integrated intrusion detection and prevention.
-
Threat intelligence sources.
-
Methods for dealing with changing cyber threats.
Today, hackers use advanced methods such as intrusions, Viruses, Spyware, Worms, Trojans, Adware, Keyloggers and Malicious Mobile Code (MMC) to attack their targets. Therefore, packet filtering is not enough to prevent these modern cyber threats and using the next generation firewall is a must to be safe for every company and even home users in the computer world.
Open source firewall is best known for protecting the network from a threat by filtering the inbound and outbound traffic and ensures network security.
Nowadays, open source firewalls which have application layer filtering capabilities are widely deployed in especially home, education, start-up and small scale industry networks.
In this article we will look at some of the best open-source firewalls that can improve your network security and cover the following topics deeply:
- What are the best/top 10 open source firewalls?
- What is an open source firewall and why should you use it?
- What are the Benefits of Using Open-Source Firewalls?
- How Secure are Open-Source Firewalls?
- What are the Challenges of Open-Source Firewalls?
- Are Open-Source Firewalls Right for Your Business?
The Best Open Source Firewalls to Protect Your Network
Open source operating systems such as Linux, FreeBSD, and OpenBSD have a vast number of networking and security features built in. As a result, they are natural platforms for developing security products, and the majority of commercial firewalls are built on one of them.
There are numerous options available, ranging from tiny embedded systems for broadband wireless routers to massive enterprise firewalls with all the bells and whistles from free community support to paid commercial support.
If you are a home user or have a small business which does not have enough budget for expensive commercial firewalls, you may use the open source firewall on your network without any hesitation.
In this article, we will be discussing briefly the best open source software firewalls that can be used as both home network security and enterprise network security solutions. Some of the open source firewalls listed below have features and capabilities comparable to expensive commercial firewall solutions. So, many companies deploy them as their main network security solution at a fraction of the cost.
These are some of the best Open Source Firewall solutions available to protect your IT infrastructure:
-
OPNsense
-
pfSense
-
IPFire
-
Untangle
-
IPtables
-
VyOS
-
Endian Firewall
-
Shorewall
-
Smoothwall
-
IPCop Firewall
1. OPNsense Firewall
OPNsense is a FreeBSD-based open source firewall and a fork of pfSense and m0n0wall. It is compatible with 32bit or 64bit system architecture and available to download as ISO image and USB installer. It provides a GUI available in multiple languages like French, Italian, Russian, Chinese, Japanese, etc. OPNSense has many enterprise levels of security and firewall features like 2FA, Netflow, Proxy, Webfilter, QoS, IPSec, VPN, etc. It also uses an inline intrusion prevention system with deep packet inspection to detect and prevent network intrusions. Another important feature is that It offers weekly security updates.
In this section, we will give information about:
-
What is OPNsense?
-
Features of the OPNsense firewall
-
OPNsense firewall installation
-
Zenarmorplugin of the OPNsense firewall
What is the OPNsense Firewall?
OPNsense is an open source, easy-to-build and easy-to-use HardenedBSD based firewall and routing platform. The OPNsense project was founded by Deciso, a company in the Netherlands, makes hardware and sells support packages for the OPNsense firewall. OPNsense began as a fork of pfSense® software and m0n0wall in 2014, with its first official release.in January of 2015. Meanwhile, when m0n0wall was decommissioned in February 2015, its creator, Manuel Kasper, assigned the developer community to OPNsense. And it continues to build a large community with thousands of supporters.
OPNsense provides weekly security updates in small increments to respond to new emerging threats in a timely manner. It has a fixed release cycle of two major releases per year.
"Our mission is to make OPNsense the most widely used open source security platform. We give users, developers and business a friendly, stable and transparent environment. The project's name is derived from open and sense and stands for: "Open (source) makes sense." -Deciso
How to Install OPNsense Firewall?
The installation of OPNsense firewall is straightforward. You can easily install the OPNsense firewall either
- on your Proxmox VE by following instructions on OPNsense Installation Tutorial or
- on a PC from USB as explained in How to Install OPNsense from USB tutorial.
Features of OPNsense Firewall
OPNsense has many features intended for advanced users. Administrators can use the OPNSense firewall to configure network flow monitoring, full mesh VPN routing, WAN load balancing, HTTP load balancing, and much more.
OPNsense's feature set includes high-end features like forward caching proxy, traffic shaping, intrusion detection, and simple OpenVPN client setup.
The emphasis on security in OPNsense results in unique features such as the ability to use LibreSSL instead of OpenSSL (selectable in the GUI) and a custom version based on HardenedBSD.
OPNsense's reliable and robust update mechanism enables it to provide critical security updates in a timely manner.
It also includes reporting and analysis capabilities. You can monitor network traffic and optimize network performance.
One of the best aspects of OPNsense is that it exposes all of its functionalities through a web-based interface that is easy to use and available in multiple languages.
OPNsense implements a stateful firewall and allows administrators to group firewall rules by category, which is useful for more complex network configurations.
OPNsense has an Inline Intrusion Prevention System which is a powerful form of deep packet inspection. Rather than simply blocking an IP address or port, OPNsense can inspect individual data packets and, if necessary, block them before they reach the sender.
Core features of the OPNsense firewall are summarized in the following list.
-
Stateful inspection firewall
-
Intrusion Detection and Prevention
-
Traffic Shaper
-
Forward Caching Proxy (transparent) with Blacklist support
-
Virtual Private Network (site to site & road warrior, OpenVPN & legacy PPTP, IPsec support)
-
High Availability & Hardware Failover (with configuration synchronization & synchronized state tables)
-
Two-factor Authentication throughout the system
-
Captive portal
-
Build-in reporting and monitoring tools including RRD Graphs
-
Netflow Exporter
-
Network Flow Monitoring
-
Support for plugins
-
DHCP Server and Relay
-
DNS Server & DNS Forwarder
-
Dynamic DNS
-
Encrypted configuration backup to Google Drive
-
Granular control over state table
-
802.1Q VLAN support
Zenarmor Plugin for OPNsense Firewall
OPNsense has a rich plugin collection that provides network security professionals the opportunity to extend their OPNsense nodes with additional functionality. All plugins can be easily installed on the firewall. Some of these are maintained and supported by the OPNsense team, while others are maintained and supported by the community or directly by businesses.
