Comprehensive Guide to Port Mirroring: Purpose, Benefits, Setup, and Beyond
Packet capture is one of the most helpful techniques available to network engineers, but in order to perform it, you'll need to learn how to use a common technique called port mirroring.
Because your switch may forward copies of passing traffic, you can capture packets without purchasing any specialized equipment. Port mirroring is the name of this procedure.
A TAP (test access point) is a hardware component that is necessary for packet capture. Fortunately, you already have switches and hubs that direct all of your network traffic. Use your current network infrastructure and port mirroring to quickly and easily gain visibility without adding any new hardware. Both the real network and virtual networks running on virtual computers can be used for this. The process of capturing traffic via your network equipment is known as "port mirroring". In many usage scenarios, network packet broker capability can be added to port mirroring to filter unwanted or unnecessary traffic or aggregate the traffic for specific centralized network analysis tools.
Through the use of a technology called port mirroring, you can connect a network analyzer, security appliance, or troubleshooting tool to one port of a LAN switch to watch the traffic on one or more other ports. For example, network performance research, security audits, intrusion detection, or protocol testing can all benefit from port mirroring. Port mirroring does, however, have some possible disadvantages that can impair the functionality and dependability of your LAN switches. We explore port mirroring in this post, including what it is, how it functions, what it excels at, its limitations, and the best ways to employ it. As a result, the following questions have answers:
- What is Port Mirroring?
- Why is Port Mirroring Used?
- What are the benefits of Port Mirroring?
- What are the Drawbacks and limitations of Port Mirroring?
- How does Port Mirroring work?
- How do I configure port mirroring?
- Port Mirroring Best Practices
- How does Port Mirroring compare to other monitoring methods like Network Taps?
- What are the different types of Port Mirroring?
- What are some real-world applications and scenarios for Port Mirroring?
- What tools and solutions are available for network analysis using Port Mirroring?
- What is the difference between Port Mirroring and Traffic Mirroring?
- How can Port Mirroring impact security and network traffic analysis?
What is Port Mirroring?
A network switch or router can utilize port mirroring to send copies of network packets viewed on one set of specified ports (source ports) to other sets of specified ports (destination ports). Additionally, port mirroring is frequently used for network appliances, including intrusion detection systems, passive probes, and real user monitoring (RUM) technologies, which are used to assist application performance management (APM), that need to monitor network traffic. The packets can be watched and studied with port mirroring enabled. Port mirroring is extensively used; for instance, network engineers can use it to examine and debug data or identify problems on their networks without affecting the ability of the network devices to process packets. In order to preserve a healthy network environment, the network administrators can gather pertinent data from port mirroring and evaluate network behaviors.
The idea behind port mirroring is rather straightforward. A switch's configuration allows you to set aside one port. The switch is then set up to "mirror" all incoming traffic to the designated port. Every time a packet is processed by the switch, a copy is made and sent to whatever is attached to the aforementioned port. Typically, some type of specialized system will be installed to keep track of the traffic on that switch.
Why is Port Mirroring Used?
Depending on the design requirements, port mirroring is advantageous to employ in a variety of network scenarios, including local area networks (LAN), virtual local area networks (VLAN), and wireless local area networks (WLAN). By helping with monitoring, examining, spotting, and then troubleshooting network anomalies, it improves network visibility.
In order to transfer a copy of network packets observed on one switch port (or an entire VLAN) to a network monitoring link on another switch port, port mirroring is employed on network switches. This is frequently used to transmit traffic to programs that analyze traffic for things like monitoring compliance, enforcing rules, discovering intrusions, and other things.
Port mirroring is a tool used by network administrators and engineers to investigate, debug, and diagnose network problems. It assists administrators in closely monitoring network performance and warns them when issues arise. On a single or a number of interfaces, it can be used to mirror either inbound or outbound traffic (or both).
What are the Benefits of Port Mirroring?
The advantages of port mirroring are outlined below:
- Port mirroring is more cost-effective, straightforward to set up, simple to use, and does not interfere with regular network operations because single ports or many ports (selectively) can be monitored using a standard network switch (without the need for any additional components).
- Port mirroring is especially useful when your network configuration is limited by physical space or when you might need to monitor a VLAN for a brief period of time.
- You only need to change the configuration of your switch, not physically install or remove gear inside a cage. Port mirroring is a tempting option for businesses making their initial forays into network observability due to its simplicity of implementation and lack of upfront investment.
- On your network, port mirroring is essentially undetectable. If you add a dedicated network tap, you'll have another device to support and maintain.
