What is IPsec VPN and How does it Work? The Complete Guide for IPsec
IPsec, the most common network layer security control, is a system of open standards for securing private communications across IP networks. It can provide numerous forms of data security, including confidentiality, integrity, data origin authentication, packet replay prevention, traffic analysis, and access control.
Since the format of Internet packets is clearly defined and widely understood, a packet traveling via the Internet can be intercepted by any of the routers that are along its path. IP packets don't have a security feature. Its contents are viewable and editable. Even checksums included in the Internet packet format cannot protect a packet from unauthorized change. They are open to a wide range of attacks, such as forged addresses, content replacement, retransmission of outdated packets, and total modification while in transit.
With Internet packets, there is no guarantee that the packet's sender and contents match what was intended to be transmitted. There is no certainty that the information has stayed secret and hasn't been leaked. IPSec was developed to address these vulnerabilities by adding many levels of security to communications, including message authentication, authentication of the sender, encryption, and authentication of the message itself. The IPsec protocols are improvements to Internet packets that allow for the sending and receiving of Internet packets that are cryptographically secured. Special IPsec headers provide the several forms of cryptographic security that were applied to the packet together with additional details required for successful decryption.
The first version of IPsec was created by John Ioannidis, Phil Karn, and William Allen Simpson in 1992. In October 1993, John Ioannidis from Columbia University and Matt Blaze from Bell Laboratories presented a case for IP layer security. It was entitled "The Architecture and Implementation of Network Layer Security in UNIX". This work marked a breakthrough in the application of security and communication, and it was way ahead of its time. The article described ways to introduce security features without changing the IP structure and then went on to examine implementations of encapsulating IP datagrams in a new IP datagram. It also covered the benefits of encapsulating protocols and authentication procedures as well as the transparency that may be offered to activities taking place at the top layer.
Due to the Internet's rapid expansion and the TCP/IP protocol's inherent security vulnerabilities, a solution that could guarantee the security of data transmitted over the Internet was urgently needed. The Internet Architecture Board (IAB) published a report titled "Security in the Internet Architecture" in 1994. The paper outlined the important areas for security improvements and highlighted the general agreement that the Internet requires more and better security.
What is IPsec?
Internet Protocol Security (IPsec) has evolved as the most widely used network layer security control for communications protection. IPsec is an open standard framework for ensuring private communications over IP networks. IPsec can provide any combination of the following types of protection, depending on how it is implemented and configured:
-
Confidentiality: IPsec can ensure that data is not viewed by unauthorized people. This is done by encrypting data with a cryptographic method and a secret key(a value known only to the two people exchanging data). The data can only be decoded by someone who holds the secret key.
-
Peer Authentication: Every IPsec endpoint verifies the identification of the other IPsec endpoint it intends to speak with to make sure that the network traffic and data are coming from the correct host.
-
Integrity: IPsec offers the ability to identify intentional or unintentional data modifications during transit. The creation of a message authentication code (MAC) value, a cryptographic checksum of the data, helps ensure the integrity of the data. When the MAC is recalculated after the data is changed, the old and new MACs will be different.
-
Access Control: IPsec may perform filtering to guarantee that users can only access specific network resources and utilize specific types of network traffic. IPsec implementations are most commonly used to provide Virtual Private Networking (VPN) services. A virtual private network (VPN) is a network that is established on top of existing networks to establish a secure communications method for data and IP information exchanged across networks. IPsec is the Internet Engineering Task Force (IETF) standard VPN technology for the TCP/IP suite. In contrast to compact VPNs, IPsec is large and complex. IPsec is a powerful VPN protocol.
What are the 3 Protocols Used in IPsec?
IPsec is a set of protocols that help to secure communications across IP networks. The IPsec protocols function in various combinations to offer communication security. There are 3 main protocols established in IPsec:
-
Authentication Header (AH): One of the IPsec security protocols, Authentication Header (AH), protects the integrity of packet headers and contents as well as user authentication. It can optionally provide replay and access prevention. AH is unable to encrypt any piece of a packet. AH and ESP (Encapsulating Security Payload) have been frequently used in combination to secure communications' confidentiality and integrity since, in the early implementation of IPsec, the ESP protocol could only offer encryption, not authentication. In reality, some IPsec software no longer supports AH since authentication features were introduced to ESP in the second version of IPsec. AH has become less important. AH is still useful, though, since it can authenticate sections of packets that ESP cannot. Furthermore, AH is used in many existing IPsec implementations. There are two modes of AH: transport and tunnel. AH generates a new IP header for each packet in tunnel mode; AH does not create a new IP header in transport mode. When using an IPsec gateway, the real source or destination IP address for packets must be changed to the gateway's IP address. Transport mode is commonly used in host-to-host designs since it cannot modify the original IP header or create a new IP header.
-
Encapsulating Security Payload (ESP): The second basic IPsec security protocol is ESP. ESP supported only encryption for packet payload data in the first version of IPsec. If needed, the AH protocol provides integrity protection. In the second version of IPsec, ESP became more configurable. It can do authentication to guarantee integrity, but not for the outermost IP header. Additionally, the Null ESP Encryption Algorithm can be used to deactivate ESP encryption. As a result, with the exception of the older IPsec implementations, ESP can be used to offer simple encryption, encryption with integrity protection, or integrity protection only. There are two modes of ESP: transport and tunnel. ESP produces a unique IP header for each packet in tunnel mode. The new IP header specifies the ESP tunnel endpoints (such as two IPsec gateways) as the packet's source and destination. As a result, tunnel mode is compatible with all three VPN architectural (Gateway-to-Gateway Architecture, Host-to-Gateway Architecture, and Host-to-Host Architecture) variants. Tunnel mode can encrypt and/or protect the data, as well as the original IP header for each packet, can be encrypted and/or protected. Encrypting the contents protects it from unauthorized access or modification; encrypting the IP header covers the origin of the communications, such as the packet's real source or destination.
