Report Views on Zenconsole
Zenarmor® has rich report views which allow you to analyze both the big picture and the detailed per-connection events. The reports may be filtered to display only the data you wish to view.
Summarized traffic data and threat activity sessions in your network may be viewed at different time intervals. With the help of Zenarmor’s reporting capabilities, you can quickly identify network security threats across your network(s).
To view the reports of a node, you may follow the next steps:
-
Select the Node that you want to view on Zenconsole UI.
-
Click Reports on the left sidebar menu.
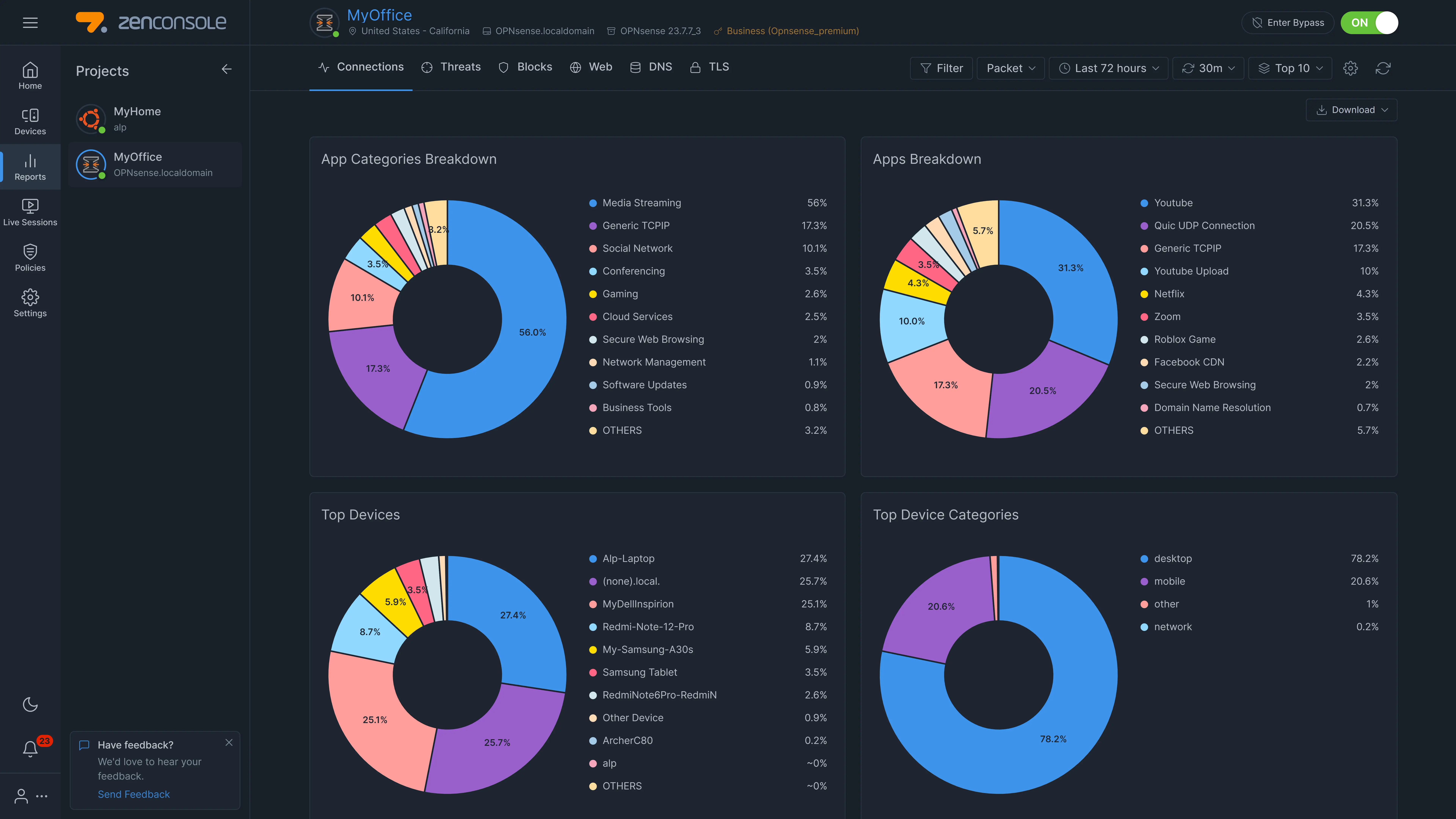
Figure 1. Viewing Zenarmor Reports
Report Views
There are six types of predefined Zenarmor report views. Each one is displayed in a different tab on the Reports page. You can easily navigate between the report views by clicking the tabs on this page.