Plugins can do the following:
-
Allow custom start, stop and early scripts
-
Persistent /boot/loader.conf modifications
-
Additional themes for the web GUI
-
Create new authentication methods to be used within other subsystems
-
Provide other types of devices and interfaces to the firewall
-
Modify the access control lists, menu and themes
-
Add additional server software and their respective GUI pages
-
Pull in additional packages that will update automatically
-
Enhance the backend services with additional work tasks

Figure 1. OPNsense Web GUI with Zenarmor Plugin
The OPNsense Web GUI shows all plugins for production use in the firmware page and the pkg tool shows all packages (all Plugins are named os-pluginname).
One of the most important and useful OPNsense plugins is Zenarmor which provides application control and web filtering to protect the network infrastructure. We will cover the Zenarmor plugin features in this article shortly. Please refer to official documentation for more information.
What is Zenarmor?
Zenarmor is an all-software instant firewall that can be deployed virtually anywhere. For open-source firewalls, Zenarmor provides cutting-edge, next-generation firewall features that are not currently available in products like OPNsense. If you want to use an open-source firewall and need features like Application Control, Network Analytics, and TLS Inspection, Zenarmor provides these features and more.
Since Zenarmor has an appliance-free, all-in-one, all-software, lightweight, and simple architecture, it can be instantly deployed onto any platform which has network access. You can install the Zenarmor on a virtual machine or bare-metal, on your promise or any cloud platform.
Zenarmor is fully integrated into the OPNsense Web User Interface and basically upgrades OPNsense into a Next Generation Firewall.
How to Install Zenarmor?
You can easily install the Zenarmor plugin on your OPNsense firewall web UI by following these steps.
-
Login your OPNsense web GUI se an account with administrative access such as
root. -
Navigate to
System->Firmware->Plugins. -
Click on the
+icon next toos-sunnyvalleyto install the plugin. Once the vendor plugin is installed, you should see the Zenarmor plugin available in the list of plugins asos-sensei. -
Click the
+icon next toos-senseito install the plugin. -
After installing
Zenarmor, you should see theZenarmormenu in the left sidebar of the OPNsense web interface. -
You will need to complete the
Initial Configuration Wizardfor Zenarmor to be fully operational. After you complete the initial configuration of Zenarmor on OPNsense, you can define Zenarmor policies to protect your network.
Although the preferred method of Zenarmor installation is the web interface, you can also install the plugin using the command line interface via SSH or direct system access.
Features of Zenarmor
Zenarmor is based on a state of the art security technology developed by Sunny Valley Networks. It is a very lightweight yet powerful packet inspection core that can provide a wide variety of enterprise-grade network security functions. Features of Zenarmor are given below.
-
Application Control
-
Cloud Application Control (Web 2.0 Controls)
-
Web Filtering and Security
-
Advanced Network Analytics
-
Real-time Cloud Threat Intelligence based blocking
-
Cloud Centralized management & reporting
-
Encrypted Threats Prevention (All-ports full TLS Inspection (for every TCP port, not just HTTPS) *Coming soon)
-
User-based Filtering and Reporting
-
Active Directory Integration
-
Policy based filtering and QoS
-
Application / Web category based Traffic Shaping and Prioritization
For detailed information about the Zenarmor features, you may view the official product documentation.
2. pfSense® software
pfSense® software is a firewall/router computer software distribution based on FreeBSD. pfSense Community Edition (CE) is a partially open-source version, whereas pfSense Plus is now closed source. pfSense® software is one of the leading network firewalls with commercial-level features.

Figure 4. pfSense® software Appliance
Chris Buechler and Scott Ullrich founded the pfSense® software project in 2004 as a fork of the m0n0wall project, and the first release was in 2006. The name comes from the fact that the software employs the PF packet-filtering tool.
You can install it on a physical computer or a virtual machine to make a dedicated firewall/router for your network. And you can configure the firewall via a web-based interface without needing any knowledge of the underlying FreeBSD system to manage.
To deploy and use the pfSense® software software, no prior knowledge of FreeBSD is required.
In addition to being a powerful, flexible firewalling and routing platform pfSense® software includes a long list of related features. To begin with, you can use pfSense® software to deploy an intrusion prevention system as well as enable VPN access.
It has successfully replaced every major commercial firewall on the market, including Check Point, Cisco PIX, Cisco ASA, Juniper, Sonicwall, Netgear, Watchguard, Astaro, and others, in numerous installations around the world.
In this article, we will cover the following topics.
-
What is pfSense?
-
pfSense® software installation
-
pfSense® software features
What is pfSense?
The pfSense® software Project is a free open source customized distribution of FreeBSD designed for use as a firewall and router that is entirely managed through an intuitive web interface.
pfSense® software is owned by Rubicon Communications, LLC (Netgate) and distributed under an open source license.
It has proven to be effective in countless installations ranging from single computer protection in small home networks to thousands of network devices in large corporations, universities, and other organizations.
pfSense® software is available as a hardware device, virtual appliance, and downloadable binary (community edition).
How to Install pfSense?
pfSense® software can be installed and configured on either virtual or physical servers. For more information about the installation of the pfSense® software firewall, please refer to pfSense® software Guide.
Features of pfSense
The pfSense® software comes with a web interface for configuring all of the included components. There is no requirement for any UNIX knowledge, no use of the command line, and no need to manually edit any rule sets. Users who are familiar with commercial firewalls adapt quickly to the web interface.
Because of its long history, pfSense® software may have the most extensive documentation and one of the largest user communities, with tutorials and videos posted on its official support channels as well as elsewhere on the web. The distro's commercial hosts also provide paid training courses to help you get the most out of your pfSense® software deployment.
The main advantage of pfSense® software is the ongoing support. The development team provides regular updates and support for this software. The pfSense® software package system allows for additional expansion without adding bloat or potential security vulnerabilities.
On a high-level, some of the worth mentioning pfSense® software features are:
-
Firewall: IP/port filtering, limiting connections, layer two capable, scrubbing
-
State table: by default all rules are stateful, multiple configurations available for state handling,
-
Multi-WAN load balancing: use more than one internet connection.
