In cybersecurity, where threats get complicated, it's important to be flexible and strengthen your defenses. This article examines an essential way to improve your cybersecurity strategy: implementing multiple security policies. Like a secure web gateway (SWG) such as Zenarmor, which can be a key part of a DIY Secure Access Service Edge (SASE) setup, having different security rules in your organization's plan can boost its overall resilience.
Figure 1: Zenarmor Policies Dashboard
In this discussion, we'll talk about the idea of using multiple security policies to make your defense stronger. We will explore how this approach lets organizations customize their security to their needs, effectively mitigating risks and responding to emerging threats. By the end of this article, you'll understand how strategic deployment of multiple policies can help your organization be more flexible, adapt to changes, and stay on top of cybersecurity initiatives.
Challenges of a Single Default Policy: Breaking Through Security Limitations
In cybersecurity, using a single default security policy is a common practice, often serving as a baseline for network protection. But this approach has its drawbacks. A single default policy typically covers the essentials of network protection, such as blocking known threats and adhering to compliance standards. While that's important, it often can't adapt to modern organizations' unique and evolving security needs.
Imagine a company that relies only on one default rule for its network security. It might give reasonable protection against known threats, but it could unintentionally limit what users can do that's legitimate. For instance, stringent web filtering might block access to essential resources or applications required for specific job functions, affecting productivity. Also, this one-size-fits-all approach might not work well against emerging threats or sophisticated attacks that bypass conventional security measures. The limitations of a single default policy become evident when organizations require tailored security measures to safeguard critical assets and adapt to the evolving threat landscape.
Empower Your Security: Advantages of Multiple Policies
Relying only on a single default security policy can pose challenges in today's cybersecurity landscape. Fortunately, a flexible solution to overcome these limitations is to use multiple security policies. Moving from the constraints of a single policy to a more diverse approach opens up many possibilities to strengthen your organization's security. Organizations can adjust their security to their needs and adapt swiftly to emerging threats. The benefits of adopting multiple security policies are numerous and will be discussed further in the upcoming sections.
Crafting Time-Based Policies: Flexibility Tailored to Needs
Time-based policies provide a level of flexibility tailored to specific organizational needs. This feature can adjust security rules based on different timeframes dynamically. Imagine a scenario where an organization needs to bolster security during non-business hours while allowing more relaxed access during the workday. Time-based policies enable this customization, allowing administrators to automatically tighten security measures during off-hours and ease restrictions during peak productivity periods. Implementing this feature typically involves defining and associating timeframes with corresponding security rules, ensuring that security adapts seamlessly to the organization's operational schedule, and enhancing protection without sacrificing efficiency.
Varied Policies for Different Users: Security Tailored to Requirements
One of the key advantages of implementing multiple security policies is the ability to create distinct policies for different user groups, thus tailoring security measures to meet specific requirements. Organizations often consist of various departments and roles, each with unique responsibilities and access needs. Organizations can ensure that security protocols align with individual roles and responsibilities by crafting varied policies for different user groups. This approach allows for fine-tuning security levels, granting access to the right users while maintaining a robust overall security posture. Such customization enhances protection and minimizes the risk of over-restricting or under-protecting specific user segments.
Device-Specific Policies: Isolation and Enhanced Protection
Varied policies for device-specific security offer a significant advantage in cybersecurity. In today's digital landscape, organizations often rely on many devices for their operations, each with unique security needs. A one-size-fits-all approach is ineffective in addressing these diverse requirements. Crafting device-specific policies enables organizations to isolate and enhance protection as needed. For instance, stricter controls can be placed on servers to safeguard data integrity while allowing more lenient smartphone access to maintain user flexibility. This approach ensures that each device receives tailored security measures, optimizing protection while accommodating diverse organizational roles. By embracing this level of customization, organizations can strengthen their defenses, ensuring that security aligns with the specific demands of each device in their network.
