Network Topologies: Definition, Types, and Examples
The shape of how computers and other networking devices are linked to each other is referred to as network topology. The word topology is formed by combining the Greek words topo and logy. "Topo" means "place" and "logy" means "study". It shows the placement and interconnection of nodes as well as the flow of data. The kind of configuration or topology determines network performance in computer networking. As a network administrator, you must have a thorough understanding of your network's topology. Without this knowledge, even simple troubleshooting might be excessively complicated.
This article will describe what a network topology is, and different types of network topology implementations including their advantages and disadvantages, and the importance of network topology. We will give key points for selecting the right network topology for your IT infrastructure as well.
What is Network Topology?
A network topology is the physical and logical configuration of its nodes and connections in a network. Network topology is an application of graph theory in which communicating devices are represented as nodes and the links or lines between the nodes. Nodes typically consist of devices like switches, routers, and software with switch and router functionality.
There are numerous methods to organize the topology of a network. Each has advantages and disadvantages, and depending on your organization's requirements, certain configurations may provide you with a higher level of connectivity and security.
There are two types of network topology:
-
Physical topology
-
Logical topology
The physical design of the network is represented physically by the topology of the physical links that are visible. When you identify a network, you create these interconnection maps in your mind, which is known as logical topology. Logical topology is a type of network topology which does not use a specific physical layout. It demonstrates the data flow inside an operational network. In such a way that a topological shape is produced when a map is created from the connections, and as a result, the network's physical topology is revealed. The logical topology, however, is formed by an awareness of the data flow details. So basically, the layout of multiple linked devices is the network topology. Even though this layout looks like a circle, it is not always a ring topology. The way the data is transferred and the devices are connected how the network topology will take shape.
Bus, Star, Ring, Mesh, Tree, and Hybrid topologies are the different physical topology examples each consisting of different configurations of nodes and connections. A network's design can directly affect how well it works. Because of this, businesses must choose the best topology for their network to boost performance and improve data efficiency. Additionally, the appropriate topology reduces operational expenses and optimizes resource allocation.
What is the Importance of Network Topology?
Comprehending network topology is crucial for guaranteeing excellent network performance and administration. Moreover, it offers understanding of the intricate structure of a network and aids in the effective solving of network nodes. A company enhances its data transmission efficiency by using a well-defined and meticulously designed network architecture, which enables easier problem detection and issue resolution.
Network topology assists a network administrator in understanding the various pieces of the network and where they link. It displays how each component interacts and assists in performance management.
The topology of a network has a significant effect on its functionality. A properly planned and managed network topology reduces energy consumption and increases data transmission velocities, which can significantly boost performance.
Network topology enables you to become acquainted with key components of your network and their connections. In addition, it illustrates their interactions and what can be predicted based on their performances. Therefore, performance management is the key to topology, regardless of the size or structure of a network and its numerous components.
One of the main design components in the process of evaluating risk, impact, and cost is network topology. Different topologies offer alternatives and possibilities for regulating the size of the attack surface, the range and complexity of the attack, and the instruments available for detection, response, and recovery. When choosing a topology that maintains a balance between operational advantages and risk tolerance objectives, analysis of operational profits and losses should be taken into account.
At this point, network topologies become even more crucial. Network topologies play an important role in network operation and help us better comprehend networking concepts. It is critical to performance and supports the reduction of operating and maintenance expenses, such as cabling costs. A network topology influences the type of device used to connect a network. Detecting errors or faults are simple with network topologies.
What are the Types of Network Topology?
Network topology is the structure of the connections between computers and other network components. There are numerous physical network topologies from which an organization can choose based on network size, suitability, and business objectives. Each network topology type comprises of various node and link configurations and has its own benefits and drawbacks. Below is a list of the six different types of physical network topologies:
-
Star Topology
-
Bus Topology
-
Ring Topology
-
Mesh Topology
-
Tree Topology
-
Hybrid Topology
1. Star Topology
Star topology is the most common network topology used today. In Star topology, each network node is connected to a central device such as a switch, hub or wireless access point, making it simple to add new nodes without having to restart all of the presently attached devices. When a cable in a star network breaks, just the node attached to that cable is disconnected from the network. The other nodes can continue to operate properly.
There is a relatively technical difference between a hub and a switch. To put it simply, a hub does not know the computers that are connected to each of its ports. A switch, in contrast, is aware of the computers that are attached to each of its ports. Only switch-based networks have a real star topology. If the network employs a hub, the network architecture looks like a star but is a bus topology. This is because, just as in a bus architecture, when a hub is employed, each computer on the network sees all packets sent over the network. In a real star topology, such as when a switch is utilized, each computer sees only packets delivered directly to it, as well as packets sent explicitly to all computers on the network.
Star topologies are frequently used in local area networks. When you have a small network that utilizes a switch or hub to connect multiple devices, you can use star topology. It can achieve very high data transmission rates, especially when the star coupler is employed in the switch mode. Among the various topologies, this is the easiest to maintain. But there are some disadvantages related to this topology. The central hub's operation is critical to network operation. As a result, if the central hub fails, the entire network fails. In addition, the number of nodes that may be added is limited by the capability of the central hub.
In Star topology, it enables ease of operation since it is centralized. Additionally, it achieves network device isolation for every device. It is simple to add or remove network nodes without impacting the network as a whole.
The following image shows an example of the star network topology.
