
Outdated Network Architectures Are Holding You Back
The modern workplace is no longer confined to a single office or data center. Teams, devices, and resources are now scattered across the globe, and legacy networking solutions simply weren’t built for this level of distribution
Traditional VPN and MPLS architectures were designed for a different era. While they still function, they fall short in today's environment:
Lack of Granular Access Control
Lack of Granular Access Control: These solutions typically grant broad network access, increasing your attack surface and violating zero-trust best practices.
Limited Visibility
Limited Visibility: Traditional architectures often obscure user activity and application-level traffic, making threat detection and policy enforcement difficult.
Operational Complexity
Operational Complexity: From managing tunnels to provisioning remote sites, setup and maintenance can be time-consuming and error-prone.
High Costs
High Costs: Expensive hardware, licensing, and infrastructure requirements make scaling both cost-prohibitive and slow.
Zenarmor ZTNA: Built for the Way You Work Today
Zenarmor’s Zero Trust Network Access (ZTNA) redefines secure connectivity by eliminating the need for outdated perimeter-based models.
Instead of forcing users through complex gateways or tunnels:
Direct, Secure Access
Direct, Secure Access: Users connect only to the specific applications and resources they need — nothing more, nothing less.
Automatic Policy Enforcement
Automatic Policy Enforcement: Application and identity-based access controls are enforced dynamically, behind the scenes.
Simple to Deploy, Easy to Scale
Simple to Deploy, Easy to Scale: With minimal configuration, you can get up and running fast, without the heavy overhead.
Zero Trust by Default
Zero Trust by Default: Enforce least-privilege principles and ensure secure, context-aware access regardless of location.
Zenarmor ZTNA is the painkiller to your legacy networking headaches — modern security, simplified deployment, and total control from day one.

Easy to deploy Zero Trust Network Access, the Zenarmor way
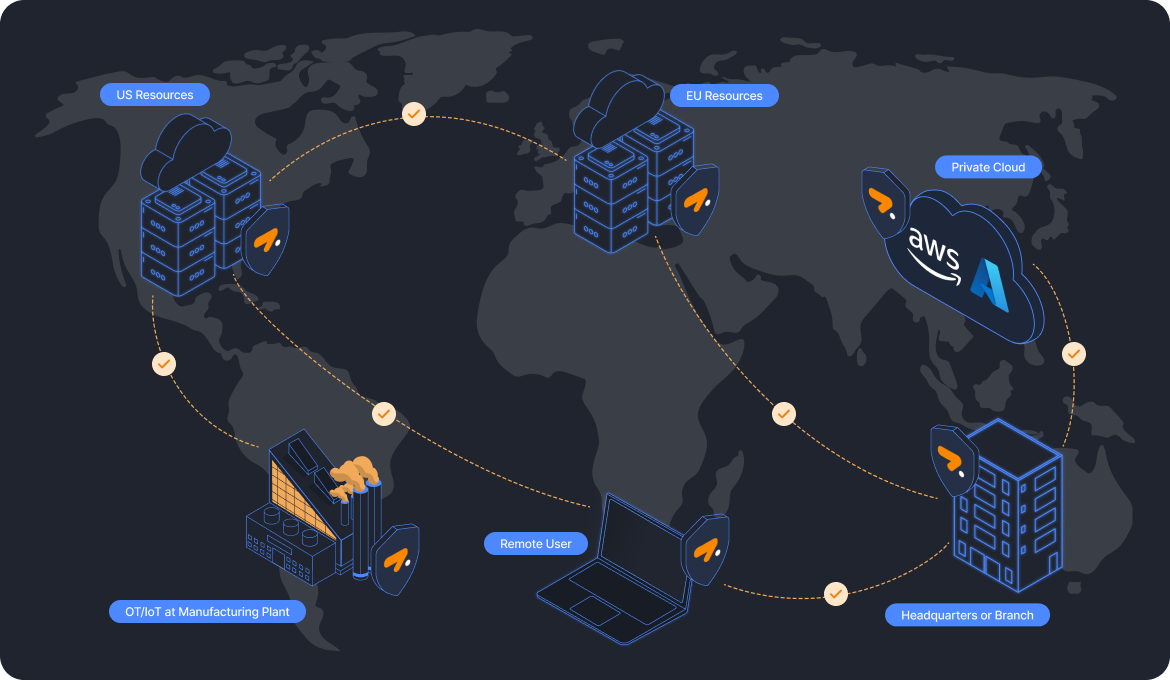
What you can expect from Zenarmor ZTNA

Secure access to enterprise private assets and networks.

Direct connectivity, no more VPN concentrators.

Resource-level authentication and access control.

Policy-driven connectivity.

Peer-to-peer and mesh-connected setup options.

Application control and micro-segmentation, island your resources reducing lateral movement and blast radius.

Zero-configuration client-side agent, install and forget.

End-to-end encryption.

Easy deployment.

Fulfill least-privilege and zero-trust requirements.
Testimonials
Watch Zenarmor in Action
Unlock the potential of Zenarmor to effectively tackle your connectivity and security challenges. Dive into our compelling use cases below to see the difference it can make!