1. Connections Report View
Connections report view shows both internal and external connections made by various applications in your network. These connections may not only be HTTP/HTTPS traffic but also any type of protocol.
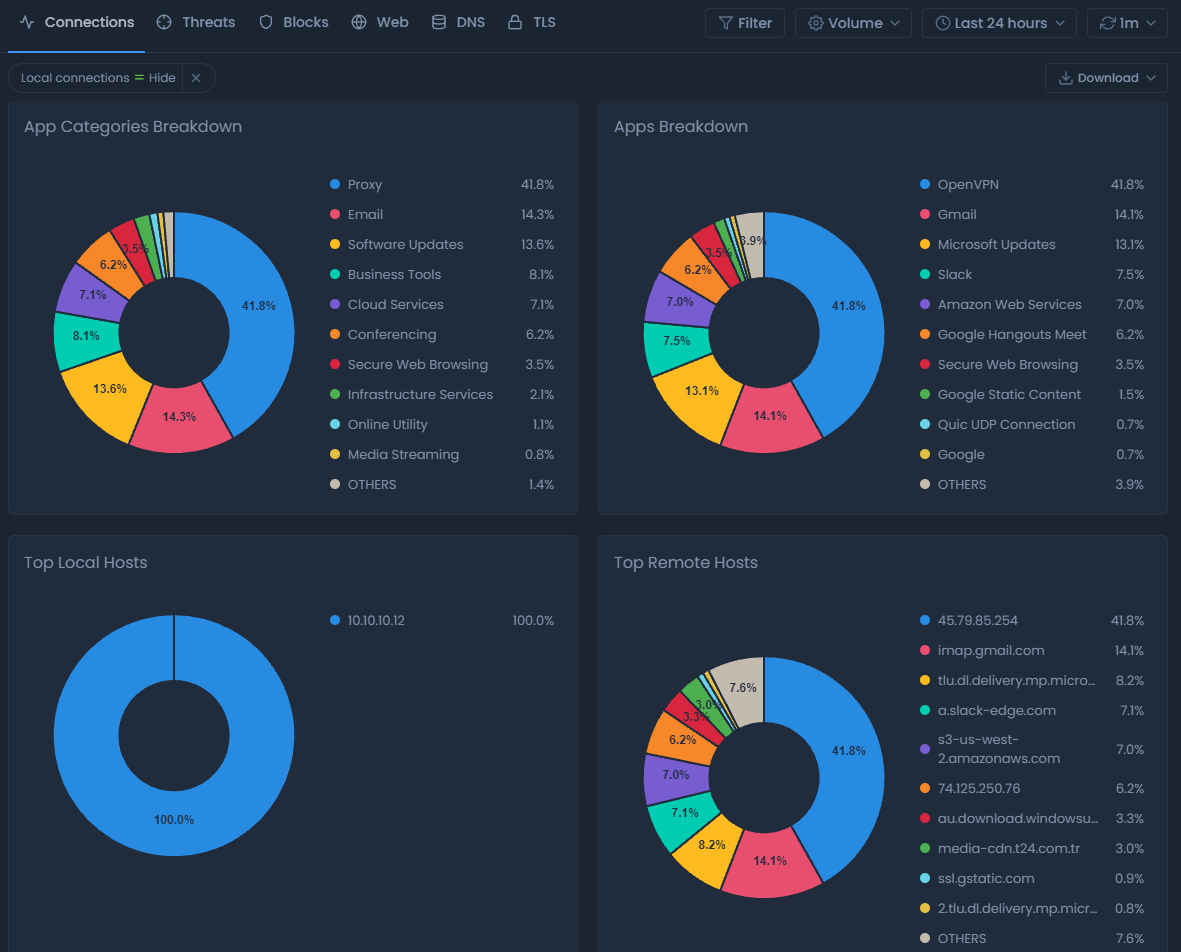
Figure 2. Connections report view
This report view includes:
-
The protocols used for the connections
-
The application name and categories
-
The duration of the connection and many other details.