Create Your Own Security Policies: Step-by-Step Guide
Creating your own security policies empowers you to take control of your organization's cybersecurity strategy. This step-by-step guide will walk you through crafting tailored security policies that align with your unique needs and priorities. By the end of this walkthrough, you will have the confidence and expertise to design security policies that bolster your defenses and adapt seamlessly to the evolving threat landscape.
Crafting Time-Based Policies: Policies Aligned with Specific Timeframes
Crafting time-based policies is crucial to aligning your security measures with specific timeframes and enhancing your organization's cybersecurity strategy. These policies enable you to adjust your security rules dynamically based on different periods of the day or week. For instance, you can tighten security during non-business hours to ward off potential threats while easing restrictions during peak operational times.
For a practical example of implementing time-based policies, consider Zenarmor, a robust cybersecurity solution. Zenarmor allows you to create time schedules within your policies to control when those policies are active. Here's how you can use time schedules with Zenarmor:
- Creating a New Schedule:
- In the Zenarmor interface, click on the "+Add New Schedule" button in the Time Schedules pane.
- A dialog box will open where you can name the schedule. For instance, you can name it "Non-Business Hours."
- Enter the name and click the "Add" button to add the new schedule to the Time Schedules list.
- Defining Active Days and Hours:
- Select the specific days you want this schedule to apply to. Selected days will be displayed with a solid blue checkmark icon.
- Specify the starting and stopping hours for which the policy will be effective. For example, you might set it to be active from 6:00 PM to 6:00 AM.
- Managing Schedules:
- All added time schedules are listed in the Time Schedules pane for your reference.
- You can easily update the existing time schedule by adjusting the start/stop hours and selecting deselecting the days as needed.
- If you need to remove a schedule, simply click on the "Remove" button with a trash icon and confirm the removal when prompted.
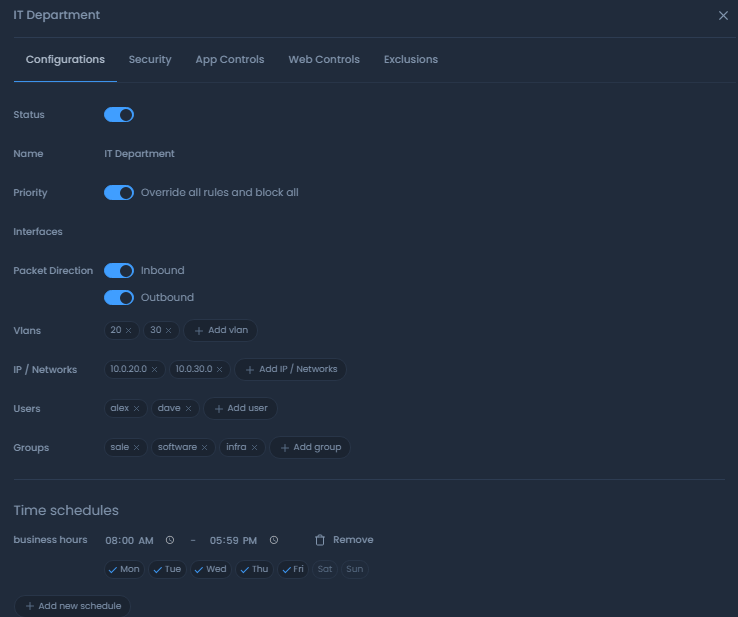
Figure 2: Time Scheduled Policy configuration with on Zenarmor
By incorporating time schedules into your policies with Zenarmor, you can tailor your security rules to align with your organization's operational schedule. For instance, you can apply stricter security measures during non-business hours when the network may be more vulnerable and relax these rules during peak operational times to ensure smooth workflow. This dynamic approach to cybersecurity helps keep your organization protected precisely when and where it's needed most.
Designing Policies for Different Users: Customized User Groups
Designing policies for different users and user groups is a crucial aspect of customizing your organization's cybersecurity strategy. Zenarmor offers user-based policy filtering, which allows you to create policies tailored to specific users or groups. This capability is essential because organizations often have diverse departments and roles, each with distinct responsibilities and access requirements.
