When Ransomware Meets Regulation: Why Insurance Companies Need Security That Never Turns Off
The insurance industry is one of the most attractive targets for cybercriminals. This is because insurance has three things that they look for: regulated personal data, a distributed workforce, and cloud-based networks.

Securing Remote Work Without the Slowdown
Mid-market companies have to juggle many things at once. Work is moving away from closed networks and into cloud apps, SaaS platforms, and distributed workforces. While all this is happening, they must also protect sensitive data, prevent cyberattacks, and meet regulatory and customer expectations all while doing it with fewer employees than large companies.
Why Distributed Networks Break Traditional SASE Models
Network security has long assumed that networks were distinct places, such as offices, branches, and data centers. This shaped how data flowed and how security protected it. But in today’s distributed reality, what constitutes a network is wherever work is happening.

Why Complexity Is the Biggest Security Risk in Distributed Networks
Today, most organizations have embraced remote work, cloud infrastructure, and hybrid architecture as core to their business operations. As a result, the number of organizational touchpoints has increased exponentially, introducing new layers of operational and security complexity. Each of these touchpoints, whether network storage, applications, or connections becomes an access point where attackers can gain a foothold. This sprawling business environment erodes visibility and makes it difficult to apply the same security controls consistently across users, devices, and locations.

Zenarmor 2.2 Expands DNS Integration for Secure Private Networks
Zenarmor 2.2 introduces custom DNS servers and search domains for secure private networks, giving organizations greater control and flexibility for hybrid cloud and multi-domain environments.

Bringing it All Together: A Unified Experience in Zenconsole
Discover how we redesigned Zenconsole to bring everything together in one place, creating a unified experience that feels simpler, faster, and more connected for all your Zenarmor needs.

Zenarmor + OpenWRT: Turn Millions of Existing ISP & CPE Routers Into Full SASE Edges
Zenarmor SASE 2.2 now installs directly on OpenWRT, the world's most widely used CPE/router platform, instantly converting existing gateways into fully capable SASE enforcement points. A game-changer for ISPs, MSPs/MSSPs, and distributed enterprises.

Introducing Automatic Failover Priority in Zenarmor 2.2: Smarter, Seamless Network Resilience
With Zenarmor 2.2, we introduce automatic failover priority for advertised secure private networks, improving network reliability and uptime across your secure overlay networks with simple, visual, and intuitive redundancy management.

Introducing Enhanced Site-Specific TLS Inspection Control in Zenarmor 2.2
With the release of Zenarmor 2.2, we've expanded our TLS inspection capabilities to give administrators finer-grained control over encrypted traffic. You can now specify individual websites and domains where TLS inspection should be applied.

Introducing Real-Time File Scanning: Instant Protection, Zero Blind Spots
The latest update to Zenarmor's Policy UI brings Real-Time File Scanning, now accessible within the all-new Content Inspection tab. This feature ensures every file that moves through your network is scanned instantly for hidden threats.

Zenarmor SASE 2.2 Release - The Breakthrough Release for MSPs, MSSPs & ISPs: Delivering Full SASE Edges on Existing Gateways and CPEs
Zenarmor SASE 2.2 delivers full SASE edges on existing gateways and CPEs. With OpenWRT support, device posture checks, GEO-aware reporting, and more, this release empowers MSPs, MSSPs, and ISPs to deliver stronger enforcement, better visibility, and simpler operations.

Multi-Cloud. Zero Trust. Full Speed: Security Built for the FinTech Workforce
For today’s dispersed, hybrid FinTech organizations, existing network security risks are being elevated to an entirely new level.The FinTech revolution has brought incredible agility, but it’s also multiplied exposure.
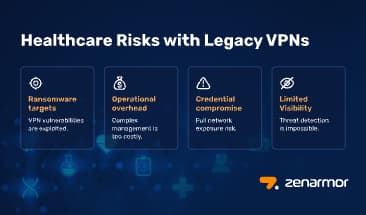
Eliminating Legacy VPNs: How Zenarmor Powers Zero Trust for Healthcare
For years, healthcare organizations have relied on Virtual Private Networks (VPNs) to secure access between users and systems. While VPNs once played an important role by creating encrypted tunnels between endpoints, they were built for a different era, when networks were centralized and most users operated within hospital walls.