There are 23 types of charts in the Connections report view:
-
App Categories Breakdown
-
Apps Breakdown
-
Egress New Connections by App Over Time
-
Egress New Connections by Source Over Time
-
Egress New Connections Heatmap
-
Table of Remote Hosts
-
Top Devices
-
Top Device Categories
-
Top Egress Users
-
Top Ingress Users
-
Top Local Hosts
-
Top Remote Hosts
-
Top Remote Ports
-
Top Locale Serving Ports
-
Top Downloaders Heatmap
-
Top Uploaders Heatmap
-
Unique Local Hosts
-
New Connections & Unique Remote Hosts
-
Facts
-
Top Destination Locations Heatmap
-
Table of Apps
-
Table of Local Assets
-
Table of Remote Hosts
-
Interfaces & Vlans
-
Policies
2. Threats Report View
If the packet engine detects suspicious activity on your network such as a spam site connection, malware activity, or a phishing server connection, you may view these security violations in the Threats tab. Any threat that has been identified by the engine based on the selected options in the Advanced Security and Essential Security panes on the Policies page will be displayed in this report view.
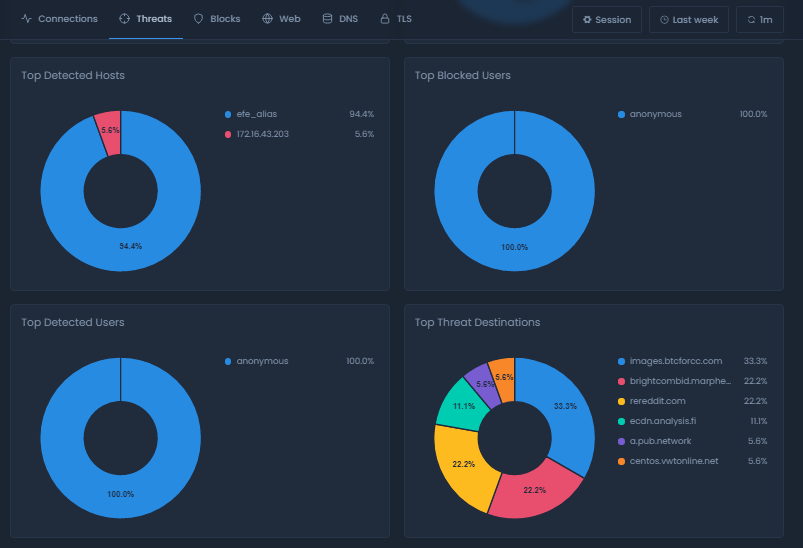
Figure 3. Threats report view
There are 15 types of charts in the Threats report view:
-
Top Blocked Devices
-
Top Detected Devices
-
Top Blocked Device Categories
-
Top Detected Device Categories
-
Top Countries
-
Threats Detected and Allowed
-
Top Detected Threats
-
Top Detected Users
-
Top Detected Hosts
-
Top Threat Destinations
-
Top Blocked Threats
-
Top Blocked Hosts
-
Top Blocked Users
-
Interfaces & Vlans
-
Policies
3. Blocks Report View
The Blocks report view displays information about the blocked sessions based on your web filtering and application control policies. If the packet engine blocks any connection according to your defined policy rules, you can find the details about these blocked connections in this view.