-
VPN (a virtual private network): support IPsec and OpenVPN
-
Server load balancing: inbuilt LB to distribute the load between multiple backend servers
-
NAT (Network address translation): port forwarding, reflection
-
HA (High-availability): failover to secondary if primary fail
-
Reporting: Keep historical resources utilization information
-
Monitoring: real-time monitoring
-
Captive portal
-
Dynamic DNS: multiple DNS clients are included
-
DHCP & Relay ready
-
Disable filtering: You can completely disable the firewall filter if you want to turn your pfSense® software into a pure router.
-
User authentication
-
Content filtering and proxy filtering capabilities
-
GeoIP blocking
-
Anti-spoofing
You also have an option to install the following packages with one click.
-
Services: iperf, widentd, syslog-ng, bind, acme, imspector, git, dns-server
-
Networking: netio, nut, Avahi
-
Routing: frr, olsrd, routed, OpenBGPD
-
Security: a stunner, snort, tinc, nmap, arpwatch
-
Monitoring: iftop, ntopng, softflowd, urlsnarf, darkstat, mailreport
We strongly recommend you to install Zenarmor on your pfSense® software firewall so that you have an additional layer of security for your network infrastructure. By installing the Zenarmor on your pfSense® software node you can get benefits of using web filtering and application controls capabilities. For more information about how to install and configure Zenarmor on your pfSense® software firewall, please refer to our official documentation.
3. IPFire
IPFire is an easy-to-use, open-source stateful firewall that is built on top of Netfilter and trusted by thousands of companies worldwide. It is designed with a lot of modular considerations and is highly flexible. It has great customization flexibility. You can use it not only as a firewall, but also as a proxy server, or VPN gateway depending on your configuration. Another important feature it has is built-in IDS to detect attacks. Moreover, the Guardian plugin provides you to implement automatic prevention.

Figure 2. IPFire Web GUI
In this article, we will cover the following topics briefly.
-
What is IPFire?
-
IPFire features
-
IPFire installation
What is IPFire?
IPFire is a fortified, flexible, cutting-edge Open Source firewall based on Linux. Its ease of use, high performance in all scenarios, and extensibility make it suitable for all users.
IPFire began as a fork of IPCop and has been completely rewritten on the basis of Linux From Scratch since version 2. It allows the installation of add-ons for the addition of server services, which can be extended into a SOHO server.
You can deploy IPFire on a wide variety of hardware, including ARM devices such as the Raspberry Pi.
How to Install IPFire?
In less than half an hour, you may simply install your IPFire firewall using a guided console conversation. To learn how to install the IPFire firewall, you may refer to the IPFire Installation Tutorial written by Sunny Valley Networks.
Features of IPFire
In this subsection, we will first discuss the most valuable features of IPFire deeply and then list all features including the additional services.
One of the most significant advantages of the IPFire is its modular structure, which allows you to run it with exactly what you need and nothing more. The package manager makes it simple to configure all features and update them. IPFire has been designed to be adaptable to any existing security architecture.
The primary goal of IPFire is security. Its simple-to-configure firewall engine and Intrusion Detection System keep hackers out of your network. To manage risks inside the network and have a custom configuration for the specific needs of each segment of the network, the network is split into various zones with different security policies in the default configuration. Each segment of the IPFire configuration is color-coded as follows.
-
Green: Trusted zone. This is where all regular client computers reside. Clients can access all other network segments without restriction.
-
Red: Untrusted Zone/Internet. Unless specifically configured by the administrator, no Internet access is permitted to pass through the firewall.
-
Blue: The wireless part of the local network. The clients on this network segment must be explicitly allowed before they may access the network
-
Orange: the demilitarized zone (DMZ). Any publicly accessible servers are isolated from the rest of the network to limit the scope of a security breach.
Regular updates keep IPFire secure against security flaws and new attack vectors.
IPFire employs a Stateful Packet Inspection (SPI) firewall based on Netfilter, the Linux packet filtering framework. It filters packets quickly and achieves throughputs of several tens of Gigabits per second.
IPFire can be enhanced to include a virtual private network (VPN) gateway, which uses an encrypted link to connect remote people and places to the local network.
The Intrusion Detection System (IDS) of IPFire analyzes network traffic to detect exploits, leaking data, and other suspicious activity. When an attacker is detected, alerts are raised and the attacker is immediately blocked.
IPFire can be run as a virtual machine on the following hypervisors:
-
KVM/Qemu
-
Xen (paravirtualized and fully virtualized mode)
-
VMWare (Workstation, vSphere, ESXi)
-
Virtualbox
IPFire has a web-based management interface for changing settings. You can configure your network to suit your specific requirements, whether you need basic firewall protection or advanced logging and graphical reports.
The distro can also be fleshed out with a useful set of add-ons, such as Guardian, to provide it with additional functionality.
Main features of IPFire are listed below.
-
Intrusion Detection system
-
Wake-on-LAN
-
Web Proxy
-
IDS
-
VPN termination
-
QoS
-
Proxy and Relay for various protocols
-
URL filtering/Content filtering
-
DNS forwarding
-
Full-fledged web proxy
-
Multi-deployment facilitation such as a VPN gateway, a proxy server, or a firewall.
You can enhance IPFire to include supplemental network services such as:
-
Routing the traffic to the Tor network or running a relay (TOR)
-
Monitoring services like Nagios/NRPE
-
Samba file server
-
CUPS print server
-
Mail server system including Postfix, SpamAssassin, ClamAV, Amavis
-
WIFI Access-Point (HostAPD)
-
Streaming server
-
vsftpd ftp server
-
Asterisk
-
TeamSpeak
-
Video Disk Recorder (VDR)
4. Untangle NG Firewall
Untangle NG Firewall is a Debian-based network gateway that includes pluggable modules for network security applications such as intrusion prevention, web filtering, spam filtering, anti-virus, anti-spyware, VPN, firewall, and others.
Untangle NG Firewall removes the complication from network security and saves administrators time. This firewall is designed to strike a balance between performance and protection, policy and productivity. It provides you a simple deployment and administration, with a user-friendly web-based GUI.

Figure 3. Untangle NG Dashboard and Appliances
It is an excellent fit for a wide range of organizations looking for a powerful, cost-effective network security solution capable of handling any IT challenge from small, remote offices to diverse school campuses and large, distributed organizations. The NG Firewall has various software modules that can be enabled or disabled based on individual needs. Untangle NG's basic network functions are supplemented with free and paid applications that add additional functions and capabilities, all managed via a web-based user interface.