-
The Internet Key Exchange (IKE): The Internet Key Exchange (IKE) protocol's main goal is to negotiate, establish, and manage security agreements. A connection's IPsec characteristics and security measures are described by a set of values known as a security association (SA), or simply as SAs. Another option is to manually build SAs using values that both sides have already agreed upon. However, this technique is not scalable for large-scale VPNs used in real-world applications. In IKE, new Diffie-Hellman groups are established, status and error information is transferred, and security associations are created using distinct types of exchanges. There are five different IKE exchange types:
- main mode
- aggressive mode
- quick mode
- informational
- group
IKE is a secure method for creating IPsec-protected connections that are utilized in IPsec. To understand IPSec and IKE, it is best to compare them with PKI and the usage of certificates. The usage of certificates for encryption, signing, authentication, and a wide range of other functions is quite simple on its own. IPSec is comparable to the program that uses the certificate to carry out the necessary operations, such as signing emails. Simply stated, the application is not at all concerned with or aware of the complex web of trusts and regulations that govern the whole PKI, from which the certificate was derived. IKE and IPSec function similarly to the PKI that generates and maintains the certificate, and IPSec is similar to the application that utilizes it. IKE ultimately requires more work and is constantly plagued by security and functionality issues.
What are the IPsec modes?
To handle differences in communication architecture and demands, IPSec offers two different modes of VPNs that can be utilized alone or in combination for certain communication features:
-
Transport Mode: In transport mode, AH and ESP protect the transport header. In this mode, AH and ESP intercept packets traveling from the transport layer into the network layer and provide defined security. As an illustration, consider two hosts, A and B, both of which have been set up to encrypt any transport layer packets that pass between them. The transport method of ESP is utilized in this situation. When just transport layer packet authentication is required, the AH transport mode is utilized. When security is not enabled, packets from the transport layer, such as TCP and UDP, flow into the network layer, IP, where the IP header is added and calls to the data link layer are issued. When security in the transport layer is enabled, packets from the transport layer join the IPSec component. The IPSec transport mode can only be utilized when end-to-end security is required. Routers make routing decisions based mostly on the network layer, and routers do not and should not modify anything beyond the network layer header. Incorporating a transport mode IPSec header into packets passing via a router is a violation of this regulation. When both AH and ESPs are utilized in transport mode. ESP should be used first. The reason is simple. If the transport packet is initially secured with AH and then with ESP, data integrity applies exclusively to the transport payload since the ESP header is introduced afterward.
-
Tunnel Mode: Tunnel mode is the other mode in which AH and ESP can operate. It is more customizable than the transport mode. However, this flexibility comes at the price of greater bandwidth requirements. When connecting two networks or a host and a network, such as when connecting a "road warrior" to the home network or a distant office network to a network at home, tunnel mode is frequently employed. An IPsec tunneled mode packet contains two IP headers, one inner and one outer. The host creates the inner header, and the device that provides security services adds the outer header. This might be the host or a router. Nothing prevents a host from providing end-to-end tunneled mode security services. However, there is no advantage to employing tunnel mode instead of transport mode in this case. If security services are provided end-to-end, transport mode is preferable since it avoids the addition of an additional IP header.
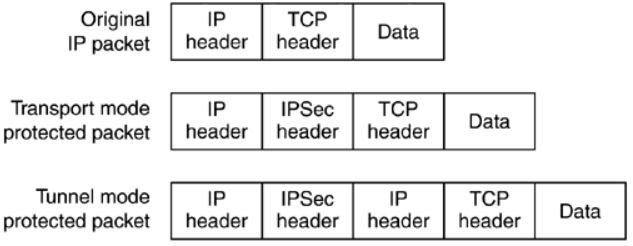
Figure 1. IPsec packets
What Ports Are Utilized for IPsec?
A network port is a virtual interface on a computer for data transmission. Computers use ports to monitor diverse connections and processes; transmitting data to a designated port enables the operating system to recognize the corresponding operation.
Internet Protocol Security primarily utilizes two ports to construct a secure channel: UDP port 4500 for situations requiring Network Address Translation (NAT) and UDP port 500 for connection initiation and key negotiation.
NAT-T may be used as an alternative to IPsec; it necessitates UDP port 4500, whilst IPsec demands UDP port 500 together with IP protocols 50 and 51. L2TP use UDP port 1701. Ports 500 and 4500 must be opened when transmitting IP traffic over a standard Wi-Fi network without an accessible IPsec pass-through option.
What are the Benefits of IPsec?
IPsec offers the following advantages.
-
Flexibility: The layer in which it is provided, the IP layer, is a significant benefit. This means that IPsec may be used to secure any sort of Internet traffic, regardless of the applications used to communicate. The apps do not need to be aware of the protection and do not need to be adjusted in any way to enable it. It also means that the complexity of protection might vary greatly: A single SA can secure all communications between two hosts or two networks, simply specified categories of traffic, a single application-specific session, or numerous intermediate gradations of coverage. The amount and kind of IPsec protection to be used, as well as the keys used to deliver that protection, are both flexible and negotiable.
-
Scalability: Its ability to be implemented gradually, as opposed to other network-related protocols or technologies, gives IPsec a distinct advantage. An organization that rents private communication lines to connect numerous sites can replace one of those lines for an IPsec-protected VPN linking two sites. IPsec may be easily used to establish numerous types of VPNs, including intranets, extranets, and other combinations.