- Dedicated network taps have a low failure rate, but they could still go wrong. A switch is no more likely to fail than any other switch when port mirroring is enabled.
- Port mirroring is compatible with numerous switches. Every switch you want to monitor requires the installation of a device similar to a network tap.
- For network administrators and engineers, port mirroring can offer a variety of benefits, including helping to troubleshoot network problems like packet loss, latency, or misconfigurations.
- Additionally, it can be used to track network performance, such as bandwidth usage, traffic patterns, or service quality.
- By spotting malicious activity, stopping data breaches, or enforcing policies, port mirroring can be used to increase security.
- By imitating and confirming the behavior of mirrored ports, it can be used to test network protocols, including new applications, standards, or features.
What are the Drawbacks and Limitations of Port Mirroring?
Port mirroring has some significant problems despite being easier and less expensive to set up. The drawbacks of port mirroring are listed below:
- The definition of true egress mirroring states that it must replicate the precise number of copies and packet modifications that left the egress-switched port. Because port mirroring uses up switch resources like CPU, memory, or bandwidth, it may have a negative effect on the performance and dependability of the network. Errors, drops, and delays may result from this.
- Port mirroring exposes the network to unauthorized access, interception, and tampering by replicating and sending traffic that could contain sensitive or regulated information.
- By altering or interfering with the traffic that is being reflected, port mirroring can impair network accuracy by distorting measurements and changing outcomes. The validity and dependability of the network analysis, monitoring, or testing may suffer as a result.
- It's possible that complete packet capture and storage will cause data confidentiality issues. Even though the majority of the data moving through your network will be encrypted, not all internal traffic will be if it is going to websites outside your company. The mail traffic around your network will not be encrypted by default unless your company has chosen to provide additional protection for emails.
- There is less chance of performance degradation when only the packets that require analysis are mirrored. Mirroring traffic from many ports may cause the output interface's capacity to be exceeded. The overflow packets are then deleted. Therefore, it is advised to pick certain interfaces and refrain from utilizing all terms in order to reduce the volume of duplicated traffic. Additionally, you can set a firewall filter to limit the traffic that is sent to the mirroring instance by limiting the amount of traffic that is reflected.
- Some network observability objectives are more challenging to accomplish due to the mirrored packets' lower priority. For instance, port mirroring might not be a suitable fit for your goals if your network observability objectives involve things like lowering network jitter or latency. This is because it may be more challenging to identify and fix those time-sensitive faults as a result of the delay in delivering mirrored packets.
- Resources are needed for either physical or virtual appliances. These can be expensive in terms of hardware and (for commercial solutions) software licenses. Because of this, it is typically only financially feasible to implement port mirroring at specific locations within the network.
- The deployment of lightweight host-based monitoring agents that export packet capture statistics obtained on servers along with open-source proxy servers results in a highly scalable and cloud-friendly solution.
How Does Port Mirroring Work?
On a network switch or router, port mirroring is used to send copies of network packets viewed on specific ports (source ports) to additional ports (destination ports). The packets can be watched and studied with port mirroring enabled.
Most LAN switches, either in terms of hardware or software, enable port mirroring as a function. By using port mirroring, you may set up one or more source ports, the ports you want to watch, and one or more destination ports, the ports you want to use to send the reflected traffic. You can mirror traffic from a single port, a group of ports, a VLAN, or the entire switch, depending on the switch model and settings. You can decide whether to mirror egress, ingress, or both types of traffic. Depending on the network architecture and switch capabilities, port mirroring can be done on a single switch or across multiple switches.
Based on various working ranges of mirroring, local and distant port mirroring are two forms of port mirroring. They function according to different precepts.
The most fundamental type of mirroring is local port mirroring. The same network device that hosts the destination ports also hosts all of the source ports. Local port mirroring allows the network switch to send a copy of the packet from the source port (Eth 1/1) to the destination port (Eth 1/2), as seen in the Figure below. The packet can then be monitored and analyzed by the monitoring device attached to the target port.

Figure 1. Local Port Mirroring
When it comes to remote port mirroring, the source ports and the destination ports are not on the same device. Figure 2 depicts a switch with the source port (Eth 1/3) and another switch to the destination port (Eth 1/3). Through the uplink connection made possible by the port (Eth 1/4) on the two switches, the source port transfers the packet copy to the destination port. As a result, local port mirroring can enable device-wide data monitoring and analysis.