Basically, you can easily install this firewall system on any hardware or virtual machine, or buy a device with NG Firewall preinstalled.
Untangle NG Firewall is available in the following deployment options:
-
Hardware Appliance: An Untangle network appliance with NG Firewall preinstalled.
-
Software Appliance: An installable version of NG Firewall for most x86 based devices.
-
Virtual Appliance: A virtual appliance optimized for VMware deployments in private cloud infrastructure.
-
Cloud Appliance: A virtual appliance available for Amazon Web Services or Microsoft Azure.
In this article, we will cover the following topics briefly.
-
What is Untangle NG Firewall?
-
Untangle NG features
What is Untangle NG Firewall?
Untangle NG is next-generation firewall/UTM software that combines everything your network requires to stay healthy on a single box: URL and spam filtering, virus scanning, VPN connectivity, multi-WAN failover capability and much more.
Untangle NG consists of a growing ecosystem of technology applications, or 'apps.' This approach makes Untangle NG Firewall extremely easy to use by greatly simplifying the UI and tailoring it to each deployment.
Features of Untangle NG Firewall
In this subsection, we will first discuss the most valuable features of Untangle NG briefly and then list all features.
-
Simplicity: Network management and ensuring that everything is adequately protected can be a time-consuming and expensive task. Untangle NG Firewall simplifies network security by providing a single, modular software platform that adapts to your changing requirements. Untangle NG Firewall has a browser-based, user-friendly, and responsive interface that allows you to quickly gain visibility into network traffic. It provides a comprehensive, enterprise-grade network security platform for organizations of any size, from content filtering to advanced threat protection, VPN connectivity to application-based shaping for bandwidth optimization.
-
Comprehensive Security: The NG Firewall offers comprehensive security at the gateway by proactively preventing malware, hacking attempts, phishing schemes, and other threats from reaching clients.
-
Dashboard: On the dashboard, you can see the network activity at a glance, ensuring compliance with full event logs, and receive notifications of network anomalies or unusual user behavior via alert rules.
-
Secure Connectivity: It also helps you to maintain user and data security regardless of location or level of access.
-
Web Caching: Web Cache is used to improve browsing performance by caching and serving static elements locally. As a result, bandwidth is reduced and page loading times are shortened. Web Cache improves browser responsiveness, which leads to higher user satisfaction.
-
Bandwidth Control: Bandwidth Control aids in the tracking and monitoring of bandwidth usage. It aids in the identification of problematic apps, websites, and users. Bandwidth control assists the user in managing bandwidth allocation.
-
Reports: Untangle Reports is one of Untangle's best and most recent features. You can add your own reports. Reports provide users with statistical data and network activity. It generates reports on Applications, Web Usage, Web Filters, and other topics. You can send personalized reports via email or fax.
All of the Untangle NGs features are listed below.
-
WireGuard VPN
-
Threat Prevention
-
Web Filter
-
SSL Inspector
-
Live Support
-
Policy Manager
-
Branding Manager
-
WAN Failover
-
WAN Balancer
-
IPsec VPN
-
Application Control
-
Web Cache
-
Bandwidth Control
-
Virus Blocker
-
Spam Blocker
-
Directory Connector
-
Web Monitor
-
Application Control Lite
-
Virus Blocker Lite
-
Phish Blocker
-
Intrusion Prevention
-
Firewall
-
OpenVPN
-
Reports
-
Spam Blocker Lite
-
Captive Portal
-
Ad Blocker
-
Tunnel VPN
5. iptables
Iptables is a well-known utility and best open source firewall for Linux applications that gives a system administrator the ability to configure and analyze network statistics. It is a terminal based, effective and customizable firewall software that is widely used among the experienced Linux administrators to protect their servers.
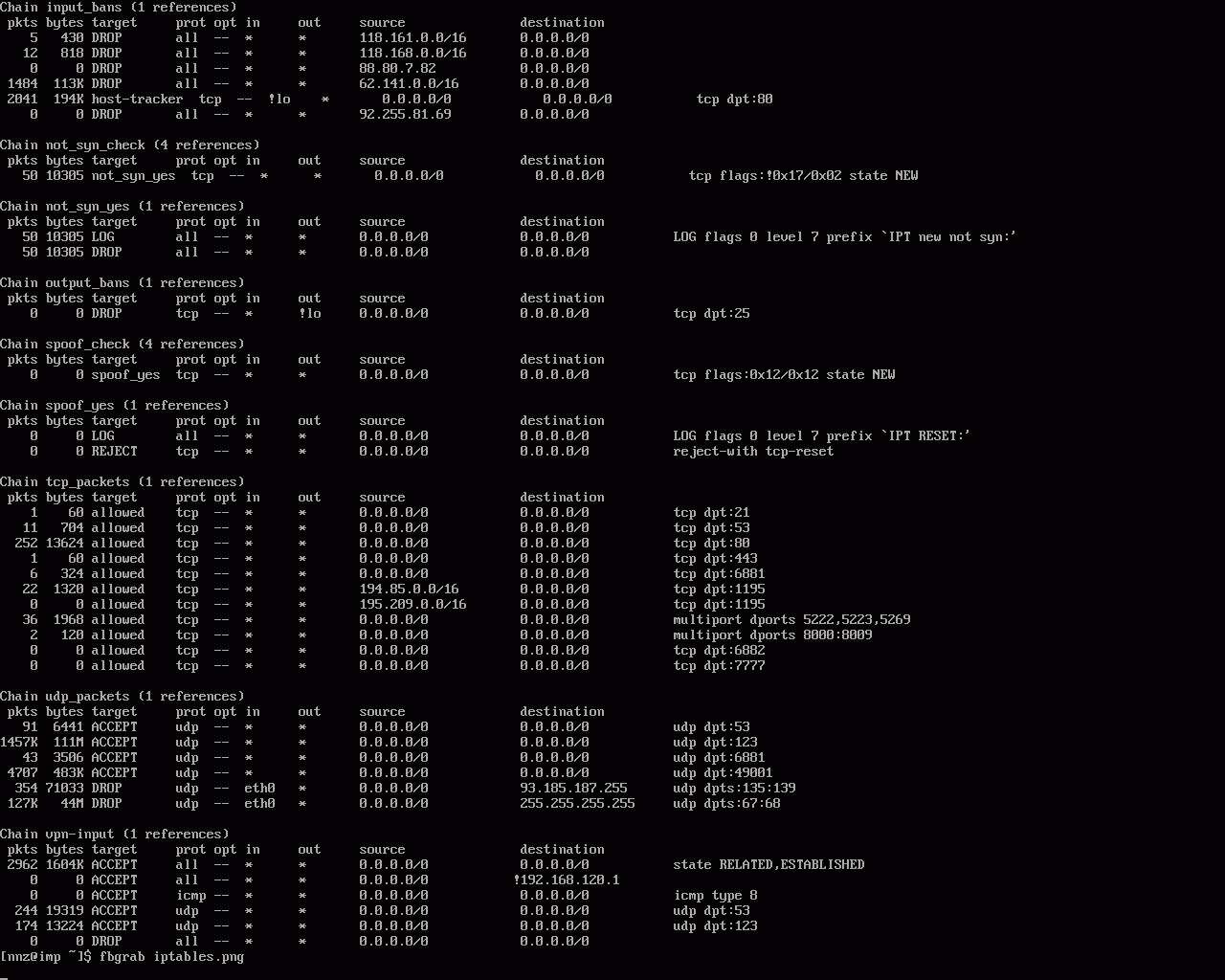
Figure 5. Iptables list output
Iptables replaced ipchains, and nftables is iptables' successor. Nftables allows for much more flexible, scalable and performance packet classification.