-
Usability: IPsec can be used outside of enterprises. Mobile workers may choose to utilize IPsec to secure their communications when they use a laptop to access a PC that is either at home or work.
What are the Disadvantages of IPsec?
The following are IPsec's disadvantages.
-
Broad Access Range: One of the most serious drawbacks of IPSec is its broad access range. When a device running on an IPSec-based network is granted access, other devices on the network are also granted access. Assume that you're connecting to a business network from your IPSec-enabled home network. If a computer on your home network contains malware, it can quickly spread to other machines in the workplace network.
-
High Cost: The usage of IPsec comes at a cost: more processing and larger packets. This covers both the IKE traffic that comes before the IPsec-protected communications and the additional information added to each IPsec-protected packet.
-
Troubleshooting Difficulties: IPsec can need a significant amount of network-level troubleshooting. Those that install IPsec but are not properly aware of the possibilities risk not just network interruption but also major security breaches.
-
Software Incompatibilities: IPSec comes with several software compatibility problems. This arises when programmers fail to follow IPSec guidelines. Likewise, from an IPSec-based VPN network, you may have difficulty connecting to another network due to firewall restrictions.
How Does an IPSec Tunnel Secure Data Transmission Over Untrusted Networks?
The primary applications of an IPSec tunnel are network-to-network communications (for example, between the gateways of several corporate branches) and end-station-to-gateway communications (for example, in a remote access scenario). The creation of Virtual Private Networks (VPNs), which aim to protect internet connections across networks, requires this tunnel.
The whole original IP packet -header and payload- is encrypted in an IPSec tunnel before being encapsulated into a new one. In addition to having a distinct source and destination IP address, this new packet contains a distinctive IP header.
When complete networks or subnetworks must securely interact over an untrusted network, such as the Internet, IPSec Tunnel is frequently utilized in site-to-site VPNs. When whole networks or subnetworks require secure communication, IPSec Tunnel is frequently utilized in site-to-site VPNs. It safeguards every exchange between two networks.
Think about a company's branch offices. To securely communicate sensitive data over the Internet, they combine the use of an IPSec tunnel. New IP packets with distinct source and destination addresses are created by encapsulating the original IP packets.
How does IPsec Work Step by Step?
The IPsec process is divided into five steps:
-
Initiation: When a host system determines that a packet requires confidentiality and should be sent using IPsec guidelines, the IPsec procedure begins. For IPsec purposes, such packets are called "interesting traffic", and they set off the security regulations. This implies that suitable encryption and authentication are used for incoming packets. If the incoming packet is considered interesting, the host will verify that the contents of this packet have been correctly encoded and authorized. When interesting traffic is created or passes through the IPSec client, the client proceeds to the next stage of the procedure, negotiating an IKE phase 1 session.
-
IKE phase 1: The two IPsec endpoints must successfully negotiate a secure channel over which an IPsec SA may be established for the "IKE phase 1" exchange to succeed. An IKE SA is the usual name for the secure channel produced during phase 1. The IKE SA is designed to provide bidirectional encryption and authentication for additional IKE exchanges, including the phase 2 negotiations and the transfer of status and error information.There are two possible configurations for IKE SA:
- Main Mode: In the main mode, the host starts the connection that makes proposals specifying the encryption and authentication algorithms it prefers. The negotiation will continue until both hosts reach an agreement and set up an IKE SA defining the IPsec channel they will use.
- Aggressive Mode: Aggressive mode is a quicker option than the main mode. Instead of three pairs of messages, it negotiates the formation of the IKE SA using three messages. The first two messages negotiate IKE SA parameters and exchange keys; the third and fourth messages authenticate the endpoints to each other.
-
IKE phase 2: Phase 2's goal is to create a SA for the IPsec connection itself. The IPsec SA is the name of this SA. IPsec SAs are unidirectional, in contrast to IKE SAs, which are bidirectional. This indicates that two SA are necessary for an IPsec connection between two systems (security associations). One method, known as quick mode, is used to construct the pair of IPsec SAs. In Quick mode, IKE builds IPSec SAs, develops shared secret keys for the IPSec security algorithms, and negotiates a shared IPSec policy.
-
Data transfer: Information is transferred through an IPSec tunnel once IKE phase 2 is finished and quick mode has created IPSec SAs. The encryption described in the IPSec SA is used to encrypt and decode packets.
-
Termination: The IPSec connection can be terminated because the traffic has finished and the IPSec SA has been removed. SA can be specified as a timeout dependent on the SA lifetime value. The SA timeout might occur after a preset amount of seconds or bytes transferred via the connection.
What Are the Key Components of an IPSec Tunnel?
A group of protocols known as IPsec, or Internet Protocol Security, was created to secure network communication, especially over the Internet. It functions at the OSI model's network layer (IP layer), offering data packet secrecy, integrity, and authentication. And it works on a few components to do all of this. You only need to comprehend its constituent parts to grasp how IPsec operates.
1. Security Association (SA)
The term "SA" describes a variety of protocols used to negotiate encryption algorithms and keys. Internet Key Exchange (IKE) is one of the most widely used SA protocols. The IPsec suite operates directly on top of IP (Internet Protocol), despite not being a part of it.
An SA specifies the components needed for the communicating parties to transmit data securely. These components consist of data encapsulation techniques, encryption and authentication methods, security protocols, and data transmission keys.
The local network device starts SA negotiation with the peer network device after determining which traffic is interested. During this stage, the communicating parties create IPsec SAs for secure data transfer based on the Internet Key Exchange (IKE) protocol, which they use to create IKE SAs for identity authentication and key information exchange.