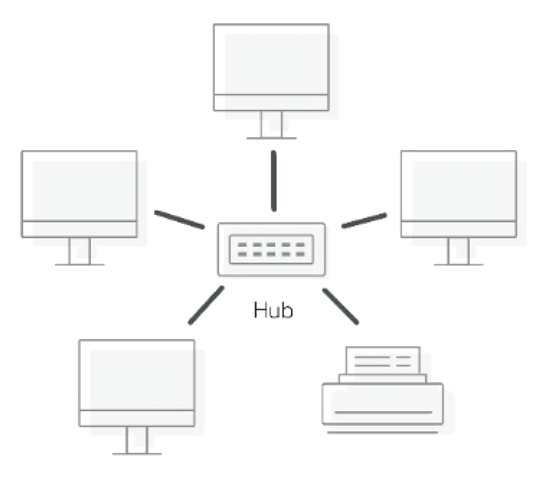
Figure 1. Star Topology
2. Bus Topology
In the Bus topology, nodes are connected in a line. To understand how a bus topology works, imagine the entire network as a single cable, with each node "tapping" into it to listen in on the packets delivered over that wire. Every node on the network can monitor every packet delivered on the cable in a bus topology. Every packet is examined by each node to see if it is meant for that node. If so, the packet is claimed by the node. If not, the packet is ignored by the node. Each computer on the network will then be able to respond to data delivered to it and ignore data sent to other computers.
If the cable in a bus network breaks, the entire network is disabled. Because data cannot span the distance formed by the break, the nodes on opposite sides of the break can continue to interact with each other. Even nodes on the same side of the break may be unable to interact with one another because the open end of the cable left by the break disrupts the efficient transmission of electrical signals.
The use of a bus topology has various advantages. It's simple to add new devices, replace current devices, or uninstall old devices without impacting other connected devices, compared to other network topologies like mesh and star, less cable is used, and the cable can be quickly extended as needed.
In a bus topology, it is simple to manage and implement. Bus topology is ideal for small networks and it is cheap to set up.
The following figure shows an example of the bus network topology.
Figure 2. Bus Topology
3. Ring Topology
Ring topology is another type of network topology. Packets are passed from computer to computer in a ring topology. Each computer examines every packet to see whether it was meant for that computer. If not, the packet is sent to the next computer in the ring. Multiple LANs can be connected to each other in a ring topology on a larger scale using Thicknet coaxial or fiber-optic cable. A ring topology, despite what some people think, is not a physical arrangement of network cables. Rings are a logical arrangement; the real connections are wired like a star, with each node linked to the access unit through its cable. In contrast, the network operates electrically like a ring, with network signals traveling around the ring to each node in turn.
The most advantageous feature of the ring topology is the halving of the number of transmitters and receivers as compared to the linear topology. Additionally, unidirectional flows minimize packet collisions. Due to the use of token-based protocols, which only permit one station to transmit data at a time, the risk of packet collisions is extremely low in ring topologies.
In a Ring topology, every hub has the opportunity to transmit information. Every one of the intermediary hubs is used to transmit information between two hubs. For the management of this topology, a core server is not required. The information is sent quickly and there is just one direction of traffic.
The following diagram shows an example of the ring network topology.
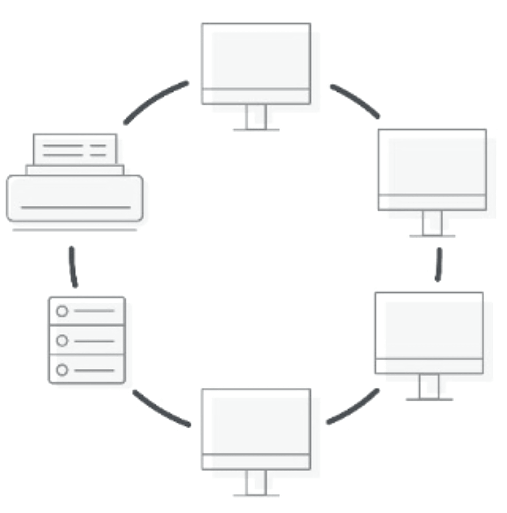
Figure 3. Ring Topology
4. Mesh Topology
Each node in a mesh topology is connected to the others and can send and receive data as well as relay information from other nodes. Mesh topologies can be completely or partially linked mesh networks. Mesh network topology does not require a specific physical layout, but each node must have multiple connections to the other nodes. Multiple LANs can be connected to each other in a mesh topology on a larger scale using leased telephone lines, fiber-optic cable, or Thicknet coaxial. The mesh topology is inflexible and poorly expandable because new nodes must be connected to each of the existing nodes by a dedicated connection, which requires the installation of all linkages before a new node can be added. The cost of cabling will be quite expensive for a broader region for the same reason. Although this design produces a very reliable network, it uses a lot of wire and is challenging to manage. This topology becomes more practical with WiFi networks. Mesh topology is the best network topology which describes the Internet. The benefit of a mesh topology is that if one cable breaks, the network may utilize another path to transmit its data.
In Mesh topology, it is possible to send data simultaneously from one hub to many other hubs. There are dedicated routes connecting any two network hubs, so it can manage heavy traffic.
The following figure shows an example of the full mesh network topology.