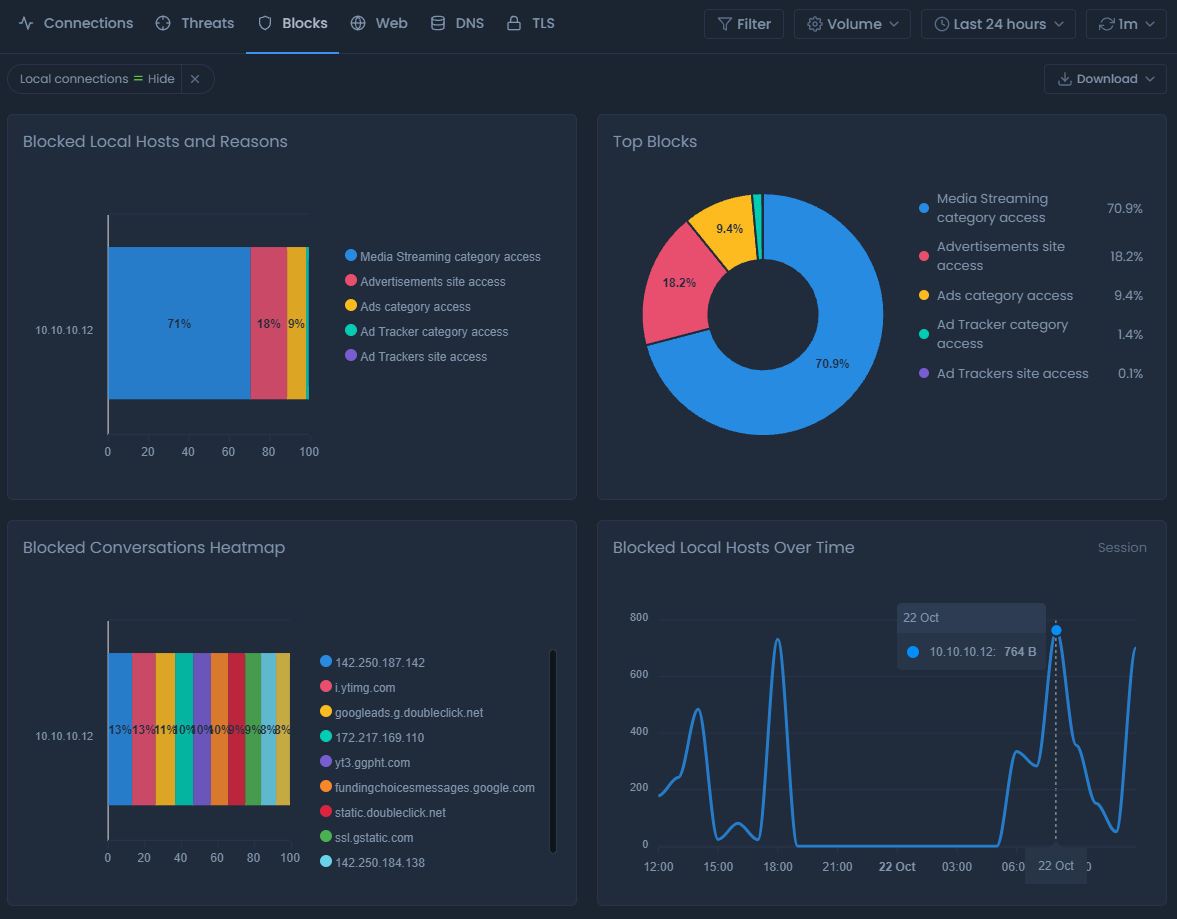
Figure 4. Blocks report view
There are ten types of charts in the Blocks report view:
-
Top Devices
-
Top Device Categories
-
Top Blocks
-
Top Egress Users
-
Top Ingress Users
-
Blocked Local Hosts and Reasons
-
Blocked Conversations Heatmap
-
Blocked Local Hosts Over Time
-
Interfaces & Vlans
-
Policies
4. Web Report View
The Web report view shows web-based traffic generated by browsing websites or API calls. This tab provides detailed information about top talker hosts, users, the request methods (GET, POST, etc.), the website category, and other information useful to monitor your network’s web activities.