Zenarmor SASE 2.1 Release: Powerful New Upgrades for Our Partners
We are thrilled to announce that the Zenarmor SASE 2.1 release officially went live yesterday, Monday, October 6th, 2025. This release delivers a redesigned Zenconsole, major Zero Trust upgrades, and important backend changes that partners should prepare for.

Some Great News! 🎉
We are excited to announce that Zenarmor has advanced to the Final Round of the 2025 SINET16 Innovator Award!🏆

Securing Healthcare in a Dispersed World: Why Compliance Can’t Wait
Healthcare systems today don’t operate within the walls of a single hospital. They are dispersed networks, spanning large hospital campuses, regional clinics, outpatient centers, imaging facilities, and even physicians’ home offices. Add in mobile nurses, third-party specialists, and remote administrative staff, and you have one of the most complex IT landscapes of any industry.

The Hidden Risks of Cloud SASE Solutions That No One Talks About
SASE has gained popularity quickly in recent times, and for good reason. It offers centralized control, cloud delivered security, and seamless security, and. All sounds too good to be true?

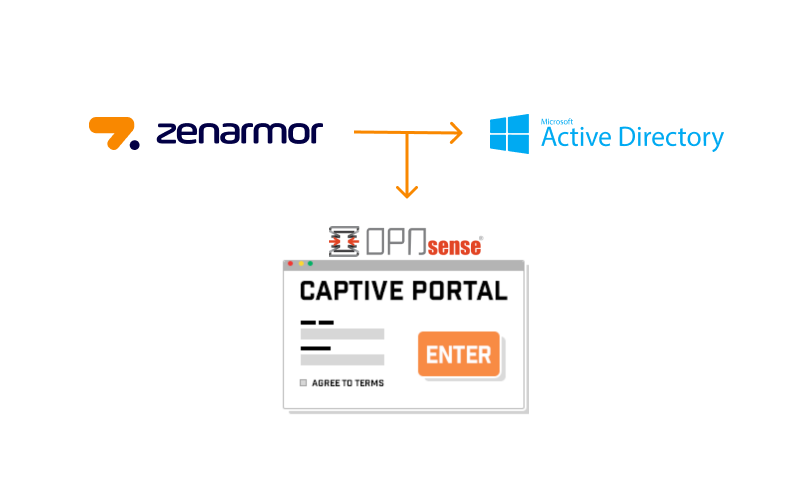
Managing Zenarmor at Scale with Microsoft Intune and Jamf
Managing security across a distributed workforce is a constant challenge. With employees using a mix of macOS and Windows devices from various locations, IT teams need a reliable way to ensure every endpoint is protected and updated without relying on manual installs or user action.

Regaining Control: How to Restore Visibility in Hyper-Distributed Networks
Everyone knows enterprise traffic is no longer confined to data centers or VPN tunnels.

What’s New in Plug and Secure Home.: More Devices, More Policies
What’s New in Plug and Secure Home.: More Devices, More Policies Zenarmor SASE 2.0 is here and it marks a turning point in how we protect networks across the globe.

A Walkthrough of Zenarmor SASE 2.0
Secure Access Service Edge, or SASE (pronounced “sassy”) was coined by the research firm Gartner in 2019 to describe a set of solutions to better protect the modern workforce. User traffic patterns shifted from occasional internet usage to being reliant on it for connectivity to the cloud and Software as a Service (SaaS) applications like Microsoft Office 365, Salesforce, Slack, and more.

Zenarmor Deploy-Anywhere SASE™ Platform: Rethinking SASE for the Real World
If you ask any IT leader today what keeps them up at night, chances are their answer is not just security. It is security at scale. As businesses strive to keep up with hybrid work, legacy technologies and remote teams, the traditional boundaries of the network have almost disappeared.