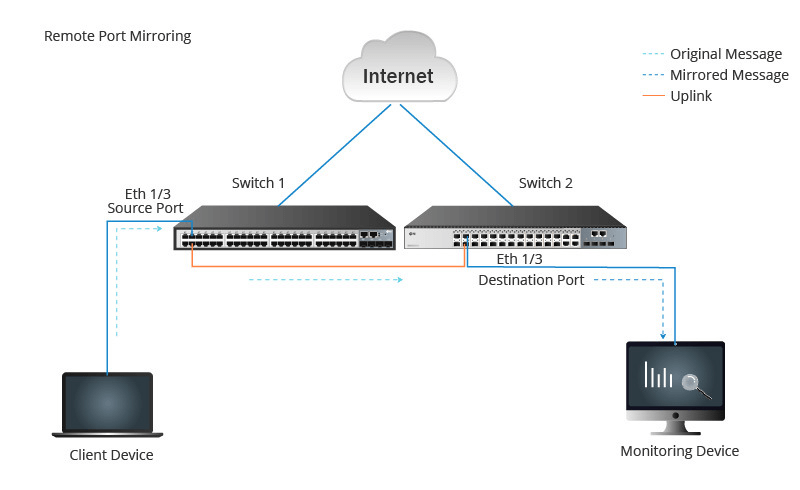
Figure 2. Remote Port Mirroring
How do I Configure Port Mirroring?
There are a few crucial factors to think about before learning how to establish port mirroring, and we can list them as follows:
- In local port mirroring, the configuration is activated after designating one port as the source port and another as the destination port.
- Only one source port may be included in a mirrored group, although there may be one or more destination ports.
- A port cannot be a member of more than one mirroring group if it has been designated as the source port in one of them.
- Applying STP, RSTP, or MSTP to the destination port is not advised because doing so could cause the device to malfunction.
Making sure the network equipment (whether a switch or router) supports port mirroring is a must before setting it up. Choose either a local port mirroring configuration or a distant port mirroring configuration.
Steps for configuring local port mirroring are given below:
- Establish a VLAN.
- Include both the source and destination ports in the VLAN.
- Set up the IP address.
- On the destination port, set up port mirroring, then duplicate the packet from the source port to the destination port.
Steps for configuring remote port mirroring are given below:
- Build a global schema with the source port.
- On one switch, configure the uplink port.
- Create a global schema with a destination port.
- Set up the uplink port on an additional switch.
Port Mirroring Best Practices
Port mirroring may be a very helpful tool if utilized properly. Nevertheless, in order to make the most of this method, it is crucial to comprehend how it operates, its advantages and difficulties, as well as best practices for maximizing it. Here are some best practices to remember if you're just getting started with port mirroring:
- Recognize the surroundings. To ensure that your SPAN port is on the right switch, you must understand where traffic flows. In order to avoid using the same ports or devices for both normal traffic and mirrored traffic, you should use dedicated ports and devices for port mirroring.
- You should adhere to a few best practices while employing port mirroring to enhance the efficiency and dependability of your LAN switches. Limiting the quantity and length of the mirrored sessions as well as specifically picking out only the pertinent ports, VLANs, or traffic directions that you need to monitor are all part of this.
- Specify a filtering area. A SPAN port has drawbacks, so you want to be careful not to over-capture traffic. Mirrored packets may be dropped by the switch if the network traffic volume is too heavy. In order to lessen the volume and nature of mirrored traffic, the right filters and triggers should be used.
- Examine your logs. Although network observability is crucial, if you never examine the traffic you record, you are doing yourself no favors.
- To guarantee the integrity and confidentiality of the traffic, secure techniques and protocols like encryption or authentication should be utilized.
- Limit your captures. You must parse out or filter through each packet you capture. Recognize what you're after, and make an effort to merely record the traffic you require.
How does Port Mirroring Compare to other monitoring methods like Network Taps?
Installing a network tap or using a mirror port are two popular ways to get a glimpse into a network. While both port mirrors and taps have advantages and disadvantages, choosing the best option will depend on your network requirements and architecture, as well as, of course, your budget.
In order to employ a network analyzer or other monitoring tool for troubleshooting, diagnostics, security, or forensics compliance, network taps, and mirror ports both offer a view into the traffic on a network segment.
The following summarizes the distinctions between network TAP and port mirroring.
- TAPs are an essential element that must be used in any system that demands complete visibility and traffic fidelity. Additionally, it is preferable to implement network TAPs while traffic volumes are moderate to high. TAPs are often deployed during a maintenance window or during the early design process because installing a TAP into an existing network link necessitates a brief cable disconnect.