Here's how you can enhance your cybersecurity strategy using Zenarmor user-based policy features with MS Active Directory or OPNsense Captive Portal integration:
- User-Based Policies:
- Navigate to the Configuration page of the policy you want to customize.
- Click on the "+ Add user" button to associate a specific user with the policy.
- Enter the username you wish to apply this policy to.
- Click the "Add" button to confirm the association.
For example, for the finance department, you can create a policy that enforces stringent access controls for users handling sensitive financial data.
- Group-Based Policies:
- Similarly, you can create policies based on user groups.
- Click on the "+ Add group" button in the policy configuration.
- Enter the group name you want to associate with the policy.
- Click the "Add" button to confirm the group association.
For instance, marketing teams may require policies with more relaxed restrictions to encourage creativity and collaboration.
- Fine-Tuning Security:
- Once you've associated users or groups with policies, these policies can have specific security rules that cater to their unique needs.
By implementing user and group-based policies, you can ensure that security measures are aligned with individual roles and responsibilities within your organization. This approach allows you to:
- Grant the appropriate level of access to users, ensuring that sensitive data remains protected.
- Customize security settings based on department requirements, promoting flexibility and productivity.
- Maintain a robust overall security infrastructure while accommodating the diverse needs of your organization.
Zenarmor's user-based policy filtering empowers you to create a cybersecurity strategy that is not only effective but also tailored to the specific requirements of different users and user groups within your organization.
Tailoring Policies for Various Devices: Comprehensive and Adaptable Protection
In the ever-evolving landscape of technology, adapting security rules to cater to different devices is paramount to achieving comprehensive and flexible protection. Zenarmor, a software-based firewall, excels in this regard by offering device identification and asset discovery features. These capabilities enable Zenarmor to effectively block and filter devices based on their unique characteristics, including MAC addresses, IP addresses, and network attributes.
Here's how Zenarmor enhances your cybersecurity strategy with its device-based blocking capabilities:
- IP / Networks Policies:
- Zenarmor allows you to create policies that are specifically applied to IPv4/IPv6 addresses.
- You can input single IP addresses.
- Additionally, you have the flexibility to include descriptions for these entries, making it easier to recall the purpose of each IP address.
- MAC Addresses Policies:
- Zenarmor empowers you to establish policies that target devices based on their MAC addresses.
- You can assign descriptions to these entries, ensuring clarity about which device each MAC address belongs to.
We're also excited to announce that Zenarmor is actively developing an advanced device identification feature that will soon be available to enhance your network security. Stay tuned for its upcoming release as we continue to prioritize your cybersecurity needs.