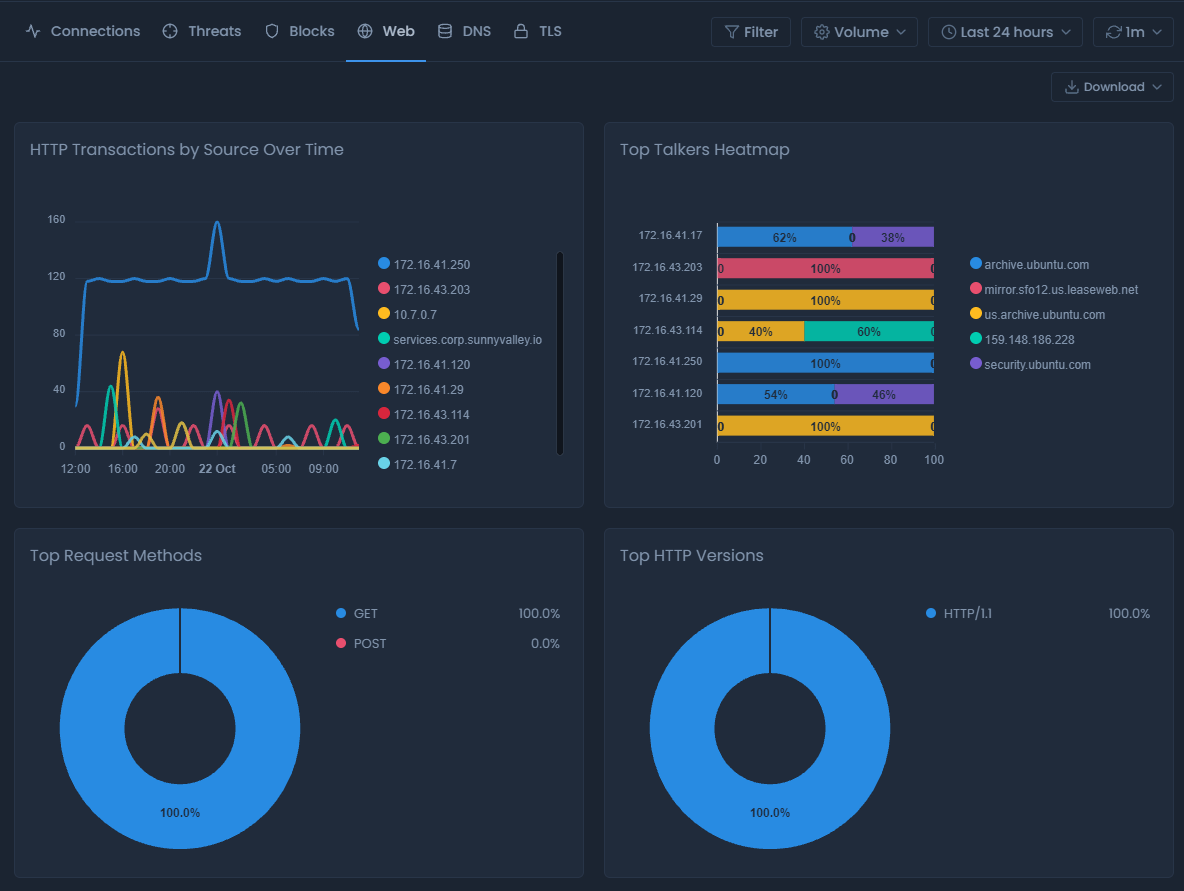
Figure 5. Web report view
There are 12 types of charts in the Web report view:
-
Top Devices
-
Top Device Categories
-
Top Eggress Users
-
Top Ingress Users
-
Policies
-
Interface & Vlans
-
Table of Sites
-
Table of URIs
-
HTTP Transactions by Source Over Time
-
Top HTTP Versions
-
Top HTTP Response Codes
-
Top Web Ports
-
Top Talkers Heatmap
-
Top Categories
-
Top OS
-
Top User Agents
-
Top Request Methods
-
Top Devices
-
Policies
-
Interface & Vlans
5. DNS Report View
You can view all information about the most frequent DNS requests and other DNS-related information on the DNS report view.