Beyond the Buzzword: Why Traditional SASE Falls Short and Zenarmor Excels
Over the past few years, a large number of tools and technologies have emerged that promise to ‘revolutionize network security’. The modern hybrid work landscape has brought Secure Access Service Edge (SASE) into the conversation too.

Traditional VPNs are Slowing you Down - And Leaving you Exposed. Here’s a Better Alternative.
Let’s face it - the way most companies handle secure access now, doesn’t cut it any more. Old school VPNs were dependable at a time when everyone worked from the office, and cloud applications weren’t a thing.

Zenarmor SASE 2.0 is Here: Plug. SASE. Everywhere. for the Modern Workforce
Today is an important day for us here at Zenarmor.

Why Zenarmor 1.18 is a Game-Changer in Boosting Revenue for MSPs and MSSPs
Endpoint devices like laptops and desktops often operate beyond the traditional security perimeter, exposing organizations to increased risks. Employees frequently connect to unsecured public WiFi networks. While VPNs are usually deployed to mitigate this, they come with limitations, including performance bottlenecks, poor user experiences, and the risk of being entirely bypassed. These gaps leave businesses vulnerable, creating a growing demand for more effective, seamless security solutions.

Zenarmor 1.18 is here, ready to secure your distributed, remote workforce
Zenarmor 1.18 has arrived, and it is one of the most feature-packed releases yet! In this release, we are one step closer to achieving our goal of delivering a truly remarkable Secure Access Service Edge (SASE) product to help address the security concerns of an ever-expanding hyper-distributed, remote workforce making use of our industry-first Plug. SASE. Everywhere. approach to network security.

Why conventional Secure Access Service Edge Solutions (SASE) are not so sassy after all
You’ve been working from home for a few years now, enjoying the flexibility and comfort it offers. But imagine this: your manager announces that the company is shifting back to a pre-COVID working style, meaning you’ll need to return to the office. Who would be happy about this change? Surprisingly, among the few colleagues who might welcome the idea, the security team stands out.

Zenarmor 1.17 TLS Inspection Statement
We have noticed some chatter about our latest release of Zenarmor 1.17 across various social channels. While it has been received well by the large majority of our customers, we have noted some concerns or confusion about our newly added Security Service Edge (SSE) subscription as well as the Full TLS Inspection capabilities made available in this release. We would like to take the opportunity to provide some clarity about this and our future roadmap.

Clarifying the Road Ahead: Zenarmor's Strategic Vision and Product Roadmap
Recent updates, particularly with the release of Zenarmor 1.17 and the integration of new advanced capabilities like full TLS inspection, have sparked discussions among our partners and users regarding Zenarmor's commitment to supporting open-source firewalls and its evolution within the network security landscape. This blog post aims to dispel any confusion about our product roadmap, reaffirm our commitment to delivering top-tier security solutions, and address any concerns our loyal community may have.