2. Authentication Header (AH)
The authentication header (AH) protocol makes sure that data packets are coming from a reliable source and haven't been altered. These headers don't help hide the data from hackers; they don't offer encryption.
Data can be sent over an IPsec tunnel once IPsec SAs have been created between the communication parties.
Data is encrypted and authenticated using the Authentication Header (AH) or Encapsulating Security Payload (ESP) to guarantee data transfer security.
3. Encapsulating Security Payload (ESP)
Unless transport mode is selected, in which case it only encrypts the payload, ESP encrypts both the IP header and the payload for every packet. Every data packet has a header and a trailer added by ESP.
Data can be transmitted over an IPsec tunnel once IPsec SAs have been created between the communication parties.
Data is encrypted and authenticated using the Authentication Header (AH) or Encapsulating Security Payload (ESP) to guarantee data transfer security.
4. Key Management Protocol
Strong key management is necessary for IPsec's encryption and authentication. Cryptographic keys are established, negotiated, and refreshed between communicating entities using protocols such as IKE (Internet Key Exchange).
An encryption protocol called Key Management Protocols connects people who share keys and controls security keys. It doesn't encrypt information. Rather, key management protocols establish the framework for the operation of protocols such as IKE.
The setting of Key Management Protocols specifies the payloads that can travel over IPSec tunnels and the allowed exchange routes. The Security Association (SA) is the name given to this interaction between hosts.
There are two negotiation stages in the formation of the SA. The policies used to safeguard data and the configuration of the connection are decided by the hosts. Once that is accomplished, Key Management Protocols uses AH to implement IP authentication or ESP to control data encryption.
5. Internet Key Exchange (IKE)
The purpose of this network security protocol is to find a way through a Security Association (SA) to dynamically exchange encryption keys between two devices. SA negotiation and key management are the primary uses for IKE, an application-layer protocol based on UDP. To facilitate secure communication between two network organizations, a Security Association (SA) creates common security properties. The Internet Security Association and Key Management Protocol (ISAKMP) offer a framework for key exchange and authentication. ISAKMP explains the creation of Security Associations (SAs) and the use of IPsec in direct connections between two hosts. Internet Key Exchange (IKE) implements common algorithms like SHA and MD5 and offers an open framework for protecting message content. Each packet is given a unique identification by IP-sec users of the technique. A device can then use this identifier to determine whether or not a packet is authentic. Unauthorized packets are not delivered to the addressee; they are thrown away.
IKEv1 and IKEv2 are the two versions of IKE. In contrast to IKEv1, IKEv2 addresses a number of known cryptographic flaws, enhances security performance, streamlines the SA negotiation procedure, and boosts negotiation effectiveness.
6. Tunnel Mode
The primary IPSec configuration is tunnel mode. This mode encapsulates and encrypts the entire IP datagram, including the header, inside another IP datagram. Usually, this is used to protect communication across subnets or entire networks. In this mode, the encrypted data payload is surrounded by an IP trailer created by ESP. After being encapsulated in an extra IP header, the complete packet travels to its destination over the VPN tunnel.
In order to unwrap and decrypt IPSec packets in IPSec tunnel mode, a gateway must be set up on both sides of the process. This gateway can be a VPN router with specialized functions. It might, however, be a VPN client that is linked to a distant network. VPNs are created using this technique.
In Tunnel Mode, IPsec utilizes the modified original packet as the payload for the new packet, encrypts (or authenticates) the entire original packet, including its header, and then generates a completely new packet with a new header.
For instance, routing information regarding private networks is included in the header of a network packet that has been transmitted from or is headed to a host on one of those networks. Hackers can examine this information and utilize it for malicious intent. Connections between the gateways at the periphery of private business networks typically use Tunnel Mode, which safeguards that data. As a packet exits one network, it is encrypted and placed inside another packet that is headed to the target network's gateway. When it reaches the gateway, it is encrypted, taken out of the encapsulating packet, and transmitted to the internal network's destination host. As a result, during the packet's journey across the public internet, the header information regarding the topography of the private networks is never revealed.
The entire packet is encrypted when data moves across an IPSec VPN in tunnel mode. The internal IP header is hidden from outside observers when IP network packets are encrypted. Data is much less susceptible to hackers as a result.
Routing information can be changed as necessary by applying an additional IP header. VPN services can more easily route traffic across their servers and anonymize IP information by adding an additional header. Additionally, it aids in navigating firewalls, a task that the IPSec transport mode finds challenging.
7. Transport Mode
End-to-end encrypted tunnels are often created using transport mode, a quicker IPSec VPN method. IPsec safeguards the payload of upper-layer protocols such as TCP or UDP in this mode. Like IPSec's tunnel mode, LKE encryption protects data payloads. As usual, AH protocols authenticate packets. However, encrypt data. There isn't an extra IP header in this instance, though. The procedure is quicker and uses less data because an additional IP header is not required. Connecting distant networks to central servers is made easier using this method. However, there is a security cost.
IP data is left vulnerable in the absence of the external IP header. Additionally, transport mode may cause problems with traversal NATs and security gateways. Nonetheless, it works well for establishing direct, encrypted connections between particular devices.
Direct host-to-host and workstation-to-gateway connections are often made using transport mode. For example, a service professional might use a Transport Mode connection when utilizing Windows Remote Desktop to assist in diagnosing an issue on a user's PC.
8. Security Policies and Rules
By using the IPsec protocol, a packet may be encapsulated for safe network transit. In a site-to-site VPN, for instance, an IP packet is sent from a source host within a network. That packet contacts a VPN gateway upon arriving at the network's edge. A peer VPN gateway at the edge of the subsequent network receives the encrypted private IP packet from the VPN gateway associated with that network, decrypts it, and sends it to the target host over an ESP tunnel.