When an iptables-enabled system receives a packet, it searches its rule list for a match. If it cannot find one, it falls back on the default action.
In this article, we will cover the following topics.
-
What is iptables?
-
iptables installation
-
iptables features
What is Iptables?
Iptables is a user-space utility tool that allows an administrator to configure the IP packet filter rules of the Linux kernel firewall, implemented as various Netfilter modules. Netfilter is the firewall framework on Linux, and iptables is the utility that manages and controls Netfilter. Iptables can be used to filter incoming and outgoing network packets as well as route them. The filters are organized in different tables, which contain chains of rules for how to treat network traffic packets.
Currently, different kernel modules and programs are used for different protocols:
-
iptables for IPv4
-
ip6tables for IPv6
-
arptables for ARP
-
ebtables for Ethernet frames.
How to Install Iptables?
Iptables almost always comes pre-installed on any Linux distribution. To update/install it, just retrieve the iptables package. Before installing the iptables, You must also uninstall any other firewall management utilities like UFW on your firewall.
On a Debian based or Ubuntu server you can run the following commands to install iptables.
sudo apt-get update
sudo apt-get install iptables
The default configuration file for iptables can be found in /etc/sysconfig/iptables. You can modify it with the text editor of your choice.
On a Red Hat Enterprise Linux (RHEL) 7/8 and CentOS 7/8 you can run the following commands to install iptables.
-
Run the following commands to stop and mask the firewalld service that you don't want to use:
systemctl stop firewalld
systemctl mask --now firewalld -
Install the iptables-services package (if it is not already installed) by running the following command:
yum install iptables-services -y -
Enable the service to start at boot time by running the following commands:
systemctl enable iptables
systemctl enable ip6tables
Features of Iptables
iptables consists of the following 3 main components.
-
chains: There are 5 chains in iptables and each is responsible for a specific task:
Input: Used to manage incoming packets/connectionsOutput: Outgoing packet after it has been created/processed.Forward: Forwards incoming packets from their source to destination (routing).Prerouting: After the packet enters the network interface.Postrouting: Before the packet leaves the network interface after the routing decision has been made.
-
tables: A table is a collection of chains that serves a particular function. There are five types of tables in iptables:
Filteris responsible for filtering and restricting the packets to/from our computer.Natis responsible for Network Address Translation.MangleTable is used to modify packet headersRawdeals with the raw packet as the name suggests. Mainly this is for tracking the connection state.Securityis responsible for securing your computer after the filter table. Which consists ofSELinux.
-
targets: Targets specify where a packet should go. This is decided using either iptables' own targets: ACCEPT, DROP, REJECT, or it's extensions' target which are 39 at the moment and the most popular ones are DNAT, LOG, MASQUERADE, REJECT, SNAT, TRACE and TTL.
ACCEPT: Stop processing and let the packet flow.REJECT: Drop the packet by giving feedback.DROP: Stops processing at the current chain and drops the packet.LOG: Similar to ACCEPT, however, it is logged to the /var/log/messages.
Iptables allows the system administrator to define tables containing chains of rules for the treatment of packets. Packets are processed by sequentially traversing the rules in chains. Every network packet arriving at or leaving from the computer traverses at least one chain. Incoming packets are analyzed at each chain and are tested against a set of rules. If a rule is matched, the target is set.
The features and attributes of the iptables firewall are as follows:
-
It has packet filter rulesets that allow for content listing
-
It employs a packet header inspection approach, which makes the firewall extremely fast.
-
Editable packet filter rulesets enable the administrator to add, modify, or remove a firewall configuration rule
-
listing/zeroing per-rule counters of the packet filter ruleset
-
It can be used for data file backup and restoration in conjunction with the firewall's functionality.
Iptables can only provide you with a L4 firewall/second generation firewall features to protect your networks. Since iptables is not a next generation firewall and does not have application layer/L7 filtering capabilities, we strongly recommend you to use Zenarmor on your iptables firewall. For more information about how to install Zenarmor on your Linux firewall, please refer to Zenarmor official documentation.
6. VyOS
VyOS is a router platform that is entirely open-source and designed for enterprise use. In 2013, VyOS was established as a community derivative of the defunct Vyatta Core project with the objective of.
VyOS is a unified management interface that integrates the GNU/Linux operating system with a diverse array of open networking utilities. It maintains the principles of free and open-source software by providing a configurable scripting library and an HTTP API, in addition to a command-line interface that is reminiscent of hardware routers.
Figure 6. VyOS Dashboard
Features
The following are the features of VyOS:
-
Stateful firewalls, zone-based firewalls, and all forms of source and destination NAT
-
Routing features include BGP (IPv4 and IPv6), OSPF (v2 and v3), RIP and RIPng, and policy-based routing.