Zenarmor’s all-new Full TLS Inspection Capability - What to Expect in Zenarmor 1.17
If the title was not enough to give it away, the long-awaited full TLS inspection capability will be officially launched in Zenarmor 1.17 and is our latest enterprise-focused capability for users with existing business subscriptions.
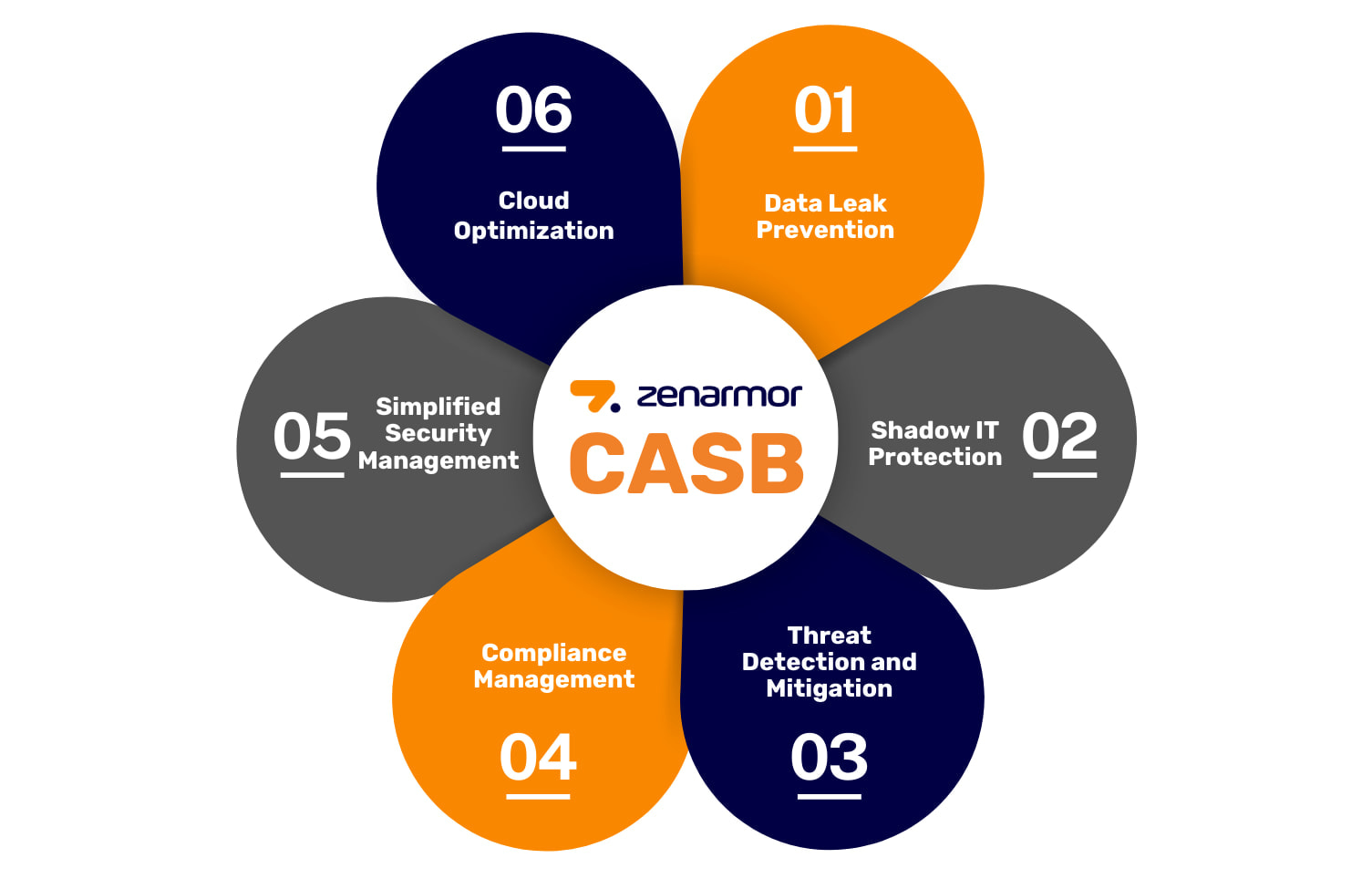
Why CASB is a need for Businesses?
Cloud has emerged as a transformative technology for all businesses regardles of their size and area of operation, as it provides access to sophisticated tools and capabilities needed to gain a technological edge without requiring substantial capital investment. However, along with this opportunity, there's also the hidden danger of security.
Zenarmor Device Identification and Access Control - A Practical Guide
Device Identification and Access Control were introduced along with other new capabilities in Zenarmor 1.16, and are available with all paid subscription plans. This capability was built keeping in mind the importance of IT asset management (ITAM) in any organization and is our simple approach to this process, which can sometimes be a mammoth task to accomplish without the correct tools. Since its introduction, this new Zenarmor engine capability has been received well by the general Zenarmor community.
The Challenge of Balancing Security and Productivity
Balancing cybersecurity with efficient workflow is a critical challenge in many organizations. Firewalls, while crucial for safety, can sometimes block access to websites needed for work. Zenarmor offers a practical solution to this problem through its bypass codes. These PIN codes are designed to grant users access to specific websites blocked by the firewall, ensuring that productivity is not hindered by security measures. This post will explore how Zenarmor’s bypass codes effectively bridge the gap between maintaining robust security and facilitating uninterrupted work.