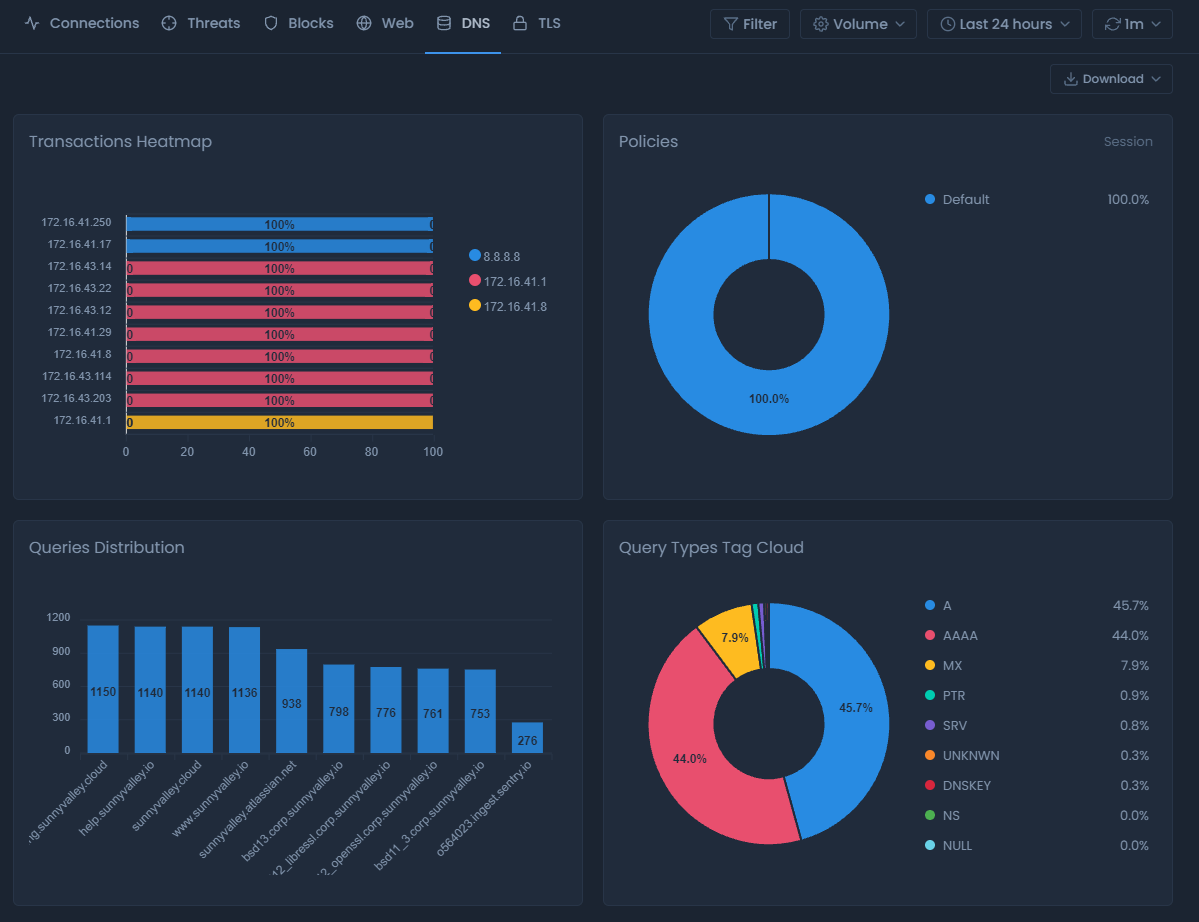
Figure 6. DNS report view
There are ten types of charts in the DNS report view:
-
Top Devices
-
Top Device Categories
-
Top Eggress Users
-
Top Ingress Users
-
DNS Query Types Tag Cloud
-
DNS Response Codes Tag Cloud
-
DNS Queries Distribution
-
DNS Transactions Heatmap
-
Policies
-
Interface & Vlans
6. TLS Report View
You can view the TLS session information such as the IP/hostname, categories of the sessions, the ports used, and other metrics in the TLS report view.