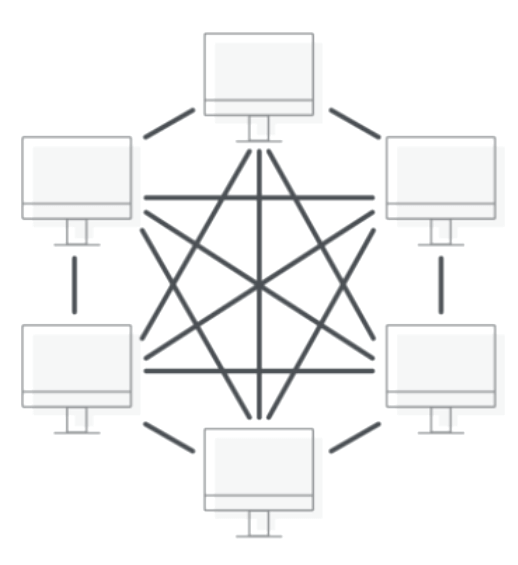
Figure 4. Mesh Topology
5. Tree Topology
We can consider the tree topology as an extension of the bus topology. It's a hybrid topology that combines the star and bus topologies. When connecting to other nodes, the core parent node acts as a "bus" while the other child nodes spread the connections to its star topology. The name of this topology comes from the manner in which trees are organized. The network is made up of additional nodes that are stretched outward like branches out of a tree, with a central node or core acting as "the root or trunk" of the system.
It commonly appears in cascading devices. For instance, if your repeater box has six ports and you have six stations, you may use it normally. However, if you need to add more stations, you may do so by joining two or more repeaters in a tree-like hierarchy (tree topology). Because of their great scalability and flexibility, tree topologies are popular among wide-area networks (WANs). The most significant disadvantage of this topology is that centralization introduces the single-point-of-failure problem. If the central node has issues or a slow-down problem, the entire network is affected and falls.
In Tree topology, it is best suited for system management in various business branches where each department operates independently and is linked to the central hub. Secondary nodes can be added to the network to increase its size. So it is scalable.
The following image shows an example of the tree network topology.

Figure 5. Tree Topology
6. Hybrid Topology
As the name indicates, a hybrid network architecture combines elements of many different topologies. The network's requirements determine how to create such a setup. Commonly, many topologies are used while designing modern networks. Network engineers, however, combine the benefits of each topology. This can be a useful method for easily connecting multiple existing networks into a single system. Star-ring and star-bus are the two most common hybrid topologies.
This topology has several drawbacks and difficulties. Its potentially complicated architecture, for example, may make troubleshooting difficult, and depending on the setup, such a network might be resource-intensive to establish and maintain. Hybrid topology offers certain advantages as well; it combines the advantages of different topologies and, when performed properly, this form of topology is very adaptable and scalable.
The following diagram shows an example of the hybrid network topology.
Figure 6. Hybrid Topology
What are Examples of Network Topologies?
Network topology diagrams are commonly used by network managers to efficiently arrange nodes and connections in network designs. While each network design is unique, the bulk of them are based on or combine components of a few basic topology types. Here are some of the most common examples of network topologies.
-
Point-to-point Topology: The point-to-point architecture enhances the performance of both the transmitter and the receiver. It is the simplest kind of communication, with one node functioning as a broadcaster and the other as a listener. Point-to-point connections offer a significant quantity of bandwidth.
-
Mesh Topology: The Internet backbone is a popular example of a mesh architecture, as it employs dedicated channels to connect many ISPs together. This format is utilized in military communication and aircraft navigation systems. Mesh Topology examples are as follows.
- Extremely dependable networks are appropriate for essential applications that require high availability and redundancy.
- Wireless local area networks, or WLANs, are extensively used to offer connectivity beyond physical boundaries.
- Big networks are useful for bigger setups in which several node connections improve data delivery reliability and speed.
-
Star Topology: A star topology is commonly seen in an office setting, where each computer is connected to a central hub. This design is also utilized in wireless networks, with each device linked to a wireless access point. Applications of star topology are as follows.
- Office settings: Typically observed in constructions with a hub or switch at the middle of a group of workstations.
- Flexible configurations: These are ideal for networks that constantly add and remove devices.
- Centralized management is useful in instances where centralized administration and control of network devices are necessary.
-
Hybrid Topology: Hybrid topology applications are as follows.
- Distinct environmental requirements: appropriate for places that require distinct topologies for different purposes (e.g., bus and star merging).
- Huge companies: Ideal for huge corporations that rely on several divisions or locations and require specialized networking solutions.
-
Tree Topology: Applications for tree topology are listed below.
- Hierarchical systems: Ideal for networks at universities or in businesses where data is arranged hierarchically.
- Networks that plan for future growth might benefit from scalable networks, which enable the addition of additional nodes without compromising current ones.
- Telecommunications: Because of its organized character, it is prevalent in a variety of telecommunications infrastructures.
-
Bus Topology: Examples of bus topology uses are as follows.
- Small networks: Perfect for networks with less need for data transfer.
- Temporary networks: Good for short-term configurations, such as at events or conferences.
- Cost-effective solutions: Ideal for businesses seeking low-cost networking solutions that need less wiring.
-
Ring Topology: Examples of ring topology are as follows.
- Token ring networks: Traditionally, token ring technology was employed in networks to ensure orderly data transfer.
- Small LANs that require consistent network administration might make use of local area networks (LANs).
- Applications where reliable bandwidth and data transmission speeds are essential can benefit from video conferencing.
What are the Advantages of Network topology?
The usefulness and effectiveness of a network are largely determined by its topology. Node and link configuration have a direct influence on a number of network administration, security, and performance factors. An organized topology may reduce downtime, facilitate troubleshooting, and encourage effective data transfer. There are different network topologies with special features according to the purpose of use. Each network topology has its pros and cons. The primary benefits of network topology are as follows:
-
Network Performance: Data transfer rates, bandwidth, and network latency are all greatly impacted by the network architecture selection. For networks with a few nodes, for example, a star topology may enable quicker data transfer; for bigger, more complicated networks, a mesh topology offers greater performance.
A network with the proper architecture is more efficient because it maximizes data flow and reduces bottlenecks. For businesses managing massive data sets or executing time-sensitive applications, this is essential.