Certain security rules, policy rules, or access lists (including source addresses, destination addresses, and ports) are set up in policy-based VPNs to allow certain traffic to pass across IPSec tunnels. These rules are sent as proxy IDs in the first or second messages and are referred to during the fast mode (also known as IPSec phase 2).
9. Tunnel Endpoints
A software feature called Tunnel End-Point Discovery (TED) enables routers to automatically find IP Security (IPsec) endpoints. A crypto map that defines the endpoint to which a secure tunnel is to be formed must be configured for each peer in order to install IPsec with Internet Key Exchange (IKE). When tunnels have to be created for several peers, this method does not scale effectively. Such a situation is made simpler by dynamic crypto maps, which automatically identify the IPsec peer. Only routers that receive IKE requests can use this. TED enables routers to dynamically find the IPsec tunnel endpoint when they send and receive IKE queries.
A unique IKE packet delivered from the initiating peer to the host or network to which the original traffic was intended is called a discovery probe, and it is used by TED. The addresses must be globally routable since TED probes use the protected entities' addresses. If Network Address Translation (NAT) is enabled, TED will not function.
10. Security Gateway
Delivering quantum-safe, reliable, and secure network access to sustain our digital economy and societies is made easier with the aid of IPsec Security Gateway solutions.
In addition to offering competitive service differentiation, our 3GPP-compliant and quantum-safe technology satisfies the security needs of delicate mission-critical applications.
Establishing secure tunnels between network endpoints is made possible by the Security Gateway, which encrypts traffic to ensure that it travels through these tunnels safely.
For mobile wireless carrier networks, the SecGW is a high-density IP Security (IPSec) gateway. Backhaul traffic between the operator's core network and the Radio Access Network (RAN) is usually secured using it.
Data secrecy, integrity, and authentication between IP layer peers are provided via the open standards set known as IPSec. SecGW connects external endpoints using IPsec-protected tunnels. The components of IKE/IPSec necessary for its function on mobile networks are implemented by SecGW.
What Are the Main Differences Between Transport Mode and Tunnel Mode in IPSec?
One protocol that offers security for IP-based communication is called IPsec (Internet Protocol Security). There are two ways that IPsec can function: Tunnel Mode and Transport Mode.
When two dedicated routers are in IPsec tunnel mode, each router serves as one end of a virtual "tunnel" that travels across a public network. In IPsec tunnel mode, both the packet payload and the original IP header, which contains the packet's eventual destination, are encrypted. IPsec adds a new IP header to instruct intermediate routers on where to forward the packets. To send the packets to their intended locations, the routers at either end of the tunnel decrypt the IP headers.
Each packet's payload is encrypted in transport mode, but the original IP header is not. Thus, unless a different tunneling protocol (like GRE) is employed, intermediary routers can see each packet's final destination.
One significant distinction between Tunnel Mode and Transport Mode is the degree of encryption offered. While Transport Mode merely encrypts the packet's payload, Tunnel Mode offers end-to-end security by encrypting the entire IP packet.
Another distinction between Tunnel mode and Transport mode is the use case: Transport Mode is used for host-to-host communication, whereas Tunnel Mode is intended to connect entire networks.
The particular needs of the network and the required level of security determine which Tunnel Mode and Transport Mode is best.
Let's examine the distinction between IPsec Transport Mode and IPsec Tunnel Mode in more detail.
| IPsec Tunnel mode | IPsec Transport mode |
|---|---|
| Two IP headers are transmitted here. The IPsec policy that safeguards its contents is chosen by the inner IP packet. | The IPsec policy that will be applied to the packet is determined by the IP addresses in the outer header. |
| The contents of the inner IP packet are subject to IPsec policy. | IPsec policy can be determined by the IP header, the next header, and any ports that the following header supports. |
| Both the payload and the IP header of the original packet are enclosed in a new IP packet. | A fresh AH or ESP header is made and added immediately after the initial IP header, depending on the protocol being used. |
| The tunnel mode supports NAT traversal. | The transport mode does not support NAT traversal. |
| For instance, ASA firewalls or Cisco routers. | For instance, a Remote Desktop or Telnet session. |
What is a Tunnel Interface?
A logical (virtual) link used to transport traffic between two endpoints is called a tunnel interface.
The tunnel interface has to be assigned to a virtual router in order to utilize the current routing infrastructure, and it needs to be part of a security zone in order to apply a policy rule. In order for the firewall to execute a route lookup and identify the proper tunnel to utilize, make sure that the tunnel interface and the physical interface are allocated to the same virtual router.
A Layer 3 logical interface is known as an IPsec tunnel interface. Dynamic routing is supported. IPsec protects all packets that are forwarded to an IPsec tunnel interface, including multicast packets.
Benefits of IPsec tunnel interface
The following are some benefits of the IPsec tunnel interface:
Configuration is made simpler using the IPsec tunnel interface than with access control lists (ACLs), which are used to identify protected packets. The IPsec tunnel interface lowers maintenance costs and increases network scalability.
-
Decreased payload: Compared to IPsec over GRE and IPsec over L2TP, which need adding a GRE or L2TP header to every packet, the IPsec tunnel interface uses less bandwidth and requires fewer protocol charges.
-
Flexible service implementation: You may add a service, such as NAT or QoS, to packets either before or after IPsec encrypts them. Apply the service to the IPsec tunnel interface in order to process packets before IPsec encryption. Apply the service to the actual outgoing interface in order to handle IPsec encrypted packets.
What Encryption and Authentication Methods Are Commonly Used in IPSec Tunnels?