-
VPN, IPsec, VTI, VXLAN, L2TPv3, L2TP/IPsec, and PPTP servers, tunnel interfaces (GRE, IPIP, SIT), and OpenVPN in client, server, or site-to-site mode. WireGuard is a VPN feature of VyOS.
-
VRRP for IPv4 and IPv6, with the capacity to implement custom health checks and transition routines; ECMP, stateful load balancing as a high-availability solution
-
Network services such as DHCP and DHCPv6 server and relay, IPv6 RA, DNS forwarding, TFTP server, web proxy, PPPoE access concentrator, NetFlow/sFlow sensor, and QoS are available.
Platforms
VyOS is compatible with a diverse array of virtualization systems, such as KVM, Xen, Citrix XenServer, VirtualBox, VMware, and Microsoft Hyper-V, as well as bare-metal x86-64 servers. The images include paravirtual drivers to optimize performance.
Google Cloud Platform, Microsoft Azure, and Amazon Web Services all offer it.
Pricing
VyOS is an entirely open-source platform, allowing anyone to audit, create customized images, contribute to the codebase, and construct a toolchain.
7. Endian Firewall Community (EFW)
Endian Firewall Community (EFW) is a security software application for the home that is based on Linux and can be used to transform any underutilized hardware device into a completely functional Unified Threat Management (UTM) system. Endian Community was established with the objective of simplifying security and aiding in the safeguarding of residential networks by utilizing open-source software.
Figure 7. Endian Firewall CE dashboard
Features
The following services are available through Endian in the context of network security and administration, providing a comprehensive set of options for optimizing and protecting your network:
- VPN (SSL & IPSec): Our VPN connection is both secure and user-friendly, enabling your staff to access remote locations and connect multiple offices.
- A Robust Firewall: Ensure that your network is safeguarded from Internet risks while simultaneously enabling appropriate access to internal and external resources.
- Intrusion Prevention (IPS): A fortified defense that analyzes traffic flows to safeguard your network from both internal and external threats.
- Antivirus: At the gateway, it detects and prevents infections in both web and email traffic. Safeguard your network from the most recent Internet attacks.
- Email Security: Ensure that your network is free of spam, phishing, and other harmful email.
- Centralized Management: The Endian Management Center (EMC) provides the ability to centrally manage your Endian Appliances.
- Multi-WAN (Wide Area Network) (with Failover): By connecting multiple Internet connections to your network, it will become more dependable. It is feasible to implement it in a fundamental failover configuration or simultaneously.
- Quality of Service (QoS): Prioritize business-critical applications, including VoIP, web, and email, by managing your network bandwidth usage.
- Reporting: Access real-time and historical data for all of your critical network traffic, including web usage reports for the days, weeks, and months.
Endian Firewall Community provides critical email and web security services by leveraging the capabilities of prominent open-source applications. This resilient solution guarantees a strong defense for your network against online hazards. Furthermore, EndianOS UTM provides centralized and secure access to all Endian appliances through its seamless integration with the Endian Network. This integration offers a comprehensive approach to protecting your digital infrastructure by streamlining network management and improving overall security.
Platforms
Endian may be implemented in three distinct environments.
-
Appliance Hardware: A wide range of specially designed devices that are compatible with UTM software to meet security requirements, ranging from industrial facilities and branch offices to large networks.
-
Virtual Appliance: Virtual appliances include VMware, Hyper-V, Xen/XenServer, and KVM.
-
Appliance Software: It is possible to convert your equipment into an Endian UTM appliance that is fully functional.
Pricing
Endian Firewall Community is a free and open-source Unified Threat Management (UTM) solution that can be employed to safeguard small businesses and residential networks. It provides an extensive array of capabilities, such as malware protection, intrusion detection and prevention, web filtering, and packet filtering. Endian Firewall Community is user-friendly and manageable, and it can be deployed on a diverse range of platforms, such as on-premises, cloud, and virtualized environments.
EndianOS UTM is a commercial UTM product that is intended for enterprise use. It provides a more exhaustive array of features than Endian Firewall Community, such as advanced application control, content filtering, and reporting capabilities. EndianOS UTM is more scalable and can be deployed on larger networks.
Price information for EndianOS UTM is available upon request. Nevertheless, it is frequently pricier than Endian Firewall Community, which is open-source and free.
Endian Firewall Community is a free and open-source UTM solution; therefore, it does not include official technical support. Nevertheless, the Endian Firewall Community forums are home to a robust and engaged community of developers and users who are able to offer assistance.
8. Shorewall
The Shoreline Firewall, which is occasionally referred to as "Shorewall," is a high-level Netfilter configuration utility. Shorewall can be installed on a multifunction gateway/router/server, a specialized firewall system, or a dedicated GNU/Linux system. As a result of its ability to manage "zones" such as the DMZ or a "net" zone, Shorewall is primarily employed in network installations. Subsequently, each zone would establish its set of limitations, which would facilitate the implementation of more permissive standards on the intranet of the workplace while simultaneously restricting Internet traffic.
For instance, you may wish to establish a covert internal network that is accessible only to specific machines, a guest network that is accessible to all, a network that is dedicated to production machines, and a network that can be accessed from computers outside of your Local Area Network (LAN). Shorewall facilitates this process effortlessly.
Features
The following is a list of the features of Shorewall 5.0.
- It is appropriate for a diverse array of gateway, firewall, and router applications.
- It utilizes Netfilter's connection tracing capabilities for stateful packet filtering.
- Central management.
- Specific IP addresses and subnetworks can be blacklisted.
- Support for VPN tunnels that are based on IPsec, GRE, IPIP, and OpenVPN, as well as clients and servers that utilize the PPTP protocol
- Address Verification for Media Access Control (MAC) is accessible.
- Assistance with traffic shaping and control.
- Assistance with firewalls and bridges
- Traffic accounting
- IPv6 Support (Shorewall 5.0.6 and later) is compatible with a diverse array of virtualization solutions, such as KVM, Xen, Linux-Vserver, OpenVZ, VirtualBox, LXC, and Docker (Shorewall 5.0.6 and later).
Advantages
Shorewall is a firewall solution that is both flexible and potent, providing a variety of benefits, such as:
-
Configuration simplicity: Shorewall is relatively straightforward to configure, even for users with limited experience with firewalls. It offers a straightforward and intuitive syntax for establishing firewall rules, and a variety of resources are available to assist users in setting up, including documentation, tutorials, and community support.