-
Management and troubleshooting simplicity: The simplicity of diagnosis and management of various topologies varies. For instance, star topologies make troubleshooting easier since problems are frequently limited to a single node or the central hub. Ring topologies, on the other hand, may take more work to identify and fix problems.
The effectiveness of network management and the speed at which issues are resolved are greatly impacted by the topology selection, which is crucial for preserving seamless operations. By speeding up and improving the detection and resolution procedures, automated monitoring solutions may further improve network management. Network topology mapping tools are another tool that administrators may use to give network teams visual representations of possible problems.
-
Flexibility and scalability: Organizations' network requirements alter as they expand and develop. The ease with which a network may grow to include more devices or reach new areas depends on its topology design.
For example, compared to bus or ring topologies, star and tree topologies make it simpler to add additional nodes. High network traffic levels are best handled by topologies like mesh and star. For companies preparing for future expansion or predicting shifts in network requirements, scalability is essential.
-
Cost factors: Costs associated with deployment and maintenance are directly impacted by network topology. Some topologies, such as mesh topologies, need more extensive cabling and equipment, while others, like bus topologies, may have cheaper initial setup costs.
But it's important to take into account the long-term expenses related to upkeep, improvements, and possible downtime. By avoiding network problems and lowering the need for in-depth troubleshooting, choosing the best architecture can eventually result in considerable cost savings. When choosing the most cost-effective topology, it's critical to take into account the total cost of ownership (TCO), which comprises the original investment, continuing operating costs, and the costs of anticipated downtime.
-
Network Reliability: Certain topologies, such as mesh and star, are dependable because they offer a backup connection in case the primary one fails.
-
Network Expansion: Selecting the appropriate topology makes it easy to add additional devices to the network without interfering with its functionality.
-
Network Security: Network topology improves network security by illuminating the connections between devices. The topology of the network influences how easily security measures may be implemented as well as how vulnerable it is to security threats. While decentralized architectures like mesh give natural security benefits through data channel variety, centralized topologies like star topologies may make it easier to install security and access control mechanisms.
Network topologies frequently utilize firewalls to defend against outside attacks. In addition to preventing unwanted access, a secure network architecture aids businesses in adhering to industry standards like GDPR and HIPAA.
What are the Disadvantages of Network Topology?
Each topology type has its disadvantages and risks. We can list the drawbacks of each network topology type as follows:
-
Both security and security response is impacted by the network topology. The occurrence and propagation of a breach become more difficult as the network becomes more segmented. Damage control and recovery are more important aspects of security than complete prevention, yet choosing the incorrect topology might increase the risk of this damage.
-
In a Bus topology, it is only effective for a small number of nodes. As more devices are connected to the bus, their efficiency decreases. It is difficult to identify errors within the network nodes.
-
In a Ring topology, a single network node's failure has the potential to bring the entire system down. A change to one of the nodes can affect the performance of the entire network.
-
In Star topology, the central hub's functionality is essential for network operation. As a result, when a central hub fails, the entire network fails. The setup cost is high, and the hub's capacity determines how many nodes may be added.
-
In Tree topology, maintenance is difficult and expensive. Additionally, setup is challenging compared to other topologies.
-
In Mesh topology, expenses during installation and maintenance of the network are high because a lot of cabling is required.
How to Determine Your Network Topology?
Before deciding on the network topology, you should consider the needs of the network you will install, your performance expectations, security requirement levels, and the costs to be spent during installation. After determining these, you should start by choosing the most suitable topology for your network.
There is no universal solution for selecting appropriate network topology. The optimal topology for one company may be ineffectual for another. Choosing an appropriate topology for your deployment environment is contingent on a number of variables. When selecting a network topology, you may adhere to the best practices listed below.
- Determine your network specifications
- Never sacrifice reliability
- Determine the spending prudently
- Ensure effective implementation
- Take into account scalability
5 best practices to choose a topology for your network are explained with more detail below:
-
Determine your network specifications: Before selecting a network topology, it is essential to contemplate the network's ultimate purpose. various network applications require various hardware, and selecting the proper hardware prior to constructing a network can prevent a great deal of operational headaches in the future.
Consider the applications that will be executed, the data transmission distance, and the expected performance levels. distinct network topologies require distinct hardware, and vice versa. Assess the existing hardware and account for the new hardware you intend to acquire. Sometimes, existing hardware can be repurposed for a new network topology without significant drawbacks, allowing you to save money and reduce procurement time.
Physical space is an additional factor to consider. If all the systems that need to be connected are in close proximity, consider a bus or star configuration that minimizes cable utilization. Additionally, you should consider cabling from a time perspective, as more cable results in a longer implementation period. As an example, mesh networks are extremely cable-intensive (and thus labor-intensive).
Consider the appropriate cable type. Twisted-pair and coaxial cables both employ insulated copper wiring, whereas fiber-optic cabling is constructed from thin, flexible glass or plastic tubes. If your bandwidth needs are modest, choose economical twisted-pair cables. In contrast, coaxial cables are advantageous when bandwidth demands are greater. However, fiber-optic cabling is more expensive and requires additional components, such as optical receivers.
Finally, consider the experience level of your IT personnel. If network implementation and maintenance are to be performed by personnel without extensive training, a simple topology, such as bus or star, is required. If you choose a mesh, tree, or hybrid topology for your network, you may want to enlist the assistance of an expert.
-
Never sacrifice reliability: Not every topology is equally trustworthy. When setting up a network for a middle school computer center, you could possibly get away with a daisy chain topology. In contrast, if you are establishing a network for a large hospital or a bank, you should most likely choose a robust mesh topology. Remember that network configuration plays a significant role in the daily disruptions and latency you will experience.