Enhance Network Security with Zenarmor's TLS Inspection Feature
In today’s digital world, data security is more important than ever. Network security becomes challenging as more websites and applications use encryption to protect their data in transit. How can you ensure that the encrypted traffic on your network is not hiding malicious content or activities? The answer is TLS inspection.
The Core of Network Security: Device Identification Defined
In this blog post, we will explore the definition and role of device identification in network security, the risks of unidentified devices, and how device identification empowers security with various controls. We will also give you a sneak peek at Zenarmor’s device identification feature, which is available in paid editions to enhance your network security.

How Zenarmor Can Help Manufacturing Organizations Overcome Cybersecurity Challenges
Cybersecurity has emerged as a critical concern in today's highly interconnected manufacturing domain. As manufacturing organizations embrace digital transformation, they face heightened vulnerabilities and sophisticated cyber threats. From safeguarding critical systems and IoT devices to defending against intellectual property theft, they must adopt effective security solutions to protect their operations and assets.
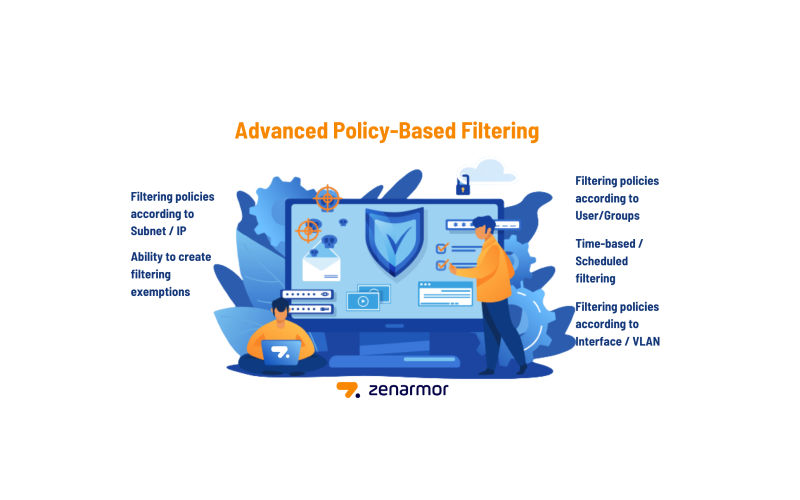
Mastering Network Control with Advanced Policy-Based Filtering
Network control and security are vital for any organization that wants to protect its data and resources from cyber threats. However, traditional firewalls and network devices are often limited in their ability to handle the complexity and diversity of modern network traffic. How can you achieve granular and flexible control over your network without compromising performance or usability? The answer is advanced policy-based filtering.
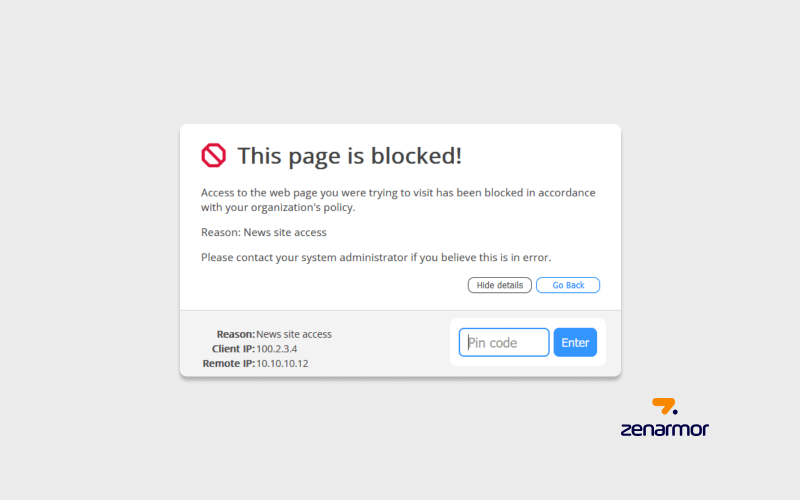
Transparent Security: How Web Blocking Explanations Enhance Online Safety
Web blocking explanations, an indispensable component of network security, play a pivotal role in safeguarding digital ecosystems. In an increasingly interconnected world, understanding the significance of these explanations is paramount. Web blocking explanations serve as the digital sentinels, elucidating the 'why' and 'how' behind the prohibition of certain web content. This transparency not only empowers administrators and end-users with insight but also aids in fostering a secure online environment.
Step into Zenarmor's Integration Galaxy: Your Passport to Advanced Security
The digital landscape of today is fast-evolving, and comprehensive security insights are not just a luxury but have become an absolute necessity. Cyber threats evolve in complexity every day, making it vital for organizations to stay one step ahead. This is where integration comes into play.