A software feature called IPSec encryption encrypts data to shield its contents from unauthorized access. An encryption key is used to encrypt data, while a decryption key is needed to unlock the data. Multiple encryption protocols, such as AES, Blowfish, Triple DES, ChaCha, and DES-CBC, are supported by IPSec.
To provide quick and safe data transit, IPSec employs both symmetric and asymmetric encryption. The decryption key is kept hidden with asymmetric encryption, while the encryption key is made public. Symmetric encryption encrypts and decrypts data using the same public key. In order to speed up data transit, IPSec first creates a secure connection using asymmetric encryption before switching to symmetric encryption.
IPSec has two primary wire-level protocols: Encapsulating Security Payload (ESP) and Authentication Header (AH). They encrypt plus authenticate (ESP) and authenticate (AH) the data that is transmitted over that connection. IP communication is authenticated using AH, but it is not encrypted.
Data packets are sent securely using IPSec protocols. Information is formatted and prepared for network transmission using a unique structure called a data packet. It is made up of a trailer, payload, and header.
The instructions for directing the data packet to the appropriate location are contained in the header information. The actual data that is contained in a data packet is referred to as the payload. Additional information provided to the payload's conclusion to signal the packet's termination is known as the trailer.
The following is a list of several IPSec protocols.
-
Header for Authentication (AH): In order to prevent unauthorized parties from altering the packet content, the authentication header (AH) protocol appends a header containing the sender's authentication information. It notifies the recipient of any potential modifications made to the original data packet. To make sure the header matches, the computer verifies the values of the cryptographic hash computation in the payload after receiving the data packet. A cryptographic hash is a mathematical algorithm that assigns a unique value to the data summary.
-
Security Payload Encapsulation (ESP): The Encapsulating Security Payload (ESP) protocol encrypts the entire IP packet or only the payload, depending on the IPSec mode that is chosen. Following encryption, ESP appends a header and trailer to the data packet.
-
Protocol for Internet Key Exchange (IKE): One mechanism that creates a secure connection between two Internet-connected devices is called the Internet Key Exchange mechanism (IKE). By negotiating the encryption keys and methods for the transmission and receipt of ensuing data packets, the two devices create a security association (SA).
What Are the Typical Use Cases for Implementing IPSec Tunnels in a Network?
IPsec can encrypt data sent between several network nodes, which makes it useful for building virtual private networks (VPNs). In order to create secure connections between fixed IP addresses and guarantee that all data is safeguarded from point to point, IPsec is frequently utilized. Use cases for IPsec are outlined below.
- VPNs, or virtual private networks: To safely link distant workers to the corporate network, a business employs IPsec VPNs. IPsec guarantees the confidentiality and authenticity of data sent over the internet.
- Secure Site-to-Site Communications: To ensure data integrity and confidentiality, two branch offices of a global corporation securely connect over the internet using IPsec Tunnel Mode.
- Security of Mobile Devices: IPsec is used to protect sensitive data when workers utilize public Wi-Fi by securing connections between mobile devices and corporate networks.
Real World IPsec Examples
Some real world IPsec examples are given below.
- Business VPN: A worldwide bank connects its branches throughout the world via IPsec VPNs. This configuration preserves consumer confidence and complies with regulations by guaranteeing that private financial transactions are safely sent over open networks.
- Communications from the Government:To protect communications between its data centers and distant offices, a government organization uses IPsec. This guarantees the confidentiality and impenetrability of classified information while it is being sent.
- Security of the Cloud: To protect data transfers between its data centers and client networks, a cloud service provider employs IPsec. This configuration aids in preventing illegal access and interception of consumer data.
How Does an IPSec Tunnel Contribute to the Security of Remote Access and Site-to-Site Connections?
A group of protocols known as IPsec was created to protect network-layer internet communications. It ensures that every data transfer between two locations on the internet is safe by authenticating and encrypting each packet in a communication session. IPsec can encrypt data sent between several network nodes, which makes it useful for building virtual private networks (VPNs). In order to create secure connections between fixed IP addresses and guarantee that all data is safeguarded from point to point, IPsec is frequently utilized.
One would not write their message on the exterior of the envelope while sending letters via the postal service. To prevent anybody who handles mail between the sender and the receiver from seeing their message, they instead wrap it inside the envelope. However, messages conveyed are not hidden by networking protocol suites like TCP/IP, which are primarily concerned with connection and delivery. They may be read by anybody in the center. In essence, IPsec and other encryption protocols enclose data in an envelope while it travels across networks, ensuring its security.
Is IPsec VPN Secure?
Yes. IPsec provides secure, two-way transmission over private and even public networks, including open WiFi hotspots and the global internet. IPsec uses a technique that encrypts all data in transit and effectively scrambles it so that only authorized receivers may decrypt it.
When compared to other competing protocols, IPsec's strength is its flexibility and maturity. The sheer variety of algorithms and sub-protocols available to companies allows them to design a custom communications system for remote customers. IPsec VPNs are widely used due to IPsec's standards-based approach to security, which is based on IPv4 and IPv6. IPsec uses AES-256 encryption, which is practically unbreakable by today's computing hardware, making it incredibly secure.
What is the Difference Between IPsec and SSL VPN?
SSL VPNs and IPsec VPNs protect network data but in different ways. The distinctions between SSL VPN and IPsec are as follows:
-
SSL VPN operates on a different network layer than IPsec VPN. SSL VPN runs on the application layer, whereas IPsec VPN functions on the network layer (L3).
-
IKE is a key management and authentication mechanism used by IPsec VPN. IKE generates a shared secret key using the Diffie-Hellman algorithm, which is then used to encrypt communication between two hosts. SSL VPN encrypts communication with Transport Layer Security (TLS). Public Key Infrastructure (PKI) is used by TLS for key management.
