Simple, always-on protection for distributed teams
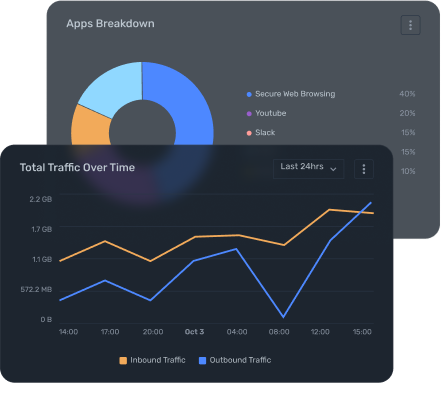
Block threats, control access, and secure every connection without performance or complexity trade-offs.
Zenarmor gives IT and security teams a simple, powerful way to secure their entire workforce across users, devices and locations.