Bus and daisy chain topologies are suitable for non-critical configurations. Ring topologies can process large loads with relative ease, but they are susceptible to a single point of failure. Star topologies are not dependent on any node and therefore fail in the event of a center failure. Hybrid and mesh topologies are robust and reliable, but setup and maintenance can be resource-intensive.
-
Determine the spending prudently: Cables and other hardware are not the only expenses you must account for. You would also need to budget for installation costs and, if necessary, a consultant to assist you in selecting the optimal topology for your computer network and to supervise its implementation. Moreover, cost can be multiplied in network topologies that incorporate multiple network components.
Establish a budget that strikes a balance between installation and operating expenses and the expected network performance. While it is understandable that more sophisticated topologies may be more expensive in the short term, you must also consider the long-term consequences of selecting a less expensive setup. However, if you do not have a use case for sophisticated components and topologies, you do not need to choose them. For example, a complete mesh topology utilizing fiber-optic cabling is likely only required by businesses with advanced dependability requirements.
In terms of pricing, ring, bus, and daisy chain topologies are less expensive to implement than mesh, star, and tree topologies.
-
Ensure effective implementation: Consider how simple it would be to implement the selected topology. Even if you intend to maintain the network in-house in the future, you should likely commission a vendor to deploy it. Choosing an experienced vendor eliminates concerns regarding the complexity of the network topology, as the vendor's networking personnel would have the necessary qualifications and experience to correctly set up the network. In contrast, implementing your preferred network topology internally may reduce costs in the short term. Nonetheless, if the proper configuration is not implemented, it may cause network disruptions.
-
Take into account scalability: It is essential to keep in mind that you are constructing a network, not only for the present but also for the future. Choose a topology that is readily adaptable. Star topologies are popular for adding, removing, and modifying nodes without disruption. In contrast, ring topologies may necessitate the shutdown of the entire network prior to any modifications.
Consider the current number of devices and recognize that it will likely increase exponentially as you observe expansion. Consider the geographical dispersion of your devices, and keep in mind that a topology that is ideal for connecting 100 terminals fails if the number of devices exceeds 1,000.
In addition, even if your current topology scales up flawlessly, there may be an affordable method to do it after a certain number of devices have been added. For example, tree topologies are optimal for larger networks, whereas bus topologies satisfy the network requirements of small businesses.
Which Network Topology is Best Used in a LAN?
A LAN is established to connect the necessary network devices so that personal computers or workstations can share all data among themselves. A special addressing scheme assigned by the TCP/IP protocol provides a connection between the computer and other devices with switches. In a local area network (LAN), Star topologies are most commonly used. In a very small LAN, like the one at your house, this is much more accurate. Because all other devices in the network are connected to a single central device at home.
Other LANs can commonly use star topologies as well. As an illustration, access switches are used in corporate networks where all hosts and computers are connected to the central switch. Although it uses a star topology. Apart from the Star topology, the Bus and Ring topologies are used for LAN. The bus topology can cause slow transactions in the network, but it can save cable expenses for installation.
Which Network Topology is Used in the WAN?
An extensive computer network known as a wide area network (WAN) links collections of computers over considerable distances. Big businesses commonly utilize WANs to link their office networks; normally, each office has its local area network (LAN), and these LANs communicate via a WAN. Wide Area Networks may use one or more different topologies. Which one is utilized for a specific WAN depends on the business requirements, the available space, and the cost-benefit analysis.
There are two distinct but connected views involved in applying the idea of topologies to WANs. The physical topology, which specifies the actual configuration of network components that enables data to transit from point A to point B, is one factor to take into account. The logical topology, which defines how data travels across the WAN, offers another viewpoint. The topologies that can be used for WANs are ring, star, and mesh topologies.
Where Should the Firewall be Placed in the Network Topology?
A firewall is a system, or group of systems, that maintains a distinction between two or more networks. A firewall can be software that runs on a computer, a specialized hardware box, access control lists (ACLs) running on a router, or any combination of these. To ensure that all traffic coming from outside the protected network passes through the firewall. A security policy determines which types of traffic are allowed to get in through the firewall. For proper security management, firewalls must be established between every network connected to the internet.
What Is the Difference Between Physical and Logical Network Topology?
The physical topology and the logical topology are two distinct features of a communications network that are described by a network topology.
The physical network topology describes the placement of each network component, as well as their physical connections. Network administrators may see how devices are connected to one another and how to best organize nodes and cables by using a network topology map.
Regardless of the physical connections, logical topology specifies how data flows through a network and how network devices appear to be connected to one another. Every network does not necessarily have omnidirectional data flow, and the logical network topology may show how data should move as well as how many connections and nodes it must pass through to get to its destination.
Physical topology and logical topology can diverge greatly, particularly in intricate networks with several data channels. A physical network diagram depicts the connections between devices, whether wired or wireless. A logical network diagram, on the other hand, depicts how signals and data are routed across a network.
| Physical Topology | Logical Topology |
|---|---|
| Shows the network's physical configuration. | Illustrates the network logistics involved in data transfer. |
| Depending on device availability and selection, this significantly affects the network's cost, scalability, and bandwidth capacity. | Data packet transmission and speed are significantly impacted by this. It manages data packet delivery in an organized fashion and flow management. |
| Depending on requirements, the layout can be changed. | This is not a case of manipulation or meddling. |
| The transmission is the real path in question. | Data flow is depicted at a high level. |
| Network's physical connection. | Data route taken by the network. |
Table 1. Physical Topology vs Logical Topology
How Do You Read and Create a Network Topology Diagram?