-
Adaptability: Shorewall is a highly adaptable firewall solution that can be customized to accommodate a diverse array of network requirements. It is compatible with a diverse array of network protocols and topologies, and it can be seamlessly incorporated with other security tools and services. Shorewall is an excellent option for users who require a firewall solution that is both flexible and potent. Nevertheless, it is crucial to recognize the complexity and learning curve associated with Shorewall.
-
Customization: Shorewall is an excellent option for users who require a firewall solution that can be customized to accommodate the unique requirements of their network. Shorewall is compatible with a diverse array of network protocols and topologies, and it can be seamlessly incorporated with other security tools and services.
Platforms
The following is a list of the deployment alternatives for Shorewall, including hardware requirements, virtualization support, and cloud deployment options.
-
Specialized firewall systems: Shorewall can be implemented on specialized firewall systems, such as hardware appliances or virtual devices.
-
Standalone GNU/Linux systems: Shorewall can be deployed on any standalone GNU/Linux system. The hardware requirements for a standalone Shorewall deployment are relatively modest; however, they may differ depending on the specific distribution and configuration that is being employed.
-
Multi-function gateway/router/servers: Shorewall can be installed on multi-function gateway/router/servers. Routing, firewall protection, and NAT are among the network services that these systems typically offer. The firewall functionality of these systems can be managed using Shorewall.
Integration
Shorewall optimizes traffic processing by employing Netfilter's connection monitoring capabilities for stateful packet filtering.
In order to centralize and analyze Shorewall logs, it is possible to integrate Shorewall with a syslog server. This can assist organizations in identifying and responding to security hazards in a more timely and effective manner.
Pricing
Shorewall is free software, which entitles you to share and/or modify it in accordance with the GNU General Public License, version 2, or (at your discretion) any successor version issued by the Free Software Foundation.
9. Smoothwall Express
Smoothwall is a compilation of Internet security technologies that safeguard your network and users from external hazards. Smoothwall Express is a firewall solution that is based on Linux. A fortified subset of the GNU/Linux operating system is included in Smoothwall, eliminating the necessity to install a separate operating system. Smoothwall is intended to be user-friendly, featuring a web-based GUI that does not necessitate any prior knowledge of Linux to install or operate.
Smoothwall is a private software company that is headquartered in the United Kingdom. It is a leader in the development of web content filtering, safeguarding, and internet security solutions, in addition to overseeing the SmoothWall open source project.
Smoothwall was initially developed as Smoothwall GPL, an open-source variant that was permissible to redistribute. In November 2001, Smoothwall LTD commenced the sale of a proprietary version that was initially released in August 2000. Smoothwall Express is still accessible today (latest release V3.1 in 2014), but the primary Smoothwall solution is now paid for and utilized by millions of individuals worldwide in both the public and private sectors. Educational institutions and corporations are the primary purchasers of Smoothwall's security and filtering solutions.
The developers of Smoothwall disclosed on August 5, 2021, that they have reached an agreement to sell their investment to Family Zone Cyber Safety, an Australian security firm, for 75.5 million pounds sterling ($142 million in cash). The deferred remainder of the sale price of 10.5 million pounds sterling was paid on September 1, 2021, following the conclusion of the transaction on August 17, 2021.
10. IPCop Firewall
IPCop Firewall is an open-source firewall distribution that is based on Linux and is intended to offer secure and efficient network protection. It is designed to cater to residential users, small offices, and small-to-medium-sized enterprises, and is based on Linux. It provides a user-friendly web interface for monitoring network security and firewall configurations.
IPCop Firewall is a user-friendly and dependable firewall solution that is well-suited for small networks. However, users may now prefer more actively supported alternatives. In recent years, the development of IPCop has halted, and a significant number of users have transitioned to alternative firewall solutions, including pfSense, OPNsense, and IPFire, which provide more active development and updated features.
Features
The primary features of IPCop Firewall are listed below.
- Stateful Packet Inspection (SPI): Enables only legitimate connections by monitoring incoming and outgoing network packets.
- Proxy and Content Filtering: Squid proxy services have been integrated to enhance the efficacy of web browsing and filter web content.
- VPN Support: Facilitates secure remote access through the use of Virtual Private Network (VPN) connections, such as OpenVPN and IPSec.
- Intrusion Detection System (IDS): Utilizes Snort-based IDS to identify and notify administrators of potential network threats.
- Web-based Management Interface: Offers a user-friendly, intuitive web interface that simplifies configuration and management.
- QoS and Traffic Shaping: Enables the prioritization of network traffic to reduce latency and optimize bandwidth usage.
- DHCP and DNS Services: Offers integrated DHCP and DNS services to facilitate network configuration.
- Logging and Reporting: Provides comprehensive reporting tools and detailed logs to monitor network activity and security events.
- Simple Updates and Maintenance: Consistent patches and updates are available to guarantee ongoing stability and security.
Platforms
IPCop is typically implemented on dedicated hardware or virtual devices, transforming a standard PC into a reliable firewall appliance.
What is Open Source Firewall and Why It is Used?
The word open source initially related to open source software (OSS) that is supposed to be publicly accessible. Anyone can examine, alter, and share the open source code.
When a person or organization uses an open source license on his/its original application, they agree to:
-
Make the whole source code of the software publicly available
-
Allow anyone to change, enhance, or re-engineer the code of a software
-
Allow derivative works to be created
-
Allow the application to be used for any purpose the user desires
Open source license provides developers to share their knowledge with each other. The entire open source community benefits from the collective innovation.
The Internet's essential functions are based on open source technologies. A large number of Internet applications are open source too. Large Internet corporations like Facebook and Google have even given the open source community access to some of their private ideas.
Many of the technologies we take for granted today would not have developed if open source licenses had not been available, or would have been locked away behind patent law. The open source movement is responsible for the rapid advancement of technology over the last few decades.
Open source firewall is a firewall which is developed and distributed under an open source license. It protects the network from a threat by filtering the inbound and outbound traffic and ensures network security.
Open source firewalls have all the benefits of open source software described above as well. There is no doubt that you can protect one of your most valuable assets with an open source firewall.
There is a wide range of open-source firewall software to choose from, depending on your level of expertise, the size of the infrastructure to be protected, ease of use, and even whether the firewall has a graphical interface.