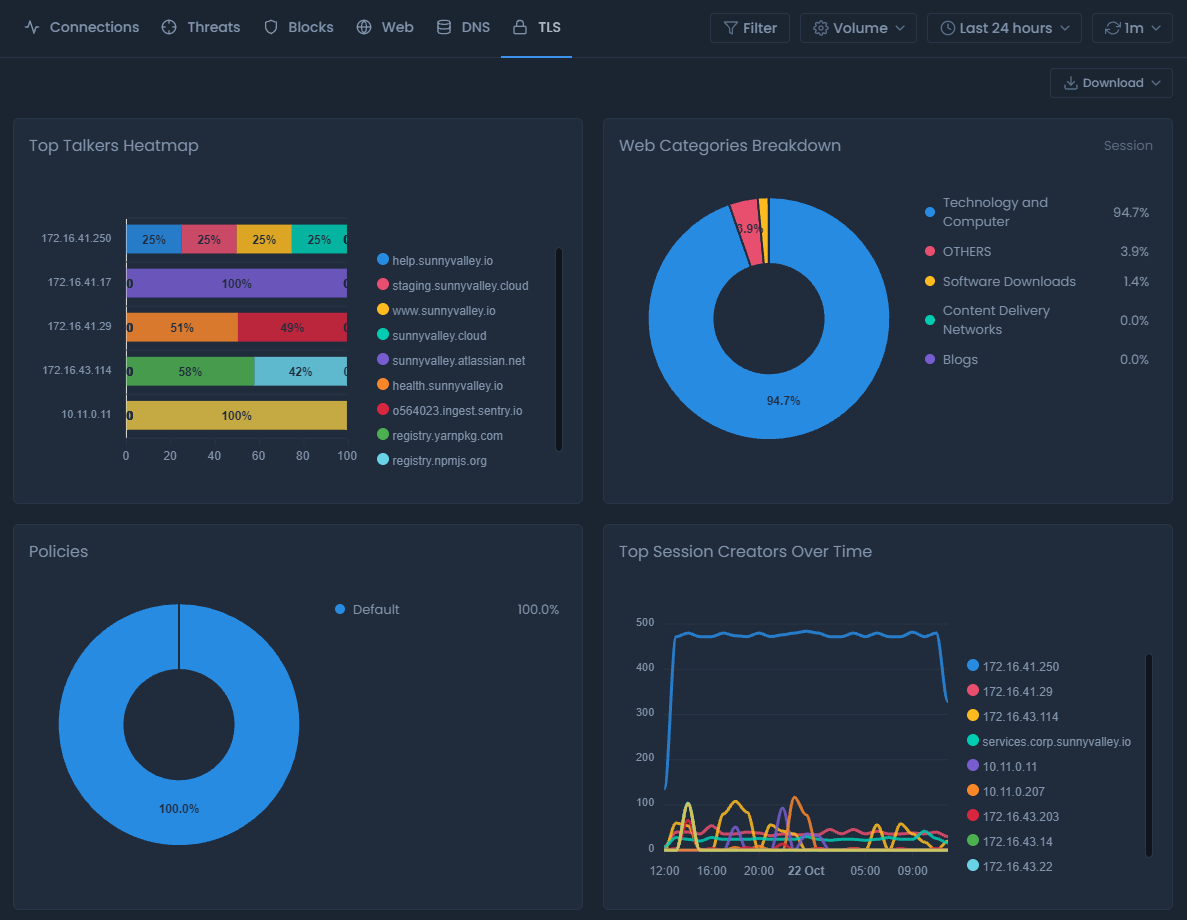
Figure 7. TLS report view
There are ten types of charts in the TLS report view:
-
Top Destination Ports
-
Top TLS Session Creators Over Time
-
Top TLS Servers Over Time
-
Top Talkers Heatmap
-
Web Categories Breakdown
-
Policies
-
Interface & Vlans
-
Top Devices
-
Top Device Categories
-
Top Eggress Users
-
Top Ingress Users