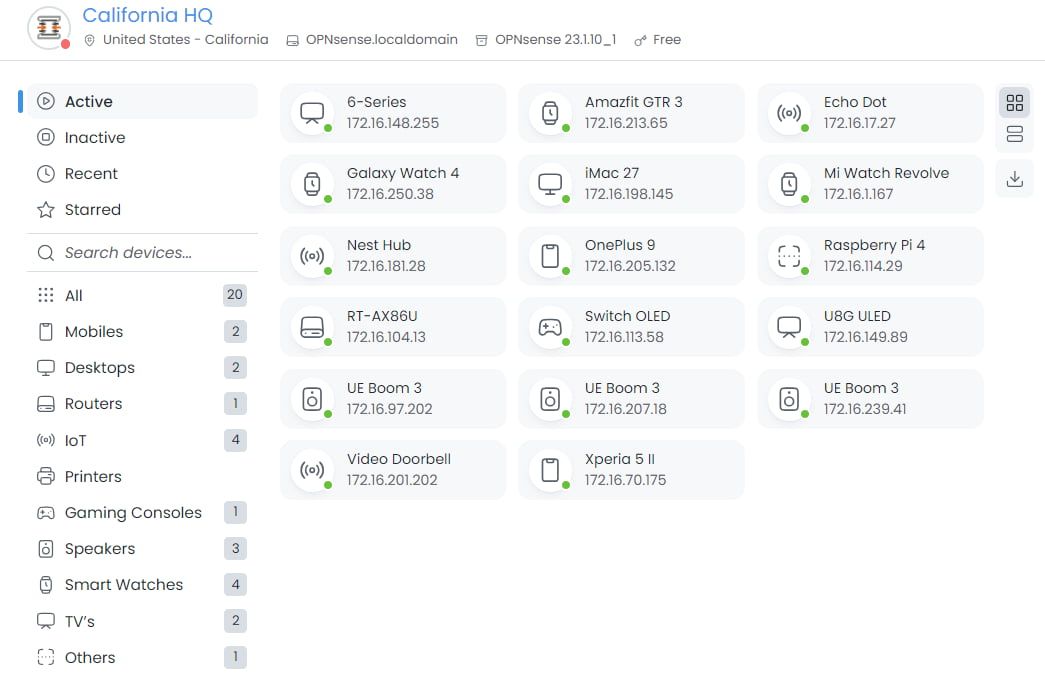
Figure 3: Zenarmor Device Identification Dashboard
By leveraging Zenarmor's device identification and policy customization capabilities, organizations can effectively address the specific security needs and vulnerabilities of various devices within their network. This approach offers several advantages:
- Tailored Protection: Security rules can be fine-tuned to match the unique features and requirements of different devices, such as smartphones, laptops, and IoT devices.
- Threat Mitigation: Device-specific policies allow organizations to address vulnerabilities and weaknesses unique to each device type, bolstering defenses against potential threats.
- Resource Optimization: By customizing security rules, organizations can allocate security resources efficiently, ensuring that devices with higher security needs receive the appropriate level of protection.
Zenarmor's device-based blocking capabilities enable organizations to craft a flexible and comprehensive cybersecurity strategy. This strategy ensures that security measures are precisely aligned with the characteristics and security needs of individual devices, ultimately enhancing the overall security posture of the organization.
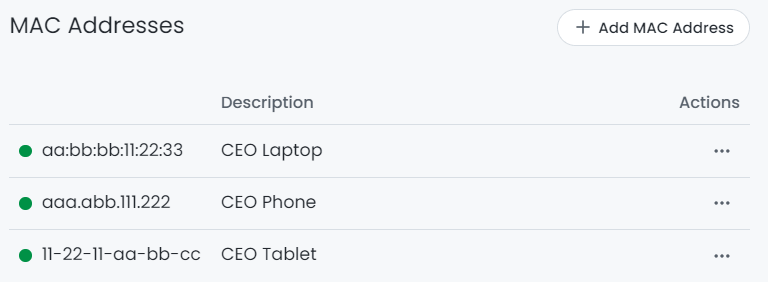
Figure 4: Device-based filtering using MAC Address on Zenarmor
Understanding Policy Allocation: How Many Policies Does Each Plan Include?
We understand that as your digital infrastructure expands, the need for flexibility in policy allocation becomes crucial. In today's dynamic landscape, organizations must tailor their security measures to meet evolving needs while staying within the bounds of their subscription plans. To clarify policy allocation, Zenarmor offers various subscription plans, each with a distinct policy allocation structure. These plans are designed to cater to different organizational sizes and requirements. By visiting the plans page, you can explore the detailed breakdown of policy allocation for each plan, making it easier to choose the one that best suits your organization's needs. With this information at your fingertips, you can make informed decisions about policy allocation and ensure that your cybersecurity strategy aligns seamlessly with your evolving digital environment. Zenarmor's commitment to transparency empowers you to optimize your security policies while staying within your chosen plan's policy limits.
Transition Today for Enhanced Security and Freedom!
We emphasize the significance of transitioning today to embrace the power of multiple policies for enhanced security and freedom. By taking action and upgrading to a plan that aligns with your organization's needs, you can empower yourself with a robust cybersecurity strategy that adapts to your unique requirements. This transition bolsters your defenses against evolving threats and affords you the flexibility to customize security measures to match your digital landscape. It's a step towards a safer, more secure, and more agile future. So, don't wait—make the transition today and experience the empowerment and peace of mind that come with knowing your organization is well-prepared to navigate the complex cybersecurity challenges of the modern world.