-
Pre-shared keys are necessary for IPSec connections to encrypt and transfer communication between the client and the server. SSL VPNs do not have this issue since they establish a connection and securely exchange encryption keys using public key cryptography.
-
IPsec VPN secures any traffic between two points indicated by IP addresses. SSL VPN is ideally suited for securing data sharing over the public Internet, email client-email server connection, web browser, and web server communication.
Is IPsec better than WireGuard?
Both Yes and No. The difference between WireGuard and IPsec is not one of superiority; rather, it is one of which solution is ideal for a certain case. The main difference between IPSec and WireGuard is that the IPsec is more sophisticated and out of date. Because of its smaller codebase, WireGuard is considered to deliver quicker performance and more security than IPSec. IPSec, on the other hand, is a well-developed protocol with several features and compatibility.
Can Multiple IPSec Tunnels Coexist Within the Same Network Infrastructure?
Yes. For the second site, create a new IKE gateway. then link it by creating a new IPSEC tunnel. You must declare a distinct IKE gateway/IPSEC tunnel for every tunnel you put up.
Set the peer IP to each site's IP address and configure the new ike gateway with your local IP address as the interface's external setting.
Actually, if you are using a regular tunnel on pfSense, you cannot have two IPSEC tunnels between the same two networks operational at the same time. You can have two active tunnels at once if you utilize a VTI/routable tunnel with a routing protocol that controls which way is used. Creating a dynamic DNS name for one or both sites and having it updated in the event that the primary internet connection fails is the answer for a conventional IPSEC tunnel. In this manner, only one path connects at a time, but in the event of a failure, it still switches on its own.
How Do IPSec Tunnels Impact Network Performance?
IPSec (Internet Protocol Security) tunnels are extensively used to secure data transfer over IP networks. They provide secrecy, integrity, and authentication, making them essential for establishing secure connections, particularly in Virtual Private Networks (VPNs). Nonetheless, the implementation of IPSec tunnels may affect network performance in many manners:
- Throughput reduction: The increased processing demands may lead to a reduction in the network's total throughput, so affecting the velocity of data transmission.
- Processing Delay: The need to process IPSec headers and execute cryptographic procedures may result in increased delays, especially if the network equipment is not optimized for effective IPSec traffic management.
- Encryption Overhead: The processes of encrypting and decrypting data need computing resources. This procedure may induce delay, particularly if the hardware is not optimized for encryption operations.
- Increased Packet Size: IPSec incorporates supplementary headers to each packet, hence augmenting the total packet size. This may result in fragmentation and increased bandwidth use.
Notwithstanding these possible disadvantages, the security advantages of using IPSec often surpass the performance limitations, particularly with contemporary technology capable of quickly managing encryption processes.
What Can Be Done to Optimize The IPSec Tunnels?
You can take the following actions to optimize IPSec tunnels:
-
Select the appropriate encryption algorithm: The encryption technique you select to safeguard your data is one of the most crucial elements influencing IPsec performance. Each algorithm has its own set of advantages, disadvantages, and resource needs. For instance, 3DES is an older and slower method that should be avoided if at all feasible, whereas AES is a powerful and quick algorithm that is advised for the majority of IPsec cases. Because they can affect the encryption process's speed and security, you should also take into account the key size and the encryption algorithm's mode of operation. In general, you should choose the most secure mode and the largest key size that your devices can handle without sacrificing functionality.
-
Turn hardware acceleration on: Turning on hardware acceleration on your devices is another method to enhance IPsec performance. A feature known as hardware acceleration enables specialized hardware components to carry out cryptographic operations more quickly and effectively than software. Hardware acceleration can improve the performance and scalability of your IPsec connections while lowering the CPU load, memory utilization, and power consumption of your devices. There are several techniques to add hardware acceleration, including system-on-a-chip devices, network interface cards, and dedicated crypto processors. Verify your devices' specs and capabilities, and if hardware acceleration is supported, turn it on.
-
Modify the MSS and MTU settings: Modifying the MTU and MSS values of your network interfaces and packets is a third method to enhance IPsec performance. The largest packet size that may be sent across a network link is known as the maximum transmission unit, or MTU. The maximum segment size, or MSS for short, is the largest TCP segment that may be sent via a network connection. The headers and trailers that IPsec adds to the original packets make them larger and may result in fragmentation or lost packets if they are larger than the MTU or MSS parameters. Your IPsec connections' performance and dependability may suffer from packet fragmentation and drops. Reducing the MTU and MSS settings of your network interfaces and packets to account for the IPsec cost will help you prevent this.
-
Make use of aggressive mode and IKEv2: Using IKEv2 and aggressive mode for your IPsec negotiations is the fourth method to increase IPsec performance. The protocol that creates and preserves the IPsec security associations is called Internet Key Exchange, or IKE. Better security, scalability, and flexibility are provided by IKEv2, a more recent and effective version of IKE than IKEv1. IKE's aggressive mode minimizes the quantity of messages and exchanges needed to create an IPsec security association. You may decrease network latency and bandwidth usage and expedite IPsec negotiations by utilizing IKEv2 and aggressive mode.
-
Keep an eye on and diagnose your IPsec connections: Regularly monitoring and troubleshooting your IPsec connections is the sixth method to enhance IPsec performance. Any problems or bottlenecks that can impair the efficiency and security of your IPsec connections can be found and fixed with the aid of monitoring and troubleshooting. For instance, you may verify your IPsec connections' connectivity, latency, bandwidth, and packet loss using tools like ping, traceroute, iperf, tcpdump, or wireshark. To examine the setup, status, and logs of your IPsec security associations, you may use programs like IPSEC, display crypto, or debug crypto. You can improve the security and functionality of your network by keeping an eye on and debugging your IPsec connections.