- In contrast, network switch port mirroring performs best for ad hoc monitoring of small amounts of data in places without TAPs. It continues to be the sole way to access some types of data, including data that moves from port to port inside the same switch, traffic that stays within a switch but never reaches a physical link, and traffic that occurs in remote areas with low traffic that cannot support a full-time TAP.
- A hardware component that is installed on your network is called a network tap. It permits unhindered network communication while copying all data to a monitor port where a network analyzer can access it.
- On the other side, port mirroring is a feature that many high-end networking devices come with. This feature makes it possible to replicate data from one port to another, resulting in a mirror port that serves as a software network tap.
- Using network TAPs, a specific segment's traffic can be monitored. However, the output of port monitoring can vary from day to day or hour to hour, leading to inconsistent reporting. Incorrect mirror port configuration will slow down the network.
- TAPs often don't care whether the protocol is being carried in the connection or if the traffic is IPv4 or IPv6. A passive TAP is used to pass through all traffic. Compared to the number of ports that may need monitoring, network switch mirror ports are few in number and take up ports that might otherwise be used for production traffic.
- Considering that most switches already have the feature built-in, port mirroring solutions don't use up a lot of bandwidth and are reasonably priced. On the other hand, tap devices can be put into the network at various locations to provide full exposure and visibility; additionally, when they are passive taps on fiber cabling, they can continue to function even in the event of a power outage.
- TAPs provide complete fidelity for network monitoring, analytics, and security by producing an identical replica of the bi-directional network traffic at a full line rate. Although network switch mirror ports are frequently overloaded, this causes dropped packets, which has an inconsistent impact on monitoring and security.
- Once implemented, passive TAPs offer constant access to traffic and don't need user assistance or configuration. While sometimes influencing network traffic, network switch port mirroring can have a detrimental performance impact on the switch itself.
What are the Types of Port Mirroring?
There are different port mirroring options that depend on the network architecture, needs, and hardware and software being utilized. Types of port mirroring are as follows:
- Copying traffic from one switch port to another on the same switch is what local port mirroring entails.
- Copying traffic from one switch to a port on another includes remote port mirroring.
- While Layer 2 port mirroring enables administrators to copy traffic inside a local area network (LAN), destination port mirroring replicates traffic from various ports.
- A more recent kind of remote port mirroring, encapsulated remote port mirroring (ERPM), can transport duplicated traffic over a Layer 3 network.
- Mirroring traffic between two switches in a two-switch arrangement offers redundancy and increased scalability.
- The ability to mirror specific VLAN traffic to a specific port is provided by VLAN-based port mirroring.
- Remote port mirroring is possible across Layer 2 and Layer 3 networks using the Cisco proprietary protocol known as RSPAN (Remote Switched Port Analyzer).
- General Routing Encapsulation, or GRE Another method of encapsulating and transmitting mirrored traffic across a Layer 3 network is tunneling.
What are some real-world applications and scenarios for Port Mirroring?
Port mirroring has a variety of applications. The most common port mirroring use cases are given below::
- Network troubleshooting: Port mirroring can be used to watch network traffic and spot problems when troubleshooting a network. For instance, port mirroring can assist in determining which hardware or software is to blame for a user's sluggish network speeds.
- Intrusion Detection System (IDS): Port mirroring can be used to monitor all incoming traffic for unusual or aberrant behavior. This can be accomplished by utilizing a different program, such as a protocol analyzer or IDS, which can analyze all incoming packets without interfering with the switch's regular operation.
- Traffic analysis: Port mirroring can offer in-depth insight into the behavior of network traffic, which can be utilized to improve network infrastructure and prepare for future capacity needs.
- Security monitoring: By observing traffic patterns, port mirroring can be utilized to find security flaws or questionable behavior. Additionally, it can aid in locating potential insider threats.
- Call logging for IP phones: Since all VOIP calls must go through the IP PBX, a network switch can deliver a copy of every packet sent or received by an IP phone to the IP logging (recording) server or application. However, all calls are captured in this manner "unobtrusively".
- Performance monitoring: Network performance and smooth operation of apps can both be checked via port mirroring. It can assist in finding opportunities for optimization and bandwidth-intensive apps that can influence network performance.
- Web-based data leakage prevention: Some applications employ port mirroring to track the traffic that users are sending to the internet. This can make it possible for such DLP(Data Loss Prevention) solutions to determine whether certain confidential information, such as credit card numbers, medical details, and intellectual property designs, is being given to someone in bulk through webmail, for example.