Understanding the symbols and notations used to represent different network components is crucial before beginning to create network topology diagrams. Consider it as learning the network diagram language. It gets much easier to comprehend and create these diagrams after you understand the fundamentals.
Typical network topology symbols and what they imply are as follows.
-
Ovals and circles (endpoints/nodes): Computers, printers, and other network-connected devices are examples of network nodes or endpoints that are represented by these symbols.
-
Squares and Rectangles: Devices like as servers, routers, and switches are represented by squares and rectangles. Servers offer services to other networked devices, switches link devices inside a network, and routers route data packets across networks.
-
Lines: Lines indicate how devices are connected to one another. Different connection types (wired, wireless) are indicated by different styles (solid, dotted). Wireless interconnections are indicated by dashed lines, whereas cable connections are often represented by solid lines.
-
Triangles: Wireless access points are typically represented as triangles, which give devices within a specific range Wi-Fi connectivity.
-
Circles: Double circles represent gateways, devices that link several networks and control traffic between them.
You may produce precise and in-depth network topology diagrams that successfully convey complicated information by becoming proficient with these symbols.
How to Create Network Topology Diagrams
Network topology diagrams should be created prior to network construction. In this manner, network administrators are aware of the elements that make up the network and their interactions. The following procedures are involved in creating the diagram.
-
Clearly state why the graphic is being drawn. Are you troubleshooting, documenting, or designing a new network? Make a list of every device connected to the network, including servers, routers, and firewalls.
-
After the objective has been established, collect data about the PCs, routers, servers, and other network elements.
-
Choose a structure, such as a bus, star, mesh, tree, or point-to-point, based on your needs and financial constraints. Select the network topology type and create the diagram. Taking data flows into account, devices should be positioned where they make the most sense.
-
At this point, organize your gadgets in the proper logical and physical order. At this point, keep the data flow in mind.
-
Make a crude illustration. If your gadgets are wirelessly linked, use dotted lines. If there are wired connections, use clean lines. The connections that the network nodes establish are represented by these lines. Try to keep the diagram clean and easy to read by avoiding having too many lines cross over one another. When designing the diagram, scalability and future changes should also be taken into account.
-
Diagram software can assist in mapping things out once the drawing has been made and shows a rough overall input. A network diagram template may be included in the software. To make the diagram easier to read and comprehend, the network nodes should be given names, and lines can be colored.
-
Label every connection and device. Annotate the symbols you have sketched. To demonstrate links, use a variety of colors. This and other small details will help you and anybody else seeing the diagram understand it.
-
Use diagram tools such as Microsoft Visio, draw.io, or other online platforms once your preliminary drawing is complete. Numerous templates are accessible online.
-
Keep scalability in mind. A scalable diagram allows for future additions and modifications.
What are the Best Practices for Creating Network Topology Diagrams?
Knowing the symbols and topologies alone is not enough to create effective network topology diagrams. Adhering to recommended practices guarantees that your diagrams are accurate, understandable, and practical. You may produce diagrams that are not only aesthetically pleasing but also useful and simple to comprehend by following established principles. By following these guidelines, you can keep your diagrams consistent, communicate better, and increase their overall efficacy.
- Keep it easy: Don't put too much information in your diagram. Pay attention to readability and clarity. By keeping your diagrams simple, you can make sure that viewers can grasp the network's structure quickly and without getting distracted by extraneous features. Keep your arrangement simple and refrain from crossing lines too much.
- Make use of uniform symbols: To make sure that other people can understand your diagrams, use standard symbols and notations. Maintaining symbol consistency makes it easier to avoid misunderstandings and guarantees that your work can be appropriately interpreted by anybody who is knowledgeable about network topology diagrams. Consult the accepted norms and regulations on the use of symbols.
- Clearly label: To prevent misunderstanding, clearly mark all parts and connections. Precise labeling guarantees that visitors get the meaning of each part and gives context. Give devices and connections meaningful names, and think about annotating complicated or unusual arrangements.
- Frequent updates: Maintain your schematics current to account for any modifications to your network. Diagrams should be dynamic, much like networks. Make sure your diagrams appropriately depict the network's current status by reviewing and updating them on a regular basis. Maintaining the relevancy and use of your documentation is facilitated by this technique.
- Work together efficiently: Involve your team in the diagramming process by using Miro's collaborative tools, making sure that everyone has access and feedback. Working together guarantees that the diagram takes into account a variety of viewpoints and areas of expertise while also fostering a sense of ownership.
What is Cloud-Based Network Topology?
A cloud service provider's network infrastructure is shared by several enterprises in cloud-based network topologies. Scalability, flexibility, and cost savings are provided by this architecture as it allows enterprises to use resources as needed.
Cloud networking is the process of establishing a business network that links the personnel, assets, and applications of a company using cloud-based services. In the past, businesses established an isolated wide area network (WAN) for safe communication and application distribution using their own specialized network hardware components. The network's setup and administration were costly and intricate. Cloud networking addresses these problems by allowing your organization to use virtual network components. A third-party cloud service provider is in charge of managing and maintaining the networking gear and equipment. Network administrators at your company may then concentrate on efficiency and configuration optimization.
Your company's productivity, scalability, and security may all be improved with cloud networking.
-
Effective network administration: Third-party telecoms carriers' dedicated networking solutions are expensive and need a large investment of resources. You must purchase new networking equipment and contact the third party for network upgrades, adjustments, or new satellite business facilities.
Cloud networking allows the administrators of your company to work on software on cloud platforms to create new network solutions or make changes to current ones. Network administration gets simpler and more economical.