Streamline Enterprise Firewall Management with RESTful API
Imagine you are a network administrator who needs to monitor and control the network activity of hundreds or thousands of users in your organization. You want to ensure that your network is secure, compliant, and efficient, but you also want to respect the privacy and preferences of your users. How can you achieve this balance without spending hours on tedious manual tasks or compromising performance and reliability?
Empower Your Network Security with User-Based Reporting
Imagine you are a network administrator who needs to monitor and control the network activity of hundreds or thousands of users in your organization. You want to ensure that your network is secure, compliant, and efficient, but you also want to respect the privacy and preferences of your users. How can you achieve this balance without spending hours on tedious manual tasks or compromising performance and reliability?

Beyond the Shadows: Why You Need Better Reporting Against Cyber Threats
In network security, information is power. Enterprises rely on comprehensive data and insights to make informed decisions, enhance their security postures, and swiftly respond to emerging threats. This is precisely where our advanced security solution truly shines.
In this blog, we embark on a journey to explore the capabilities of advanced reporting with Zenarmor, shedding light on how they can empower organizations to bolster their cybersecurity strategies.
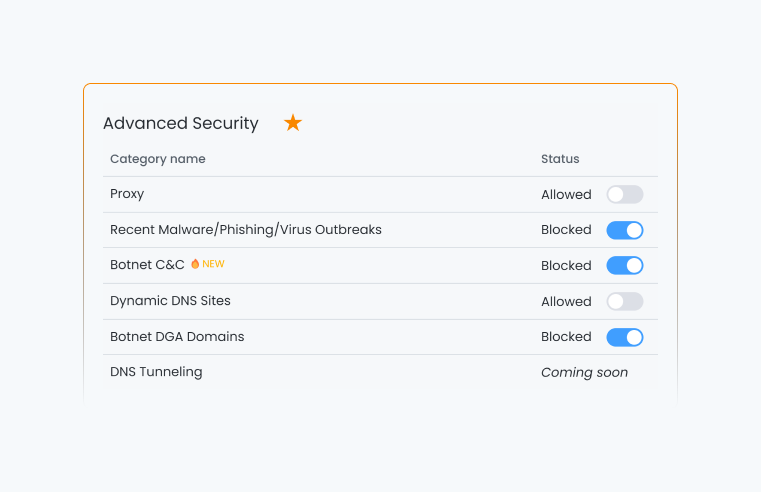
Zenarmor Advanced Security Rules: Staying Ahead of Emerging Threats
The digital landscape that we are navigating today is ever-evolving. Staying ahead of emerging cyber threats is paramount for organizations of all sizes. As the sophistication of malicious intruders continues to grow, so must our defenses. This is where advanced security rules come into play; they are the frontline of defense in safeguarding your network, applications, and sensitive data.
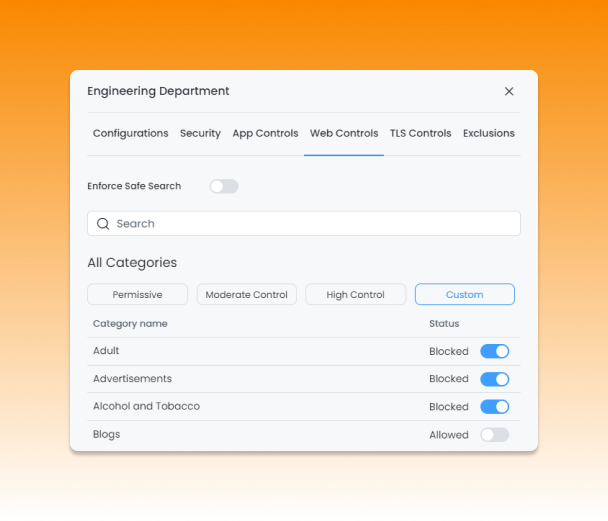
Gain Granular Control Over Web Access with Zenarmor Custom Web Profiles
In the dynamic field of cybersecurity, the importance of tailored solutions cannot be overstated. As digital threats grow in complexity and diversity, organizations must have the tools to adapt and strengthen their defenses. This is precisely where the significance of custom web profiles in network security comes into play, offering a dynamic means of safeguarding digital landscapes against cyber threats.
Strengthen Your Security Posture with Multiple Policies
In cybersecurity, where threats get complicated, it's important to be flexible and strengthen your defenses. This article examines an essential way to improve your cybersecurity strategy: implementing multiple security policies. Like a secure web gateway (SWG) such as Zenarmor, which can be a key part of a DIY Secure Access Service Edge (SASE) setup, having different security rules in your organization's plan can boost its overall resilience.