Are There Specific Challenges or Security Concerns Associated With IPSec Tunnels?
Businesses and private individuals looking to protect their online anonymity are big fans of IPSec VPN technology. However, since its creation in the 1990s, rivals have contested the IPSEC protocol. Because of this, it is crucial to comprehend its drawbacks. The broad access range of IPSec is one of its significant drawbacks. In an IPSec-based network, granting access to one device will grant access to other devices as well.
Second, a variety of software compatibility issues are introduced by IPSec. This occurs when software developers disregard IPSec standards.
Regretfully, IPSec is known to use a lot of central processing power. To cipher and decode all of the data that travels through the server, a significant amount of computing power is required.
In addition to these, the following is a list of the IPsec drawbacks:
-
Utilization of data: All traffic is encrypted by IPSec, which also uses stringent authentication procedures. Both processes increase data utilization and network bandwidth consumption. Because of this, IPSEC is a less desirable choice for networks that handle a lot of little data packets. SSL-based VPNs might be better in those cases.
-
May be misleading: IPSec provides outstanding security when properly implemented with robust IP packet encryption. However, in certain situations, this might be an issue. For instance, IPSec may unintentionally or intentionally be implemented without ESP. Managers can be unaware that data is in danger if ESP's encryption isn't in place.
-
Security issues are well known: Despite providing strong authentication and encryption, IPSec has a few well-known security flaws. First and foremost, users need to tightly regulate important interactions. Encryption keys must be kept private and hidden from prying eyes. Second, the access range of IPSec is broad. This may give users undue access to network resources, which could result in cyberattacks.
-
Complexity: Although IPSec is easy to implement, it can be difficult to use. Different characteristics are delivered by the protocol's multiple moving components. There are several steps involved in building an encrypted tunnel, including several transfers to verify, encrypt, and track data. Finding a secure configuration might be challenging due to the additional complexity caused by the availability of tunneling and transport modalities.
What Are the Best Practices for Monitoring and Maintaining IPSec Tunnels for Ongoing Security?
The recommended practices for configuring an IPsec tunnel are listed in the sections that follow.
-
Using Both Peers with the Same Configuration: Misconfiguring IPsec settings is one of the most frequent problems encountered while establishing an IPsec connection. Ensuring that both connection peers' parameters are 100% same is crucial while building an IPsec tunnel. Both connectivity and routing issues might arise if the configuration parameters for the two sides of the connection are different. The tunnel may appear in some situations, but traffic cannot be transmitted across it if the routing is not set up correctly. Thus, before configuring IPsec connection settings, you check the IPsec settings on your edge device (router, firewall, virtual machine, etc.). The IPsec site should then be configured using the same parameters.
-
Choosing an Appropriate Diffie-Helman Group: The use of an incompatible Diffie-Helman (DH) group is among the most frequent setup errors. The strength of the keys used for the Auth and Init messages between the connection peers is decided by the DH group. The tunnel cannot connect if the DH group on both sides is different. As a result, on both sides of the IPsec connection, you need to choose the DH group that matches.
For installations that employ Perfect Forward Secrecy (PFS) for key renewal, this is yet another crucial suggestion. The PFS is turned off when the DH group option is set to None. Thus, make sure the DH group is set up in the Auth Message Parameters section if you're turning on the PFS.
-
Child Security Association (SA) configuration: A DH group may appear in the Init Message Parameters for the Child Security Association (SA) even if no DH group is set up for IKEv2 in the Auth Message Parameters while you are setting the site in the Cato Management Application. This is due to the fact that the first Child SA always utilizes the same key materials as the IKE SA and is formed in the initial IKE_AUTH transaction. The DH group that is set up in the Init Message Parameters section is used by the IKE SA. The IKE_AUTH does not have a DH group exchange. A DH group is only utilized during CREATE_CHILD_SA exchanges, which either establish new Child SAs or rekey existing ones if it is set in the Auth Message Parameters section.
Mismatched DH groups set up in the Management Application and the IKEv2 peer are one thing to watch out for. Here, the tunnel first appears after the IKE_AUTH exchange, but it is unable to rekey via the CREATE_CHILD_SA exchange. Before the tunnel is restored via the IKE_SA_INIT and IKE_AUTH exchanges, there may be a temporary interruption.
-
Choosing Particular Cryptography Algorithms: Using the same encryption technique for both connection peers is crucial. On their edge devices, people occasionally activate many encryption methods rather than just one. It takes longer for the device to connect when too many algorithms are enabled. Because less is better, we advise you to only enable the algorithm you use on both sides of the tunnel. Use only the AES 128 GCM-16 or AES 256 GCM-16 algorithms for IPsec sites with bandwidth =100 Mbps. Only websites with bandwidth under 100 Mbps employ AES CBC algorithms.
-
Setting Up Primary and Secondary Networks: It is advised that you set up redundancy in both your primary and secondary IPsec connections. Additionally, you should utilize distinct destination PoPs and source IP addresses for the connections. The second tunnel forwards traffic to the other PoP in the event that one source or destination fails to connect and the tunnel goes down. No alternative connections are available to pass traffic if the source IP address you have configured in both the primary and secondary connections fails.
-
Making use of IKEv1 or IKEv2: Choose the Internet Key Exchange version (IKEv1 or IKEv2) that is compatible with your edge device when you create an IPsec site in the Management Application. IKEv2 is typically advised to be used if it is supported. The IKEv2 parameters that are available in the Management Application, however, are not supported by all devices. Use IKEv1 instead in such a situation. For instance, avoid using AES CBC 256 encryption in your IPsec setup if your firewall does not support it.