-
Enhanced scalability: Scalability aids in your organization's readiness for a wide range of potential future events. Deploying and retiring IT services may be done with more agility. Historically, the establishment of new corporate buildings included expenditures in physical infrastructure and strategic network layout. Scaling was sluggish and costly.
Instead of taking days or weeks to set up a new facility, cloud networking allows you to do so in a matter of hours. In a few simple steps, you may establish direct and secure connections to company facilities and resources. In a similar vein, it is simple and rapid to take networks and infrastructure down.
-
Simpler security: Solutions for virtual cloud networking are made especially to let businesses use software to build their own safe networks. Because of economies of scale, cloud enterprises may deploy state-of-the-art technology and highly secure physical network components. You may utilize cloud networking security technologies and adhere to recommended practices while configuring networks to further improve security.
-
Improved upkeep and observation: Some physical networking systems need in-house physical administration, although many are handled and maintained by telecom carriers. Physical administration and upkeep are totally eliminated with cloud-based networking. Using a variety of network management software tools, it provides your company with complete insight into network traffic statistics.
How Does Network Topology Affect Security?
The configuration of the connections between various devices in a network, including computers, servers, and other nodes, is specified by the network topology. This structure can be constructed in a variety of ways, each with unique advantages and disadvantages in terms of IT security.
In a well-designed network, topology may assist in decreasing the risk of attacks, enhance resilience in the event of a breakdown, and simplify data traffic management. However, selecting the inappropriate network design might expose systems to vulnerabilities, making them simpler to exploit.
For example, with a bus topology, all devices share a communication channel, allowing for eavesdropping. In contrast, the star architecture contains a core node that, if compromised, may bring the entire network down. Mesh topologies provide resilience because of their high redundancy, which allows data to be redirected if some channels are affected. However, its intricacy can make monitoring difficult. Because compromising an upper node affects all of its subordinates, tree topologies pose a risk.
Regardless of the architecture chosen, security procedures such as segmentation, monitoring, and access restrictions are critical.
In fact, the security of a network is determined not only by its topology but also by how it is administered and safeguarded.
-
Bus Topology: The bus architecture, which is defined by a single central wire that connects all network devices, poses a considerable danger of data collisions and eavesdropping. Since the core backbone is required for all communications, the network as a whole collapses if the primary cable breaks. This single point of failure exposes the network to denial-of-service attacks. Furthermore, without strong encryption and secure access protocols, every device on the bus has the capacity to monitor traffic, increasing the danger of data interception and illegal access.
-
Star Topology: All nodes in the star topology are connected by a single hub or switch. While this configuration simplifies monitoring and management, it creates a vital point where security must be tight: the central hub. If the hub is hacked, either due to a breach or malware infection, the attacker obtains access to all linked devices. Furthermore, the centralized nature of the star topology requires powerful security measures such as firewalls and intrusion detection systems to prevent unwanted access and preserve the network's integrity.
-
Ring Topology: In a ring topology, where each device is linked to two others to form a closed loop, the failure of one device can disrupt the entire network. Security problems include ensuring that each node can survive assaults and that all data going via each node is encrypted to prevent eavesdropping. The ring arrangement further complicates isolating and addressing security vulnerabilities since traffic must transit through numerous devices before completing its circle.
-
Mesh Topology: Mesh topology, with complete interconnectivity and multiple redundant connections between nodes, provides excellent resilience but also adds complexity to security administration. Every link is a possible entry point for attackers, necessitating extensive encryption and authentication protocols. A mesh network's strength resides in its capacity to redirect traffic around damaged or compromised nodes; yet, this flexibility needs complex security mechanisms to prevent unwanted access and assure safe communication over the several channels.
-
Hybrid Topology: Hybrid topologies incorporate aspects from two or more separate topologies, resulting in a complicated security landscape. The integration of many topologies necessitates a customized security strategy that tackles the vulnerabilities of each topology inside the hybrid network. Maintaining consistent security rules and procedures across the various components is difficult but critical to guard against attacks that may exploit network segment changes.
What Mistakes Should Be Avoided When Designing a Network Topology?
Here are the most typical network design blunders for system administrators.
-
Lack of redundancy: One of the biggest network design mistakes made by sysadmins is relying on a single point of failure, such as a router, switch, server, or cable. If any of these components fail, the entire network may fall down, resulting in downtime, data loss, and dissatisfaction for users and customers. To avoid this, always build your network with redundancy in mind, which means having backup or other devices, pathways, or sources that can take over in the event of a breakdown. For example, you may utilize numerous routers with separate ISPs, multiple switches with different VLANs, many servers with load balancing or clustering, and multiple cables with distinct paths.
-
Poor security: Another typical network design error made by sysadmins is failing to prioritize security, such as using weak or default passwords, leaving ports or services open, failing to encrypt critical data, or failing to update or patch devices and software. These activities may expose your network to a variety of dangers, including unauthorized access, data breaches, malware infections, and denial-of-service attacks. To avoid this, always use the best security practices for your network, such as strong and unique passwords, shutting or filtering superfluous ports or services, encrypting data in transit and at rest, and routinely upgrading and patching devices and software.
-
Insufficient documentation: A third typical network design error made by sysadmins is failing to create or update network diagrams, label or inventory devices and cables, record changes or incidents, or have a backup or recovery strategy in place. These habits can make your network more difficult to administer, debug, or grow, as well as increase the likelihood of mistakes, conflicts, or inconsistencies. This can be prevented by always sizing your network realistically and appropriately. This includes purchasing devices that meet your present and future requirements, allocating bandwidth in a way that balances cost and quality, using performance standards that are accurate to your actual usage and expectations, and planning for future expansion or changes with scalability and flexibility.