Advanced Security, Simplified Experience: Zenarmor’s Agile Approach to Safeguarding UK Students Online
In today's interconnected digital age, school environments are no longer just physical spaces. They are also vast, intricate digital networks where students engage and learn.
However, as the children navigate this space with youthful curiosity, they face a barrage of risks that can often be invisible to the untrained eye. From harmful content like racism and extremist ideologies to insidious threats like phishing scams and online gambling, the online world presents challenges that can impact their mental, emotional, and even physical well-being

Towards a device-agnostic netmap in the FreeBSD kernel
As some might have already noticed, OPNsense’s 23.1.6 release has delivered some important kernel updates to the netmap subsystem. The goal of this blog post is to provide some insights into what we’ve been up to and what we’re planning to do in the future in the context of improving device driver support for the netmap subsystem in the FreeBSD kernel.

Why is Zenarmor the perfect content-filtering solution for educational institutions?
It’s a necessity that educational institutions implement proper cyber security and access control measures, not only to protect their systems, teachers and administrators, but most importantly, the bright and impressionable minds accessing these systems and internet services. In this article, we are going to unpack the benefits and capabilities of Zenarmor and look at how it provides a formidable content filter, protecting minors and students alike from inappropriate online content and online threats.

How MSSPs can leverage Zenarmor combined with open-source firewalls to increase the value of their offered services
There has never been a more exciting time for MSSPs. With more businesses adopting the cloud and staff working remotely from anywhere, it can be challenging for organizations to navigate this new territory, especially when it comes to providing and managing their cybersecurity requirements. Here are all the ways Zenarmor favors MSSPs.

How will Zenarmor SWG as a policy-driven cloud egress traffic filtering and control solution improve your network security?
In this article we are going to explore why Zenarmor SWG should be the first product to come to mind, when looking for a rapid-to-deploy, low-cost, cloud egress traffic filtering and control solution, with the ability to control all Zenarmor SWG deployments from a centralized control panel.

How to use a cloud-deployed Zenarmor SWG to secure cloud resources and users in a DIY SASE architecture
If you're an enterprise or MSSP, you can now easily deploy Zenarmor as a Secure Web Gateway solution to keep your network safe and clean from malicious attacks on the internet.

How OPNsense and Zenarmor® Next Generation Firewalls Help Schools Optimize their Networks and Increase Security
Typical educational institution computer networks, from K-12 to College and Universities, are much like enterprise networks. Devices ranging from mobile phones to tablets, desktop computers,…