- Application monitoring: By using port mirroring, you may keep tabs on particular programs and find problems with their usage or performance. For instance, it can assist in determining which users and how frequently they access a specific program.
What tools and solutions are available for network analysis using Port Mirroring?
Network administrators can configure, monitor, and analyze network traffic with the use of numerous port mirroring solutions. These tools come in a variety of forms, from straightforward command-line interfaces to sophisticated graphical user interfaces that offer real-time network traffic analysis and alarms. Wireshark, Tcpdump, SolarWinds Network Performance Monitor, and PRTG Network Monitor are a few well-known port mirroring tools.
- Wireshark: The most well-known tool in any sysadmin's toolbox is certainly Wireshark. It has several cutting-edge analysis tools in addition to being able to record data. The fact that Wireshark is open source and has been adapted to practically all server operating systems makes it even more appealing. Originally known as Ethereal, Wireshark is now available everywhere, including as portable standalone software.
- tcpdump: TCPdump is the primary tool for virtually all network traffic collection. Almost all operating systems that are similar to Unix already have this open-source program installed. Tcpdump is a great tool for data collection and has a highly sophisticated filtering language built in. To end up with a manageable volume of data to analyze, it is critical to know how to filter the data at the time of collection. Even a moderately busy network can produce too much data if a network device's whole data stream is captured.
- SolarWinds Network Performance Monitor: A network monitoring software called SolarWinds Network Performance Monitor has a network packet analyzer that can automatically collect data from more than 1,200 apps. Using the Quality of Experience (QoE) dashboard of SolarWinds Network Performance Monitor, you can monitor packet transfer in real-time.
- PRTG Network Monitor: The network monitoring tool Paessler PRTG Network Monitor features a packet sniffer and bandwidth monitoring features. With SNMP and WMI, the software can track bandwidth utilization, upload and download speeds, and availability in real-time.
What is the Difference between Port Mirroring and Traffic Mirroring?
The mirroring feature includes port mirroring and traffic mirroring.
Traffic mirroring copies the specified traffic to the destination port that fits a specific configuration rule for analysis and monitoring. Client 2's data flow that complies with the rule is duplicated from the source port to the destination port, which sends the copied data flow to the monitoring device. By using configuration instructions or an ACL (Access Control List), the matched data flow can be defined. While port mirroring duplicates every packet that comes across the interface to the monitoring device, traffic mirroring only sends the selected or matched traffic.
The distinctions between traffic mirroring and port mirroring are as follows:
- You copy each packet that goes through the interface when you use port mirroring.
- By using traffic mirroring, you can choose to duplicate only specific traffic, saving your monitoring equipment from having to process irrelevant data.
- While traffic mirroring is a more scalable option, port mirroring has significant drawbacks, such as the ability to only apply the policy in one direction at the interface.
- The act of mirroring traffic to an interface and the act of mirroring are both traffic behaviors.
How can Port Mirroring impact Security and Network Traffic Analysis?
During their professional careers, network, and security engineers will definitely encounter the idea of traffic monitoring. A single source of traffic can be transmitted in real-time to several destinations thanks to traffic mirroring.
Organizations may want to mirror traffic as it passes through specific areas of their networks for a variety of reasons. The main use cases are the ability to troubleshoot, examine, and enable particular security mechanisms. Mirrored traffic that is recorded to disk or examined in real-time can be used to identify the cause of difficult-to-find outages, such as a flawed firewall block rule or a problem with routing protocols.
The capacity to examine traffic without affecting the flow itself is the main advantage of traffic mirroring in the cloud. Companies frequently can't afford the hardware and licenses needed for a sandbox or intrusion detection system (IDS), and as a result, they run the risk of traffic flow delays. These problems are fixed via a mirrored traffic stream. Additionally, it increases the possibility of testing controls without disrupting live traffic. Finally, security experts can use packet capture technology for compliance testing and security analysis. This is done by writing network traffic to a disk, which calls for a location to tap into the network and listen in on the communication.
From this perspective, we need to know: Using network performance analysis software can assist your team in accurately and quickly locating and resolving network issues. Your company can proactively monitor bandwidth availability, network bottlenecks, Wi-Fi speeds, and much more with the correct network analysis tools.
In conclusion, enhanced network visibility, troubleshooting, and security are advantages of port mirroring. Administrators can improve network performance, spot security threats, and swiftly identify and fix network issues by monitoring network traffic.
Additionally, it can be used to track network performance, such as bandwidth usage, traffic patterns, or service quality. Port mirroring can be used to strengthen security by spotting malicious activity, stopping data breaches, or enforcing rules.