In no particular order, this article highlights the best open-source firewalls available. You can easily download and deploy all of these firewalls on any hardware, virtual platform, or cloud. Moreover, many sell them with pre-configured appliances if you like their functions or support and do not want to build your own device.
What are the Benefits of Using Open-Source Firewalls?
In contrast to proprietary firewall solutions, open-source firewalls provide numerous advantages, including cost savings, security transparency, flexibility, community support, vendor independence, reliability, scalability, compliance simplicity, and educational opportunities. Open-source firewalls are an appealing option for organizations that are seeking to develop secure, cost-effective, and customizable network security solutions due to these advantages. Significant benefits of using open-source firewalls are outlined below.:
- Cost-Effectiveness: Open-source firewalls are available for free download and use, which significantly reduces both upfront and ongoing expenses. Organizations can allocate expenditures toward infrastructure, support, and customization instead of licensing fees.
- Transparency and Security: Users have the ability to audit the source code, which reduces the probability of concealed backdoors or vulnerabilities and ensures transparency. The community is actively involved in the review and patching of vulnerabilities, often at a quicker pace than proprietary solutions.
- Learning Opportunities: By directly interacting with the source code and configurations, IT teams can acquire a more profound understanding of firewall technologies. By acquiring a comprehensive understanding of cybersecurity best practices and firewall management, staff can enhance their overall security posture.
- Customization and Flexibility: Users have the ability to modify firewall configurations and features to meet their unique security requirements. Open-source firewalls can be readily integrated with third-party software and other open-source tools, allowing for customized security configurations.
- Vendor Independence: Organizations are not obligated to select hardware and software solutions from a single vendor, which provides them with more flexibility. Users have the ability to switch hardware suppliers or support providers without experiencing substantial disruptions.
- Community Support: Open-source solutions tend to have large and active communities that offer support, documentation, and troubleshooting assistance. The community provides users with forums, resources, and collective knowledge.
- Performance and Scalability: Open-source firewalls are known for their ability to operate efficiently on commodity hardware due to their lower hardware requirements. Organizations can simply scale their firewall solutions in accordance with their evolving security requirements and growth, either horizontally or vertically.
- Reliability and Stability: Open-source firewalls are frequently subjected to extensive testing by the community and deployed in a variety of environments, which contributes to their reliability. Numerous open-source firewalls (e.g., pfSense, OPNsense, IPFire) have a lengthy history of successful deployments in enterprise and SME environments.
- Easier Auditing: Open-source firewalls simplify the process of complying with regulatory standards by allowing auditors to directly access and examine source code. The openness and visibility of firewall configurations and operations enable organizations to more effectively demonstrate compliance.
How Secure are Open-Source Firewalls?
If effectively configured, routinely updated, and actively managed, open-source firewalls can be highly reliable and secure. Although they offer transparency, flexibility, and cost savings, the security efficacy of these systems is ultimately contingent upon the user's capacity to maintain and configure them correctly.
The source code of open-source firewalls is publicly accessible, enabling security specialists and the community to promptly identify, audit, and resolve vulnerabilities. The duration of vulnerability exposure is reduced by the prompt provision of remedies and security updates by active communities. Additionally, users have the ability to customize firewall rules and configurations to meet their unique security needs, thereby granting them more control over their network security.
However, open-source solutions may not have official support channels, which could result in delays in critical scenarios (although some open-source firewall projects offer paid support options).
What are the Challenges of Open-Source Firewalls?
Despite the fact that open-source firewalls offer cost savings, transparency, and flexibility, organizations must meticulously evaluate these obstacles. The primary challenges of using open-source firewalls are as follows.
- Limited Support and Documentation: The majority of open-source firewalls rely on community forums, documentation, and online resources, which may not be sufficient for immediate, mission-critical support. In contrast to proprietary solutions, open-source firewalls generally do not provide dedicated vendor support, which can result in a delayed resolution of critical issues.
- Complexity and Learning Curve: Open-source firewalls frequently necessitate advanced technical expertise and intimate familiarity with command-line interfaces, networking concepts, and firewall configuration techniques. In order to effectively administer and configure open-source firewalls, administrators may require additional training or experience.
- Maintenance and Updates: Administrators are forced to manually deploy security upgrades, patches, and updates, necessitating ongoing monitoring and maintenance efforts. Particularly for organizations with inadequate IT personnel, routine maintenance and updates can necessitate substantial time and resources.
- Regulatory and Compliance Concerns: Open-source firewalls may not meet the legitimate certifications or compliance standards that are mandated by specific industries or regulatory bodies, which can complicate the process of meeting specific regulations for organizations.
- Limited Advanced Security Features: Open-source firewalls may not have the same advanced security features and capabilities as commercial firewall solutions, such as deep packet inspection, advanced threat detection, or integrated intrusion prevention systems (IPS).
- Security Risks and Vulnerabilities: Despite the fact that the open-source community is actively involved in the identification and resolution of vulnerabilities, there may be delays in the release of patches or updates, resulting in systems being exposed for extended periods. The risk of misconfigurations is elevated by the complexity of open-source firewall configuration, which may introduce security vulnerabilities.
- Compatibility and Integration Issues: Open-source firewalls may not seamlessly integrate with existing proprietary infrastructure, tools, or security products, necessitating additional customization and integration efforts. The open-source firewall ecosystem is subject to frequent changes that may result in compatibility issues with third-party software or hardware.
- Scalability and Performance: In high-demand or enterprise environments, certain open-source firewalls may not scale efficiently, which could potentially affect network performance. In order to achieve optimal performance, open-source firewall solutions may necessitate substantial hardware resources, which may result in an increase in operational costs.
- Reliance on Third-Party Solutions: Organizations may require the integration of supplementary third-party tools to accomplish comprehensive security, which may result in an increase in complexity and management overhead.
Are Open-Source Firewalls Right for Your Business?
You should evaluate your company's particular needs, capabilities, and regulatory environment carefully to ascertain whether an open-source firewall fits your business goals. A commercial firewall solution could be more appropriate if your company lacks the required technical knowledge or prefers guaranteed vendor-backed support. Open-source firewalls are extremely effective, cost-efficient, and configurable solutions for enterprises with the required knowledge and resources. They are often preferred by consumers seeking freedom and customization, as well as by small enterprises aiming to save licensing expenses.