-
Lack of testing: A fifth common network design mistake made by sysadmins is failing to test the network, either by verifying the functionality, performance, or security of the devices, connections, or configurations; simulating various scenarios, workloads, or failures; or monitoring or measuring network behavior, traffic, or health. These behaviors can result in unnoticed or unsolved difficulties, problems, or vulnerabilities, as well as impacts on network efficiency, stability, and quality. In order to prevent this, you should always test your network thoroughly and on a regular basis. This includes using tools and methods to simulate various scenarios, workloads, or failures; monitoring or measuring network behavior, traffic, or health; and confirming the security, functionality, or performance of the devices, connections, or configurations.
-
Lack of communication: A sixth common network design mistake for sysadmins is failing to communicate the network, either by informing or consulting stakeholders, users, or customers about network design, changes, or issues; by failing to collaborate or coordinate with other sysadmins, IT staff, or vendors; or by failing to provide or receive feedback or support. These activities can lead to confusion, misunderstanding, or unhappiness, as well as have an impact on network alignment, integration, and improvement. In order to prevent this, you should always communicate with your network in an efficient and proactive manner. For example, you should consult or inform users, customers, or stakeholders about changes, issues, or the network design in a clear and timely manner; work with other sysadmin IT staff or vendors who have similar goals and standards; and give or receive feedback or support in a courteous and constructive manner.
How Do Network Topologies Handle Scalability and Redundancy?
Since network topology specifies how devices are connected and arranged, it is crucial to network architecture. Performance, scalability, and fault tolerance are all directly impacted, and a carefully thought-out architecture maximizes data flow, lowers latency, and makes troubleshooting easier.
As the company expands or its needs change, a suitable network design makes growth simple. This makes it possible for the network to support additional users, devices, and applications without requiring a major overhaul or disruption. The ease with which a network may grow to include more devices or reach new areas depends on its topology design.
For example, compared to bus or ring topologies, star and tree topologies make it simpler to add additional nodes. High network traffic levels are best handled by topologies like mesh and star. For companies preparing for future expansion or predicting shifts in network requirements, scalability is essential.
Different topologies provide different fault tolerance and redundancy levels. For instance, mesh topologies increase network stability by offering many data pathways. Data can be redirected via alternate routes in the event that one node or connection fails.
Bus or star topologies, on the other hand, may be more susceptible to single points of failure. The likelihood of downtime can be decreased with a well-designed topology.
If one node fails, the mesh architecture makes sure the network won't go down entirely. Once more, in an office setting, you have several backup pathways for your data if the computers in each department are physically connected to each other. Thus, data swiftly finds a different path in the event of a computer crash, keeping everything running smoothly.
Strong redundancy may be provided even with a partial mesh configuration. Assume that IT acts as a central center in your workplace, directly connecting to both finance and human resources. Don't worry if HR has to provide Finance with important data and their direct link is unavailable. IT can be used to route the data. In this manner, you may preserve a high degree of dependability without having to deal with the intricate web of a full mesh network.
Applications in the real world might be completely transformed by this redundancy. Partial mesh configurations are frequently used in advanced mesh Wi-Fi networks to strike a compromise between functionality and performance. Numerous nodes are connected to a primary router. The technology minimizes downtime and keeps a strong signal across the region by rerouting data through a different node in the event that one connection is disrupted.
How Are IoT and Edge Computing Changing Network Topology Design?
The design of network topologies is being revolutionized by the introduction of new elements and the optimization of data processing and transmission through the use of Edge Computing and IoT (Internet of Things). The following is a summary of the ways in which they are affecting network designs:
- Decentralization of Data Processing: Previously, data was transmitted to centralized cloud data centers for processing. The proliferation of IoT devices has facilitated the development of edge computing, which allows for data processing to occur at the "edge" of the network, which is closer to the source. This minimizes bandwidth consumption and latency.
- Enhanced Complexity of Network Topologies: The addition of millions of endpoints to networks by IoT devices results in a more intricate topology. Before connecting to the broader network or cloud, these devices frequently communicate with peripheral nodes or gateways.
- Real-Time Data Processing: Edge computing enables real-time analytics and decision-making by processing data locally. This is especially beneficial in applications such as smart cities, industrial automation, and autonomous vehicles.
- Increased Security Requirements: IoT devices are frequently susceptible to attacks. Features such as ZTNA and network segmentation are now integrated into network designs. Zero Trust architecture guarantees that each user and device is authenticated. The process of isolating IoT devices to prevent the spread of intrusions.
- Bandwidth Optimization: The bandwidth requirements are reduced by reducing the amount of data that is transmitted to the cloud by processing it at the periphery. This is essential due to the vast quantities of data that the Internet of Things (IoT) produces.
- Dynamic and Scalable Networks: Modern networks are engineered to be dynamic, allowing for the installation of new IoT devices without the need for extensive reconfiguration. Scalable processing centers are frequently implemented by edge computing nodes.
- Integration with Emerging Technologies: The designs of networks are further influenced by the integration of AI, machine learning, and 5G with IoT and edge computing. For example, 5G facilitates connections that are both low-latency and high-speed, which are indispensable for peripheral devices and the Internet of Things.
- Fault Tolerance and Redundancy: Networks are designed to be more fault-tolerant by incorporating distributed processing at the periphery. The continuity of the network is guaranteed by the ability of other peripheral nodes to assume responsibility in the event of a failure.
In conclusion, the transition from centralized to decentralized network designs is being facilitated by IoT and edge computing, which prioritize real-time processing, scalability, and security. These modifications are establishing the foundation for networks that are more resilient and efficient, and that are specifically designed to meet the needs of contemporary applications.
